Risky Biz News: Sisense breach has CISA and everyone else panicking
In other news: Apple sends mercenary spyware notifications in 92 countries; US prepares a full Kasperksy ban; BatBadBut bug impacts multiple programming languages.

This newsletter is brought to you by GreyNoise. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The US Cybersecurity and Infrastructure Security Agency (CISA) has urged customers of business analytics company Sisense to rotate all credentials and access tokens linked to the company's tools and services.
The agency said it was responding to a security breach discovered at Sisense by "independent security researchers."
At the time of writing, details about the hack and what exactly happened remain shrouded in mystery, but infosec peeps in the know seem to be treating it as a DEFCON 1 incident.
Sisense has not publicly disclosed the incident.
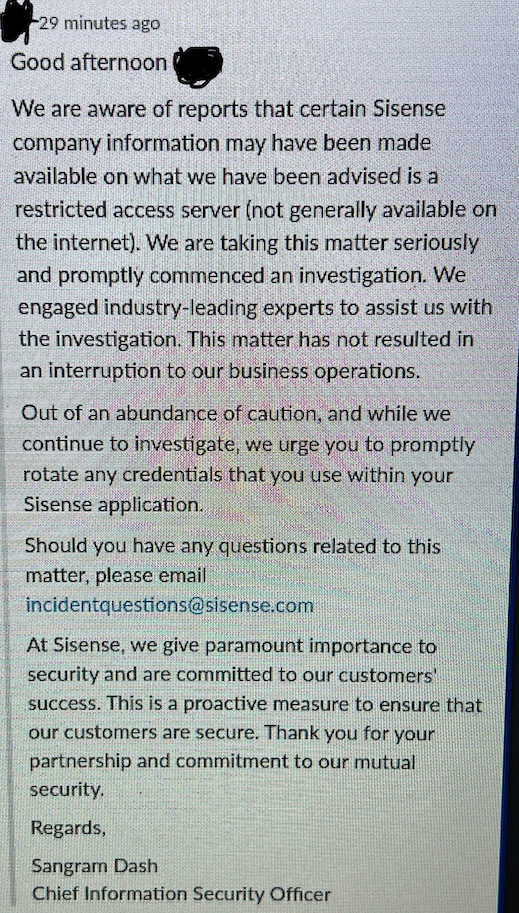
The company sent an email to customers earlier this week, asking customers to rotate any credentials they stored on Sisense servers.
The company stores customer credentials on its servers as a way for its business intelligence tools and services to access customer infrastructure and products and gather analytics. The company claims to have more than 1,000 customers, including some of the world's largest corporations and critical infrastructure operators.
The email—first obtained and shared by infosec reporter Brian Krebs—talks about a compromise of an internal Sisense server that stored customer data.
Although this looks like a hack of Sisense's internal network, several cybersecurity folks have described the incident as a supply chain attack, and there are many rumors going around on social media that the hackers might have already weaponized some of the credentials from the Sisense server to breach the company's customers.
Again—at the time of writing—this has not been confirmed.
In a forum post, one of the Sisense community managers promised more details later in the day (April 11), which may turn out to be after this newsletter goes live.
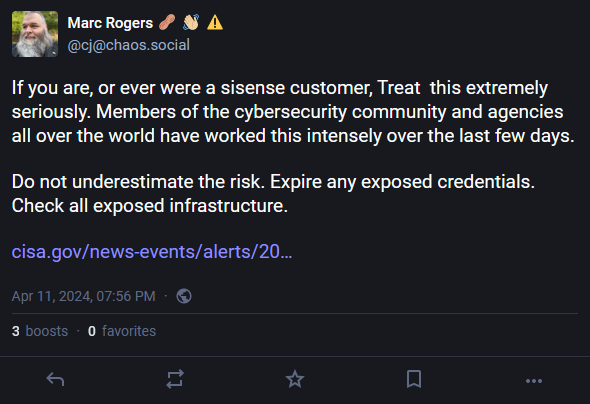
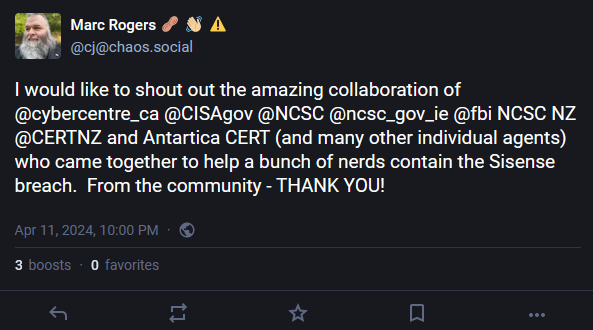
According to cybersecurity researcher Marc Rogers, cybersecurity agencies across the Five Eyes countries have been involved in responding to the breach, which may be a telling sign of its severity.
Breaches, hacks, and security incidents
Apple mercenary spyware notice: Apple has sent security alerts to users in 92 countries warning they might have been targeted with mercenary spyware. The company didn't say what kind of spyware it detected. Apple began notifying users of spyware attacks in 2021. It has notified users in over 150 countries since then. [Additional coverage in TechCrunch]
SiegedSec hack: Hacktivist group SeigedSec claims it hacked the River Valley Church in Burnsville, Minnesota, and used its funds to buy around 100 inflatable sea lions. The group says it hacked the church after its pastor made transphobic comments. [Additional coverage in the Daily Dot]
iCabbi leak: UK and Ireland-based ride-hailing service iCabbi left a server exposed online and leaked customer data.
False alarm code leak: Software maker SMC leaked the false alarm passwords for thousands of users. These are the passwords customers give to SMC to confirm a false alarm and not send a police unit to their premises. A security researcher found the leak via an older version of the SMC mobile app the company retired in 2022 but was still available via the Play Store. SMC says there was no evidence anyone abused the false alarm codes. [Additional coverage in BNR/English coverage in NL Times]
Israel MoD hack: An Iranian hacking group named NetHunter claims to have breached Israel's Ministry of Defense and stolen information on more than 500 Palestinian prisoners. [Additional coverage in NourNews]
Tkachev ransomware: One of Russia's largest agricultural enterprises has fallen victim to a ransomware attack. The incident impacted NI Tkacheva, a company owned by the family of former Russian Minister of Agriculture Alexander Tkachev. Hackers have breached the company's systems, encrypted files, and are now demanding a $5 million ransom. The incident is the latest in a series of ransomware attacks that have hit major Russian companies. [Additional coverage in Kommersant]
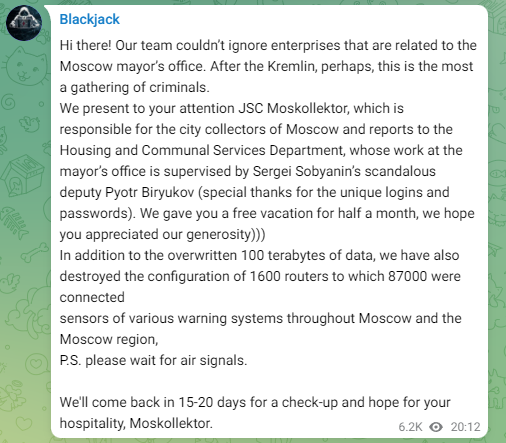
Moskollector wiper incident: Ukrainian hacking group BlackJack claims to have hacked and wiped the IT infrastructure of Moskollector. The company operates the IT systems of Moscow's sewage network. BlackJack says it wiped over 100TB of data and disconnected more than 87,000 water sensors from the central network. Neither the company nor Russian media have confirmed the incident. [Additional coverage in Liga.net/English coverage in the Kyiv Post]
General tech and privacy
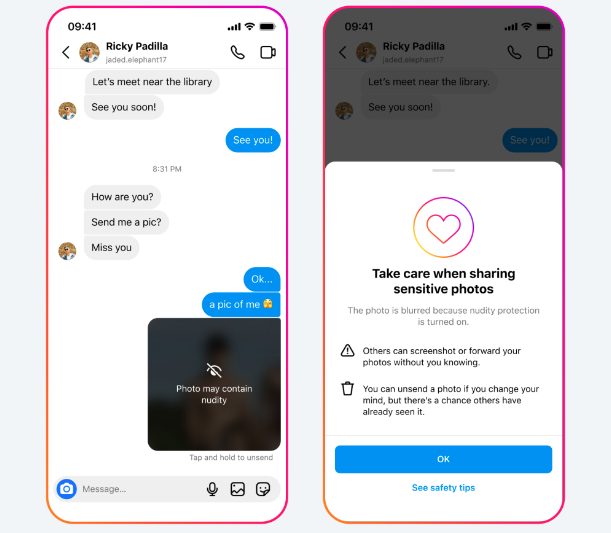
New Instagram anti-nude tools: Meta is testing a new tool on its Instagram platform that scans private messages for nudes and intimate images. The tool uses on-device scanning to detect nudity and automatically blur images. The company says it designed the tool to detect and block sextortion attempts against teens. The new nudity protection feature will be turned on by default for all teens under 18. Meta will also prompt adults to turn the feature on.
Chrome Enterprise Premium: Google has launched a premium version of its Google Chrome enterprise browser. The new Chrome Enterprise Premium will be available for $6/user/month. It provides new tools for data loss prevention, more granular filtering controls, and better malware scanning. Through the move, Google enters the commercial enterprise browser market. The former Chrome enterprise release will remain available for free under the name Chrome Enterprise Core.

Government, politics, and policy
CyberCom hunt-forward missions: US Cyber Command has deployed 22 hunt-forward missions to help US allies during 2023. Teams were sent to 17 countries and found 90 malware samples that were later made public. CyberCom has conducted hunt-forward missions since 2018. Officials say 2023 was the first year when Cyber Command had hunt-forward teams deployed simultaneously in all DOD geographic commands. [Additional coverage in The Record]
CISA ED on Microsoft hack: CISA issued an emergency directive in the aftermath of Russia's hack of Microsoft systems in January this year. Russian hacking group Midnight Blizzard compromised Microsoft last year and stole emails from the company's corporate server. CISA has now ordered federal agencies to reset any credentials included in email communications with Microsoft. Officials have also instructed federal agencies to review sign-in activity and other logs for suspicious activity. Agencies must complete security audits by the end of the month and report any breaches back to CISA.
CISA expands Malware Next-Gen: CISA has opened the Malware Next-Gen service to the general public. The service allows companies to submit malware samples and suspicious URLs for analysis by CISA systems. CISA launched Malware Next-Gen in November of last year for the use of US government and military organizations only. The service currently has more than 400 registered users.
US dam cybersecurity: The US Congress is worried about the poor state of digital defenses around the country's more than 91,000 dams. A recording of the hearing can be found here. [Additional coverage in CyberScoop]
US mulling full Kaspersky ban: The White House is preparing to issue an executive order that will ban the use of Kaspersky software in the US. The US government previously banned the use of Kaspersky software on government systems in 2017. The new ban will also apply to the private sector and home consumers. Sources have told CNN the ban is expected this month.
FISA S702 falls short: The vote to reauthorize Section 702 of the Foreign Intelligence Surveillance Act has failed in the US House of Representatives after former US President Donald Trump urged Republicans not to pass it. FISA S702 is set to expire on April 19. [Additional coverage in Axios]
Olympics cybersecurity: The French government has stepped in to provide emergency financing for Atos, the flailing French cybersecurity company tasked with securing this year's Summer Olympics Games. The company has a mind-numbing $5 billion in debt. [Additional coverage in Politico]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with GreyNoise founder Andrew Morris about last year's vulnerability exploitation trends, how the company's AI system works, and Catalin makes a fool of himself because he can't pronounce 'abnormalities.'

Cybercrime and threat intel
Cybercrime syndicate disrupted in Zambia: Zambian officials have arrested 77 individuals suspected of running an internet fraud syndicate. The raid targeted the offices of a Chinese company named Golden Top Support Services. Officials say the company ran call centers that spoofed phone numbers to run online scams. Zambian police seized 13,000 SIM cards for both domestic and international numbers. Twenty-two of the 77 detained suspects are Chinese nationals. [Additional coverage in the BBC]
Sextortion suspects plead guilty: Two Nigerian men pleaded guilty to sextortion-related charges.
NSO transparency report counter: Researchers at Always Watching have published a counter—or call it a debunk—of NSO's most recent Transparency Report [PDF].
Intellexa's Alladin: Israeli news outlet Haaretz reports that Intellexa has developed a new product named Alladin that can infect both Android and iOS devices using online ads only.
Cognyte may be in trouble: Israeli surveillance company Cognyte sold cyber-intelligence systems to Myanmar in violation of a global arms embargo. Israeli news site Haaretz reports the country's attorney general's office has declined to open an investigation.
Threat/trend reports: Abnormal Security, Bitdefender, Check Point, CyberCX, CyFirma, the IMF, and Uptycs have recently published reports covering infosec industry threats and trends.
Nitrogen campaign: Malwarebytes breaks down a malvertising campaign using malicious PuTTY and FileZilla apps to infect users with the Nitrogen malware.
TA547 campaigns: Proofpoint identified TA547 targeting German organizations with an email campaign delivering Rhadamanthys malware. This is the first time researchers have observed TA547 use Rhadamanthys.
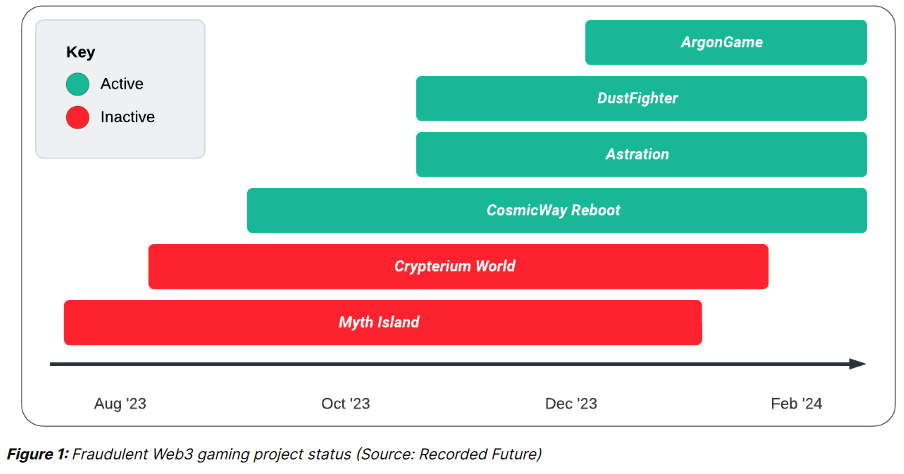
Web3 malware campaign: A Russian-speaking threat actor has set up fake Web3 gaming projects that infected users with malware. The projects mimic legitimate games but infect macOS and Windows users with infostealers. Recorded Future says the campaign has been active since August of last year and has run at least six malicious Web3 gaming projects so far.
Fake GitHub popularity campaign: Threat actors are using fake stars and automated updates to manipulate GitHub search results and promote malware-infected projects. The repos are Visual Studio projects that install malware on a developer's system when they build the app. According to Checkmarx, the malicious code installs a version of Keyzetsu, a malware strain that can manipulate the Windows clipboard.
FBI social engineering warning: The FBI published a recent reminder about common social engineering techniques used by threat actors in recent attacks.
New NSA guidance: The NSA has published new guidance on how to implement zero trust access principles to data at rest and in transit.
LockBit investigations: UK police claim to have identified the real-world identities of several members of the LockBit ransomware gang. The suspects are part of a group of over 200 LockBit members officials are tracking. Law enforcement agencies from across the world disrupted the LockBit gang in an operation at the end of February. [Additional coverage in Bloomberg]
DarkVault RaaS: The new DarkVault ransomware operation is apparently LockBit's attempt at a rebrand. I wonder what gave it away.
Malware technical reports
ScrubCrypt: Fortinet researchers look at how the ScrubCrypt file crypting service has been used across a wide range of malware campaigns.
Havoc C2: Immerisive Labs analyzes Havoc C2, one of today's most popular command-and-control frameworks, used for red team exercises but also often abused by threat actors.
Raspberry Robin: HP looks at the Raspberry Robin malware and its new infection vector that relies on Windows Script Files (WSF). The malware has been using this technique since March.
New Vultur infrastructure: Embee Research used passive DNS data to discover new server infrastructure associated with the Vultur Android banking trojan.
XZ backdoor: SentinelOne has published its own report on the XZ Utils incident and backdoor.
Sponsor Section
GreyNoise founder Andrew Morris demonstrates how people use the GreyNoise sensor network.
APTs, cyber-espionage, and info-ops
eXotic Visit: ESET is tracking a cyber-espionage campaign they have named eXotic Visit. The campaign has been taking place since November 2021 and targeted individuals in India and Pakistan. ESET has identified at least 380 victims who have downloaded malicious Android apps from the official Play Store and third-party websites. The apps were infected with a version of the open-source XploitSPY malware. ESET has linked the campaign to a new threat actor it calls internally as Virtual Invaders.
Turla: EclecticIQ looks at Turla's latest campaign, which targeted European organizations with the TinyTurla-NG backdoor.
Earth Hundun: Trend Micro looks at recent operations of the Earth Hundun APT, also known as BlackTech. The report looks at Deuterbear, a new version of their older Waterbear backdoor.
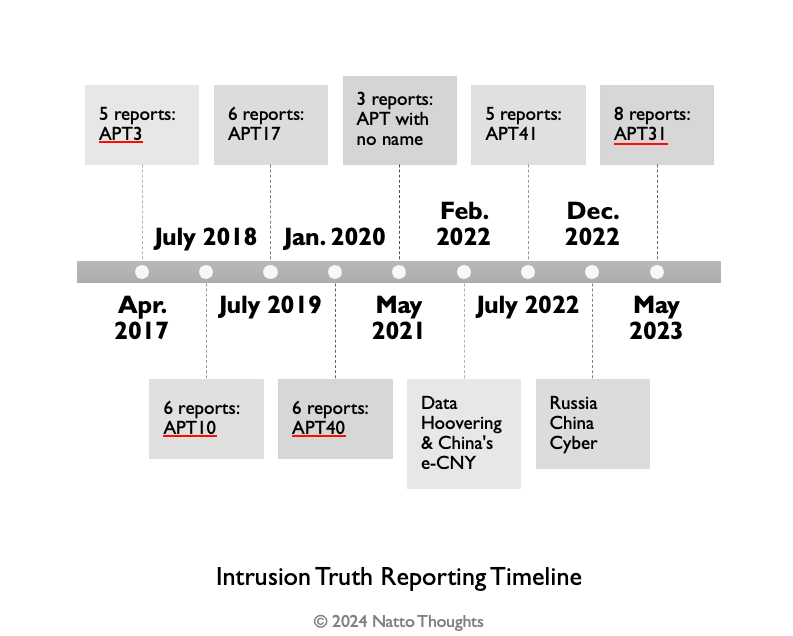
Intrusion Truth profile: The Natto Thoughts team has published a profile on APT-doxing group Intrusion Truth and what threat intel analysts can learn from its methods.
Vulnerabilities, security research, and bug bounty
Microsoft adds CWE data: The April Patch Tuesday was the first time that Microsoft has used the Common Weakness Enumeration (CWE) industry standard to describe its security bugs. The new addition should make it easier for security vendors to categorize Microsoft patches going forward. Microsoft previously used its own in-house system to describe vulnerabilities.
Spring Framework update: The Spring Framework has released security patches for a bug tracked as CVE-2024-22262.
TP-Link factory reset bug: TP-Link routers are vulnerable to a DoS bug that can be abused to reset devices to factory settings via the TP-Link Device Debug Protocol (TDDP).
AWS STS bug: Stedi researchers have identified and helped fixed a bug in AWS STS that could have allowed threat actors unauthorized access to customer resources.
XZ Utils: The XZ Utils source code is back on GitHub and the account of the project author has also been unbanned.
Tor security audit: The Tor Project published a security audit for its censorship circumvention tools like WebTunnel, OnionShare, and others.
Linux kernel zero-day: Ukrainian security researcher Yurii Crimson has published details and proof-of-concept exploit code for a zero-day in the Linux kernel. The zero-day is a race condition in the Linux kernel module that supports the GSM 07.10 multiplexing protocol. It can be exploited for privilege escalation attacks. Details were published last week, but no patches have been released so far. Another researcher appears to have tried to take credit for the bug. Vuln disclosure drama incoming! [h/t Voidzero]
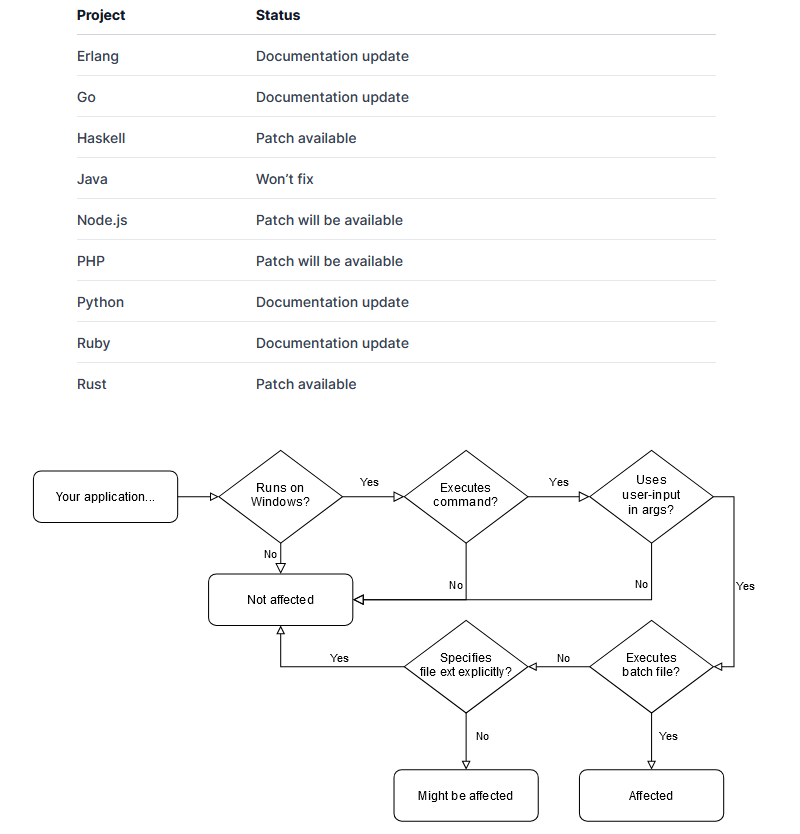
BatBadBut vulnerability: Security researchers have discovered a vulnerability in multiple programming languages that can allow threat actors to run malicious code on Windows systems. The vulnerability impacts any Windows app that can execute batch files. Affected programming languages fail to sanitize batch file command-line arguments, which allows the execution of malicious code. The issue impacts Rust, PHP, Node.js, and many others. Researchers at Flatt Security discovered the bug, which they named BatBadBut "because it's about batch files and [is] bad, but not the worst."
Infosec industry
Acquisition news #1: Cloud security firm Wiz has acquired cloud detection and incident response startup Gem Security.
Acquisition news #2: Proton, from ProtonMail fame, has acquired encrypted notes app Standard Notes.
New tool—Monocle: Roke vulnerability researcher James Stevenson has released Monocle, a Large Language Model for binary analysis.
New tool—Voipire: Cryptic Red's Darren McDonald has released Voipire, a tool that can scan and exploit the RTP bleed vulnerability.
New tool—Malwarebytes Digital Footprint Portal: Malwarebytes has launched the Digital Footprint Portal, a new web service that allows users to check what kind of data they have had exposed online through data breaches.
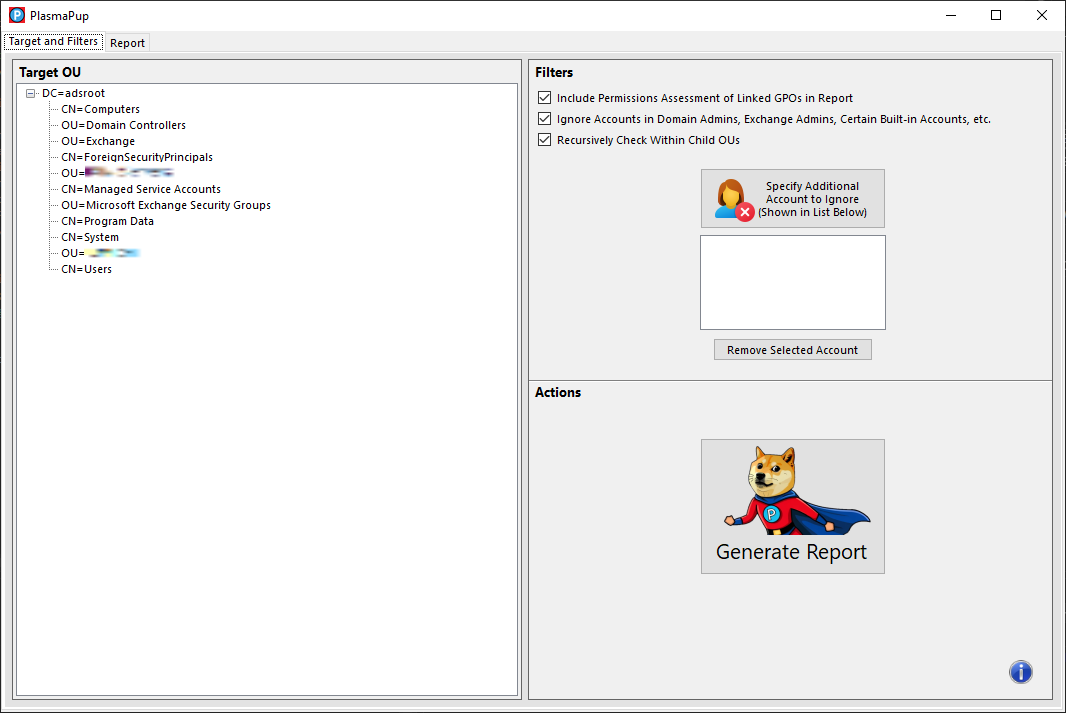
New tool—PlasmaPup: Ross Geerlings has open-sourced PlasmaPup, a tool is designed to help central and departmental IT personnel understand their exposures in Active Directory.
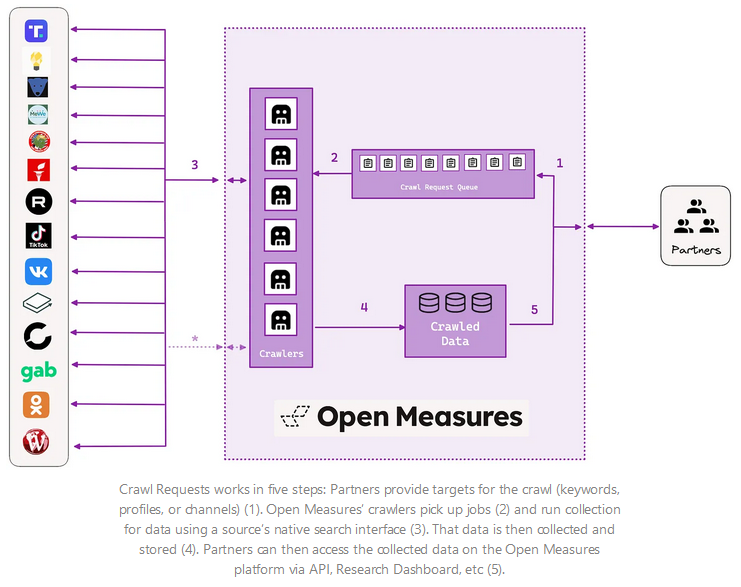
New tool—Crawl Requests: Social media research group Open Measures has published a new tool named Crawl Requests that can retrieve content from multiple social media networks, regardless of limitations and blocks.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the tradecraft used in the compromise of the XZ open-source data compression project.




