Risky Biz News: Secure Boot not working on recent MSI motherboards
In other news: Norton Password Manager hit by credential-stuffing attack; hacktivists leak Cellebrite tools; Lexmark printer zero-day disclosed.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
For almost a year, the Secure Boot feature on MSI motherboards has been broken and allowing malicious code to run, Dawid Potocki, a Polish IT student studying in New Zealand, has discovered.
Secure Boot is a feature that works at the motherboard chipset level, where it uses cryptographic signatures to verify the authenticity of drivers and operating system files before booting up a computer.
When Secure Boot is enabled inside the BIOS or UEFI firmware of a computer (actually the motherboard firmware), if drivers or the OS bootloader have been tampered with by malware, the boot-up process stops with warnings for IT administrators.
But while this works as intended for many motherboard vendors, Potocki says that since January 2022, MSI appears to have changed the default settings of its Secure Boot section in its UEFI/BIOS with new defaults that effectively make Secure Boot useless.
The new defaults are in the "Secure Boot" section, under the "Image Execution Policy" menu, where all options are now set to "Always Execute."
What this means is that even if malware has modified an OS bootloader, the MSI UEFI/BIOS will still boot the image, even if the cryptographic signature has failed.

Potocki says that since January 2022, MSI has been shipping MSI firmware updates that contain the new insecure Secure Boot defaults.
Tens of MSI motherboard models currently ship with these new settings for both Intel and AMD CPUs, impacting both Windows and Linux distros. A full list of impacted MSI motherboard models is available here.
While it may take some time for MSI to ship new firmware versions with fixed settings for its Secure Boot section, Potocki recommends that all MSI motherboard owners who rely on Secure Boot go into their UEFI/BIOS and change away from "Always Execute" to another policy.
"Don't trust that whatever security features you enabled are working, TEST THEM! Somehow I was the first person to document this, even though it has been first introduced somewhere in 2021 Q3."
Breaches and hacks
CircleCI shares more info: After disclosing a security breach at the start of the year, continuous integration and continuous delivery platform CircleCI has published more details about what really happened behind the scenes. CircleCI says that hackers broke into its internal network after infecting one of its engineers with malware. The hacker used the malware to steal a session cookie for CircleCI's backend network, where they lingered for four days between December 19 and December 22, stealing internal databases and data stores, including from systems that stored customer environment variables, tokens, and keys. CircleCI says that even if this data was normally encrypted, the hacker also dumped and stole the encryption key needed to read the data. CircleCI says it learned of the incident after one of the affected companies notified them about suspicious activity coming via their CircleCI-GitHub integration. CircleCI says that since learning of the hack, it worked with GitHub to rotate all CircleCI OAuth tokens, which should prevent the threat actor from using any of the stolen access tokens to pivot and hack other companies. Regardless, CircleCI still recommends that customers also investigate any irregular activity that took place via its integration between December 19 and January 7.
Datadog incident: Cloud security firm Datadog says it was impacted by CircleCI's recent incident and that one of its secret access tokens was theoretically exposed. Despite this, Datadog says it saw "no indication that the key was actually leaked or misused."
SEC sues law firm following APT attack: The US Securities and Exchange Commission has sued DC-based law firm Covington & Burling in an attempt to reveal the names of customers impacted by a security breach that took place in November 2020. The SEC says the breach was carried out by Hafnium, a suspected Chinese cyber-espionage group, and targeted lawyers that dealt with "policy issues of interest to China in light of the incoming Biden Administration." According to court documents, Hafnium accessed internal network drives and email accounts, and the law firm extensively cooperated with the FBI. The SEC is now trying to use the courts to force Covington & Burling to disclose the names of its affected customers and see if the law firm and its customers broke any securities laws by not disclosing the existence or the breadth of their respective breaches. [Additional coverage in Reuters]
NortonLifeLock cred-stuff attack: NortonLifeLock is sending data breach notifications to customers of its Norton Password Manager service, alerting users that hackers have breached their accounts using a credential-stuffing attack. The incident took place in the first half of December last year. NortonLifeLock says that 925,000 accounts were targeted but did not disclose how many were compromised. Passwords stored in those accounts should be considered compromised, and users will need to change them as soon as possible.
24h Le Mans Virtual incident: This year's edition of the virtual version of the 24 Hours of Le Mans race has been interrupted twice after two servers that were used to host the event have been impacted by what organizers have described as a "security breach." The interruptions lasted around 90 minutes, but the race eventually resumed and concluded without any other issues. Despite this, the event has been deemed a success, mostly because of the participation of both e-sports content creators and professional drivers, such as IndyCar driver Felix Rosenqvist, former F1 driver Romain Grosjean, and two-time F1 champ Max Verstappen (while it lasted).
Goose Goose Duck attacks: Goose Goose Duck, a Steam game that currently averages around 600,000 users/day, says its servers have been under a constant and daily DDOS attack for almost two months. The game's developer says the attacks are the reason why its services have often gone down for the past month but that they have now hired cybersecurity specialists to help them deal with the ongoing threats, responsible for downtime as recent as this past week. Games that find sudden success often face issues like these, usually from extortion groups or rival competitors.
Royal Mail was ransomware: The "cyber incident" that brought down international shipping for the Royal Mail postal service in the UK has been linked to the LockBit ransomware gang, according to a ransom note seen by BBC reporters. The LockBit gang denied involvement in the intrusion for several days before admitting they were behind the attack; via a post made on an underground Russian cybercrime forum. A possible reason for the gang's anxiety in linking their name to the attack is that postal and shipping services are considered critical infrastructure, and the incident is very likely to draw both the attention and action from the British government in a similarly aggressive way as the US has reacted to the Colonial Pipeline and the Kaseya attacks and how Australia reacted to the Medibank incident.
Alleged Reg.ru hack: A group of pro-Ukrainian hackers has claimed to have breached Reg.ru, Russia's largest domain name registrar. The group has leaked the data via their Telegram channel and even claimed to have breached the company twice after initially being booted from the network.
Cellebrite & MSAB leak: Hacktivist group Enlace Hacktivista has leaked phone forensics software and documentation from Cellebrite and MSAB, two companies known for selling forensics software to law enforcement agencies. Enlace says they received the files from an "anonymous whistleblower" and leaked them because tools from both companies were used in the past for human rights abuses.
General tech and privacy
Brave expands Tor support: The team behind Brave has updated their browser to support Tor bridges, which are special servers that constantly change their IP addresses to avoid censorship. This feature has rolled out with Brave 1.44 and will allow Brave users in oppressive regimes or from inside restricted networks to connect to the Tor network via a Tor bridge—either automatically selected by the Brave browser itself or via one provided by the user. In addition, the most recent Brave 1.47 version also comes with support for Snowflake, an extension developed by the Tor Project that allows users' browsers to serve as proxies for users in censored countries and relay their connection to the Tor network.
Intel, Microsoft "return" to Russia: Both Intel and Microsoft have restored the ability for Russian users to access their websites and download drivers and OS updates. Both companies blocked Russians from accessing their sites in mid-2022 after Russia's invasion of Ukraine.
Meta sues scraper: Meta has filed a lawsuit against Voyager Labs for using fake accounts to scrape data from Facebook and Instagram profiles. Meta says the Israeli company is scraping other social media sites as well and is offering the data for sale via its proprietary platform, advertising itself as an "AI-based investigation solutions" to fight against cybercrime, terrorism, and organized crime. Complaint is here [PDF].
TrustCor removed from Chrome root store: Google's security team has removed the TrustCor certificate authority from the Android and Chrome root stores, systems that control which certificates are trusted by the Android OS and the Chrome web browser, respectively. The decision comes after a group of academics found ties between the Panamanian company and companies from the surveillance industry [also see WaPo coverage]. Microsoft and Mozilla also removed support for TrustCor certificates from their browsers in December last year.
Twitter cuts off third-party apps: In what looks to be a desperate attempt to get users back on the official site and app, where it can flood them with ads, Twitter has cut off access to its platform for third-party apps without any warning or explanation. [Additional coverage in 9to5Google]
Government, politics, and policy
TikTok banned in North Carolina and Wisconsin: The governors of North Carolina and Wisconsin have banned the use of TikTok's app and website on government employee devices. The bans aren't a surprise at this point since TikTok is now banned in more than half of the US states, but the bans are somewhat important because they are in Democrat-led states, with North Carolina [PDF] and Wisconsin [PDF] becoming the third and fourth blue states to ban the app after Kansas and New Jersey.
French general warns of US cyber experts: In an interview with French newspaper Le Monde, General Aymeric Bonnemaison, the head of France's Cyber Defense Command, has warned that US cyber defense teams helping European countries defend their networks in light of Russia's invasion of Ukraine also expose those countries to Washington's intelligence gathering. The general is referring to what US Cyber Command calls hunt forward operations. Gen. Bonnemaison described the missions as "relatively aggressive" and that they go "go far enough" inside networks in order to secure them, access that could also be abused for espionage. [Source in Le Monde, English coverage]
NSA FISA renewal: NSA and Cyber Command head honcho Gen. Paul Nakasone is back in lobby mode, asking US lawmakers to extend the NSA's surveillance capabilities. Section 702 of the Foreign Intelligence Surveillance Act, which allows US intelligence agencies to collect online communications without a warrant, is set to expire this year. Gen. Nakasone says this provision has been extremely fruitful for US agencies and has allowed the US to uncover future terrorist attacks and fend off cyberattacks. "We have saved lives because of 702," Naksanoe said during an event last week.
CISA FY2022: CISA has published its year-in-review report for fiscal year 2022. The report primarily deals with the agency's work on national cybersecurity defense and agency task unification efforts.
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
BitConnect restitutions: A US judge has ordered that over $17 million be paid to approximately 800 victims from over 40 different countries as restitution for their investment losses in a fraudulent initial coin offering orchestrated by cryptocurrency service BitConnect. US authorities say that, in reality, BitConnect operated as a "textbook Ponzi scheme" by paying earlier BitConnect investors with money from later investors.
Malicious PyPI packages: Fortinet says it discovered three malicious Python libraries uploaded on the official PyPI portal. The packages, named colorslib, httpslib, and libhttps, were uploaded to the site by the same author (Lolip0p) and contained the same malicious code that would attempt to download and run malicious EXE files.
GhoseSec claims: The team at SynSaber dumped a truckload of cold water on GhostSec's claims that they've successfully deployed ransomware on an RTU (remote terminal unit), a type of ICS equipment.
Crypto address poisoning attacks: Cryptocurrency wallet service MetaMask is warning users about a new type of scam that relies on a technique called "address poisoning."
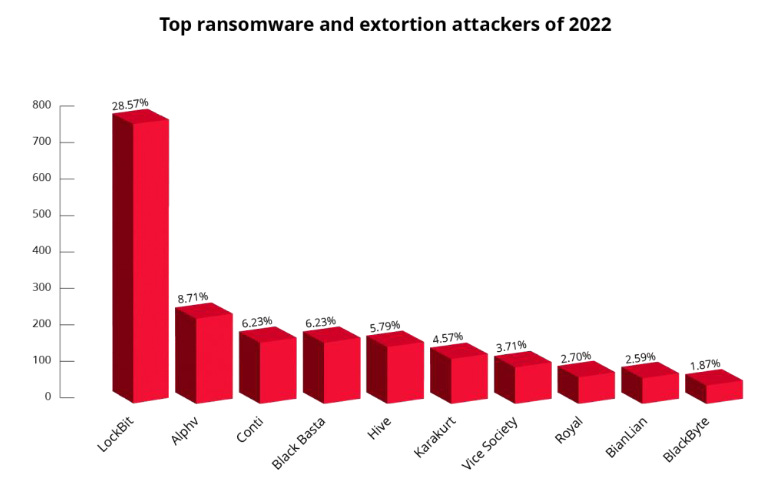
Cybercrime in 2022: Threat intelligence company KELA has published its yearly report [PDF] on cybercrime for the past year. Some of the company's main findings are below.
- Almost 2,800 victims of ransomware and extortion attacks.
- Victims were listed on 60 different leak sites.
- 52% of these new platforms emerged in 2022.
- Lockbit was 2022's most active group.
- Initial access brokers offered access to more than 2,200 networks, collectively valued at more than $4.5 million.
Malware technical reports
Mr.SNIFFA: The Malwarebytes team has a breakdown of an e-skimmer campaign that was built on the Mr.SNIFFA Magecart framework.
Sliver C2 implant analysis: CuratedIntel's Michael Koczwara has published a technical analysis of the Sliver C2 framework's implant.
VagusRAT: A new remote access trojan named VagusRAT has been spotted sold online via a dedicated website. According to cybersecurity firm CYFIRMA, the malware has already been used in the wild in campaigns that abuse Google ads to redirect users to malicious sites hosting cracked software. Once infected, the campaign's operators use VagusRAT to access a victim's device to either steal sensitive files and credentials or install additional payloads.

APTs and cyber-espionage
Bitter APT: Chinese security company Zhongfu Information has published a report on recent Bitter APT operations.
MuddyWater APT: The security team at the China National Technical Import and Export Corporation (CNTIC) has published a report on the recent operations of the MuddyWater APT.
Kimsuky: If you're in South Korea, just be aware that Kimsuky has been spear-phishing Kokoa users over the past few weeks.
Vulnerabilities and bug bounty
wolfSSL vulnerabilities: Trail of Bits researchers have published details about four vulnerabilities they found and helped patch in the WolfSSL library. All are denial of service (DoS) issues.
Lexmark zero-day: Security researcher Peter Geissler has published the exploit they used during the Pwn2Own Toronto 2022 hacking contest. While the exploit failed during the contest, Geissler says the vulnerability at its core is still unpatched more than a month later.
CVE-2023-21752 (Windows): Proof-of-concept code for CVE-2023-21752, an elevation of privilege vulnerability in the Windows Backup Service, has been published on GitHub. The vulnerability was patched last week during the January 2023 Patch Tuesday. Filip Dragovic from Infigo IS, the security researcher who found and reported the issue to Microsoft, released the PoC.
CVE-2022-31705 (VMWare): Proof-of-concept code for CVE-2022-31705, a heap out-of-bounds write vulnerability in VMware ESXi, Workstation, and Fusion, was published on GitHub. The vulnerability was revealed at the GeekPwn 2022 security conference and patched last month.
CVE-2022-42841 (macOS): Details have also been published by Sector7 on CVE-2022-42841, a bypass of the macOS package signature verification system. The bug was patched by Apple in mid-December.
Another MacDirtyCow exploit: After exploits for the MacDirtyCow vulnerability were released for both macOS and iOS, now Google's Project Zero team has also joined the party with their own versions. The vulnerability can be used to get root on macOS and jailbreak iOS devices. Apple patched MacDirtyCow, also known as CVE-2022-46689, in mid-December 2022.
Infosec industry
Guccifer interview: The Intercept has an interview with Guccifer, the Romanian hacker who breached the email account of a Hillary Clinton aid and leaked their sensitive emails back in 2013 and, as The Intercept puts it, "changed the world almost by accident." Guccifer, real name Marcel Lehel Lazar, was released from prison in August 2021.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




