Risky Biz News: Russia sentences REvil members to prison. Yes! Really!
In other news: Delta sues CrowdStrike; Chinese telco hack also targeted Trump and Harris campaigns; Satya Nadella asks for a pay cut after cybersecurity failures.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Russian authorities have sentenced four members of the REvil ransomware gang to prison on hacking and money laundering charges.
The sentence was announced last week by a St. Petersburg military court in a case that has taken more than two years to unfold.
Artem Zayets was sentenced to 4.5 years, Alexey Malozemov to five years, Daniil Puzyrevsky to 5.5 years, and Ruslan Khansvyarov to six years in a general regime penal colony.
The four were arrested in January 2022 in a raid that detained 14 suspects. Authorities dropped charges against six and then spent almost two years moving the case back and forward between a criminal and military court.
Russian authorities complained they had sparse evidence after US counterparts ceased all communications after Russia's invasion of Ukraine.
Authorities eventually split the case in two earlier this year in order to send to trial suspects for which they had enough evidence.
The four suspects are believed to have been directly involved in REvil's attack on the Kaseya managed service provider over the July 4 holiday in 2021.
The attack caused massive damage to thousands of companies across the world and triggered a massive response from US officials. US authorities allegedly broke into the group's servers to retrieve decryption keys and started pressuring Russian officials to take action against rogue ransomware groups.
The REvil gang disbanded two weeks after the Kaseya attack, made a quick comeback a few months later, but disbanded again after the US Cyber Command took control over its server infrastructure.
Last week's sentencing marks the first time Russian authorities have sentenced members of a large ransomware operation to prison in a move that surprised many cybersecurity researchers. Members of Russian-speaking cybercrime forums showed the same level of surprise, with some showing their dismay that the suspects weren't "recruited" to hack for Russia in Ukraine.
The case has been challenging for Russian prosecutors because Russian law does not criminalize cyberattacks against foreign businesses. The four were eventually sentenced for creating and distributing malware and money laundering.
Breaches, hacks, and security incidents
China telco hack targeted Trump and Harris phones: US investigators have notified members of the Trump and Harris campaigns that Chinese state-sponsored hackers targeted their phones. The attacks allegedly targeted the phones of former president Donald Trump and vice-president candidate JD Vance. The Wall Street Journal says the attackers are a group known as Salt Typhoon. The group breached telco systems used by the US government for court-authorized network wiretapping requests. Both CISA and the FBI confirmed they were notifying victims but did not reveal any of their names.
Maribor ransomware attack: A ransomware attack has crippled the IT systems of the University of Maribor, the second-largest university in Slovenia. The attack took place last Wednesday and hit the university's official website, email server, WiFi network, and student systems. Recovery has been slow as the attack also hit the university's backup system. Classes have taken place normally at the university's 17 faculties. [h/t Amadej Papež]
Bucharest ransomware attack: A ransomware attack has crippled the IT network of one of Bucharest's six major districts. The RansomHub ransomware gang says it successfully breached and encrypted the IT network of Bucharest's Sector 5 town hall. The group is allegedly demanding $5 million to release a decryption key and delete stolen data. At the end of August, the same group also ransomed Timisoara, another major Romanian city.
US govt crypto-wallet heist: A hacker stole and then returned almost $20 million worth of crypto-assets from a US government crypto-wallet. The funds were stolen last Thursday and returned a day later. The assets represented cryptocurrency the US government recovered from the 2016 Bitfinex hack. The identity of the attacker remains unknown, but cryptocurrency experts said the theft resembled the playbook of a bad actor. [Additional coverage in Decrypt]
Ledger fined over data breaches: France's privacy watchdog has fined crypto-wallet vendor Ledger €750,000 over two security breaches in 2020. Both breaches took place in June, one via Ledger's Shopify store and the second via a misconfigured API. The incidents exposed the details of over 290,000 and over a million customers, respectively. Data from both hacks made its way online and was shared on hacking forums. [Additional coverage in Siecle Digital] [h/t Gabriel Thierry]
Bytedance fires malicious insider: TikTok owner Bytedance has fired an intern after the individual allegedly tried to sabotage the company's AI model. He allegedly exploited a HuggingFace vulnerability to gain access to the model after growing frustrated with the company's allocation of resources. According to an inside report, the intern tampered with the company's large language model for nearly two months before they were caught. Bytedance fired the employee in August and said that rumors that the incident caused millions of dollars in losses were exaggerated. [English coverage in AI News]
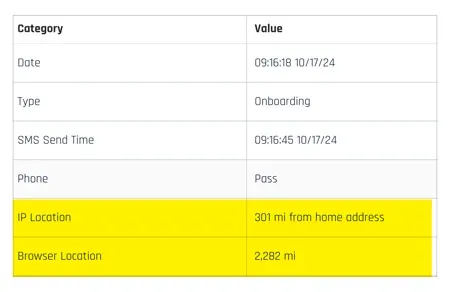
HYPR DPRK worker incident: Cybersecurity firm HYPR says it almost hired a North Korean IT worker for one of its software engineering roles. The company says it discovered the ruse after offering the worker a contract and starting the onboarding process. HYPR says a location check did not match the information the worker provided, who then refused to attend a video call and eventually dropped out of the job. HYPR becomes the second security firm to disclose a similar incident after KnowBe4 in July.
General tech and privacy
Delta sues CrowdStrike: Delta has sued CrowdStrike over a widespread IT outage that caused the airline to cancel over 7,000 flights across the US. Delta is asking for damages to cover over $500 million in losses, claiming the outage reduced revenue by $380 million and incurred $170 million in costs. The airline hired a prominent litigation lawyer at the end of July and started publicly blaming CrowdStrike for the incident. Both CrowdStrike and Microsoft made a common front against the airline. The two said Delta was at fault for its situation after the company ignored their help while the rest of CrowdStrike clients restored systems far faster. [Additional coverage in CNBC]
New Cisco firewall security features: Cisco has added a new security feature to detect and block brute-force and password spray attacks against ASA and FTD firewalls. The feature was made available last week and was specifically designed to protect the device's VPN authentication feature. Threat actors had used a zero-day in this feature for the past months to target and take over Cisco firewalls with weak passwords on the VPN accounts. A patch for the zero-day was also made available last week.
Wireguard Shadowsocks Obfuscation: Mullvad has added Shadowsocks obfuscation for its WireGuard VPN.
Opera's MV2 support to continue: Opera has announced, again, that it plans to continue supporting the old Chromium extensions that were built to run on the old Manifest V2 extension framework. This means the old and incredibly efficient Chrome ad-blockers will continue to work just fine in Opera once Google moves to Manifest V3.
Second Arc browser: The Browser Company, the software firm behind the Arc Browser, says it will build a second and much simpler web browser. [Additional coverage in The Verge]
Telegram finally removes bang lists: Telegram is finally removing channels that share "bang lists" with the personal information and nudes of young Dutch women. Dutch officials publicly complained in April that the company was failing to act on its reports. Telegram's actions come after its founder and CEO was arrested in Paris in August on charges of facilitating crime and CSAM. Shortly after his arrest, Telegram publicly promised to tackle abuse reports on its platform. [h/t M.A.]
Nadella asks for pay cut over cybersecurity failures: Microsoft CEO Satya Nadella has asked the company's board of directors to cut his failure in managing the tech giant's cybersecurity issues. The failures included getting hacked by both Russian and Chinese state-sponsored hackers. Nadella asked the board to withhold $10.6 million in cash compensation. The board approved only a $5.2 million cash payout over the company's "extremely strong performance" last year. In total, the board approved a $79 million salary for Nadella, 63% over his 2023 salary. [Additional coverage in CybersecurityDive]

Government, politics, and policy
Russia's VPN ban: The Russian government ban on VPN services is close to reaching 200 entries, according to Kremlin officials. The count is currently at 197. [Additional coverage in Interfax]
New EU security rules: The EU has passed a set of basic cybersecurity requirements for data centers, cloud providers, domain registrars, and DNS operators. It's the basic stuff like update your gear, use MFA, and so on.
CFPB warns of workspace surveillance: The US Consumer Financial Protection Bureau (CFPB) has warned companies against using invasive surveillance and tracking solutions to track employees. The agency says that employers must obtain consent before tracking workers while at work. Employers must also inform workers how they plan to use the collected data and if and how it will be used for automated systems like AI to evaluate their work. The agency says workers have the right to dispute inaccurate information collected through invasive tracking systems.
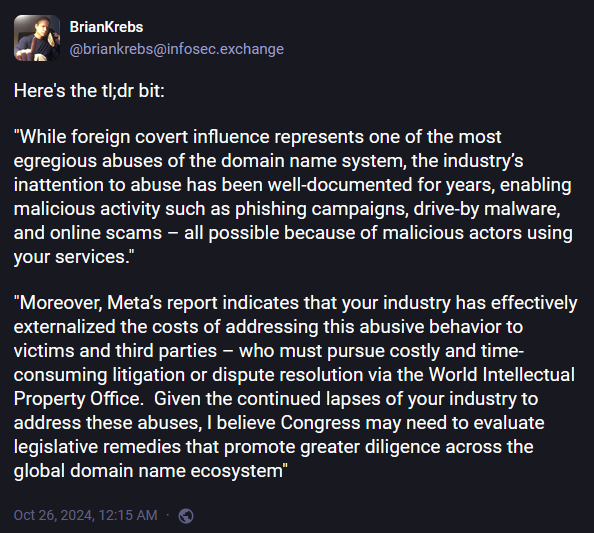
Senator inquires tech firms on foreign propaganda: A leading US senator has asked six US tech companies to investigate how a Russian disinformation group went unnoticed on their services. Senator Mark Warner has sent letters to Cloudflare, GoDaddy, NameCheap, NameSilo, Newfold, and Verisign. The Senator has asked the companies to take steps to address the abuse of their infrastructure by a Russian operation known as Doppelganger. The group had registered and hosted domains at the six companies that mimicked legitimate news outlets. The fake sites spread propaganda and disinformation targeting the US election and the US support for Ukraine. Senator Warner has accused the companies of failing to tackle and profiteering from the abuse taking place on their platforms.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about a new attempt to measure cyber power, the International Institute for Strategic Studies Cyber Power Matrix.
Cybercrime and threat intel
Police hackers detained in Italy: Italian police have arrested four suspects for allegedly hacking three government databases, including one storing police investigation data. One of the detained suspects is Leonardo Maria Del Vecchio, the son of the late billionaire founder of eyewear company Luxottica. Sources have told Reuters that Del Vecchio hired a private intelligence company to gather data for the inheritance lawsuit filed by his family following his father's death. Investigators believe the company accessed the government databases as part of its data-gathering procedures. The other two databases allegedly stored alerts on suspicious financial activities and national tax information. [h/t DataBreaches.net]
New npm malware: Twenty-two malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Pink slime news threat: Intel471 looks "pink slime" journalism, news sites using algorithms to generate politically biased news stories and misinformation surrounding the US presidential election and other topics.
Temu Work Platform: Palo Alto Network has identified a Temu-themed cryptocurrency scam using over 60 domains to lure victims to its platform.
Black Basta moves to Teams social-engineering: The Black Basta ransomware gang is social engineering attacks conducted via Microsoft Teams to compromise company networks. According to ReliaQuest, the group is posing as corporate help desks and contacting employees. The attacks use QR codes and remote management tools to achieve initial access in a corporate environment.
Akira & Fog continue SonicWall rampage: The Akira and Fog ransomware gangs have breached at least 30 companies using a vulnerability in their SonicWall firewalls. Security firm Arctic Wolf says data encryption typically followed on the same day when the firewall was breached. The two groups exploited a vulnerability (CVE-2024-40766) that allowed them to bypass authentication and access firewall management resources. The bug was patched in late August and entered widespread exploitation in early September.
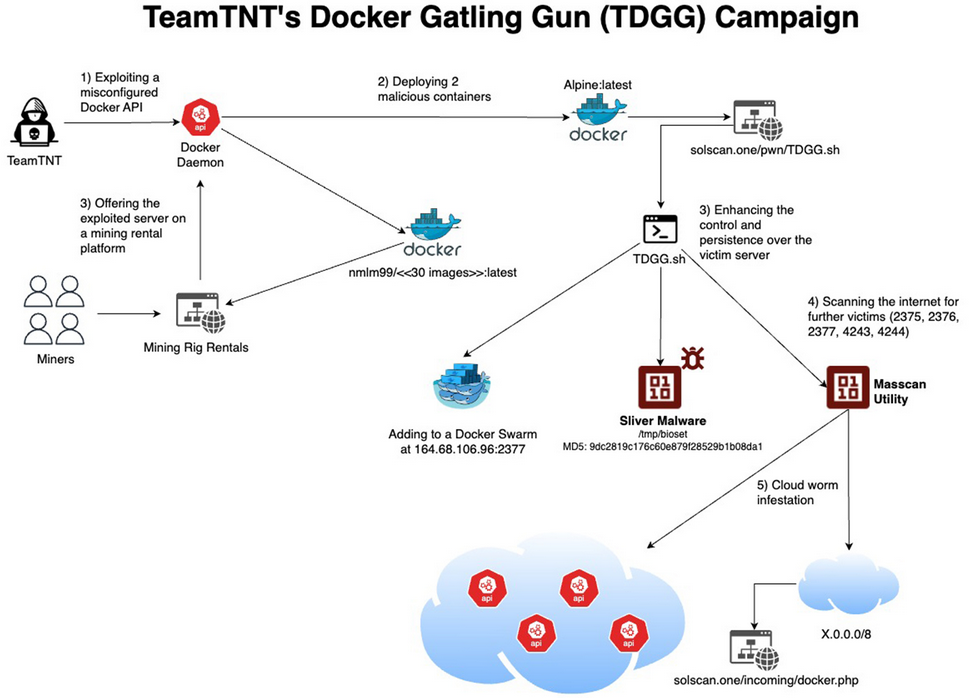
TeamTNT TDGG: AquaSec has published a report on Docker Gatling Gun, a campaign targeting Docker servers from the TeamTNT crypto-mining gang.
Malware technical reports
Sadism ransomware: SonicWall has published a report on Sadism, a ransomware strain from Irani-based Hackersadism group.
Parano Stealer: Symantec warns of a new "run-of-the-mill" Python-based infostealer named Parano Stealer.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
APTs, cyber-espionage, and info-ops
China cyber-reconnaissance in Canada: A Chinese state-sponsored threat actor is conducting large-scale reconnaissance operations in Canada. The country's cybersecurity agency says it detected reconnaissance scans throughout 2024. Most scans targeted the infrastructure of government agencies and political parties. To a lesser degree, scans also targeted critical infrastructure, think tanks, NGOs, media organizations, and the defense sector. The agency did not report any breaches and advised organizations to implement MFA and deploy logging capabilities.
Kimsuky: AhnLab has published a report on Kimsuky operations leveraging the PebbleDash and RDP Wrapper malware strains.
Operation Cobalt Whisper: Seqrite researchers are tracking a new APT targeting the defense sector in Pakistan and various Hong Kong researchers.
APT28 (UAC-0001): Hackers linked to the Russian military have adopted a technique that recently became popular with cybercrime groups. The technique is known as ClickFix and relies on tricking users into copying-pasting malicious commands in a Windows terminal. Ukraine's CERT says Russian group APT28 used the technique in a massive phishing attack targeting Ukrainian government agencies. Emails led victims to a web page with a fake CAPTCHA that hijacked their clipboards. Users were then told to open a PowerShell console and paste and run the malicious code secretly added to the clipboard.
Michigan misinformation campaigns: The Open Measures research team has published a report on election misinformation campaigns targeting Michigan, a critical US swing state in the upcoming presidential election.
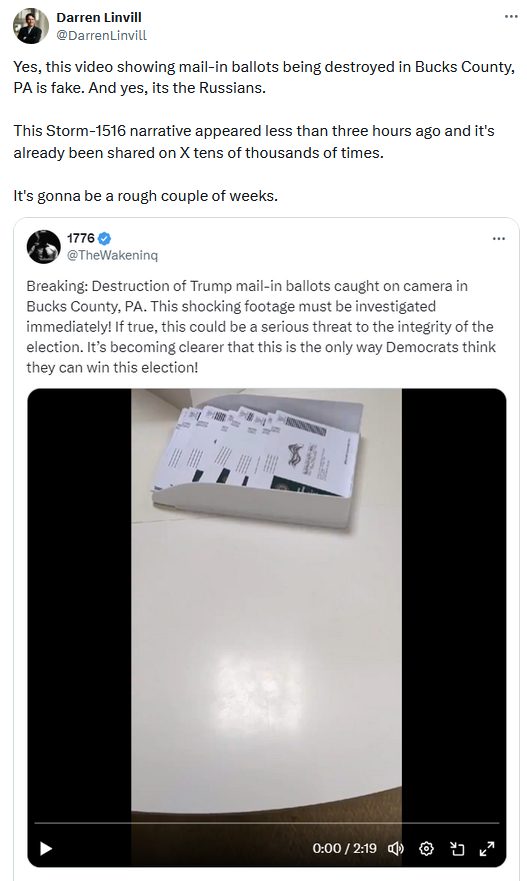
Pennsylvania misinformation campaign: US government officials say that a Russian disinformation group is behind a fake viral video that was shared on Twitter showing a Pennsylvania man destroying Trump mail-in ballots. Officials say the video is part of Russia's attempts to meddle in the upcoming US election.
Vulnerabilities, security research, and bug bounty
CLFS EoP mystery: Details and proof-of-concept code have been made public for an elevation of privilege vulnerability in the Windows 11 Common Log File System (CLFS) driver. The vulnerability was discovered and used by a security researcher at the TyphoonPWN 2024 hacking contest. The researcher won first place, but there is some drama surrounding the vulnerability. Microsoft said the issue was a duplicate of a bug it had already fixed, but didn't provide a CVE identifier to the researcher.
Windows Downdate attack: SafeBreach researchers have published a bypass for Microsoft's patch of the Windows Downdate downgrade attack.
AMD SMM write-up: IOActive has published a technical write-up on CVE-2023-20596, a vulnerability the company found in the AMD SMM Supervisor last year. The issue was patched last November.
Linux EoP analysis: Security researcher Maher Azzouzi has published an analysis of CVE-2024-26926, a somewhat unexploitable elevation of privilege in the Linux Binder service.
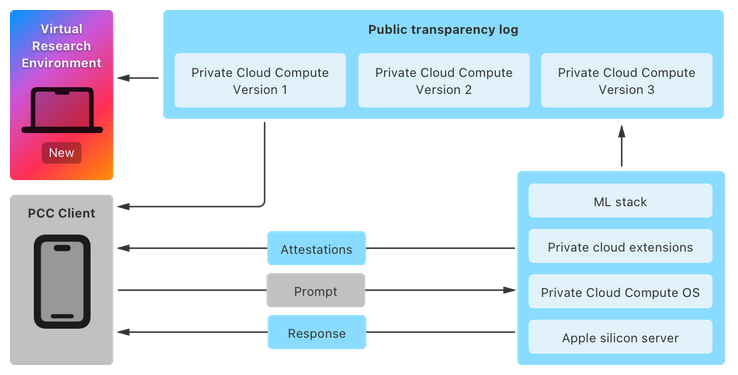
Apple VRE available: Apple has made a Virtual Research Environment (VRE) for its Private Cloud Compute VM available to security researchers. The company has also released source code for some PCC components to help researchers analyze the feature's privacy and safety levels. PCC is a new Apple feature that will take user data and process it inside an ephemeral encrypted cloud server. The feature is designed to support Apple's new AI services that require more processing power than is available on the user's device. Apple says it will pay up to $1 million for remote attacks against PCC servers.
Infosec industry
Acquisition news: Identity fraud detection company Socure has acquired fraud prevention platform Effectiv for $136 million.
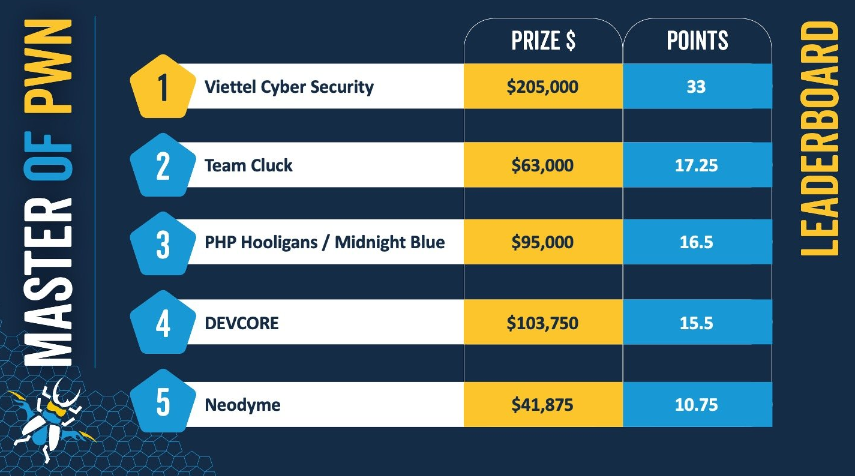
Pwn2Own Ireland results: Results from the three days of the Pwn2Own Ireland hacking contest are now up. The contest focused on smartphones, messengers, and IoT solutions. In somewhat of a rare event, QNAP published a statement thanking researchers for hacking its products. [Day 1, Day 2, Day 3, and Day 4]
New tool—NIFO: Security researcher Lars Karlslund has released NIFO (Nuke It From Orbit), a tool to remove AV and EDR software on systems where users have physical access.
Threat/trend reports: Arctic Wolf, AuditBoard, ENISA, HYPR, Red Canary, Sysdig, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats.
No Hat 2024 videos: Talks from the No Hat 2024 security conference, which took place last week, are now available on YouTube.
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about the evolving relationship between Russian intelligence services and the country’' cybercriminals. The GRU's sabotage unit, for example, has been recruiting crooks to build a destructive cyber capability. Tom suspects that GRU thugs are not so good at hands-on-keyboard operations but excellent at coercing weedy cybercriminals to hack for the state.




