Risky Biz News: Russia cracks down on foreign web hosting and email providers
In other news: US hosting provider accused of helping APTs; White House publishes national cyber workforce strategy; Minecraft servers hacked using BleedingPipe RCE.
This newsletter is brought to you by GreyNoise. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The Russian government passed last week a series of laws aimed at cracking down on the use of foreign IT services inside Russia and driving citizens to Russian alternatives where it can easily exert pressure through its state apparatus.
Law amendments have been passed to limit the use of foreign web hosting providers, foreign email services, and foreign news aggregators.
In addition, the government also passed a generic law banning Russian citizens from participating in the activities of foreign non-profit organizations, which theoretically criminalizes participation in foreign open-source projects.
The laws come as the Kremlin is rushing to establish a tighter grip on its portion of the internet—which it refers to as RuNet—as its invasion of Ukraine falters, and dissatisfaction and dissent grow internally.
The Russian government is obviously aiming at replicating China's success in managing its internet space by creating its own Great Firewall-like system and having citizens use 100% Russian services where it can keep a watchful eye on anything that may threaten its oligarchic mafioso grip on power structures.
Any foreign web hosting provider that wants to provide services in Russia will have to open local offices and be approved for use by the country's telecommunications watchdog, the Roskomnadzor.
Government agencies and local companies will be prohibited from hosting websites on the infrastructure of web hosting providers that are not included in a Roskomnadzor special register.
The new law has been in the works since 2019 and explains why the Roskomnadzor sent out a public warning to 12 foreign web hosting companies at the end of June to open local offices or risk fines or getting banned. The 12 listed at the time were:
- AWS
- DigitalOcean
- GoDaddy
- HostGator
- DreamHost
- Bluehost
- Hetzner
- WPEngine
- Network Solutions
- Ionos
- FastComet
- Kamatera
The government says the law wants to make sure foreign web hosting providers follow Russian data and privacy protection rules. This includes a KYC-type system and mandatory notification of the Roskomnadzor when companies start providing services to a client. It also includes mandatory cooperation with Russian law enforcement.
Another law amendment also prohibits Russian websites from registering new user accounts using a foreign email address, such as AppleID or Gmail.
Instead, RuNet sites will only be allowed to create new accounts if the user provides a Russian phone number, a Russian email address, any biometric data, or a Gosuslugi account. This enters into effect in December 2023 and will tie Russians to their online identities by removing the option to use foreign privacy and anonymous email providers.
A third law passed last week addresses the Kremlin's ever-growing need to control its online news ecosystem. The law effectively bans foreign news aggregators. It mandates that any news aggregator must be owned by more than 50% by a Russian citizen or organization.
Any kind of foreign ownership is basically frowned upon and will basically force the service to pull out of the Russian market or sell to a Russian organization in some sort of forced legal and state-mandated expropriation. Russian citizens with dual citizenship or Russian organizations that have foreign backers or capital will not be allowed to own more than 20% of a news aggregator. If they own more, they'll most likely have to sell or have content blocked.
Things are getting fun fun fun in Russia.
(h/t Oleg Shakirov)
Breaches, hacks, and security incidents
EraLend crypto-heist: The EraLend lending protocol has been hacked for $3.4 million worth of crypto assets. The exploit was a read-only reentrancy attack, but a different one from the vulnerability that impacted Vyper-based contracts over the weekend. [Additional coverage in CoinDesk]
Hot Topic credential stuffing attack: US retail chain Hot Topic says that its reward points program was targeted by a credential stuffing attack over the course of multiple months. Despite discovering the attack, the company says it's still unable to determine which accounts were accessed by hackers.
Tempur Sealy cybersecurity incident: Mattress maker Tempur Sealy has disclosed a cybersecurity incident that forced it to shut down some of its IT systems. No other details provided, for now.
Poast data leak: Far-right social media site Poast suffered a security breach in May that exposed the email addresses and private DMs of its users. Three months later, researchers have sifted through the leaked data and are starting to link some of the 30,000 Poast profiles to real-world identities. Current reports have found the developer of the rTorrent BitTorrent client, members of the US military, and a bunch of tech bros, including employees from Google, Microsoft, and Apple. Oh, and the owner of a daycare center in Georgia, US.
"The woman's name matches up with a person who was recently involved in a case where she was accused of using Gab to send racist threats to an employee at her husband's work."
Just a bunch of very fine people, I guess!
SolarWinds settlement: A judge has approved a settlement in a class-action lawsuit filed by shareholders in 2021. The company agreed earlier this spring to pay $26 million to shareholders for misleading investors about its 2020 hack. [Additional coverage in Bloomberg]
General tech and privacy
Canon printer warning: Canon is warning customers that WiFi network information stored on some inkjet printer models may not be deleted from its memory during the usual initialization process. The company warns that a specific set of steps must be taken when decommissioning, selling, or sending one of these printers for repairs. More than 200 Canon printer models are affected.
Firefox 116: Mozilla has released Firefox 116. New features and security fixes are included. The biggest change is the ability to copy-paste files from your local system into an upload form. Previously you had to open a popup window and manually select them or drag-and-drop them into the form. Should be easier to upload files online now.
Government, politics, and policy
National Cyber Workforce and Education Strategy: The White House unveiled a document outlining a national strategy to address the US' cybersecurity workforce shortage. Named the National Cyber Workforce and Education Strategy [PDF], the document focuses on four major pillars. These include equipping every American with cyber skills, integrating cyber in educational programs, expanding the national cyber workforce to underrepresented groups, and strengthening federal cyber workforce recruiting programs. As CyberScoop pointed out, the document calls on Congress to enact meaningful reform of immigration programs to help in expanding and retaining foreign-born cyber professionals. Various market studies have estimated the US cybersecurity workforce shortage to range from 300,000 to 800,000 positions.
Section 702 FISA renewal: The White House Intelligence Advisory Board says the FBI should stop using FISA Section 702 surveillance powers meant to track foreign national security threats to investigate internal common crimes. The board recommended that Congress renew FISA Section 702 but add more oversight on how the FBI uses these powers to prevent abuse.
"We agree with the unanimous conclusion reached by this group of independent, deeply experienced experts that failure to reauthorize Section 702 could be 'one of the worst intelligence failures of our time.' We also agree with the Board's recommendation that Section 702 should be reauthorized without new and operationally damaging restrictions on reviewing intelligence lawfully collected by the government and with measures that build on proven reforms to enhance compliance and oversight, among other improvements."
FBI and NSO: The FBI has canceled a contract with one of its contractors after the company signed a deal with Israeli spyware vendor NSO Group days after the Biden administration sanctioned NSO in late 2021. According to the NYT, Riva Networks started using NSO's Landmark to track individuals in Mexico using cellphone data and provide that information to the FBI. The FBI says it told Riva they could no longer use NSO tools, but the contractor never disclosed how it was obtaining the data.
Ethiopia ends social media ban: The Ethiopian government has lifted a social media ban it imposed in February amidst a weeks-long wave of anti-government protests. At the time, access was blocked to sites like Facebook, Instagram, Telegram, TikTok, and YouTube. The ban was lifted after an Ethiopian human rights group reminded the government the ban was still in place five months later. [Additional coverage in Addis Standard]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with GreyNoise founder and CEO Andrew Morris about the company's vast network of honeypots and how they're preparing to take it to the next phase.
Cybercrime and threat intel
Russian wins extradition battle: A Kazakhstan court has ruled to extradite a prominent Russian cybersecurity executive to Russia even if the suspect was detained at the request of US authorities, which also lodged an extradition request before Russian officials. The suspect is Nikita Kislitsin, the top executive for Russian cybersecurity firm FACCT—the former Russian branch of Group-IB. He was detained in June for allegedly selling user accounts from the now-defunct FormSpring social network. Immediately after his arrest, Russian officials also issued an arrest warrant in a mysterious hacking case. Russian officials didn't provide details on their case, but the Russian government has previously used the same tactic to attempt to block the extradition of hackers to the US. This is the second time this tactic worked, but the decision isn't a surprise since it came from a country from the former USSR. [Additional coverage in RBC]
Blade of Picture Poor: Chinese security firm Anheng have covered a campaign of SEO poisoning attacks carried out by a gang they're calling "Blade of Picture Poor" and which has targeted Chinese users. The campaign used malicious ads for popular Chinese software in Google search results that led users to websites hosting malware-laced installers. The gang, which has been active since April 2022, targeted users looking for versions of the WPS office software suite and the Skype and Potato IM apps. Interesting report from a security firm in a country where Google is blocked. (⌒.−) kek
Meow campaign hits Jupyter Notebooks: A unidentified threat actor is accessing misconfigured and internet-exposed Jupyter Network virtualization instances. The attacks are part of a massive data-wiping campaign, with the attacker listing local databases and deleting their data. Cloud security firm AquaSec believes the attacks are related to similar data-wiping attacks dating as far back as 2017 and which have targeted MongoDB, Elasticsearch, Hadoop, and other database systems.
macOS HVNC tool: Security firm Guardz says it has discovered a threat actor advertising a novel HVNC (Hidden Virtual Network Computing) tool targeting macOS systems. It's being advertised for $100,000, which is wild, or a gigantic scam.
Akira gang still active: Threat intelligence company KELA says that even if security researchers released a free decrypter for the Akira ransomware, the gang has continued to operate undisturbed. KELA says the group has continued to extort and list victims on its data leak site, even if they haven't managed to encrypt their files. In July alone, the gang listed 15 new victims on its leak site even if Avast released its decrypter weeks before, at the end of June.
Qilin RaaS: The same KELA researchers have also noted a change in the way the Qilin RaaS works, which has switched to a model where ransom payments are first sent to affiliates instead of them taking their cut. This is a trend with RaaS platforms these days, with several players changing to this model to convince affiliates they won't be scammed out of their earnings—which, tbh, has happened a few times.
Knight RaaS: And in a third item from the same KELA, the company says the Cyclops RaaS has now rebranded as Knight with the launch of v2.0 of its ransomware strain.
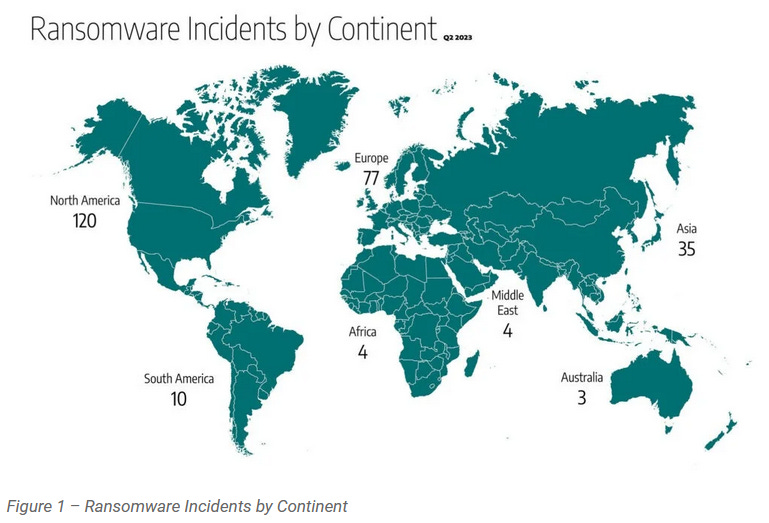
Industrial ransomware stats: ICS security firm Dragos says the number of ransomware attacks that have hit infrastructure and industrial companies has doubled in Q2 2023 compared to the same quarter last year. Almost half (120) of all incidents (253) hit North American organizations.
Malware technical reports
SpyNote: Cleafy researchers look at recent smishing campaigns that have distributed a copy of the SpyNote Android trojan.
"During the months of June and July 2023, we have observed an extensive campaign against multiple European customers of different banks."
P2PInfect: Cado Security has published a report on the new P2PInfect worm that's currently spreading on the internet, targeting Redis database servers. Palo Alto Networks also saw the worm last month.
SocGolish: Panda Zhengzheng researchers have published a report on the SocGolish malware framework.
IcedID: Team Cymru reports that the IcedID malware gang has updated its C&C protocol, known as BackConnect. The updates rolled out in mid-April, with the number of C&C servers going down, and servers being kept online for shorter periods of time.
WikiLoader: Security firm Proofpoint has identified a new malware strain named WikiLoader that is currently being used by multiple threat actors to gain initial access to users' computers. The malware is a sophisticated downloader with advanced evasion techniques that's been active since at least December 2022. Proofpoint suspects access to WikiLoader is sold via a Malware-as-a-Service scheme. Proofpoint says it named this new strain WikiLoader because the malware makes a request to the Wikipedia portal and checks if the response contains the text "The Free" in the reply. This is a clever sandbox evasion technique to check if the malware is being analyzed by a security product in a sandboxed environment with no external internet connection.
NodeStealer 2.0: Palo Alto Networks says it discovered what appears to be a new version of NodeStealer, an infostealer focused on stealing Facebook Business accounts that was initially spotted by Meta last year. The new variants come with cryptocurrency stealing and downloader capabilities.
Bandit Stealer: OALABS has taken a look at a new version of the Bandit Stealer.
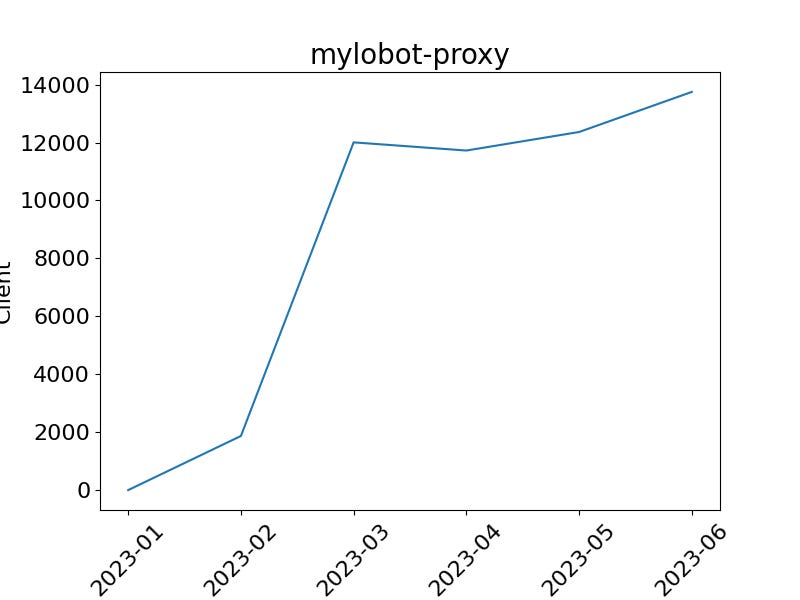
Mylobot: Chinese security firm QiAnXin has a breakdown of the Mylobot Windows malware. According to researchers, the malware's botnet is currently estimated at around 14,000 infected systems, many used as proxies in traffic forwarding schemes.
Sponsor Webinar
In this webinar, GreyNoise's Abigail Whidden explores the powerful combination of Splunk and the GreyNoise platform and how customers can leverage GreyNoise's vast intelligence on internet-wide scans and attack activity to enhance security operations.
APTs and cyber-espionage
Konni: South Korean security firm Genians has published a report on the Konni APT. The report covers a spear-phishing campaign targeting South Korean residents with a tax-themed lure.
JumpCloud incident: ReversingLabs identified a number of additional npm packages with links to the same malicious campaign that North Korean hackers used to breach US cloud provider JumpCloud.
APT31: Kaspersky has a follow-up on APT31's attacks on the industrial sector across Europe. The company published a first report last month on the group's attacks and its MeatBall and FourteenHi malware strains. The malware has data exfiltration capabilities from air-gapped systems using USB drives.
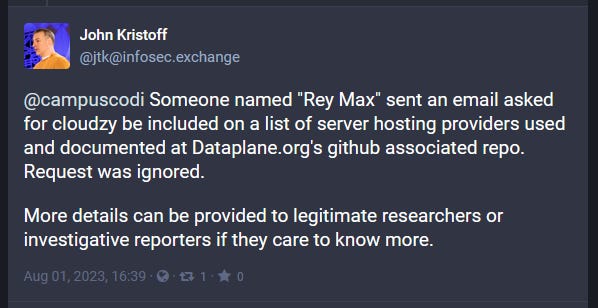
Cloudzy: Security firm Halcyon says that cloud hosting provider Cloudzy is secretly operating as a provider of server infrastructure for APT groups, ransomware gangs, and spyware vendors. The company says it identified more than two dozen different threat actors hosting command-and-control (C&C) servers on Cloudzy infrastructure. APT groups tied to the Chinese, Iranian, North Korean, Russian, Indian, Pakistani, and Vietnamese governments have repeatedly hosted C&C servers on Cloudzy for years. Halcyon says that while Cloudzy is incorporated in the US, the hosting company is "almost certainly" operated out of Tehran, in violation of US sanctions on Iran.
Vulnerabilities, security research, and bug bounty
Collide+Power: A team of academics has discovered a novel side-channel attack that can allow threat actors to infer data from a CPU's shared internal memory just by looking at its power consumption. Dubbed Collide+Power, the attack (CVE-2023-20583) impacts CPUs from all the major vendors, such as AMD, Arm, and Intel. The attack is different and easier to execute in contrast to similar side-channel attacks that target a CPU's power consumption, such as Hertzbleed and Platypus.
"First of all, ordinary users do not have to be worried. The leakage rates of Collide+Power are relatively low with the current state-of-the-art, and it is highly unlikely to be a target of a Collide+Power attack as an end-user."
BleedingPipe vulnerability: Hackers are using a vulnerability named BleedingPipe to take control of modded Minecraft servers, pivot to player devices, and steal Discord and Steam session cookies. The vulnerability impacts Minecraft mods created on the Forge modding software, and the first BleedingPipe attacks were spotted earlier this month. Minecraft community MMPA says at least one threat actor scanned the internet and conducted large-scale exploitation. MMPA devs released a mod named PipeBlocker that can block BleedingPipe attacks.
BeyondTrust vulnerability: Remote access management provider BeyondTrust has quietly fixed a major vulnerability in two of its products that allow unauthenticated attackers to run malicious code on a customer's system. The vulnerability impacts the company's Privileged Remote Access (PRA) and Remote Support (RS) products and received a rare 10/10 CVSS score.
EmpowerID MFA bug: A bug was fixed in the EmpowerID authentication platform that sent MFA codes to unintended email addresses.
Decidim vulnerabilities: GitHub's security team has helped patch a series of vulnerabilities in Decidim, a digital platform for citizen participation. The platform is used by some of the world's largest cities, such as New York, Barcelona, Ciudad de Mexico, Helsinki, as well as many EU bodies.
TruVision pre-auth RCEs: The SSD bug bounty platform is apparently desperately looking for pre-auth RCEs in TruVision CCTV systems for some reason. If anyone knows what this is about, feel free to let us know.
Infosec industry
Cyber insurance study: British think tank RUSI has published a study examining the role of cyber insurance in the ransomware landscape. The report found no evidence that cyber insurance is fueling the ransomware epidemic but found that insurers could do much to discourage ransom payments by their clients. The mammoth 84-page report made nine recommendations for cyber insurers, clients, and the UK government.
"Recommendation 1: To increase oversight of ransomware response, insurers should use policy language to require that insureds and incident response firms provide written evidence of negotiation strategies and outcomes."
New Reddit CISO: Reddit has named Fredrick Lee as its new CISO. He previously served as Gusto's CISO and Square's CSO. [Additional coverage in SecurityWeek]
New tool—Legitify: Legit Security's Legitify tool has reached v1.0. The tool can be used to detect and remediate misconfigurations and security risks across all your GitHub and GitLab assets.
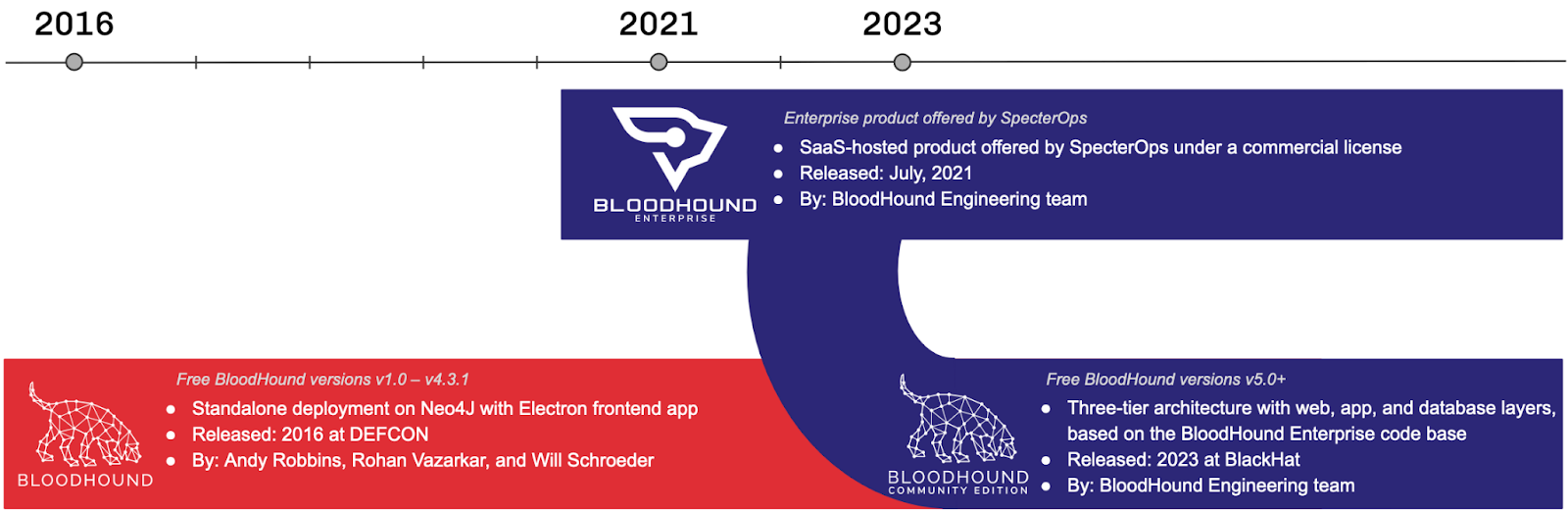
Tool update—BloodHound: SpecterOps has re-launched the community edition of its BloodHound tool, re-written using code from its SaaS enterprise version.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the arguments against intellectual property theft and why there isn't a universal agreement that it should be prohibited.




