Risky Biz News: Smart TVs take snapshots of what you watch
In other news: China wiretaps US wiretapping system; Australia provides free cyber support for small businesses; Ukraine clears Vitiuk in corruption probe.

This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

LG and Samsung smart TVs are shipping with intrusive technology that takes snapshots of the screen in order to track what users are watching.
The technology is named "Automatic Content Recognition" (ACR) and was pioneered in the early 2010s by Shazam.
It was initially offered via software libraries and SDKs, and was found only in a few apps, such as Netflix, Hulu, and others. However, over the past few years, ACR tracking tech has slowly crept into the core firmware of almost all modern-day smart TVs—making it almost impossible to avoid if you've bought a recent TV.
In a research paper published at the start of September, a team of academics from the US, the UK, and Spain has looked at how ACR works on LG and Samsung smart TVs.
The team used TVs in different modes and looked at network traffic to see when the TV was uploading captured snapshots to a central ACR server for analysis.
On the server side, these snapshots are analyzed against a database of known visual/video fingerprints to determine what type of content users are watching and then show relevant ads to the owner of that TV.
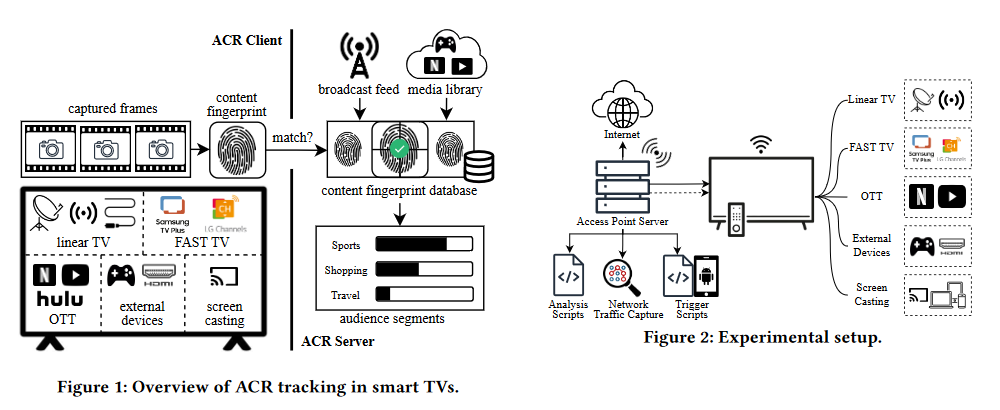
Researchers say that during their experiments, they've noticed traffic to known ACR server domains when users watched classic TV channels but also when the TV was connected to a PC or gaming console via HDMI.
ACR snapshots were taken multiple times per second, but data was only uploaded to ACR domains only once every 15 seconds.
Surprisingly, there was no ACR traffic when users watched streaming apps, such as Netflix or YouTube.
ACR tracking worked regardless if the user had registered or not an account on their TV.
The two TV makers also used different ACR domains per geographic region, suggesting the companies were at least trying to play nice with local privacy laws.
When researchers configured the smart TVs to opt out of ACR tracking, traffic to the ACR domains stopped, which means if you're just as creeped out as I am about this behavior, you can "safely" (for now) turn it off. You can follow the steps to disable ACR on your LG and Samsung smart TVs in this guide from The Markup. Congratulations to Samsung for making this entire process a 37-step ordeal.
Breaches, hacks, and security incidents
China wiretaps US wiretapping system: A suspected Chinese hacking group has breached systems at US broadband providers used by the US government for court-authorized network wiretapping requests. According to the Wall Street Journal, hackers breached wiretapping systems at AT&T, Lumen, and Verizon, and had access for months. Sources linked the incident to a Chinese hacking group known as Salt Typhoon. Officials are investigating if hackers breached the affected networks via Cisco routers.
Prison leak settlement: Medical claims processing company CorrectCare will pay $6.49 million to US prison inmates to settle a class action lawsuit. The company leaked the personal information of almost 600,000 prison inmates in 2022 after it misconfigured one of its web servers. Inmates in California, Louisiana, Georgia, and South Carolina who had data leaked in the incident are now eligible to receive $10,000 each for expenses related to the data breach. [Additional coverage in GovInfoSecurity]
General tech and privacy
The Broadcom skinning job continues: AT&T has sued Broadcom for hiking its VMware price by 1,050%. [Additional coverage in ArsTechnica]
Google standards meddling: There's some drama in the webdev world after Google's V8 team tried to block some JavaScript features because it would impact their performance. The incident has been described as the result of giving Google engineers too much say in web standards organizations and using that power to make their jobs easier.
WPP ships: Windows 11 version 24H2, which shipped last week, includes support for Windows Protected Print (WPP), a new and more secure Windows printing service.
Ecovacs privacy debacle: Chinese company Ecovacs is secretly using its smart vacuums to collect images, videos, and voice recordings to train AI models. The vacuums are also used to record 2D and 3D maps of users' homes. Ecovacs has also given itself the right to keep the recordinds even if users request to have them deleted. The new behavior is part of a privacy policy the company has silently rolled out to customers. According to the ABC, the policy is hidden inside its mobile app and fails to load when users try to read it.
Meta's EU case: The European Union Court of Justice ruled that Meta must reduce the collection and use of personal data for its Facebook advertising business. The ruling came in a lawsuit filed by European privacy organization Noyb. The court found that Meta was not following the core GDPR principle of "data collection minimization" and was still extracting heaps of information from its users.
Google smears more shit over its products: Google has announced new AI features for its search engine.
Mozilla announces move to advertising business: Mozilla has announced a major pivot from its browser to the online advertising business. This shift has been noticeable for a while, such as the organization laying off browser engineers and hiring AI and advertising people, adding ad-related settings and enabling them by default, or buying ad-related startups. It's only a matter of time until they sabotage ad-blockers in their browser, just like Chrome did.
Government, politics, and policy
Australia's free cyber support: The Australian government is providing AUD$11.1 million to small business owners to help them recover from cyberattacks. A non-profit advisory group named IDCARE will manage the fund and provide free assistance to small businesses dealing with cyberattacks. Minister for Small Business Julie Collins says the new service is expected to go live by the end of the year. [Additional coverage in the North West Star]
Moldova blocks more RU propaganda sites: The Moldovian government has blocked access to the four Russian websites used to spread Kremlin propaganda. The blocked websites include RuTube, Yandex, and the Dzen and Moldova24 news agencies. The move comes the Moldovian government has accused Russia of sending more than $15 million into the country to bribe voters ahead of an upcoming referendum to join the EU and the country's presidential election. Moldovan officials have also recently charged local priests urged their communities to support Kremlin candidates after taking trips to Russia. It also sentenced seven individuals to prison after organazing a violent protest with the purpose of overthrowing the government.
Ukraine clears Vitiuk: Ukraine's National Agency for the Prevention of Corruption has cleared Illia Vitiuk, the former head of the SBU's cyber division. The agency says it found no evidence to suggest that Vitiuk was living in a property that exceeded his family's legal income. Vitiuk was suspended in April and reassigned to the front after a news outlet claimed that he and his wife bought expensive real estate despite not having the financial means to do so. [Additional coverage in Censor.net]
"As a reminder, questions to Vitiuk arose after a Slidstvo.Info story in April. According to the journalists, the apartment bought by the official's wife is worth more than it is stated in the declaration. In fact, it was purchased at the market price and without renovation. And the wife is engaged in entrepreneurship, having a registered individual entrepreneur, whose income is declared as required by law."
Neuberger's message to cyber insurers: In an opinion piece in the Financial Times, US Deputy National Security Adviser for Cyber and Emerging Technology Anne Neuberger has urged cyber insurance companies to stop financing ransom payments. Neuberger says cyber insurance companies are using policies that cover ransomware payments, which encourage victims to take the easy way out and pay attackers. The official's op-ed comes as an informal warning and nudge to improve the practice. The US and its allies have repeatedly floated the idea of banning ransomware payments.
Election security: A month away from the US presidential election, CISA Director Jen Easterly says the country's election infrastructure is safer than it's ever been. [Additional coverage in the AP]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Airlock Digital founders Daniel Schell and David Cottingham about other things Microsoft can do to secure and harden Windows.

Cybercrime and threat intel
New npm malware: Twenty-eight malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
OT guidance: Cybersecurity agencies from Australia, Canada, New Zealand, the US, and others have published guidance for securing OT networks.
Dutch NCSC warns of fraud: The Dutch National Cyber Security Center says its phone number has been spoofed as part of a phishing campaign targeting Dutch organizations.
Wazuh abuse: Kaspersky has published a report about a threat actor that uses poisoned search results to infect users with crypto-mining malware. The novelty of this campaign is its use of the Wazuh open-source SIEM client as a backdoor and remote access to victims' systems.
Narketing163: Russian security firm FACCT has published a report on Narketing163, a new threat actor targeting Russian companies with phishing campaigns. The group has been active since July last year and has also run campaigns targeting other countries across Europe and Asia. Payloads include an assortment of malware, such as RedLine Stealer, Agent Tesla, FormBook, and the Snake Keylogger.
Malware technical reports
Snapekit: The Gen Threat Labs team has discovered Snapekit, a new rootkit targeting Arch Linux users.
Vilsa Stealer: CyFirma looks at Vilsa Stealer, a new infostealer that's been shared on GitHub.
Embargo ransomware: SonicWall's security team has published a report on the Embargo ransomware.
Sponsor Section
David Cottingham, CEO of Airlock Digital, shows Patrick how Airlock's execution control and allowlisting solution works.
APTs, cyber-espionage, and info-ops
Cuckoo Spear: Cybereason has published part two of its analysis of Cuckoo Spear, a campaign carried out by APT10. See part one here.
Okinawa independence disinfo: Japanese news agency Nikkei has uncovered a network of around 200 Twitter accounts pushing a disinformation campaign for the independence of the Okinawa region from Japan. The campaign is most likely Chinese in origin since China has made claims over the entire Ryukyu island chain in the past. Very friendly country, this China!

New Russian disinfo targets foreign mercenaries: Two Russian bot networks are running disinformation campaigns designed to deter foreign mercenaries and military instructors from helping the Ukrainian army. The two networks are using videos claiming that Russian forces execute mercenaries on the spot, that Russian businessmen are paying bounties for their heads, and that mercenaries fighting for Ukraine die due to poor training and lack of weapons. The two campaigns have been active on Twitter and have received more than 2.2 million views, being one of the most popular Russian disinfo operations in a while. [Additional coverage in Agents Media]
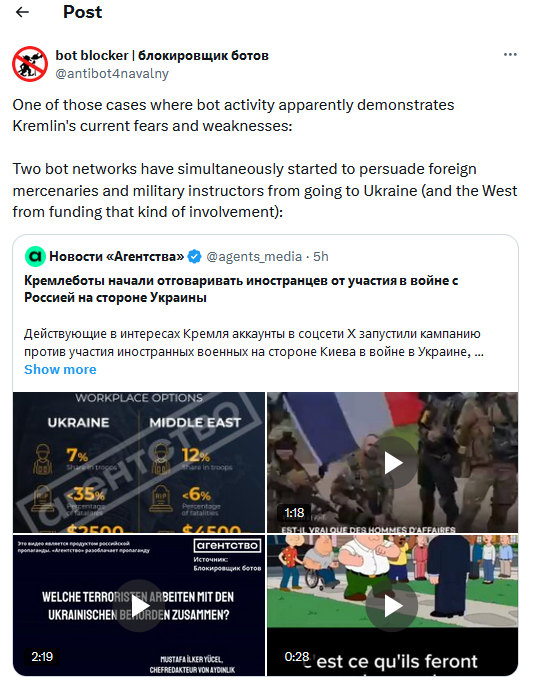
InfoRos reward: The US State Department is offering a $10 million reward for information on individuals working for Russian news agency InfoRos. Officials say the agency is secretly run by Unit 54777 of the Russian military intelligence service GRU. The unit has used InfoRos to spread Kremlin propaganda, disinformation, and meddle in the US elections. The US Treasury sanctioned InfoRos in March 2022, shortly after Russia's invasion of Ukraine.

Vulnerabilities, security research, and bug bounty
iOS security update: Apple has rolled out an iOS update to fix two security issues.
Visual Studio RCE: Serbian security researcher Miloš has published a write-up on CVE-2024-30052, a remote code execution in the Microsoft Visual Studio app that can be exploited via malicious dump files.
Okta patches: Identity management service Okta has rolled out a fix for a vulnerability that could have been used to bypass specific sign-on policies. The issue could have been exploited by attackers who had a user's password to bypass additional login checks and access secure systems. Okta says the bug had been present in its product since July this year.
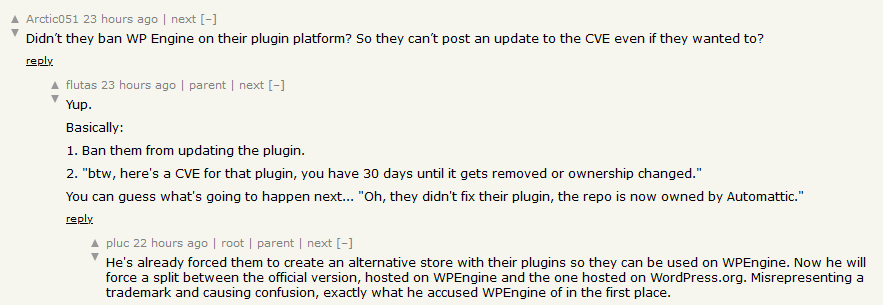
Automattic weaponizes bug disclosure: In a now-deleted tweet, Automattic has threatened to publish details about a bug in WP Engine if the company doesn't fix it in 30 days. Automattic is the owner of WordPress.com and a direct rival for WP Engine. Automattic's CEO Matt Mullenweg, has engaged in a public smear campaign of WP Engine over the past month and even used Automattic's influence over the WordPress open-source CMS to cut WP Engine's access to WordPress.org resources. More on this never-ending drama in TechCrunch.
Infosec industry
Google removes Kaspersky app: Google has removed the Kaspersky security and mobile VPN apps from the official Play Store, in the US and other regions of the world.
MITRE launches AI Incident Sharing initiative: MITRE has launched AI Incident Sharing initiative, a project for companies to share threat intel data about security incidents targeting AI-based systems.
Industry moves: Former Mandiant CEO Kevin Mandia has joined the board of directors of cybersecurity startup Expel. The move comes after Mandia also joined SpecterOps as chair of its board of directors last week. Mandia stepped down as Mandiant CEO in May after the company was acquired and integrated into Google Cloud.
New tool—Venator: Niantic Labs has released Venator, a flexible detection platform that simplifies rule management and deployment with K8s CronJob and Helm.
New tool—encap-attack: Security firm WithSecure has released encap-attack, a tool to sniff and attack networks that use IP-in-IP or VXLAN encapsulation protocols.
Threat/trend reports: Dashlane, Vectra AI, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats. The most interesting of these reports is the one from Dashlane that found that users of its password manager are still reusing passwords. The company says 48% of passwords stored in password vaults are reused.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about various Southeast Asian countries investing in cyber forces, the drivers behind these decisions, and what kind of actions make sense.
In this podcast, Tom Uren and Adam Boileau talk about how the US government's response to Iranian election interference is proceeding at light speed. This allows other actors, such as Meta, to make decisions relating to interference with certainty.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!






