Risky Biz News: Russia preparing new Vepr surveillance system
In other news: Coinbase's fast reaction avoids major breach; 0ktapus hacks Activision; Samsung announces new Message Guard security feature.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The Russian government plans to roll out a new internet surveillance system in the second half of the year.
Named Vepr (Вепрь, the Russian word for "boar"), the system is allegedly capable of detecting "points of tension" and "threats to the individual, society, and the state" on the public internet.
According to TASS, the system is being built by Neobit, a Sankt Petersburg software company that was sanctioned by the US Treasury in April 2021 for developing cyber tools for Russia's intelligence and military services.
Work on Vepr began last year in the aftermath of Russia's invasion of Ukraine, and the system appears to have been designed to allow the Russian government to track potential dissent or mis/disinformation efforts on Russia's internet space.
Officials told Vedomosti the system is not designed to remove information from the internet but to allow to monitor and predict potential "points of tension."
Vepr is currently undergoing tests at the Main Radio Frequency Center (GRFC), a subdivision of the Roskomnadzor, Russia's communications watchdog.
Since Russia's invasion of Ukraine, the Kremlin has ramped up its national surveillance capabilities in attempts to prevent dissent from its own population.
For example, last week, the Russian Duma also started working on a project that would fine telcos that fail to properly implement SORM—special equipment installed in a telco's backend network that logs internet and telephony traffic and allows Russian law enforcement and intelligence services to search through the data.
Earlier this month, Russia also launched Oculus, a system that scans the internet and detects banned content, either in text or image format.
Last year, Russia began work on a system that aggregates CCTV video streams from all over the country at a new data center near Moscow.
Breaches and hacks
Coinbase phishing incident: Cryptocurrency trading platform Coinbase disclosed that earlier this month, on February 5, one of its employees fell victim to a phishing attack and allowed a threat actor to collect their Coinbase login credentials. The company says that MFA protections prevented the attacker from silently logging into the employee's account. Nevertheless, the attacker was able to gain access to some Coinbase systems after calling the phished employee and posing as one of the company's IT support staff. Coinbase avoided a larger breach because its security team spotted the unusual activity on the phished employee's account and contacted them while they were still on the phone with the attacker. While it couldn't be sure, Conibase says it believes the threat actor behind this attack is a group known under the names of 0ktapus and Scatter Swine.
"Fortunately no funds were taken and no customer information was accessed or viewed, but some limited contact information for our employees was taken, specifically employee names, email addresses, and some phone numbers. "
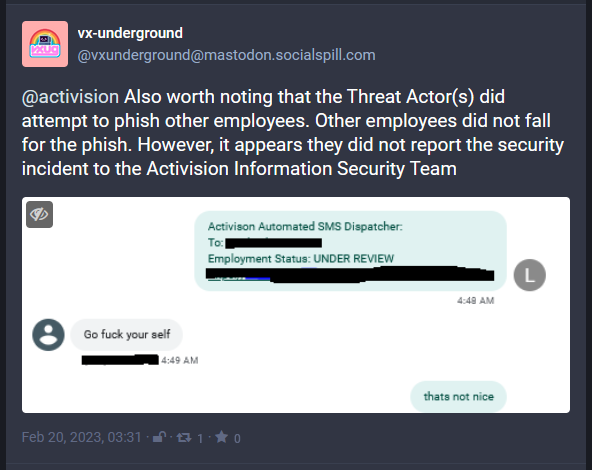
Activision breach: Activision, the game publisher behind the Call of Duty franchise, has confirmed a security breach that took place in early December 2022 after a hacker gained access to one of its internal Slack channels. Activision didn't reveal the incident on its own, but only after it was pressed by reporters after infosec threat intel-sharing group VX-Underground published redacted screenshots they received from the attacker. The intruder told VX-Underground that they gained access to Activision's Slack channel after phishing a "privileged user." The attacker stole internal documents related to the Call of Duty franchise and the content scheduled to be released throughout 2023. Activision says no employee or user data was stolen, nor any of the game's source code. VX-Underground says the attacker also tried to phish other Activision employees, but the attempt failed. [More context on the stolen files via GamesRadar]
RailYatri leak: The personal details of more than 31 million Indians is currently on sale on an underground hacking forum. The seller claims the data belongs to RailYatri, a ticket-booking app used by India's national railway. A government official told the Hindustan Times they are currently investigating the incident.
Virgin Media incident: Virgin Media Television broadcasts were impacted across Ireland after the company discovered an "unauthorised attempt to access [their] systems." According to Ireland's national television RTE, as a result of the attack, Virgin Media aired recorded programming on several channels on Monday, such as Virgin Media 3, 4, More, and VMTV Player.
DOD leak: The US Department of Defense has leaked sensitive emails after it left one of its Azure servers exposed on the internet without a password. According to TechCrunch, the server hosted internal mailboxes for US Special Operations Command, or USSOCOM, the US military unit tasked with conducting special military operations. Some of the emails exposed in the incident also contained SF-86 questionnaires used by DOD employees to apply for security clearances.
General tech and privacy
Google Chrome Memory and Energy Saver: After becoming the butt of internet jokes about its resource-hungry browser, Google has finally had enough and is adding Memory Saver and Energy Saver to Chrome, two features that will improve Chrome's RAM and battery usage. Both features are currently being rolled out to Chrome 110 for desktops. See here for instructions on how to turn them on.
Linux on M1: Linux 6.2 is out and the first version to support Apple's M1 chips. This comes after three years of work.
Outlook spam: Microsoft has confirmed that the increased spam users got in their Outlook inboxes earlier this week was the result of some malfunctioning email filters.
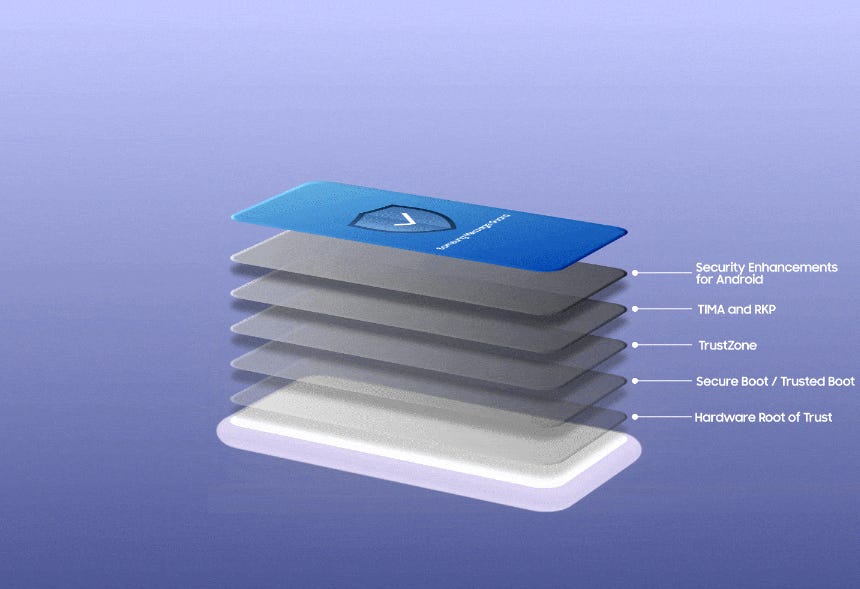
Android firmware hardening: Google has announced plans to harden the security of Android devices at the firmware level. The plan is to port some of the security features added to the Android OS over the past years to the third-party firmware components that are bundled together with the Android OS on modern smartphones. This includes firmware that powers smartphone features like WiFi, GPUs, secure CPUs, and others. Google says it’s already working with several ecosystem partners to add features like compiler-based sanitizers, exploit mitigations, and memory safety features to firmware packages. Google says it's taking these steps after it saw attackers moving away from targeting the Android OS itself to going after third-party components and their firmware.
Samsung Message Guard: South Korean phone maker Samsung has announced a new security feature for its line of Galaxy smartphones. Named Samsung Message Guard, this new technology isolates messaging apps inside their own sandbox, where incoming messages are executed and checked for exploits before the content is shown to the user. Samsung says it created this technology after seeing a rise in zero-click exploits delivered via messaging applications. Message Guard works inside messaging apps like Samsung Messages and Messages by Google and only on Samsung Galaxy S23 devices. Samsung plans to gradually roll it out to other Galaxy smartphones and tablets later this year.
Government, politics, and policy
UK to review Computer Misuse Act: The UK government is asking for public feedback on three changes it plans to make to the Computer Misuse Act, the UK's cybercrime law. Initially passed in 1990, the UK government announced last year plans to revamp some of the CMA provisions in light of recent technological advanced. The three proposals would grant UK law enforcement agencies the power to (1) seize domains and IP addresses used for malicious activity, (2) require companies to preserve computer data until law enforcement agencies can determine if it's evidence in an investigation, and (3) allow law enforcement agencies to go after individuals for "possessing or using" hacked data.
Supreme Court declines to hear Wikimedia NSA case: The US Supreme Court has declined to hear a petition filed by the Wikimedia Foundation—Wikipedia's parent entity—that challenged the NSA's warrantless interception and mass surveillance capabilities. The petition, filed together with the ACLU and the Knight Institute, asked the Supreme Court to force the program to go under constitutional and judicial review in the courts. Wikimedia filed the petition last fall after losing in lower courts, where the NSA argued that the review process would expose "state secrets."
Call to ban spyware across the EU: The European Digital Rights (EDRi) civil rights group has asked the EU's PEGA committee to push for an EU-wide ban on spyware and surveillance software.
Sponsor section
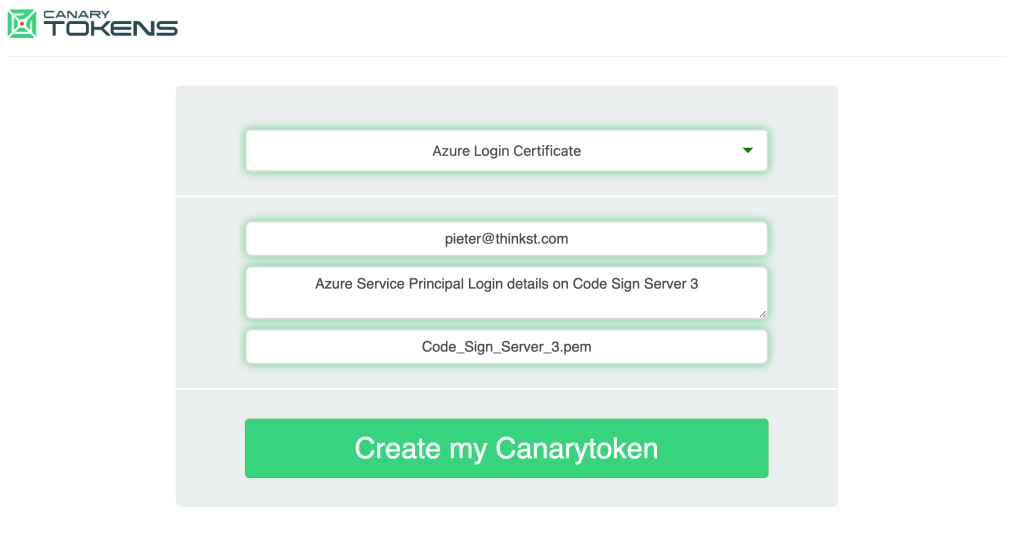
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company has recently launched a new type of canary token that looks like an Azure login token and warns companies whenever a threat actor tries to use them.
Cybercrime and threat intel
Hackers detained in South Korea: South Korean police have detained 12 individuals part of a cybercrime crew that hacked into 385 websites and stole the personal data of 7 million users. The group is believed to have breached a South Korean dating company, a major news outlet, and a plastic surgery clinic, among many others. Officials say the group ran a hacker-for-hire service, advertising their services for fees ranging from $800 to $4,000 on various social media platforms. They also offered DDoS-for-hire services as well.
Loyalist thefts: A threat actor tracked as Loyalist (Lukas or Shibango) has stolen more than $4 million worth of cryptocurrency and NFTs throughout 2022 and 2023. According to blockchain investigator ZachXBT, the attacker mostly relied on phishing sites promoted on Twitter. More than 400 victims have been identified so far.
Azure DDoS attacks report: In its yearly DDoS report, Microsoft says its Azure cloud service mitigated an average of 1,435 attacks per day throughout 2022, with attacks peaking at 2,215 separate incidents on September 22, 2022. Microsoft says the largest attack took place in May of last year when one of its clients was hit by a 3.25 terabits per second (TBps) flood. While several networking protocols and servers can be abused for large-scale DDoS vectors, Microsoft says that TCP-based attacks remained the top preferred attack method, such as TCP SYN, TCP ACK, and TCP floods. Overall, while some attacks can be quite large, shorter DDoS attacks continue to be more popular and just as offensive.
Anonymous Sudan linked to Russia: Cybersecurity firm TrueSec says the Russian government is most likely behind a new incarnation of the Anonymous Sudan hacktivist movement. Since the end of January this year, the group has launched DDoS attacks against Swedish targets in retaliation to a far-right group burning the Quran. TrueSec says this new version of the group has no connections to the original Anonymous Sudan collective, is only active on Telegram, its operations are amplified by Russian groups, and only interacts with Russian actors. TrueSec calls the new Anonymous Sudan an influence operation trying to sabotage Sweden's bid to join NATO. Its report comes after the Guardian also discovered that the burning of the Quran in front of Turkey's embassy in Sweden was organized by far-right journalists with links to Russian media.
Malware technical reports
PoshC2: SecurityScorecard's Vlad Pasca has a deep dive into the PoshC2 red-team tool, abused in some recent malware campaigns.
Royal ransomware: The Royal ransomware now has a Linux variant capable of encrypting ESXi systems. Royal joins a long list of ransomware strains that have rolled out Linux/ESXi variants, such as Darkside, BlackMatter, REvil, Hive, LockBit, HelloKitty, Black Basta, AvosLocker, RansomExx, RedAlert, Cheers, Nevada, GwinsinLocker, Luna, and more.
HardBit ransomware: Varonis researchers have a report out on HardBit 2.0, a new version of the Hardbit ransomware. Varonis says the HardBit ransomware was first spotted in the wild in October 2022, and v2 was seen a month later, in November 2022, in attacks targeting companies with double extortion (encryption and leak) tactics.
"Notably, as part of these negotiations, victims with cyber insurance policies are also encouraged to share details with HardBit so that their demands can be adjusted to fall within the policy."
Andoryu botnet: Chinese security firm QiAnXin has discovered a new botnet named Andoryu. Researchers say the botnet was assembled using compromised GitLab servers and Lilin DVRs. The botnet is currently used to launch DDoS attacks.
Rhadamanthys: Zscaler has a report out on the new Rhadamanthys stealer, which is slowly becoming very popular among malware crews.
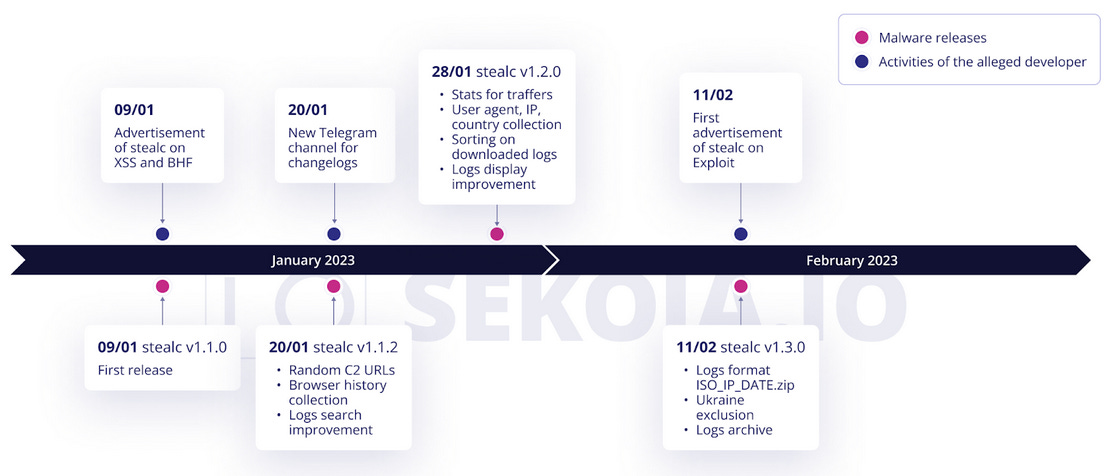
Stealc: Sekoia says it identified a new infostealer strain named Stealc. Researchers say they spotted ads for this new malware on underground forums in January 2023 and spotted the first samples in the wild earlier this month. The company says it's currently tracking more than 40 Stealc command and control servers in the wild.
APTs and cyber-espionage
UAC-0050 and UAC-0096: CERT-Ukraine has put out an alert about a new spear-phishing campaign targeting Ukrainian organizations with the Remcos RAT. Officials linked the campaign to the UAC-0050 and UAC-0096 threat actors.
SideCopy: A report we missed last week is ThreatMon's coverage of recent SideCopy APT attacks targeting Indian government entities using the new ReverseRAT.
Russia’s Viasat attack: Sekoia has published an overview of Russia's cyber operations in Ukraine last year and the company believes it has found how the Sandworm APT has taken control of Viasat modems last year, before wiping their firmware—namely, via SSH!
Our analysis showed that the firmware was entirely wiped by the same algorithm as the one present inside the AcidRain wiper (cf. FLINT 2022-015). Moreover, by diffing two firmware versions (pre- and post-attack) our analysis showed that the vector of this compromise was likely SSH as every SurfBeam2 modems has SSH enabled on SDWAN network, and the new firmware versions has almost no changes, except for the SSH public key of the root user.
Vulnerabilities and bug bounty
iOS/macOS bug class: Trellix researchers have discovered a new bug class that impacts both iOS and macOS that can bypass code-signing requirements and allow malware to elevate privileges and escape sandboxed environments. The vulnerability resides in iOS and macOS services that accept arguments via NSPredicate, a class that allows developers to filter lists of arbitrary objects. Trellix says some arguments were not properly filtered and could be used to run malicious code. Apple has addressed the reported issues in macOS 13.2 and iOS 16.3.
CVE-2022-27925 (Zimbra): BishopFox researchers have a write-up on CVE-2022-27925, a vulnerability they found in the Zimbra app that could be abused for unauth remote code execution.
Graphana vulnerability exposure: Vulnerability management platform VulnCheck says that more than 7,500 (or 8% of) Grafana instances indexed by Shodan remain vulnerable to a vulnerability disclosed in December 2021. Tracked as CVE-2021-43798, the vulnerability was a zero-day for a short time before Grafana released an update and before the Log4Shell hysteria reprioritized security teams' remediation efforts.
Infosec industry
New job: CrowdStrike is hiring a new CISO. 20+ years of experience and a degree in information assurance, cybersecurity, information technology, or a related field are some of the basic requirements.
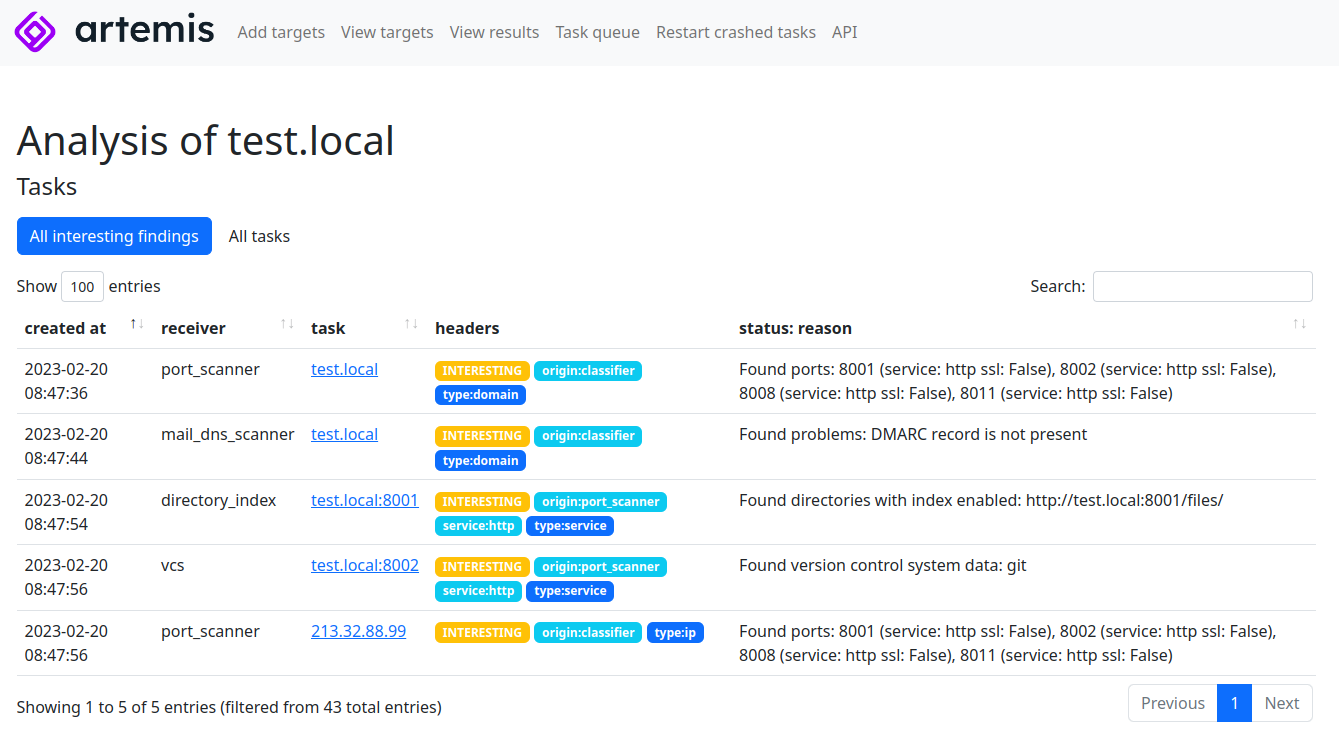
New tool—Artemis: CERT-PL has open-sourced Artemis, a modular web reconnaissance tool and vulnerability scanner.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




