Risky Biz News: Rare pro-Western influence operation caught and exposed
In other news: LastPass and Plex disclose security incidents; and Twilio hack also impacted Okta and DoorDash.
This newsletter is brought to you by Airlock Digital, Proofpoint, RunZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
While we've gotten accustomed to social media influence operations carried out from and promoting the national interests and political agendas of China, Russia, Iran, and other oppressive regimes, pro-Western operations are also taking place, but at a far smaller scale.
In a joint report published on Wednesday, social media research group Graphika and the Stanford Internet Observatory Cyber Policy Center (SIO) published an analysis of two overlapping sets of accounts that promoted pro-Western views.
The accounts—registered on Facebook, Instagram, and Twitter—had been active since at least early 2012 and were removed by the companies in July and August this year, with data on their activity made available to Graphika and Stanford researchers for further analysis.
The resulting 57-report details separate influence operations targeting Central Asia, Iran, Afghanistan, and the Middle East, with posts made in Russian, Persian, Urdu, and Arabic, targeting local audiences.
The campaigns promoted pro-US views but also narratives critical of Iran, the Islamic State, the Taliban, China, and Russia, ranging in topics from local politics to the treatment of minority groups.
But unlike bot networks and influence operations carried out by Russian and Chinese troll farms, both campaigns were small, comprising of roughly 200 accounts spread across all three social media sites.
As a result, Graphika and SIO said that despite the years-long effort, both clusters were mostly ineffective and failed to garner any meaningful support for their narratives.
The Twitter dataset provided to Graphika and SIO covered 299,566 tweets by 146 accounts between March 2012 and February 2022. These accounts divide into two behaviorally distinct activity sets. The first was linked to an overt US government messaging campaign called the Trans-Regional Web Initiative, which has been extensively documented in academic studies, media reports, and federal contracting records. The second comprises a series of covert campaigns of unclear origin. These covert campaigns were also represented in the Meta dataset of 39 Facebook profiles, 16 pages, two groups, and 26 Instagram accounts active from 2017 to July 2022.
Graphika and SIO said that despite the obvious promotion of pro-US and pro-Western views, neither Meta nor Twitter made any public or firm attribution of their findings.
According to the joint report, Twitter described the "presumptive countries of origin" of the two clusters as the US and Great Britain, while Meta said the "country of origin" was the US but did not say if the US government was the entity behind the operation. As Motherboard pointed out in its coverage, social media influence campaigns have been run from inside the US by private entities before.
But going past the shock of discovering a rare pro-Western influence operation, other interesting conclusions were also drawn, such as the fact that pro-Western campaigns largely used the same tactics as Chinese, Iranian, and Russian operators—namely fake personas, GAN-generated avatars, fake independent news outlets, loads of images and video memes, hashtag campaigns, and boring online petitions.
What appears to have lacked in these campaigns was scale, something that Russian and Chinese trolls appear to have figured out and fixed a long time ago, probably because both states have put a much greater onus on this particular tactic and approach to destabilizing their international rivals.
Breaches and hacks
LastPass breach: Password management utility LastPass disclosed a security breach on Thursday. The company said an unidentified attacker compromised a single developer account and accessed a dev environment from where they took portions of its source code. LastPass said the intruder did not gain access to any user data or master passwords.
Twilio hack impacted Okta: Identity and authentication provider Okta said on Thursday that it is one of the companies impacted by the recent Twilio hack. The company said the threat actor, which it tracks as Scatter Swine, has used its Twilio account to view SMS one-time passcodes the company sent to some mobile phone numbers. In the meantime, Twilio has also updated its breach disclosure for the second time since the hack earlier this month and changed the number of affected customers from 125 to 163. Okta now becomes the fourth known company targeted during the Twilio hack after similar disclosures from Cloudflare, Signal, and…
DoorDash too: …and DoorDash, which also disclosed yesterday that it was impacted by the Twilio hack as well. [Additional coverage in TechCrunch]
Plex breach: Streaming service Plex notified users of a security breach this week and asked them to reset their passwords. The company said it discovered the hack on Tuesday and that the attacker accessed "a limited subset of data that includes emails, usernames, and encrypted passwords." According to a statement to TechCrunch, Plex said the passwords were salted and hashed (with bcrypt).
Just got an email from Plex regards to potential breach on their customers details. As anyone else seen this? @troyhunt @briankrebs @campuscodi
— Paresh Kerai (@mamboz01) 5:56 AM ∙ Aug 24, 2022
OneTwoTrip leak: Ukrainian security researcher Bob Diachenko said he identified Elasticsearch servers belonging to OneTwoTrip, a Russian online travel service, that had leaked the company's data for several days last week. Leaked data included information on the company's customers and their trips.
Adorcam leak: The operators of Adorcam, an iOS and Android app that can let you connect to some IP security cameras, left an Elasticsearch server exposed online that leaked more than 124 million records from its customers.
Dominican Republic ransomware attack: A ransomware attack has encrypted the data of the Dominican Republic's Ministry of Agriculture, local media reported. According to BleepingComputer, the attack has been claimed by the Quantum gang, which has allegedly requested $650,000 for the state agency to decrypt its files.
Binance COO deep fake incident: Binance CCO Patrick Hillmann said last week that scammers used a deepfake video of himself to reach out via video calls to representatives of various cryptocurrency projects. Hillmann said the scammer requested large sums of money from the projects to have them listed on the Binance exchange.
Intellexa docs appear to have leaked online: Documentation files related to Nova, a powerful hacking and surveillance platform for Android and iOS devices developed by the Intellexa intelligence alliance, are believed to have been leaked online. The files were leaked in July on XSS, a Russian-speaking cybercrime forum, but the company has yet to confirm the leak.
A thread on the infamous forum of xss.is featured a proposal contract from Intellexa for (one of?) their mobile spyware platform that's able to target recent versions of both Android and iOS. I break it down in this 🧵👇
— 🏴 Jurre van Bergen (@DrWhax) 10:32 AM ∙ Aug 25, 2022
Entrust data leaks online: Data stolen during the ransomware attack that took place at security firm Entrust has been leaked online on the Breached cybercrime forum. The leak comes after the website of the LockBit ransomware gang has been under a constant DDOS attack for days, with the attackers telling the gang to delete the data from its servers. Apparently, LockBit didn't like that, and now the data is available for all via today's most popular data trading forums.
#Entrust data is allegedly being shared via #BreachForums following the ongoing #DDoS attacks against #Lockbit's Darkweb sites...
— BetterCyber (@_bettercyber_) 4:22 PM ∙ Aug 25, 2022
General tech and privacy
SSH commit verification: GitHub now supports SSH commit verification, so you can sign commits and tags locally using a self-generated SSH public key. If a commit or tag has an SSH signature that is cryptographically verifiable, GitHub makes the commit or tag "Verified" or "Partially Verified."
Meta settles Facebook tracking suit: Meta has settled a class-action lawsuit for violating the privacy of Facebook users and tracking their location via their smartphones without permission. The lawsuit, filed in California, was preliminarily settled for $37.5 million.
Google reported for inserting ads inside inboxes: EU privacy watchdog noyb has filed a complaint with the French privacy agency CNIL, reporting that Google is inserting and disguising ads as emails in its Gmail service.
Sephora fine: Cosmetics giant Sephora has agreed to pay a $1.2 million fine in the state of California for violating the state's privacy law and collecting data on its online users.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
NFT thief investigation: OSINT researcher ZachXBT published a report on Wednesday alleging that a young Canadian—who we will not be naming here despite being named in the report—is responsible for recent thefts of popular and high-priced NFT items. ZachXBT said the same individual is the teen who pleaded guilty in June to SIM swapping and then stealing more than $37 million worth of cryptocurrency from California-based entrepreneur and Bitcoin pioneer Josh Jones.
From game anti-cheat to ransomware: Trend Micro researchers said they discovered that a vulnerable anti-cheat driver for the popular role-playing game Genshin Impact is currently being abused by a ransomware actor to kill antivirus processes and services to mass-deploy ransomware.
Confirmed, this is real, used on a few thousand devices.
— Cloudflare Support Hate (@GossiTheDog) 5:03 PM ∙ Aug 25, 2022
To be clear you don't have to be a Genshin Impact player for this - they reuse the vulnerable kernel driver during hands on ransomware deployment.
Sliver C2 framework abuse: Microsoft said in a report on Wednesday that it is seeing an increase in the use of Sliver, an adversary emulation framework developed by BishopFox. Microsoft's warning comes after a similar one from Team Cymru last month.
We've seen these actors use Sliver with—or as a replacement for—Cobalt Strike. Given Cobalt Strike's popularity as an attack tool, defenses against it have also improved over time. Sliver thus presents an attractive alternative for actors looking for a lesser-known toolset with a low barrier for entry.
Raven Storm tool: CloudSEK has a report on Raven Storm, a DDoS tool used by the Mysterious Team hacktivist group in recent attacks.
New Monster ransomware: Kaspersky said it discovered a new ransomware strain named Monster. The ransomware is written in Delphi, comes with a UI, and supports multiple OS platforms.
Black Basta ransomware: Palo Alto Network's Unit42 has published a report on the Black Basta ransomware and its preferred intrusion and operational tactics.
TeamTNT: CloudSEK researchers have also published a timeline and TTPs for TeamTNT, the cryptomining gang, not the phishing crew.
AgentTesla phishing campaign: Security firm Avast has details on a new phishing campaign that has sent out more than 26,000 emails to organizations across Europe and South America. The final payload in these attacks is the AgentTesla RAT.
Other malware campaigns: AhnLab also has two reports out on malops campaigns distributing payloads like AsyncRAT and BitRAT+XMRig.
PyPI phishing campaign: The Python security team said it detected a phishing campaign targeting the authors of Python libraries listed on the PyPI portal. The emails asked library owners to verify their packages by logging into a phishing site that collected their credentials. The Python team said that "some maintainers of legitimate projects have been compromised, and malware published as the latest release for those projects," packages that the PyPI team has since removed. It also froze the compromised accounts.
Today we received reports of a phishing campaign targeting PyPI users. This is the first known phishing attack against PyPI.
— Python Package Index (@pypi) 2:10 PM ∙ Aug 24, 2022
We’re publishing the details here to raise awareness of what is likely an ongoing threat.
0ktapus: Group-IB said it identified a spear-phishing campaign targeting the Okta accounts of corporate entities. Named 0ktapus, this campaign has been going on since March this year and based on data Group-IB obtained from the attacker's infrastructure, 0ktapus operators collected almost 10,000 victim credentials for more than 130 organizations.

Malware technical reports
New HavanaCrypt ransomware: Cybereason has published a technical report on a new ransomware strain named HavanaCrypt. First observed in the wild in June this year, HavanaCrypt targets home users and typically masquerades as a legitimate Google Chrome update in order to gain access to a system and encrypt its files.
New Agenda ransomware: Another new ransomware strain discovered this week is the new Agenda ransomware. According to Trend Micro, the ransomware is written in Go, has been used in targeted attacks in Asia and Africa, and has demanded ransom payments ranging from $50,000 to $800,000, depending on the victim.
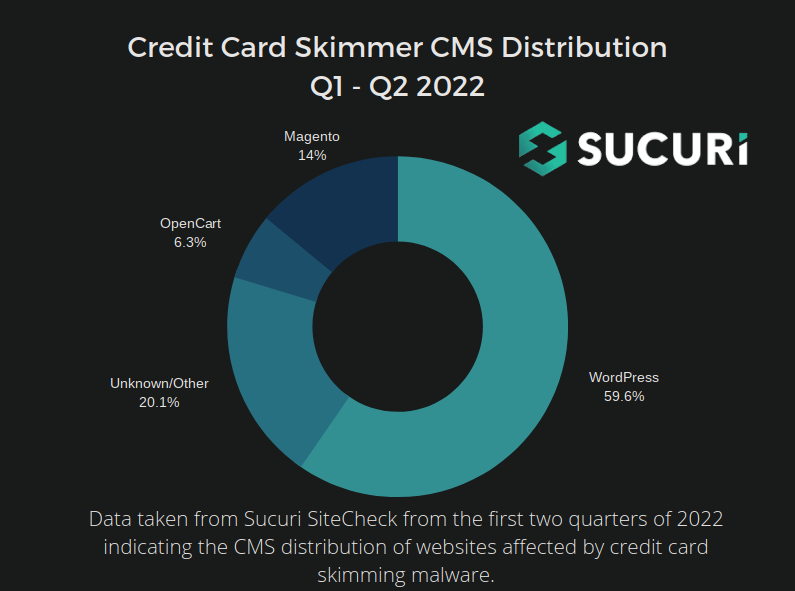
Web skimmers: GoDaddy's Sucuri team has analyzed some of the less-common credit card skimmer scripts that it found in malware campaigns this year. According to the same report, Sucuri said that almost 60% of all skimmer detections this year have been for scripts installed on WordPress-based sites; a change from July 2021, when the vast majority of web skimmers were installed on Magento-based stores.
APTs and cyber-espionage
Kimsuky: Kaspersky researchers have analyzed an infrastructure cluster (named GoldDragon) operated by the Kimsuky APT and used in attacks this year against a media organization and a think-tank in South Korea.
Nobelium: Microsoft said it uncovered a new malware strain named MagicWeb that has been developed by the Nobelium threat actor and used as a post-compromise toolkit as part of recent attacks. Microsoft says Nobelium is using this tool to backdoor AD FS servers and maintain access to hacked networks during defenders' remediation efforts.
Skeleton key attack ported to AD FS.
— Tal Be'ery (@TalBeerySec) 6:17 AM ∙ Aug 25, 2022
An excellent blog post
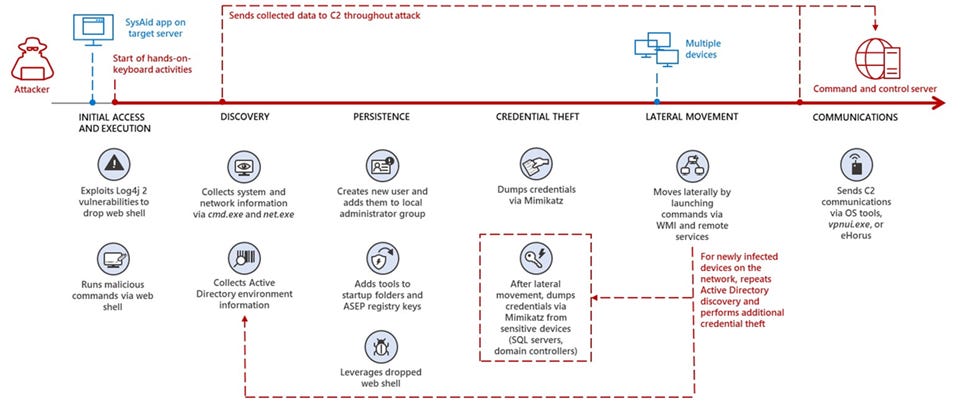
Mercury: Microsoft's security team also said it detected Iran-based threat actor MERCURY leveraging exploitation of Log4Shell vulnerabilities to compromise SysAid remote IT management servers used by Israeli organizations. Previously, the same threat actor also used the Log4Shell vulnerability to compromise VMWare servers as well.
Vulnerabilities and bug bounty
Another WatchGuard RCE: Ambionics security researcher Charles Fol said he discovered and helped patch another dangerous RCE vulnerability in WatchGuard Firebox firewalls. These are the same devices that have been targeted and exploited by the Sandworm APT earlier this year with the Cyclops Blink malware.
Linux kernel vulnerability: South Korean security firm Theori has published details on CVE-2022-32250, a Linux kernel exploit that can be used to elevate an attacker's privileges on Linux systems. The vulnerability resides in Netfilter, the Linux kernel network package filtering framework.
Infosec industry
New tool—RPCMon: Cybersecurity firm CyberArk has open-sourced a new tool called RPCMon, a GUI for scanning RPC communication through Event Tracing for Windows (ETW).
New tool—YaraML: Sophos researchers have open-sourced a new tool named YaraML that uses machine learning to generate YARA rule from a dataset of malicious/benign labeled data.
Rust malware tut: BinaryDefense researchers have a tutorial out on how to extract artifacts from Rust malware.




