Risky Biz News: Samsung, MediaTek, and other Android platform certs were leaked and used to sign malware
In other news: Rackspace discloses security incident; Black Panthers gang detained in Spain; new CertPotato attack.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Platform certificates from major Android vendors and software makers have leaked and were used to sign malware, the Android Security Team discovered last month.
Platform certificates are digital certificates used by Android OEMs and ODMs to sign versions of the Android OS they deploy on their devices, their firmware, and official vendor apps they might ship to consumers. Because of the crucial role they play, any Android app signed by a platform cert usually gets the highest level of trust and access to an Android device.
Last month, the Android Security Team found several malware samples in the wild that were signed by platform certificates used by major vendors like Samsung, LG, MediaTek, and Revoview.
Since discovering the incident, the Android Security Team said it worked with the affected companies to revoke and rotate the leaked platform certificates.
"OEM partners promptly implemented mitigation measures as soon as we reported the key compromise. End users will be protected by user mitigations implemented by OEM partners. Google has implemented broad detections for the malware in Build Test Suite, which scans system images. Google Play Protect also detects the malware."
It's unknown if the platform certificates were hacked from the vendors' infrastructure or if they were leaked to a threat actor by malicious insiders. Google has asked vendors to launch internal investigations.
While malware signed using the leaked platform certs was spotted in the wild, Google said none was uploaded on the official Play Store.
In a blog post last week, security firm Rapid7 said that while the use of certificates to sign malware is usually the sign of a state-sponsored threat group, the malicious apps that were signed in this incident are run-of-the-mill adware.
"This finding suggests that these platform certificates may have been widely available, as state-sponsored actors tend to be more subtle in their approach to highly privileged malware," said Rapid7's Erick Galinkin.
Breaches and hacks
Rackspace security incident: Cloud hosting platform Rackspace took down its hosted Microsoft Exchange email server infrastructure following what the company described as a "security incident." The incident took place on Friday, December 2, and Rackspace was still working on restoring affected services at the time of this newsletter on Monday morning. No confirmation yet that this is a ransomware attack. British security researcher Kevin Beaumont believes Rackspace's Exchange servers were most likely hacked using the ProxyNotShell vulnerability.
Accuro hack: New Zealand health insurer Accuro said that hackers gained access to its systems in a security incident last week. The company said that while it has no evidence that customer data was accessed, it can't rule out this possibility and urged users to be vigilant of possible fraud.
Ankr crypto-heist: Cryptocurrency platform Binance said it paused its integration with the Ankr DeFi protocol after an attacker used a leaked Ankr platform developer key and minted Binance BNB coins worth more than $4 billion in fiat currency. The attacker is believed to have stolen roughly $5 million worth of cryptocurrency before Binance stopped in to cut off their access, although it appears that Binance did manage to freeze $3 million of this.
CoinTracker email leak: Cryptocurrency wallet CoinTracker said that a compromise of one of its service providers exposed a list of customer emails and referral links. CoinTracker said no other personal data was exposed and that hackers did not gain access to any of its infrastructure.
FBI investigating DraftKings credential stuffing incident: ESPN is reporting that the FBI is investigating the credential stuffing attack that hit sports betting platform DraftKings last month and following which hackers stole more than $300,000 from the company's customers. Rival sports betting platform FanDuel also reported a spike in account takeover attacks at the same time as the DraftKings incident.
ARSAT incident: ARSAT, an Argentinian state-owned terrestrial and satellite telecommunications provider, said it suffered a security breach of its corporate network. Although the incident took place right before the Argentina-vs-Poland World Cup soccer match, ARSAT said customer service was not disrupted by the attack.
Beeline hack: Hackers have leaked the personal information for thousands of Beeline employees. Beeline—one of Russia's largest mobile telecommunications providers—confirmed the leak to Russian news outlet Vedomosti. The hackers claimed they obtained the data after accessing one of the company's internal LDAP servers. The same group previously leaked data from other major Russian organizations, such as the Russian state-owned postal service, travel booking platform Tutu, delivery service DeliveryClub, and online learning platform GeekBrains.
General tech and privacy
Chrome Enhanced Protection: In its quarterly report for Q3 2022, the Chrome security team said they saw a 16% quarter-over-quarter growth in the number of Chrome users who opted into the Enhanced Safe Browsing Protection feature. In addition, Google said they also revamped rules and increased payouts for the Chrome bug bounty program, which resulted in an increase in submissions that contained functional exploits and bisections (where the bug reporter points out the specific commit or commit range where the bug was introduced in the Chrome source code).
Dumb Twitter stuff: This weekend, Elon Musk released what he described as internal documents related to Twitter's alleged "censoring" of the Hunter Biden laptop story (sincere apologies for bringing this dumb thing up, but there's a reason). The documents were released to a questionable reporter, who then proceeded to tweet out some of their content. The reporter, Matt Taibbi, forgot to redact the documents, and several US politicians, their staff, and Twitter employees, including former CEO Jack Dorsey, had their emails and other details leaked in the whole saga, which, btw, was a wet fart, as everyone expected. [Coverage in The Verge]
@elonmusk Got to the end of that thread and the TLDR is basically:
— Adam Hollander (@HollanderAdam) 12:25 AM ∙ Dec 3, 2022
"A bunch of Twitter employees would routinely block tweets at the request of both Democratic and Republican white houses. Here's one example from the Democratic side."
Government, politics, and policy
DHS CSRB to review Lapsus$ activity: The Department of Homeland Security (DHS) Cyber Safety Review Board says it intends to review attacks carried out by the Lapsus$ extortion group. The board says it plans to put out a report on how the group bypassed a broad range of security measures without the use of advanced malware and managed to breach a large number of high-profile targets. Lapsus$ has been linked to intrusions at Cisco, Microsoft, Nvidia, Samsung, Uber, Rockstar Games, and other big corps.
GAO report on IoT/OT security: A GAO report published last week found that US government departments have paid little to no attention to the types and security of their internet-connected devices. What else is new? The report has several recommendations for the Department of Energy, the Department of Homeland Security, and the Department of Health and Human Services.
UK MSP regulation: The UK government has introduced new mandatory reporting rules for managed service providers (MSPs). Following an update to its NIS regulation, the UK government says that MSPs have become an unofficial part of most of the UK's critical infrastructure, and just like most operators in this field, they will have to report all cybersecurity-related incidents that disrupt their infrastructure and the services of their customers. Besides new reporting rules to government agencies like Ofcom, Ofgem, and the ICO, MSPs will also have to follow a set of basic cybersecurity standards to ensure their systems are protected against common attacks. Organizations that fail to follow the new rules could be fined up to £17 million ($20.9 million), the government said.
Fidesz abused government data for political spam: A report from Human Rights Watch says that Hungary's ruling political party Fidesz has abused personal data stored in government databases to send political-themed spam to citizens in this year's parliamentary elections. HRW says that data from the country's COVID-19 vaccine signups and tax benefits applications was pilfered by Fidesz officials and then bombarded with political campaign messages. The party's entire campaign was fraught with abuses, and international observers noted that Fidesz abused its control over government resources to break campaign financing rules and restrict the opposition's air time.
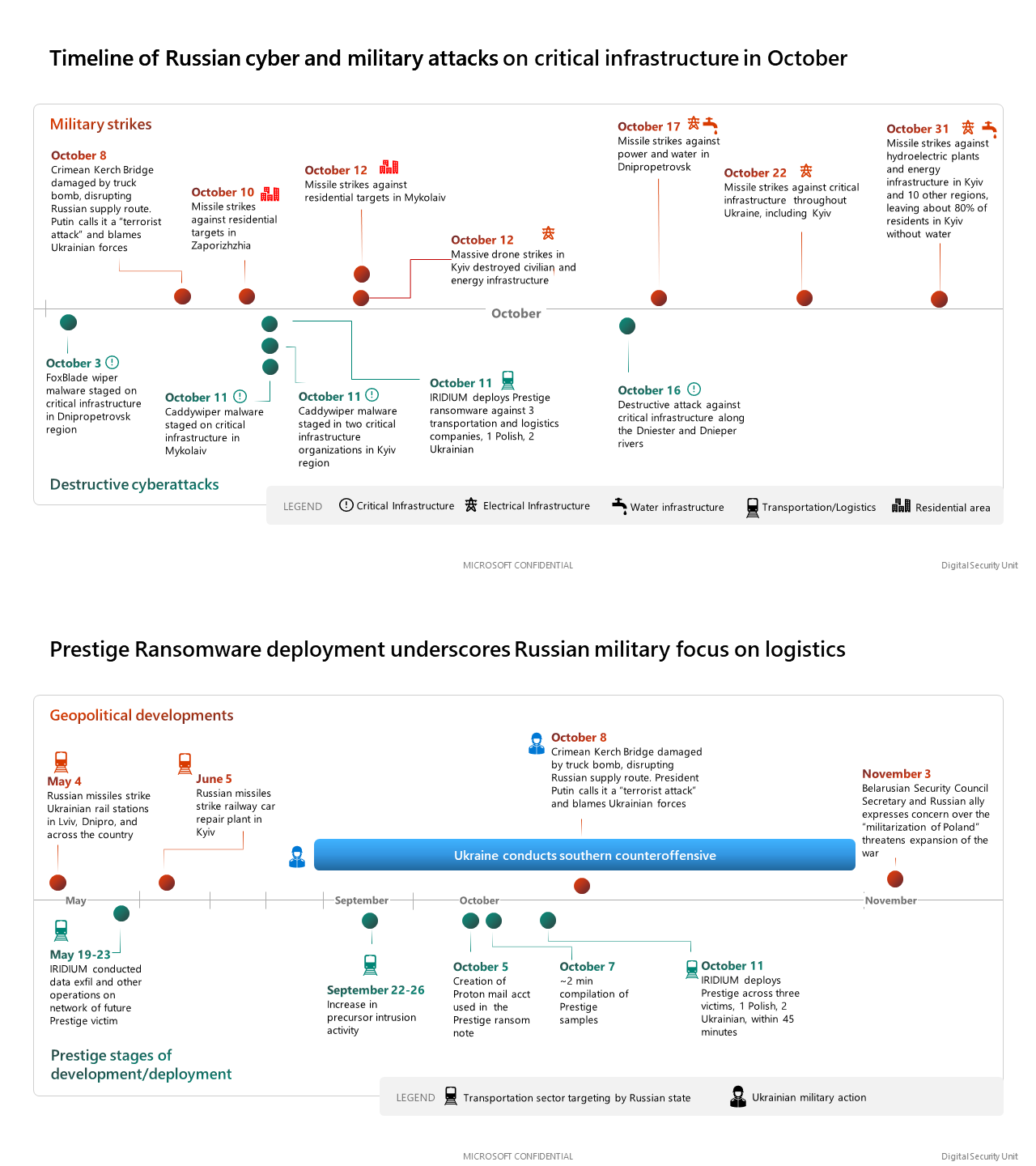
Coordination between Russian kinetic and cyberattacks: Microsoft said it is continuing to see "strong circumstantial evidence" that Russia is coordinating cyberattacks and military kinetic operations in Ukraine. In a report published on Friday, Microsoft said they saw destructive malware deployed in Ukrainian regions that were often hit by missile strikes a few days later. The report covers operations that took place in October 2022, and is the third report Microsoft published this year—after one in April and then June—where the company saw the same pattern of Russia deploying destructive malware before launching military operations.
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
Black Panthers gang: Authorities in Spain have detained 55 members of the Black Panthers cybercrime gang, a group suspected of stealing more than €250,000 from more than 100 victims. Spanish police said the Black Panthers operated out of Barcelona, and the gang was split into multiple cells, each specialized on one single task, such as phishing, vishing, carding, social engineering, and SIM-swapping attacks. The group's leader was also detained in the recent raids.
SIM swapper gets 18 months: A New York judge has sentenced Florida man Nicholas Truglia to 18 months in prison for helping launder more than $20 million worth of stolen cryptocurrency. The Justice Department said Truglia made his cryptocurrency wallet available to a group of SIM swappers, which then used it to send stolen funds and then redirect the profits to their own accounts. US officials said Truglia's account was used to launder $20 million, of which he kept $673,000 for himself.
$140 million revenue: A team of academics says that data they collected from 30 dark web underground markets over a period of eight months suggests that cybercrime groups made roughly $140 million from the sale of stolen data. The report, published in January this year, compiled data from 96,672 ads placed by 2,158 vendors across the dark web's largest markets. Academics say marketplaces had 26,342 sales and generated $5,847,417 in revenue on average, but a large part of the profits was concentrated in a few hotspots, such as Agartha ($91 million), Cartel ($31 million), and DeepMart ($9 million). [Press coverage in The Conversation]
$3.3 billion in crypto stolen this year: Blockchain security firm PeckShield said roughly $391 million worth of cryptocurrency funds were stolen in November 2022, bringing this year's total to more than $3.37 billion so far.
Pass-the-Cookie attacks: Netwrix has a basic breakdown of a Pass-the-Cookie attack. These types of attack is seeing broader adoption by phishing kits, as it allows them to steal cookies via phishing sites, not only just the user's credentials. These authentication cookies are then used to bypass 2FA protections.
BlackProxies: DomainTools researchers have a report out on BlackProxies, a malicious proxy service that has been gaining adoption in the cybercrime underground. The service claims to have access to more than one million residential IP addresses, which it offers to rent out to cybercrime gangs to help disguise their malicious operations.
New npm malware: Five new malicious npm packages spotted. Check out GitHub's security advisory portal for details.
PyPI malware: ReversingLabs researchers discovered ten PyPI packages pushing modified versions of the W4SP Stealer malware. Researchers say the packages appear to be part of a concerted malware campaign that has been specifically focused on infecting Python developers with the W4SP Stealer malware, a campaign that has been ongoing since September and has also been spotted by other security firms like Checkmarx and Phylum.
Conti gang: Chinese security firm has a report out on the Conti ransomware gang and some of its recent attacks that leveraged an Exchange vulnerability to breach corporate networks.
Malware technical reports
QakBot: Here's one more report on QakBot, this time from Splunk.
Titan Stealer: OALABS has TTPs and IOCs for the new Titan Stealer malware.
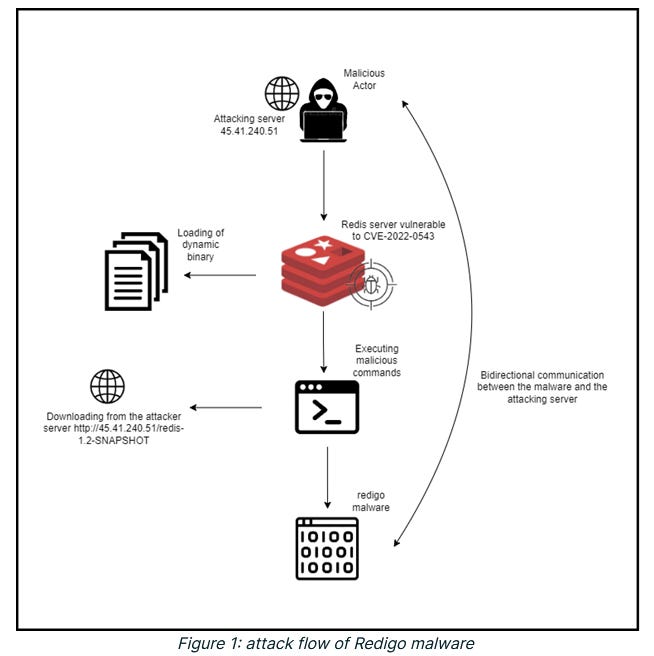
Redigo: AquaSec researchers have spotted a new malware strain named Redigo that is currently being used to attack and infect Redis database servers. Redigo is written in the Go programming language and leverages an exploit for the CVE-2022-0543 vulnerability to compromise unpatched Linux servers. AquaSec said Redigo-infected servers are being added to a botnet but that it's unclear what these systems will be used for. Typical scenarios usually include cryptomining, DDoS attacks, or proxy networks.
APTs and cyber-espionage
Lazarus AppleJeus campaign: Volexity researchers have spotted a fake cryptocurrency application that installs a version of AppleJeus, a malware strain previously associated with the Lazarus North Korean hacking group. Volexity says the malware used a novel DLL side-loading technique to infect targets, a technique that was later also spotted as part of a Lazarus spear-phishing campaign as well.
More Lazarus: More on another Lazarus campaign, this time targeting South Korea with malicious LNK files.
Mustang Panda: Avast has a write-up on a Mustang Panda APT campaign that is heavily exfiltrating data from Myanmar government agencies and embassies across the world. The stolen data includes email inbox dumps, stolen documents, and browser data (passwords, cookies, history, and payment card information). It's a pretty cool report overall since it focuses on analyzing exfil methods and infrastructure, stuff that's not typically covered in APT reports.
Influence operations: Google's TAG security team has published a summary of the coordinated influence operation campaigns terminated on Google platforms in Q4 2022 (so far). The biggest takedowns this quarter were linked to China (5,197 YouTube channels and 17 Blogger blogs) and Russia (783 YouTube channels, 5 AdSense accounts, and 2 Google News domains), as always, but also one influence op in Brazil that was propping up Jair Bolsonaro's campaign.
Vulnerabilities and bug bounty
Chrome zero-day: Google has released a security update for the Chrome web browser to fix a zero-day vulnerability exploited in the wild. Google said it tracks the zero-day as CVE-2022-4262 and describes it as a type confusion in V8, Chrome's JavaScript engine. The vulnerability was discovered by one of the Google TAG researchers. This also marks the ninth Chrome zero-day discovered this year.
ConnectingWise quiet patching: Remote desktop management service ConnectWise has quietly patched a vulnerability that was being abused in the wild by phishing gangs to take over ConnectWise accounts, Brian Krebs reported.
Artifact poisoning: Researchers from Legit Security have published a report on a new technique called Artifact Poisoning that can be used to modify a GitHub project's resources using the GitHub Actions feature. Researchers said the technique is useful for carrying out supply chain attacks.
"We have discovered that when transferring artifacts between different workflows, there is a major risk for artifact poisoning – a technique in which attackers replace the content of a legitimate artifact with a modified malicious one and thereby initiate a supply chain attack. This is similar to the CodeCov supply chain breach, where attackers put a backdoor into one of Codecov's artifacts which were later used by users to update their software and thereby got hacked."
Visual Studio Code RCE: Microsoft has fixed a major vulnerability in its Visual Studio Code service that could have been used for remote code execution on the web and desktop versions of Visual Studio Code.
Hell's Keychain: Cloud security firm Wiz discovered a vulnerability that allowed them to access the internal infrastructure of IBM Cloud. Wiz says they could have modified the company's CI/CD pipeline and poison artifacts deployed in the company's production-ready PostgreSQL environments. IBM has patched the vulnerability, which Wiz named Hell's Keychain. IBM said it was aware of Wiz's actions at all times, and no customer data was ever in danger.
CertPotato attack: Orange's SensePost team has a report out on CertPotato, a new privilege escalation attack for elevating virtual and network service accounts to NT AUTHORITY\SYSTEM. The attack abuses the Windows Active Directory Certificate Service (ADCS).
Anker Eufy camera vulnerability: Security researchers have discovered that you can bypass authentication and encryption on Anker Eufy internet-connected cameras and access other people's live feeds just by connecting to an IP address from Anker's cloud using the VLC media player. When confronted by reporters about the issue, Anker denied that was possible but silently started making changes to its backend to address the issue. [Coverage of the whole disaster is available in The Verge]
Infosec industry
New tool—WindowSpy: Security researcher CodeX has published a project named WindowSpy, which is a Cobalt Strike beacon mod that can be used to spy only on certain OS windows, based on the window title, such as browsers navigating to login pages, VPN sessions, confidential documents, and so on.
"The purpose was to increase stealth during user surveillance by preventing detection of repeated use of surveillance capabilities e.g. screenshots. It also saves the red team time in sifting through many pages of user surveillance data, which would be produced if keylogging/screenwatch was running at all times."
Loj4Shell anniversary: The Log4Shell anniversary will be coming this week, and most likely a new vulnerability too. That's how the month of December works in infosec. A major security disaster before everyone's winter holiday.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




