Risky Biz News returns! The catch-up edition :(
In other news: APT29 hacks TeamViewer; Indonesia crippled by ransomware attack; Google yeets Entrust certificates.

This newsletter is brought to you by Rad Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The Risky Business News team has been on a break for the past two weeks, and as such, we're a little bit behind.
Below are the major headlines from the past week as we play catch-up with the infosec news cycle. We'll see you back on Wednesday with our usual super-detailed coverage of the infosec field!
Breaches, hacks, and security incidents
TeamViewer hacked: TeamViewer says Russian hackers have breached its internal network in a security breach last week. The company says the hackers obtained an employee's credentials and accessed its corporate network on Wednesday, June 26. TeamViewer says there is no evidence that the hackers accessed customer data or its main product environment. The company has attributed the hack to APT29 (Midnight Blizzard), a cyber-espionage unit inside Russia's SVR intelligence agency.
Microsoft hack update: Microsoft is notifying additional customers that had data stolen by Russian hackers (Midnight Blizzard) in a breach at the end of last year. [Additional coverage in Reuters]
CISA confirms breach: CISA confirmed last week that hackers breached its Chemical Security Assessment Tool in January this year. CISA says the breach took place after hackers exploited a vulnerability in an Ivanti ConnectSecure appliance. CSAT is an online portal where organizations from the US chemical sector file surveys and security assessments with CISA and the federal government.
US Federal Reserve non-breach: American private bank Evolve has disclosed a security breach after some of its data was posted on a ransomware leak site last week. The bank's data was published on the Lockbit gang's leak site. The ransomware gang initially advertised the data last year as belonging to the US Federal Reserve. Evolve is now notifying all affected customers. The bank's services are used by many of today's most popular fintech startups and lending services. [Additional coverage in TechCrunch]
HubSpot breach: Online marketing company HubSpot has disclosed a security breach that impacted around 50 of the company's customer accounts. The breach took place on June 22, and HubSpot says that by June 28, it secured all affected accounts. The company did not disclose the nature of the incident.
ANY.RUN breach: Security firm ANY.RUN says one of its employees fell victim to a spear-phishing attack. The company says the spear-phishing email came from the email of one of its customers, which was compromised as part of a larger campaign that targeted popular companies. ANY.RUN says the attacker didn't pivot to its internal network and only used its employee's account to phishing other victims.
Polyfill supply chain attack: A Chinese company has taken over the domain of a popular JavaScript library named Polyfill and used the CDN-hosted version to insert malicious code on millions of websites. According to security firm SanSec, the code redirected a site's regular visitors to sports betting websites. Despite being caught by multiple security firms hijacking legitimate traffic, the Chinese company denied any wrongdoing and claimed it was being defamed. Google, Fastly, Cloudflare, and several ad-blockers have since intervened to warn website owners about the library's new owners and replace Polyfill links with clean versions of the library.
Conceptworld supply chain attack: A threat actor has compromised the website of Indian software company Conceptworld and added an infostealer to all of its apps. The incident compromised installers for apps like Notezilla, RecentX, and Copywhiz. According to security firm Rapid7, the compromise appears to have taken place in early June and used a malware strain known as dllFake.

GUR hacks in Crimea: Ukraine's GUR military intelligence has launched a series of cyber operations that disrupted IT services across the Russian-occupied territory of Crimea. DDoS attacks targeted local ISPs, Russian propaganda sites, and the traffic control systems on the Kerch Bridge. The attacks took down internet connectivity and restricted car traffic on the Kerch Bridge. GUR also says it worked with an independent hacker group named BO_Team to attack Russian companies supporting the Kremlin's war in Ukraine. This included hack-and-leak attacks against Russian military equipment suppliers and DDoS attacks on Russian telcos.
MedvedevLeaks: Pro-Ukrainian hacktivist group Cyber Resistance claims to have hacked one of the six assistants for Dmitry Medvedev, the deputy chairman of Russia's Security Council. The group claims it hacked the assistant's inbox at the start of the year and quietly intercepted emails for more than six months. [Additional coverage in InfoNapalm]
ISP malware implants: South Korean telecom company KT has infected more than 600,000 users with malware. The infections took place since May 2020 and exclusively targeted the users of Webhard, a local cloud service provider. The malware created random folders with junk data, deleted files, and sometimes even disabled PCs. KT targeted Webhard users in an attempt to sabotage the company's BitTorrent file-sharing service. The telco argued the Webhard file-sharing service was generating large quantities of traffic on its internal network. It even won a lawsuit that found Webhard responsible but continued with its malware scheme. South Korean authorities have charged 13 KT employees in connection to the malware last month. [Additional coverage in JTBC/ English coverage in Tom's Hardware]
BtcTurk crypto-heist: A threat actor has stolen $55 million worth of crypto assets from BtcTurk, one of Turkiye's largest cryptocurrency exchanges. The attack took place on June 22, and the attacker stole funds from hot wallets holding 10 different cryptocurrencies. The incident is the year's second-largest crypto-heist.
CDK Global ransomware attack: A ransomware attack on software vendor CDK Global has crippled the activity of thousands of car dealerships across the US. Pat and Adam covered the attack in more depth in last week's RiskyBusiness podcast, so I'm not going to go over the fine details over here, but there's also a good report about it on CBS.
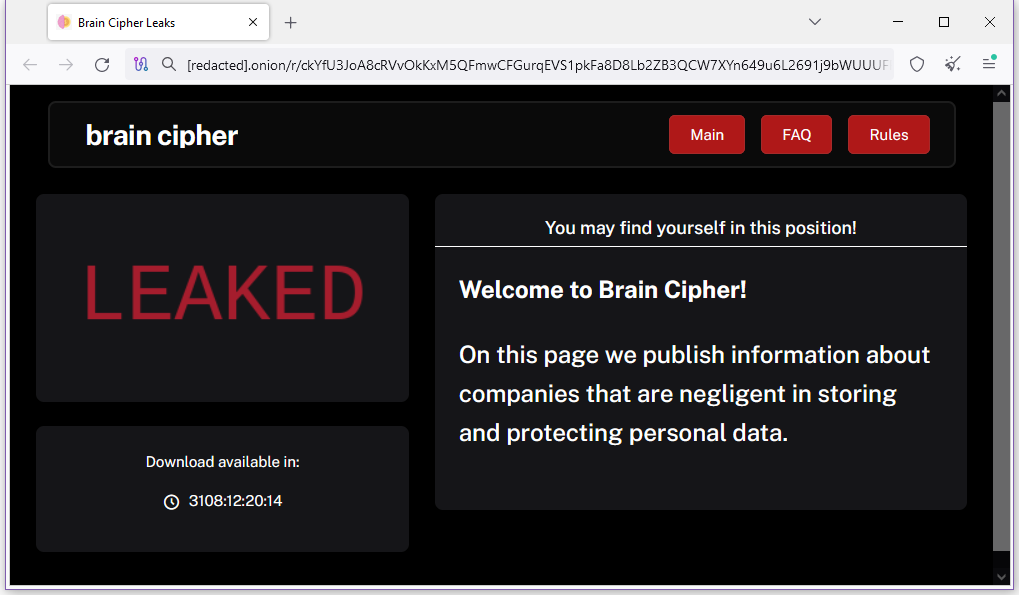
PDN ransomware attack: A major ransomware attack has crippled the activity of more than 280 Indonesian public agencies over the past week. The incident took place on June 20 and hit the government's national data center (PDN). The attack has caused delays in airport immigration services and new student registrations. The incident has been linked to a new ransomware strain named Brain Cipher, a version built on the leaked LockBit ransomware source code. The Indonesian government is working on moving some of its databases to AWS but says the bulk of the encrypted data is most likely lost since it was not backed up. Officials have declined to pay a $8 million ransom to get their data back. [Additional coverage in the Jakarta Globe and itNews Asia]
General tech and privacy
Google distrusts Entrust: Google is removing Entrust certificates from the Chrome browser's certificate root store. The ban will apply to any new certificate issued by Entrust after October 31 this year. Chrome will continue to trust older Entrust certificates, and websites using them will work as before. Google says Entrust has failed to report multiple incidents over the past years. Other major browser vendors, such as Apple, Microsoft, and Mozilla, have not yet announced a similar ban.
Windows 10 EOL: ACROS says its 0Patch micro-patching service will support Windows 10 unofficial security updates after the OS reaches end-of-life in October 2025.
Another Windows 11 scandal: Microsoft is forcibly syncing the files of Windows 11 users to its OneDrive service without asking permission beforehand. [Additional coverage in PCWorld]
And another Windows 11 scandal: And since Microsoft insists on enshittifying Windows 11, we now also know that the new Windows 11 Outlook client proxies all your email data through Microsoft servers, including login operations. Beautiful! Truly beautiful!
The disappearing internet: As cloud hosting prices continue to explode, there are multiple reports that companies are now quietly ditching old content and archives as a way to cut costs. See recent reports about Paramount and several Chinese companies.
New Google Translate languages: If the Google Translate dropdown interface looks weird, it's because Google added a whopping 110 new languages to the service. Most are local dialects such as Sicilian, Marwadi, Crimean Tatar, or Mauritian Creole.
Government, politics, and policy
Poland's spyware inquiry: The Polish Parliament has stripped legal immunity from an opposition MP in connection to the country's investigation into Pegasus spyware abuses. Michał Woś stands to face a legal inquiry for authorizing the purchase of the Pegasus spyware during his time at the Polish Ministry of Justice. Woś is a member of the Law and Order Party (PiS) and was deputy minister during the country's previous government. [Additional coverage in Notes from Poland]
US privacy bill: The American Privacy Rights Act looks dead and buried after House Republicans had a fit at the concept of having civil rights protections in a—checks notes—privacy law. [Additional coverage in Wired]
Ransomware payments ban: While in the UK last week, CISA director Jen Easterly has dismissed the idea of a blanket ransomware payments ban coming any time soon. [Additional coverage in The Record]
Kaspersky ban: Russian security firm Kaspersky says the recent US government ban won't significantly affect its operations since its US business only accounts for "just under 10% of the company's total revenue," according to a report from Kim Zetter.
Slack leaves Russia for good: Slack is cutting off services to all Russian users in compliance with the latest expanded US sanctions. The company previously disabled some services to some Russian companies in March 2022. [Additional coverage in RBC]
EU sanctions Russian hackers: The European Council has added six Russian nationals to its sanctions list for their role in launching cyberattacks against Ukraine and EU member states. The six include two members of the Calisto APT group, two members of the Armageddon APT group, and two individuals involved in the Conti and TrickBot malware operations. The EU has previously sanctioned multiple members of Russian, Chinese, and North Korean APT groups. This marks the first time the EU has sanctioned members of a cybercrime operation.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Jimmy Mesta, CTO and Co-Founder of Rad Security (formerly KSOC). Jimmy explains how Rad Security has replaced signature-based detections with a new concept the company calls "behavioral fingerprints" or "verified runtime fingerprints," which can detect malicious activity in cloud environments using a wider set of indicators.

Cybercrime and threat intel
Evil twin hacker detained: Australian police have arrested a 42-year-old man for allegedly setting up fake WiFi networks to steal personal data. Officials say the suspect set up fake free WiFi access points at the Perth, Melbourne, and Adelaide airports. He also set up fake networks during domestic flights and at locations linked to his previous employment. The Australian Federal Police says the man used evil twin attacks to redirect users of his fake WiFi network to phishing pages and capture credentials.
FIN9 members detained: Something a little bit older—the US charged four Vietnamese men for their role in the FIN9 cybercrime group.
Bulgarian hacker detained: Bulgarian officials have arrested and charged a man named Teodor Iliev with several computer crimes. According to a report from DataBreaches.net, the man is believed to be behind the Magadans and Emil Külev hacker personas, active on several underground hacking forums. Iliev is accused of hacking multiple Bulgarian companies and state institutions over the past five years. He is also a known associate of the RansomedVC extortion group.
Indonesian raids: Indonesian authorities have arrested over 100 foreigners suspected of their involvement in a cybercrime syndicate. The suspects were detained following raids at villas across the island of Bali. Officials say most of the 103 detained suspects hold Taiwanese passports. According to The Record, it's unclear if the suspects were running the cybercrime schemes or if they were forced to commit cyber scams against their will.
Operation First Light 2024: Interpol says it detained almost 4,000 suspects as part of an operation against online scam syndicates. Officials say the suspects were involved in phishing, investment fraud, fake online shopping sites, and romance scams. Interpol says it seized bank accounts, real estate, and other assets worth over $257 million.

Unfurling Hemlock: Outpost24 has published a report on Unfurling Hemlock, an Eastern European cybercrime group behind a strange malware delivery campaign where victims are infected with more than 10 malware strains at a time—in what the company calls malware cluster bombs.
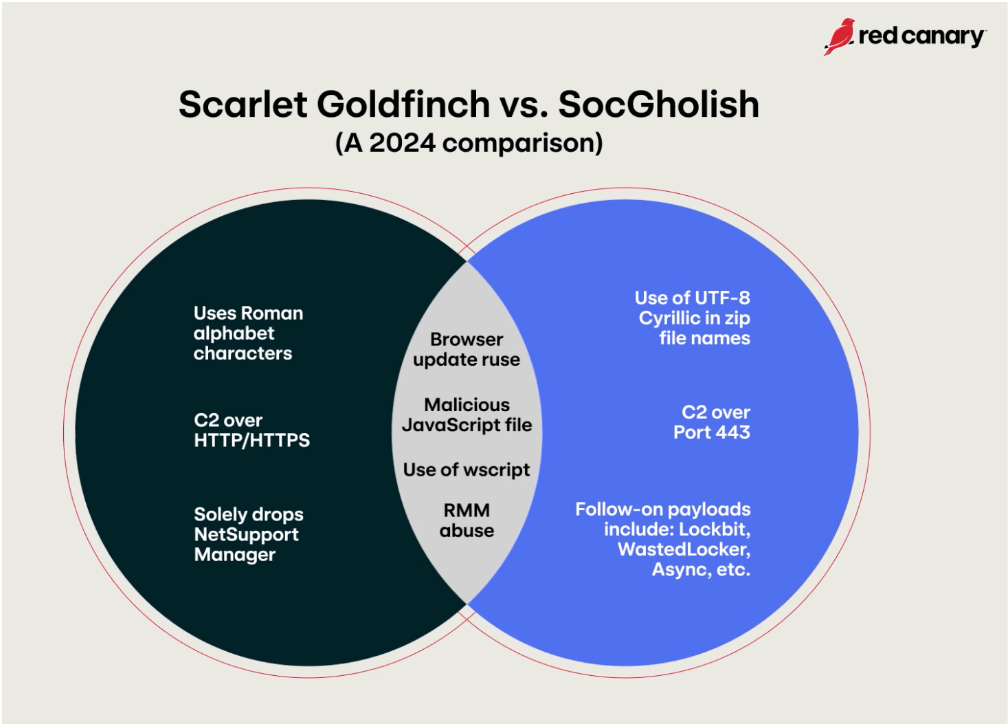
Scarlet Goldfinch: Red Canary looks at the operations of a threat actor the company tracks as Scarlet Goldfinch, which shares some of the distribution tactics employed by the older SocGolish group.
South Korea DDoS attacks: All the pro-Kremlin faketivism groups are launching DDoS attacks on South Korea, citing their regular excuse of "russophobia," per Netscout.
Nebula: Huntress has spotted a new ransomware strain named Nebula.
Threat/trend reports: ESET, Thales [PDF], and Trustwave have recently published reports covering infosec industry threats and trends.
Deepfake crypto crime: Crypto trading platform Bitget anticipates that deepfake-driven crypto crime will top $25 billion this year. The company also anticipates that deepfakes may reach 70% of all crypto crimes within the next two years.
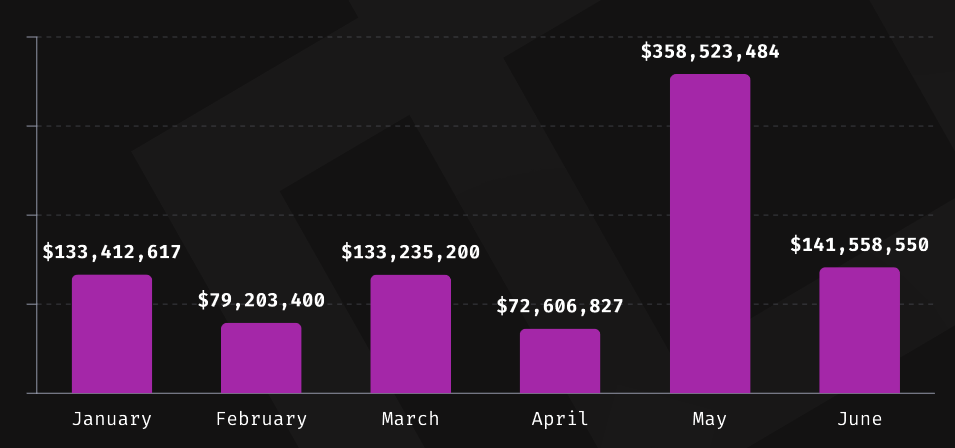
Crypto-heist numbers: Hackers have stolen more than $570 million worth of assets from crypto platforms in the second quarter of the year. According to blockchain security firm Immunefi, this brings the year's total to just over $920 million. Fraud accounted for only 1.5% of the stolen funds, while the rest was lost to platform hacks. This year's largest hack remains the $305 million heist of Japanese cryptocurrency trading platform DMM Bitcoin.
Malware technical reports
MerkSpy: Fortinet researchers look at MerkSpy, a new spyware payload distributed after threat actors exploit CVE-2021-40444, a vulnerability in Microsoft Office.
IDATLoader: Kroll's security team has a report on new updates to the IDATLoader malware family.
GootLoader: Cybereason has published a report on GootLoader and the recent SEO poisoning campaigns that are distributing the malware.
"GootLoader is a malware loader known to abuse JavaScript to download post-exploitation malware/tools and persist within the infected machine. GootLoader is a part of the GootKit malware family, which is a banking Trojan written in NodeJS that has been active since 2014. The threat actors behind GootKit, tracked by Mandiant as UNC2565, started to shift towards delivering GootLoader instead of the GootKit banking trojan."
DarkMe RAT: Sonicwall has published a report on DarkMe, a new remote access trojan that has been advertised in underground circles since February 2024.
LummaStealer: CyFirma has published a report on LummaStealer, a quite popular infostealer these days.
"Lumma Stealer, also known as LummaC2 Stealer, has been accessible via a Malware-as-a-Service (MaaS) model on Russian-speaking forums since at least August 2022. The threat actor behind its development is believed to be Shamel, who operates under the alias Lumma."
GlorySprout: eSentire researcher Ann Pham (RussianPanda) has published a report on GlorySprout, a new infostealer based on the old TaurusStealer strain.
StrelaStealer: Sonicwall has published a report on the resurgence in attacks using the StrelaStealer malware, most of them targeting European users.
SpyMax: K7 Computing looks at the new SpyMax Android RAT.
Medusa Reborn: Mobile security firm Cleafy has found a new version of the older Medusa (TangleBot) Android RAT.
Snowblind: Promon has published a report on Snowblind, a new Android banking trojan active in Southeast Asia.
P2PInfect: Cado Security looks at recent updates to the P2PInfect botnet. The botnet launched in July last year and was used to infect systems via SSH attacks. New P2PInfect modules include rootkit, crypto-mining, and ransomware components.
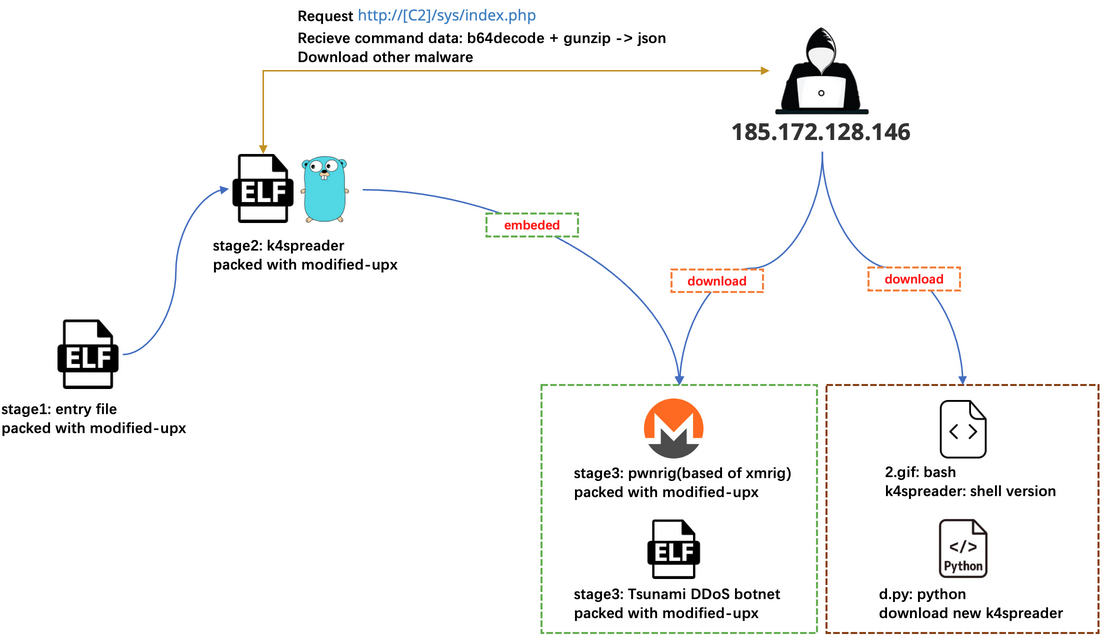
k4spreader: Chinese security firm QiAnXin has published a technical write-up on k4spreader, a new tool used by the 8220 Gang cryptomining group. The tool works as a loader for the gang's other malware strains. Trend Micro also looks at the the group's cryptominer in a separate report here.
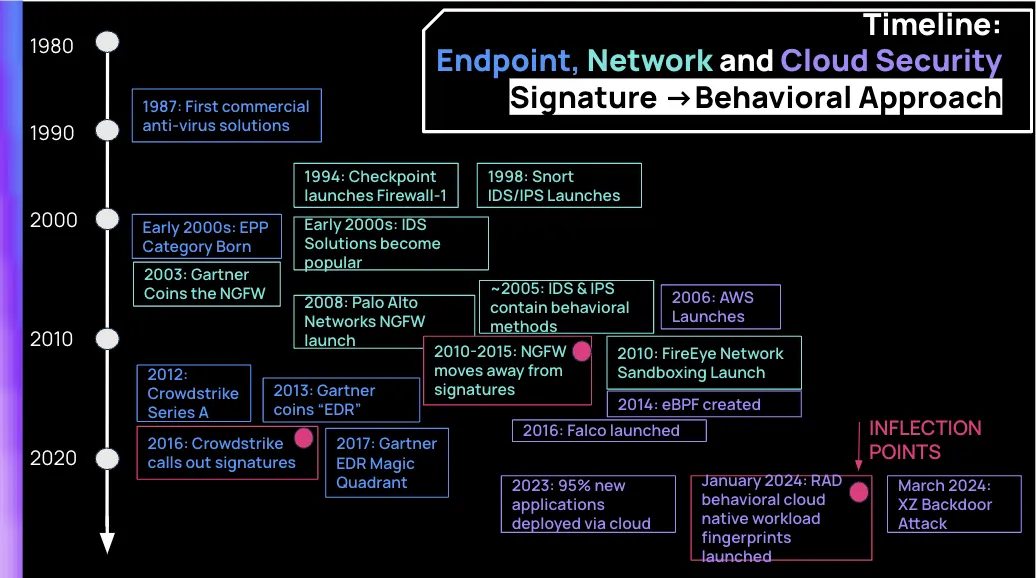
Sponsor Section
This week's sponsor, Rad Security, takes a look at how security products have evolved from older signature-based detection technologies to a more modern behavioral-based approach over the past decade.
APTs, cyber-espionage, and info-ops
WhisperGate hacker charged: The US government has charged a 22-year-old Russian national for helping Russia's military cyber units. Amin Stigal allegedly managed infrastructure that was used to hack and deploy the WhisperGate data-wiping malware ahead of Russia's invasion of Ukraine. US officials say the malware was deployed on Ukrainian government systems, as well as on US and NATO computer networks. According to court documents, Stigal had worked with the GRU military intelligence service since at least 2021. The US State Department is also offering a $10 million reward for information on Stigal's whereabouts.

Armageddon's new technique: StrikeReady looks at new malicious HTML documents used by the Armageddon Russian APT that require users to move their mouse first, before executing their payloads.
RedJuliett: Recorded Future says a suspected Chinese APT group named RedJuliett has intensified its cyber-espionage campaigns in Taiwan.
"RedJuliett compromised 24 organizations, including government organizations in Taiwan, Laos, Kenya, and Rwanda. The group also conducted network reconnaissance or attempted exploitation against over 70 academic, government, think tank, and technology organizations in Taiwan, as well as multiple de facto embassies operating on the island."
SneakyChef: Cisco Talos has discovered a new threat actor engaging in cyber-espionage campaigns across EMEA and Asia. Preferred malware include SpiceRAT and SugarGh0st RAT. No formal attribution just yet.
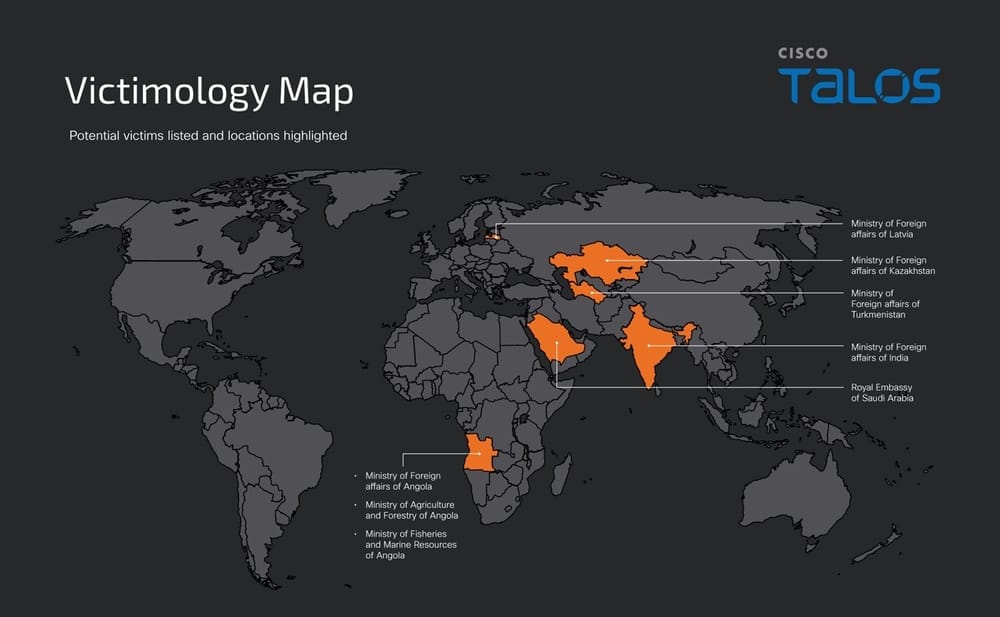
ChamelGang: A suspected Chinese espionage group named ChamelGang has deployed ransomware to hide some of its intrusions over the past years. SentinelOne and Recorded Future say the group created CatB, a ransomware strain active since mid-2022 [technical reports via Fortinet, MinervaLabs, SentinelOne]. Researchers believe the ChamelGang used CatB to hide intrusions and intelligence collection during breaches at the Presidency of Brazil and AIIMS, a major Indian healthcare institution. ChamelGang joins a list of APT groups that use ransomware to disguise and misattribute intrusions. The tactic has been used by APTs from Iran, North Korea, Russia, and China.
Operation Blotless: Japan's CERT/CC team says it discovered activity similar to Volt Typhoon that has targeted some of critical infrastructure since last year, around the same time the US revealed its initial Volt Typhoon discoveries.
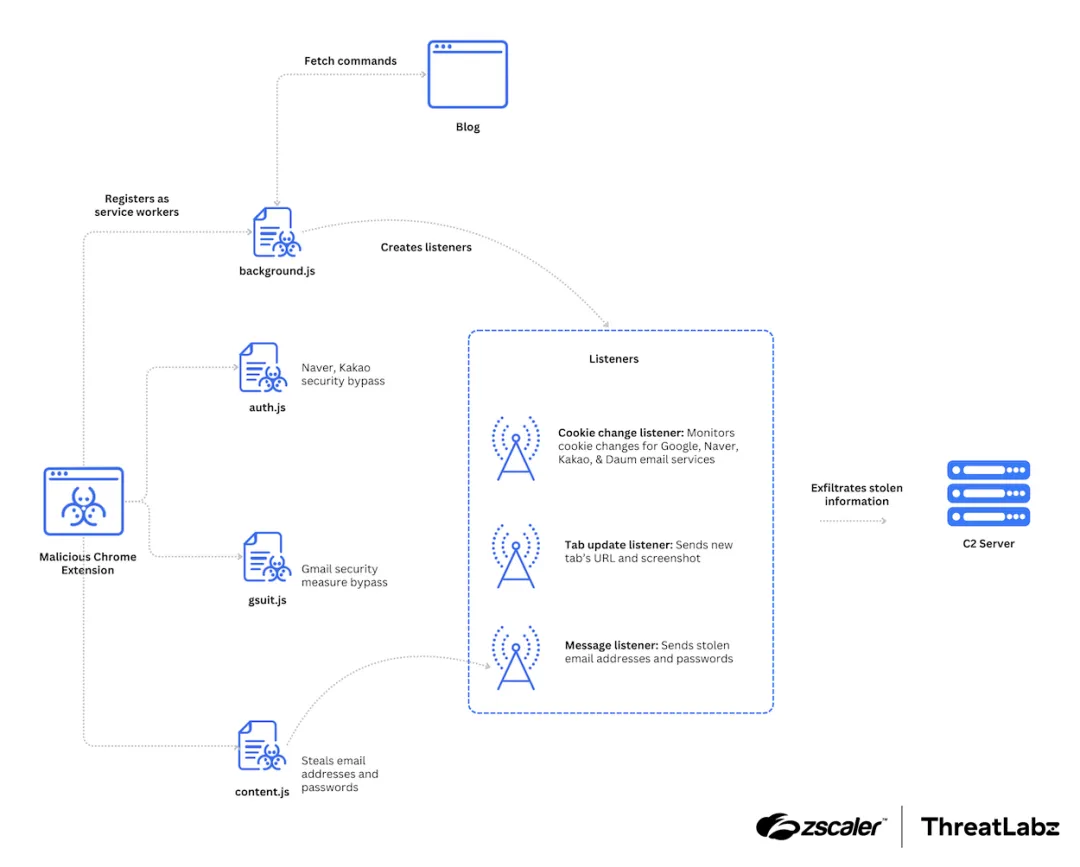
Kimsuky's TRANSLATEXT: Zscaler researchers say that North Korean APT group Kimsuky has used a new malicious Google Chrome extension named TRANSLATEXT to target and steal credentials from South Korean academics.
Kimsuky's HappyDoor: AhnLab researchers have published a report on HappyDoor, a new backdoor used by the aforementioned Kimsuky APT.
DRAGONBRIDGE info-ops: Google says it took down more than 10,000 pieces of info-ops this year linked to a Chinese influence network known as DRAGONBRIDGE.
Election audit group activity: OpenMeasures has published reports on how US right-wing groups are using Telegram and TruthSocial to organize election "audit" initiatives. Yes, you read that right. Red-blooded Americans—or so they claim—are using a Russian instant messenger to organize election integrity initiatives designed to promote the good ol' "election was stolen, we must protec" shtick.
Pile-up on the French elections: Security firm Recorded Future says that Russia and Iran are running influence operations targeting France's upcoming legislative elections. The campaigns use the same old tactics of fake news sites that mimic legitimate outlets that promote pro-Kremlin content and far-right parties. Russia's presence includes campaigns from the Doppelganger and CopyCop groups, while Iran's influence is more limited, as a clap-back for France's current support for Israel. Per another Recorded Future report, CopyCop is also targeting the upcoming US elections—because of course they are.

Vulnerabilities, security research, and bug bounty
NEWAG scandal: Train manufacturer NEWAG has filed a lawsuit against Dragon Sector, a group of Polish security researchers who hacked the company's trains to restore their functionality. NEWAG bricked the firmware of trains sold in Poland after local authorities serviced the trains at an independent maintenance shop instead of using NEWAG's expensive services. NEWAG has now filed a lawsuit accusing the security researchers of "copyright infringement and unfair competition." The company also filed a criminal complaint against the researchers at the end of last year.
Crypto white hat drama: Web3isgoinggreat has a great write-up on the whole CertiK-Kraken drama, where crypto-trading platform Kraken accused blockchain security firm CertiK of overstepping the bounds of white-hat bug bounty security research. Kraken claims CertiK found a bug in its platform, stole millions in assets, laundered the funds through the US-sanctioned Tornado Cash platform, and then reported only taking a few dollars and refused to return all the taken funds. CertiK claims it was only doing vulnerability research and that Kraken is trying to intimidate its researchers. Kraken claims it has notified authorities of the incident.
New MOVEit exploitation: Threat actors are exploiting a new vulnerability in Progress MOVEit file transfer servers. The attacks are exploiting a new authentication bypass vulnerability in MOVEit's SFTP module, tracked as CVE-2024-5806. Exploitation attempts were spotted last week, a day after Progress released a patch and a security firm published proof-of-concept code.
New D-Link exploitation: Threat actors are exploiting a recently disclosed vulnerability in D-Link to attack and hijack DIR-829 router models. The attacks are targeting a path traversal vulnerability (CVE-2024-0769) disclosed in January this year. D-Link did not release a security update because the router reached end-of-support in 2020.
New Zyxel exploitation: Threat actors are exploiting a vulnerability in Zyxel network-attached storage devices that was patched at the start of June. The vulnerability (CVE-2024-29973) allows remote code execution on two Zyxel NAS models that reached end-of-support at the end of last year. Although the products were EoL, Zyxel has released firmware updates. According to the Shadowserver Foundation, the attacks appear to be coming from a Mirai-like IoT botnet.
New printer vulnerabilities: Security researcher Pierre Barre (aka Pierre Kim) has published some of their infamous write-ups documenting tens of vulnerabilities in Sharp and Toshiba multi-functional printers. Barre found 17 bugs in Sharp printers and 40 in Toshiba ones. Vulnerabilities range from simple bugs to the worst of the worst—such as pre-authentication remote code execution attacks as the root user. More than 400 different Sharp and Toshiba printer models are impacted.
Plug&Track vulnerabilities: Nozomi has found vulnerabilities in Plug&Track Sensor Net Connect, a temperature sensor used in hospitals, and its accompanying Thermoscan IP desktop application.
UEFIcanhazbufferoverflow: Eclypsium has published a write-up on UEFIcanhazbufferoverflow (CVE-2024-0762 ), a vulnerability in Phoenix SecureCore UEFI firmware. The firmware runs on multiple families of Intel Core desktop and mobile processors.
Jenkins security updates: The Jenkins project has published security updates for some of its plugins.
Juniper security updates: Juniper has released a security update for some of its router products to fix a major vulnerability. Juniper says the issue allows threat actors to bypass the router's API authentication and control the device. Tracked as CVE-2024-2973, the vulnerability received a severity score of 10/10 and is believed to be easy to exploit. Juniper says it is not aware of any attacks exploiting the bug—so far.
GitLab security update: GitLab has also released a security update to fix 14 issues, including a bug that lets attackers run build pipelines as any user.
ORM Leaks: Security company elttam has published details on a new class of vulnerabilities it is calling "ORM Leaks." These are vulnerabilities in Object Relational Mappers (ORMs) that can leak information from apps that use affected ORMs. The company says it found leaks in ORM components used by the Django Python framework and CMSs like Label Studio, Ghost, and Payload.
Probllama vulnerability: The good ol' ../ attack hits AI models. Meet the Probllama vulnerability (CVE-2024-37032) in the Ollama large language model. The vulnerability allows RCE attacks on servers running the Ollama. The issue was found by Wiz and responsibly disclosed to Ollama's maintainers, who have since patched it.
Skeleton Key: Microsoft's security team has published details on Skeleton Key, a new AI model jailbreaking technique.
Microsoft will issue CVEs for cloud bugs: Microsoft will issue CVE identifiers for critical vulnerabilities in its cloud services. An example CVE is here.
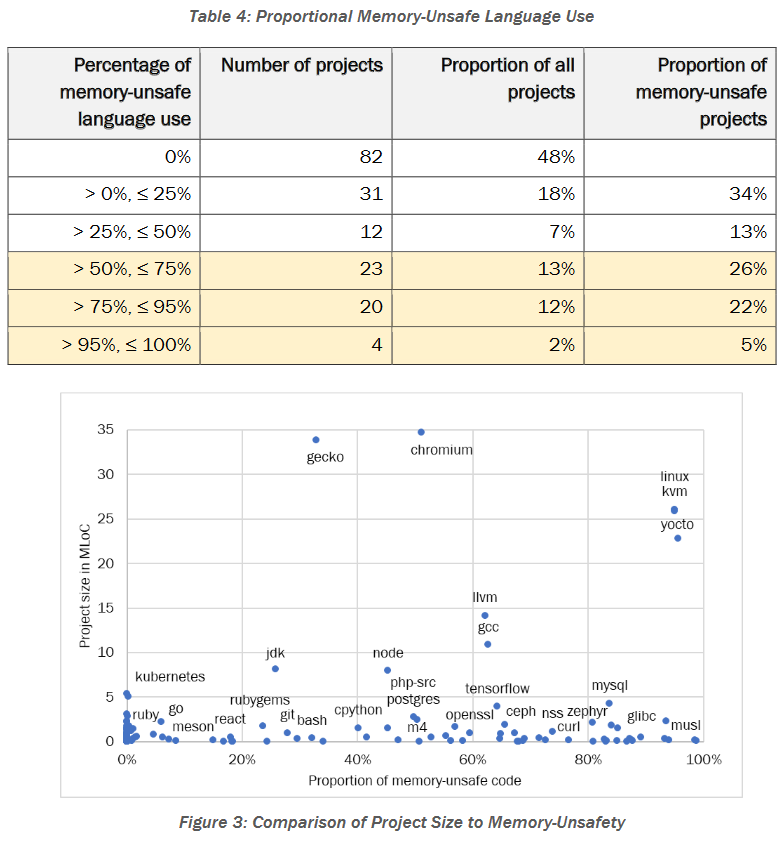
Memory-safe languages: Research from cybersecurity agencies in Australia, Canada, and the US has found that the vast majority of popular open-source projects don't use or use very little code written in memory-safe programming languages. Only 47 of the world's 172 most popular projects used memory-safe languages on more than half of their code. Projects like the Linux kernel, Chromium, and the LLVM and GNU compilers accounted for most of the code written in unsafe languages. Smaller open-source projects contained more code written in memory-safe languages such as Rust or Go.
Infosec industry
New tool—Expired Systems: IT security engineer Jeffrey Tigchelaar has launched Expired Systems, a portal that keeps track of expired certificates at big companies and the chaos they're causing.
New tool—Certiception: German security firm SRLabs has open-sourced Certiception, an Active Directory Certificate Services (ADCS) honeypot tool.
New tool—RedFlag: Software company Addepar has open-sourced RedFlag, a tool that leverages AI to determine high-risk code changes in CI pipelines and source code repos.
New tool—CGPwn: Security firm NetSPI has open-sourced CGPwn, a pen-testing framework for the Google Cloud Platform. See fwd:cloudsec conference talk here.
New tool—LetterDrop: i365 Tech has released LetterDrop, a replacement for Mailchimp's now-defunct TinyLetter newsletter service.
New podcast: Ryan Naraine, Costin Raiu, and J. A. Guerrero-Saade have launched a new weekly infosec podcast named The Three Buddy Problem.
ZeekWeek cancelation: The Zeek project has canceled this year's edition of the ZeekWeek conference due to poor attendance.
HITCON 2023: Talks from the HITCON 2023 security conference, which took place in August last year, are now available on YouTube. Talks are available in Chinese and English.
OFFZONE 2023: Talks from the OFFZONE 2023 security conference, which took place in August last year, are available on YouTube. Talks are available in both Russian and English.
fwd:cloudsec 2024: Talks from the fwd:cloudsec 2024 security conference, which took place last month, are now available on YouTube.
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about a new report [PDF] that explores how China's vulnerability discovery and research ecosystem is linked to state-sponsored espionage. This research finds that a relatively small number of people are responsible for an outsized contribution to vulnerability discovery. They also talk about difficulties at CISA's Joint Cyber Defence Collaborative initiative and why it should be retired.
Abhishek Agrawal is the CEO and co-founder of Material Security, an email security company that locks down cloud email archives. Attackers have been raiding mailspools since hacking has existed, and with those mailspools now in the cloud with services like o365 and Google Workspace, guess where the attackers are going?




