Risky Biz News: Samsung smartphones impacted by no-user-interaction zero-days
In other news: FBI investigates TikTok for spying on journalists; BreachForum admin arrested in the US; aCropalypse vulnerability can recover cropped and redacted screenshots.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Google's Project Zero research team has identified 18 vulnerabilities in Exynos, a modem chipset manufactured by South Korean company Samsung and used by multiple smartphone vendors and even some vehicles.
Project Zero says that of the 18 vulnerabilities, four are incredibly dangerous as they allow for what the company calls "Internet-to-baseband remote code execution attacks."
Google says that tests carried out by Project Zero researchers have confirmed that attackers can compromise a smartphone with no user interaction and only require that the attacker knows the victim's phone number.
Of the 18 vulnerabilities, Samsung has patched only six in security updates in January and March this year. Of the four big RCEs, only one has received patches—see CVE-2023-24033.
Google has published its findings after some of the 18 bugs it reported to Samsung hit the 90-day deadline, which it gave Samsung to fix the issues.
Based on publicly available information, none of the 18 vulnerabilities appear to have been exploited in the wild, but Google says that skilled attackers would be able "to quickly create an operational exploit to compromise."
Until Samsung releases patches and until the patches make it to consumers, Google says that users should be safe if they turn off "Wi-Fi calling" and "Voice-over-LTE (VoLTE)" in their device settings.
While a list of affected users who might be using a device with an Exynos modem/chipset may not be complete, the following are known to be vulnerable:
- Mobile devices from Samsung, including those in the S22, M33, M13, M12, A71, A53, A33, A21s, A13, A12 and A04 series;
- Mobile devices from Vivo, including those in the S16, S15, S6, X70, X60 and X30 series;
- The Pixel 6 and Pixel 7 series of devices from Google; and
- any vehicles that use the Exynos Auto T5123 chipset.
Breaches and hacks
Wawa breach settlement: Convenience store chain Wawa has agreed to pay $28.5 million to settle a class-action lawsuit stemming from a 2019 data breach. Hackers breached the company in 2019 and ran malware on its point-of-sale systems for eight months. The intruders collected more than 30 million credit card details, which they later sold on the dark web. Three major credit unions sued Wawa in 2020 for financial relief after they had to replace cards and reimburse stolen funds.
NBA breach: The NBA is notifying users of a data breach that impacted its email service provider. The sports league says that names and email addresses were stolen from the third-party's systems. While the NBA warns of increasing phishing-related risks, it says that now passwords for its website were compromised. The NBA didn't name the email service provider.
HMIS hack: Indian cybersecurity firm CloudSEK says that a pro-Russian hacktivist group named Phoenix has compromised the website of India's Health Ministry and gained access to the ministry's official database system, the Health Management Information System (HMIS). The hackers claimed to have gained access to information on all Indian hospitals, doctors, and other employees. The group claimed they carried out the attack as a consequence of India's agreement to honor oil price caps and sanctions imposed on Russia by fellow G-20 countries.
ParaSpace avoids hack: Cryptocurrency platform ParaSpace paused transactions and prevented a hacker from stealing $5 million worth of funds from its accounts. The attempted hack was described as an exploit against one of the platform's smart contracts and was spotted before it did any damage by blockchain auditing firm BlockSec. It also helped that the attacker also didn't have enough funds for the necessary "gas price" to run the exploit during their first hack attempt. Ironically, after the attack was spotted the second time, the hacker had the audacity to ask BlockSec to refund the gas price they wasted on the second attack. [Press coverage in BitcoinInsider]
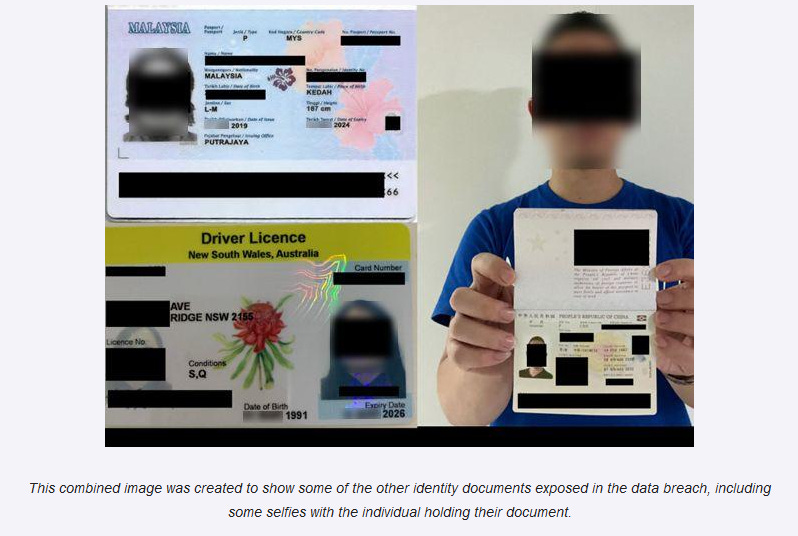
Fiatusdt leak: The Fiatusdt cryptocurrency platform left a database with KYC data exposed online. Passports and IDs for 20,000 users were exposed.
General tech and privacy
GitHub stars black market: DevOps company Dagster has a deep dive into how to spot projects that have bought GitHub stars off the black market.
Safe npm: DevOps company Socket has released what it calls "safe npm," a security wrapper for the npm package manager utility that pauses installations whenever it detects a malicious or risky package.
NordVPN goes FOSS: NordVPN has open-sourced its Linux VPN client, Libtelio, a networking library used across NordVPN apps, and Libdrop, a library used to share files over Meshnet.
Meta tracking deemed illegal: The Austrian Data Protection Authority (DSB) has ruled that Facebook's use of its tracking pixel directly violates the GDPR. The ruling comes after consumer protection organization noyb filed more than 100 complaints against the company across Europe.
Linux project refuses Russian company's patches: The Linux kernel project has declined to accept a patch submission request from Russian hardware vendor Baikal Electronics. See the full message below:
"We don't feel comfortable accepting patches from or relating to hardware produced by your organization.
Please withhold networking contributions until further notice."
Government, politics, and policy
NZ'z TikTok ban, warning in Scotland: New Zealand has banned the use of the TikTok app by lawmakers and other Parliament workers. The ban enters into effect at the end of March.
TikTok warning in Scotland: Scottish government officials were "strongly advised" to remove the TikTok app from all their government devices. While not an official ban just yet, Scotland joins the increasing ranks of countries who are beginning to distrust the Chinese-owned app.
Australia investigating TikTok: In the meantime, the Australian government has published a 113-page report [PDF] it received from academics as part of its TikTok investigation. The document describes TikTok's deep ties to the Chinese Communist Party and is viewed as preparation for a government-wide ban that may arrive in the coming weeks.
FBI investigates TikTok: The FBI and Justice Department have allegedly launched an official investigation into ByteDance for using the TikTok application to spy on American journalists. The news comes via Forbes [Non-paywall version here], which reported last December that Bytedance spied on one of its reporters covering the company in an attempt to identify their sources [Non-paywall version here]. ByteDance says it fired the individuals who surveilled the journalists.
FCC action on scam texts: The US Federal Communications Commission adopted new regulation mandating that US telecommunications providers block SMS messages coming from invalid, unallocated, or unused numbers. The FCC described the move as the "first regulations" that target the increasing problem of scam SMS text messages sent to US consumers, also known as robotexts. The FCC says that while some robotexts are advertising, some messages also contain links to phishing sites and mobile malware.
EU's Cyber Resilience Act: The European Commission is circulating a new version of the upcoming EU Cyber Resilience Act. This new version makes automatic security updates the default option for IoT devices and removes the five-year limit during which vendors are required to carry out security assessments of their products and offer security patches. Despite the changes, the document has not been modified to remove clauses that were deemed harmful to open-source projects. [More coverage in Euroactiv]
Russia criminalizes data theft and data trading: The Russian Duma will vote in April on an update to its criminal code that will criminalize the theft and sale of personally identifiable information (PII), per Interfax. Miscreants would face up to 10 years in prison and fines of up to two million rubles ($26,000).
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
BreachForums admin detained: The FBI has arrested a New York man for allegedly running BreachForums, or Breached, today's largest cybercrime forum for trading stolen data. The suspect has been identified in court documents as Conor Brian Fitzpatrick, who goes under the hacker alias of Pompompurin and is listed as one of the BreachForums administrators. The BreachForums is considered the successor of RaidForum, which the FBI took down in April 2022. While BreachForums has been around for months and used to trade billions of stolen personal records, the reality is that the arrest comes days after one of the BreachForum users used the forum to sell the personal data of US lawmakers. While the charges don't mention it, Fitzpatrick was also involved in hacking the FBI's servers in November 2021 to send out hoax messages. BreachForums remains live. In a statement following Fitzpatrick's arrested, a data trader known as Baphomet announced they had taken over the forum as the main administrator in Pompompurin's place. [More in KrebsOnSecurity]
Second ViLE member arrested: Law enforcement officials in Florida have detained a suspected hacker. The suspect, named Nicholas Ceraolo, was charged last week by the US Justice Department for allegedly hacking into one of the DEA's web portals. Ceraolo—together with a second suspect named Sagar Steven Singh—stole data from the DEA portal and extorted victims for money with threats of posting their information online. Singh was detained prior to the DOJ announcing charges. According to Motherboard, Ceraolo was detained shortly after officials announced the charges. He is now free on bail.
Malware dev detained: Ukraine's Cyber Police detained a 25-year-old man for allegedly developing a malware strain that infected more than 10,000 computers worldwide. Officials say the suspect distributed the malware, which appears to be a remote access trojan, using boobytrapped computer games. The malware had the ability to download and upload files, install and uninstall programs, take screenshots of the user's screen, capture sound from the microphone and video from built-in or external cameras. Ukrainian officials say the suspect stole information from infected systems in order to hijack online accounts and potentially steal electronic funds. At the time of the arrest, officials say the suspect still had access to 600 systems.
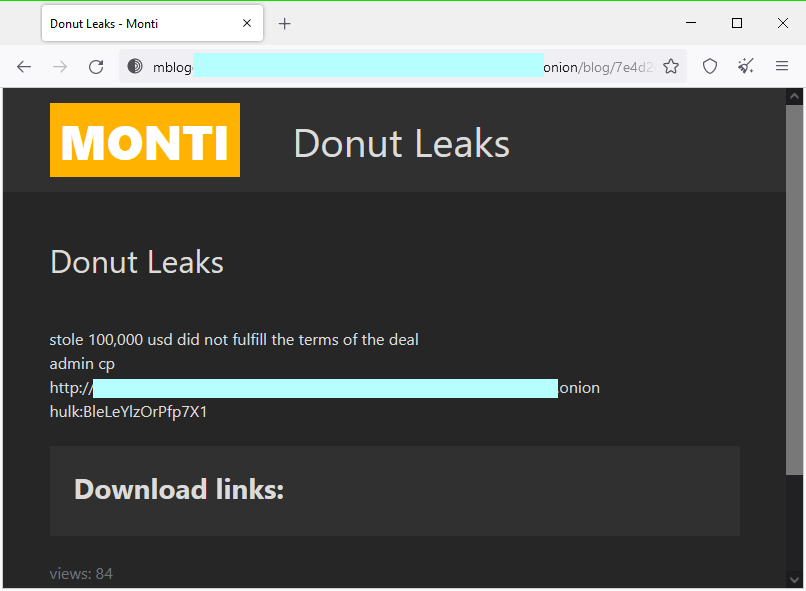
Monti leaks Donut: The Monti ransomware gang has leaked the cPanel (web hosting software) credentials for one of their rivals, the Donut data extortion group. In a post on the Monti leak site, Monti claims the Donut gang did not fulfill the terms of a "deal" and stole $100,000. No other details at the moment, but grab your popcorn.
Ransomware decrypter: Kaspersky researchers have released a free decrypter to recover files that were encrypted by a ransomware gang known as MeowCorp. Kaspersky says it built the decrypter after the gang released the decryption keys for their past victims on a Russian-speaking forum. The group's ransomware was built on the old Conti ransomware that was leaked online last year.
Killnet DDoS attacks: Microsoft has an analysis of the DDoS attacks carried out by the Killnet group against healthcare providers since the start of this year. Microsoft said the group's attacks had no impact on Azure services and its customers.
Tax season is here: And ArmorBlox has a report on a phishing campaign impersonating the US Social Security Administration.
HP Wolf Security report: HP's Wolf Security team has published its Q4 2022 threat report. Some of the report's highlights include:
- Archive file types remained the most popular form of delivering malware (42%). Imaging file types, like IMG, came second with 31%.
- Threat actors are experimenting with QR codes in their lures to steal credit and debit card details from victims.
- Attackers are bypassing perimeter network security controls, such as email gateway scanners, by embedding malicious links in PDF files.
- Q4 saw a surge in SEO/SERP poisoning campaigns.
Infostealer landscape: Chinese security firm Antiy has a report summarizing all the infostealer it detected in the wild in 2022. All the usual suspects show up.
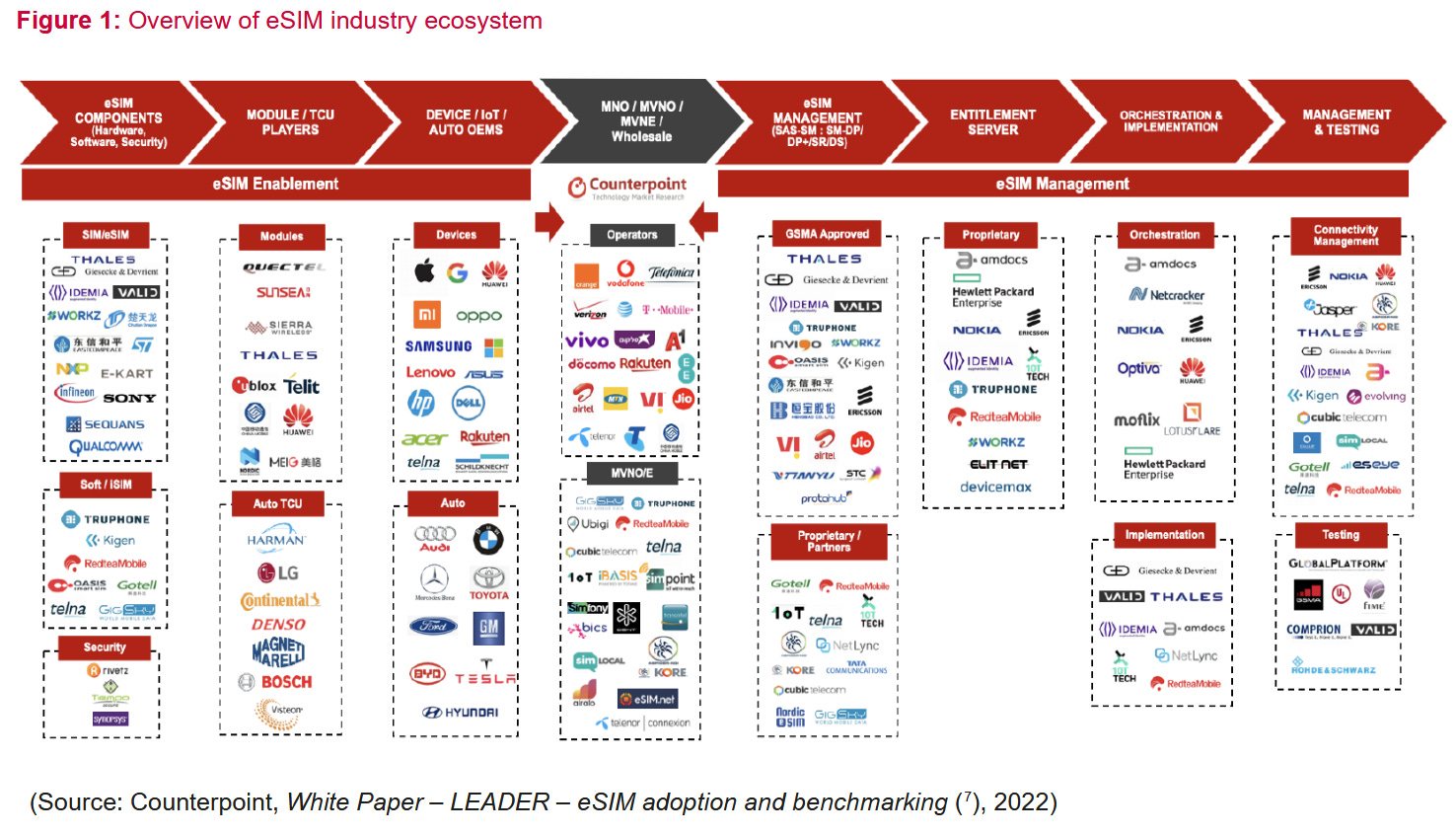
eSIM threat landscape: ENISA, the EU's cybersecurity agency, has published a threat landscape assessment of the embedded SIM ecosystem. Threat intel firm Intel471 published a report earlier this year warning about the possibility of eSIMs being abused for number hijacking.
Malware technical reports
Android clippers: ESET researchers have identified dozens of copycat Telegram and WhatsApp websites that are trying to trick visitors into installing malicious Android and Windows apps on their devices. ESET says both the Android and Windows apps contain clippers, a type of malware that replaces cryptocurrency addresses copied in the device's clipboard with addresses controlled by the attacker, hoping to hijack transactions. Furthermore, ESET says some of the clippers also took a screenshot of a user's cryptocurrency wallet and then used OCR technology to extract the mnemonic phrases—that act as passwords—and hijack the victim's wallet. ESET says this was the first time it saw OCR abused this way.
IcedID: Elastic's security team details a recent GZip technique employed by the IcedID trojan.
CryptBot: OALABS has published an analysis and IOCs for the CryptBot infostealer.
Healer AVKiller: OALABS has published an analysis and IOCs for Healer, a .NET tool typically used together with Redline Stealer to shut down antivirus products.
ShellBot: AhnLab researchers have a report on ShellBot, a variant of the PerlBot DDoS botnet malware that typically infects Linux systems via poorly configured SSH.
Chaos botnet: Sysdig has a report out on Chaos, the Go-based DDoS botnet spotted last year by Lumen.
EvilQuest ransomware: Reverse engineer Amr Ashraf has a very deep technical breakdown of the EvilQuest macOS ransomware strain.
CatB ransomware: SentinelOne has a report on the CatB ransomware, previously analyzed by Fortinet and MinervaLabs.
"As the time of writing, the BTC address associated with CatB ransomware have zero transactions and a zero balance."
Sponsor Section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company has recently launched a new type of canary token that looks like an Azure login token and warns companies whenever a threat actor tries to use them.
Our (free) AWS Canarytokens have always been popular.
— Thinkst Canary (@ThinkstCanary) 5:04 PM ∙ Feb 13, 2023
Today, we released the Azure alternative on our canarytokens.org server¹
Attackers who find ‘em have to use ‘em (and reveal their presence).
Check out Pieter’s blog post at: blog.thinkst.com/2023/02/canary…
__
¹ also free
APTs and cyber-espionage
Roaming Mantis: Team Cymru has published the third part of its report on MoqHao (or XLoader), an Android malware strain used by the Roaming Mantis group, typically deployed via SMS phishing. This part covers attacks from the past months, which targeted Africa, Asia, and Europe. The first two parts covered the group's phishing infrastructure and attacks in Japan (part 1.5), and its attacks expanding into Europe.
Kimsuky: South Korean security firm S2W notes that the Kimsuky cyber-espionage group is now abusing OneNote documents for their spear-phishing campaigns. The group follows in the footsteps of financially-motivated cybercrime groups, which have been using OneNote for payload distribution for the past few months. See Emotet as the most recent adopter of this technique.
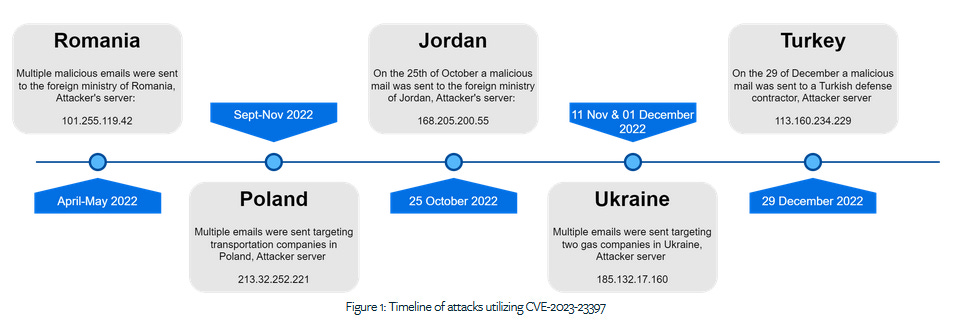
Outlook RCE exploitation: Security firm DeepInstinct published details about the targets where the recent Outlook zero-day was used last year. Microsoft says the Outlook zero-day (CVE-2023-23397) was used by "a Russia-based threat actor" in limited attacks against "a limited number of organizations in government, transportation, energy, and military sectors in Europe." DeepInstinct report identified the targets as the Foreign Ministry of Romania, the Foreign Ministry of Jordan, transportation companies in Poland, two gas companies in Ukraine, and a Turkish defense contractor.
Vulnerabilities and bug bounty
D-Link vulns: GreyNoise has an analysis of CVE-2022-41140 and CVE-2023-24762, two vulnerabilities in D-Link router firmware.
OpenSIPS security audit: Enable Security has published the full version of their security audit of OpenSIPS, a multi-functional, multi-purpose signaling SIP server used by major telecoms. The audit identified 15 vulnerabilities, all of which have been patched.
aCropalypse vulnerability: Two security researchers—Simon Aarons and David Buchanan—have discovered a serious vulnerability in Markup, the built-in screenshot editing tool that ships on Google Pixel smartphones. Named aCropalypse, the vulnerability can be used in some instances to fully or partially recover the original image data of a cropped screenshot. Furthermore, the vulnerability can also be used to decloak redacted screenshots. The vulnerability was fixed earlier this month in the Pixel March 2023 security updates. However, Aarons and Buchanan say that screenshots taken via Pixel devices over the past several years are affected and can be recovered or decloaked if they have been shared online. The duo has set up a demo tool that takes advantage of the aCropalypse bug to recover original screenshots.




