Risky Biz News: Ransomware wave hits thousands of VMWare ESXi servers
In other news: Vastaamo hacker arrested; Google lays off 60% of Jigsaw staff; 28% of Microsoft user accounts use MFA.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
A massive ransomware wave has hit VMWare servers over the weekend, encrypting thousands of unpatched and internet-exposed ESXi systems.
The attacks are exploiting a two-year-old vulnerability tracked as CVE-2021-21974, which allows the threat actors to execute remote commands on unpatched VMWare ESXi servers via their OpenSLP service (on port 427).
Once the attackers get in, they encrypt files on the ESXi server and leave a ransom note behind, asking for $50,000 in bitcoin to decrypt each infected server.
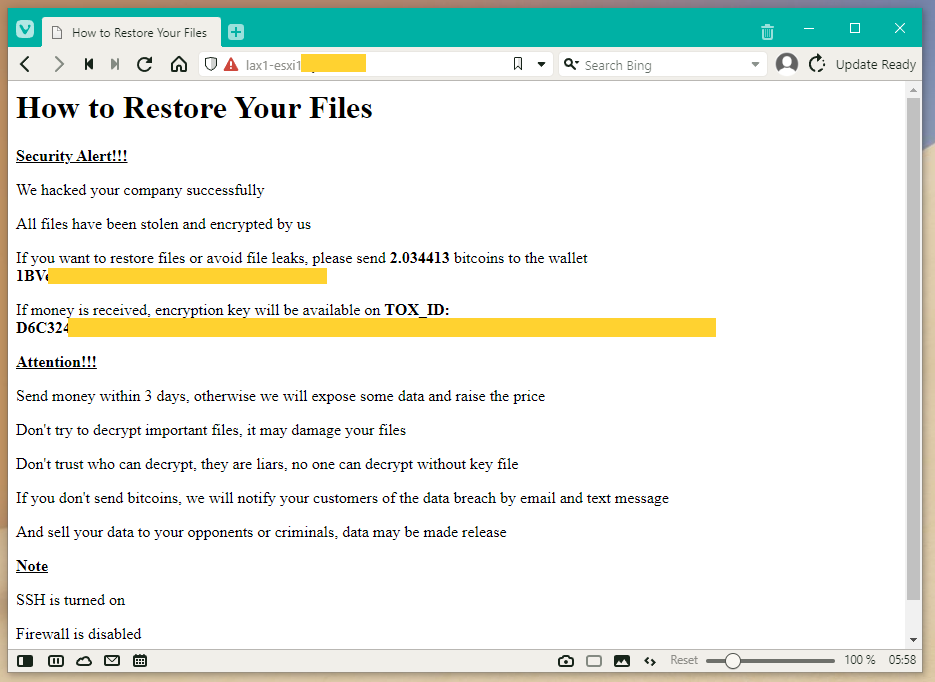
An analysis from OVHcloud's security team initially identified the ransomware as a version of the newly launched Nevada strain. Another report identified it as a version of the Cheerscrypt ransomware—and based on the leaked Babuk ransomware source code.
In the end, both initial assessments proved to be incorrect, and currently, the ransomware strain is tracked as ESXiArgs.
All in all, French cloud hosting provider OVH had a front-row seat to the attacks because France hosted most of the affected servers, hence why France's CERT team was the first agency to spot the outbreak before anyone else.
According to a Censys search query for the ransomware note, more than 2,500 servers have been encrypted so far, and more than a third of these are hosted in France.
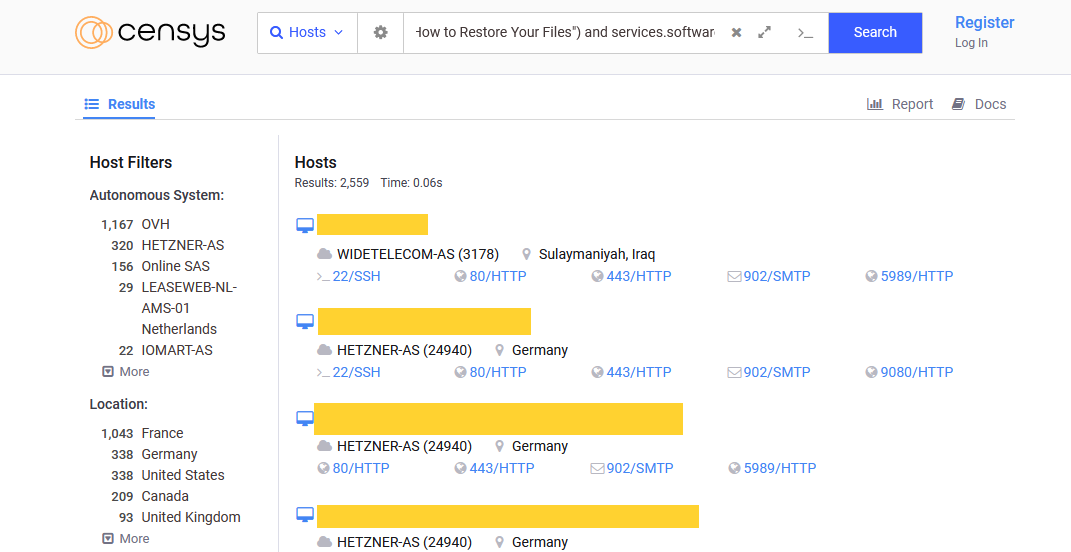
According to replies in a thread on the attacks hosted on the Bleeping Computer forum, most of the affected organizations were using ESXi servers rented from cloud providers.
As Kevin Beaumont perfectly summarized it on Mastodon:
"One lesson learned from this — some cloud providers that offer managed VMware hosting haven't been patching and leave all ports open to the internet on management IPs 🤦♀️"
To mitigate attacks, organizations running VMWare servers are advised to patch ESXi servers, move to a version not affected by the attacks (such as v8), or disable the OpenSLP service (see instructions here).
It is also not recommended paying the attackers. As security researcher Soufiane Tahiri spotted, the threat actor reused some Bitcoin addresses to collect ransoms, which could cause issues when proving payment and receiving/releasing the proper decryption key.
With this campaign having proved so successful for the attackers, it should be expected that other threat actors will also move in to exploit the same CVE-2021-21974 vulnerability soon. A public proof-of-concept exploit has been available for this bug since March 2021, shortly after the bug was disclosed, so, honestly, we have no idea why companies haven't rushed to patch this back then. Some people like playing with fire, we guess!
Breaches and hacks
Orion Protocol crypto-heist: DeFi trading platform Orion Protocol has lost ~$3 million worth of cryptocurrency assets after a hacker exploited a re-entry attack vulnerability in one of its smart contracts last week. Following the hack, Orion Protocol CEO Alexey Koloskov went online to reassure users that all their funds were safe. [Press coverage in Coindesk; technical analysis by Numen Cyber Labs]
Canceled surgeries: The Tallahassee Memorial HealthCare (TMH) hospital says it was forced to cancel all non-emergency surgeries and other medical procedures following what officials described as an "IT security issue" that crippled its computer systems on Thursday night last week. The hospital says that with the exception of Level 1 traumas and other life-threatening scenarios, it will also divert all incoming emergency patients to other nearby hospitals. The incident is believed to be yet another ransomware attack on US healthcare providers.
988 cyberattack: US federal officials say that a cyberattack has caused a nearly daylong outage to the nation's new 988 mental health helpline in an incident that took place on December 1, last year. The attack hit the network of Intrado, the company that provides telecommunications services for the helpline, a spokeswoman for the US Substance Abuse and Mental Health Services Administration told the AP last week.
General tech and privacy
Microsoft MFA stats: Microsoft says that 28% of its userbase is now using a multifactor authentication solution to protect their Microsoft accounts.
Microsoft Office update: Microsoft has pushed a special update to Windows users that will gather diagnostics and telemetry data from users who still run outdated versions of Office, such as Office 2013, Office 2010, and Office 2007. Microsoft says this update (KB5021751) is only meant to determine the number of users still running the outdated versions and see how it can support them beyond those products' EOLs.
"This update gathers diagnostic and performance data to estimate the usage of installed Office versions to determine how best to support and service these systems. This data is gathered from registry entries and APIs."
MetaMask security updates: Cryptocurrency wallet MetaMask has announced new security features for its service, such as the addition of a new "Security and Privacy Settings" section, phishing detection capabilities, and warnings for incoming malicious transactions.
Spyware maker to notify all victims: The New York Attorney General's Office has fined a New York businessman $410,000 for misleading customers into thinking mobile apps he was advertising online were legal to use. New York Attorney General Letitia James says apps developed by Patrick Hinchey and advertised through a network of 16 software companies were actually spyware, allowing abusers to track the location and communication of partners and spouses without their knowledge, an action that violates numerous state and federal laws. In addition to the fine, Hinchy will also have to modify all spyware apps to notify device owners that they are being monitored without their consent or knowledge. Spyware apps identified by New York officials as spyware in court documents [PDF] include Auto Forward, Easy Spy, DDI Utilities, Highster Mobile, PhoneSpector, Surepoint, and TurboSpy.
"The companies owned by Hinchy and named in today's agreement include Powerline Group Inc., Powerline Media LLC, Powerline Data LLC, Powerline Digital LLC, Powerline Commerce LLC, ILF Mobile Apps Corp., Auto Forward Data Services LLC, DDI Utilities Inc., DDI Data Solutions Inc., Highster Mobile Inc., Highster Data Services LLC, PhoneSpector LLC, Safeguarde LLC, BFG Marketing LLC, Digital Security World LLC, and CTS Technologies Corp."
Government, politics, and policy
Proposed EU chat control law: The EU is working on a draconian and overly broad regulation that would force all messaging providers to search all their users' private chats, messages, and emails. Authorities claim they want to prevent child sexual exploitation material (CSEM) from being sent across the internet, but privacy advocates say the upcoming regulation would effectively be akin to a total mass surveillance system. Even worse, the law's overly broad and unclear text also seems to (accidentally) ban the use of open-source software.
New cybersecurity law in Tibet: Chinese authorities have passed a new cybersecurity law for its Tibet province allowing law enforcement to crack down on anyone for "public disorder by engaging in separatist acts." According to RadioFreeAsia, the law has been intentionally left very vague, and experts believe officials will use it to go after anyone promoting Tibetan values and topics and not state-approved narratives.
Sponsor section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Vastaamo hacker arrested: French authorities have detained Julius Kivimäki, a 25-year-old Finnish national accused of hacking the Vastaamo Psychotherapy Center. The Vastaamo incident, considered one of the worst in the country's history, took place in 2018 and 2019 when a hacker stole the personal medical records of the clinic's patients and attempted to extort the clinic. To put pressure on the company, the hacker leaked extremely sensitive client files on the dark web. When that failed, the hacker sent emails with ransom demands to more than 30,000 of the clinic's patients, asking for €200 and threatening to publish their medical records if they didn't pay. Finnish authorities formally identified Kivimäki as the Vastaamo hacker in October last year when they issued a European arrest warrant in his name.
Exclu takedown: Dutch authorities have dismantled Exclu, a secure messaging service used by criminal groups. Dutch police claim they were able to use "specialist knowledge and expertise in the field of technology and cybercrime" and "hacking warrants" to breach the service and read messages exchanges over the past five months. Exclu operated as a mobile app that allowed users to exchange encrypted messages, photos, videos, and voice memos. The service was rented for €800 for six months of use and had about 3,000 users before it was taken down. Dutch authorities say that besides taking down Exclu's infrastructure, they also detained its owners, administrators, and some of its users.
Revil case in Russia: Russian news outlet Kommersant says Russian officials have completed the investigation into the alleged REvil ransomware gang members detained at the start of 2022. Citing a source close to authorities, Kommersant says the Russian government was only able to charge the eight suspects with payment card fraud after stealing funds from US citizens, but not with their involvement in the ransomware attacks. Just like they said before, Russian authorities blamed the case's unraveling on the FBI, which stopped communicating with Russian counterparts after Russia's invasion of Ukraine.
KEV update: CISA has updated its KEV database with two new vulnerabilities that are currently being actively exploited. The first is CVE-2023-22952, a zero-day in SugarCRM that was exploited in early January as a zero-day. The second is CVE-2022-21587, an Oracle E-Business Suite vulnerability patched in October last year that has recently come under exploitation after Viettel Cybersecurity published a PoC for it.
Dread down for a month: Dread, a Reddit-like clone hosted on the dark web where most dark web marketplaces like to advertise, has been down for more than a month since the end of December last year. The site's administrators say they had to take down the site after they were hit "with the largest scale DoS attack yet." Despite several attempts to bring back the site, Dread, along with Recon and the DNM Bible, two services run by the same admin team, are all still down.
Out in the open: In the meantime, dark web drugs marketplace BlacSprut is running electronic billboards for its service across Moscow in the open. At this point, we have to wonder which Russian intelligence agency is behind this one that they feel so emboldened to NGAF.
VSTO PoC: Researchers with security firm DeepInstinct say they are seeing threat actors abuse the Visual Studio Tools for Office (VSTO) add-in to run malicious code and install malware on user devices. The team released a PoC to help companies test their defenses for this new threat vector.
OneNote abuse: Security firms Proofpoint, WithSecure, OpalSec, and Yoroi say that over the past few months, the number of threat actors abusing Microsoft OneNote documents to deliver malware via email has increased dramatically. The trend appears to have caught on with many groups after Microsoft's moves last year to counter the use of VBA macros to install malware via Office documents. Just like with the malicious VBA macros delivered via Office files, in order to install malware on their devices, end-users must interact with the malicious OneNote document they receive via email, which provides opportunities for employee training and systems defense. Malware delivered via OneNote documents in January 2023 includes the likes of AsyncRAT, Remcos, Redline, AgentTesla, Quasar RAT, XWorm, Netwire, DOUBLEBACK, and Qbot.
Telegram and cybercrime: KELA has a 59-page report [PDF] on how Telegram turned from an IM service into a cybercrime haven.
"The anonymity of Telegram is one of the main reasons it appeals to hackers. Telegram allows users to register accounts without disclosing personal information, making it simple to set up many identities and use them to converse without revealing one's genuine identity. Because of this anonymity, law enforcement organizations have a tough time tracking down and identifying individuals who are using the program for illicit activities."
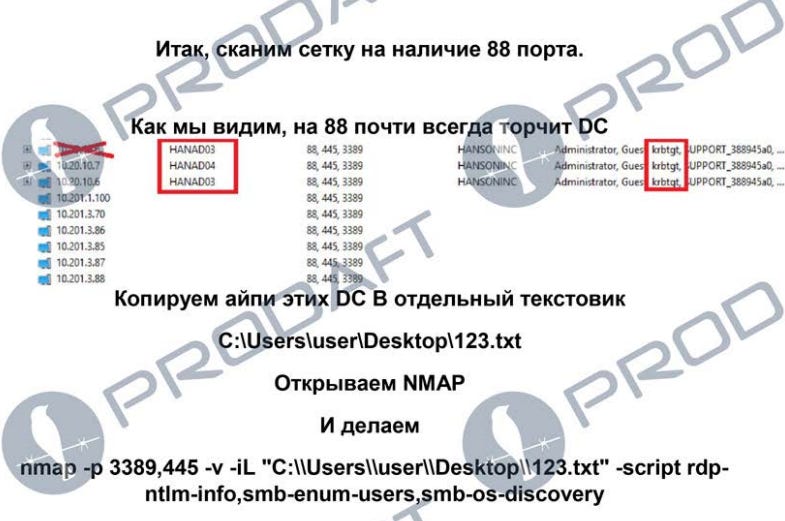
Ransomware manual: Threat intel company Prodaft has obtained and translated a so-called "ransomware manual" that is currently being sold on underground forums for around $10,000. The manual is being sold by a threat actor named "Bassterlord" and includes step-by-step guides on how to scan and brute-force enterprise-grade VPN servers and how to take over VMWare ESXi systems.
Malware technical reports
TgToxic: Security firm Trend Micro says it is tracking an ongoing malware campaign that has been targeting Android mobile users in Taiwan, Thailand, and Indonesia since July 2022. Trend Micro says the malware, which they named TgToxic, can steal user credentials, cryptocurrency from digital wallets, and money from bank and finance apps. One of the malware's defining features is its use of the legitimate Easyclick app testing framework to automate taps and gestures using JavaScript code. Trend Micro says the TgToxic gang has used SMS phishing, WhatsApp, Facebook, and Viber spam messages to distribute their malware to victims.
PixPirate: Mobile security company Cleafy says it identified a new Android banking trojan named PixPirate. Campaigns distributing this malware were spotted at the end of 2022 and are ongoing. Cleafy says the malware targets Brazilian banks only, as it uses their integration of the Pix instant payment service to exfiltrate funds from compromised accounts.
AveMaria RAT: Zscaler researchers have a report out on the tactics used to distribute the AveMaria remote access trojan throughout last year.
Trigona ransomware: A new ransomware strain named Trigona has been spotted in the wild by Fortinet researchers.
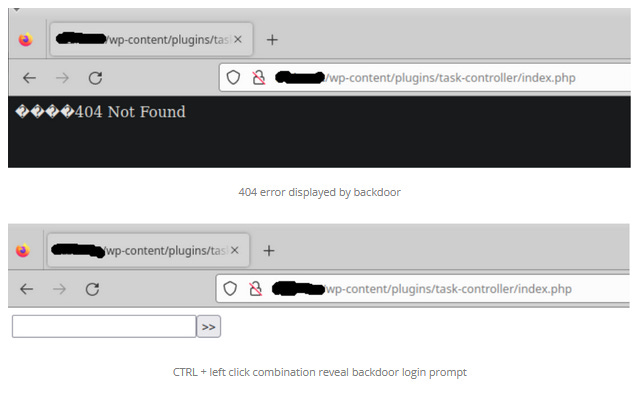
Konami code backdoor: Sucuri researchers have found WordPress sites hacked by the SocGolish operation with a clever backdoor that uses a secret key combination (CTRL+LeftMouseClick) to reveal its login prompt.
APTs and cyber-espionage
Patchwork APT: Chinese security researchers have published an analysis of Patchwork, an Indian cyber-espionage group, also known as the White Elephant or the Mahacao APT.
Blind Eagle APT: CNTIC researchers have an analysis of a recent Blind Eagle phishing campaign targeting Ecuador organizations. Blind Eagle, also known as APT-C-36, is a financial and cyber-espionage APT group that has targeted various countries across South America since 2018.
Mustang Panda APT: EclecticIQ researchers put out a report on a recent Mustang Panda spear-phishing campaign distributing the PlugX malware. The attacks were spotted in December 2022 and targeted European organizations.
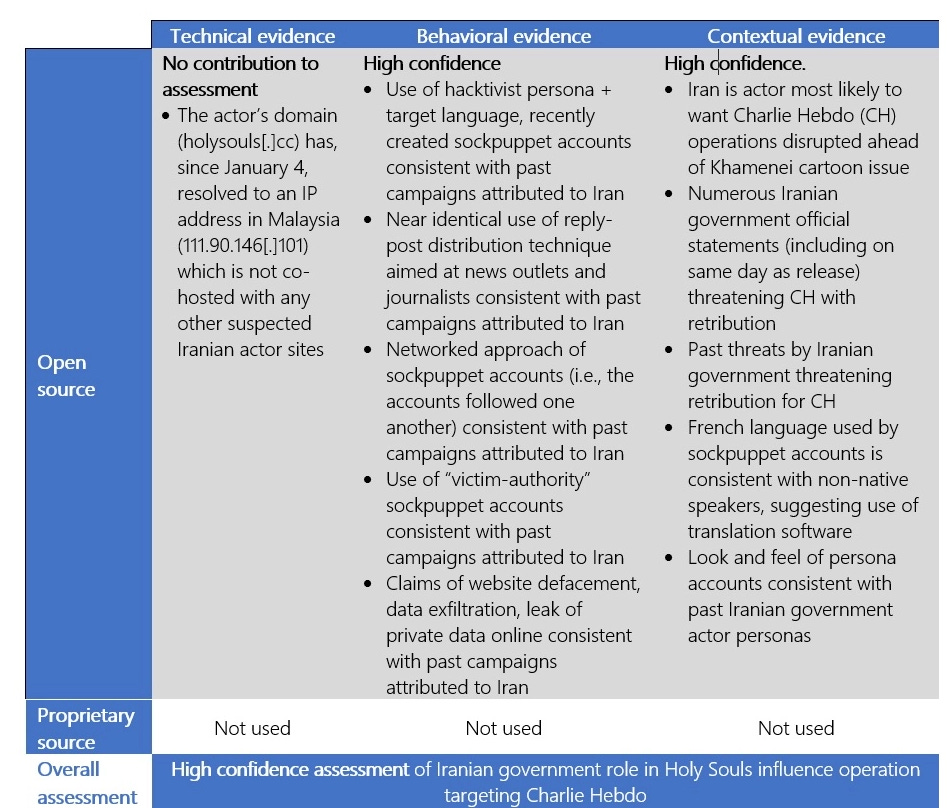
Iran influence operation: Microsoft says that a hacking group named Holy Souls that hacked and stole the personal information of more than 230,000 Charlie Hebdo customers in early January this year was actually working on behalf of the Iranian government. Microsoft says it tracks this group internally under the codename of NEPTUNIUM, but they are more widely known as Emennet Pasargad [PDF], a hacking group that tried to meddle in the 2020 US Presidential Election. Microsoft says it believes that Emennet Pasargad hacked Charlie Hebdo after the French satirical magazine launched an international competition in December 2022 to produce caricatures of Iran's Supreme Leader Ali Khamenei for his brutal crackdown against the Iran protests.
Vulnerabilities and bug bounty
Docmosis vulnerability: Security researcher Frycos has a write-up on a vulnerability he discovered in PDF and Word file generator Docmosis. One of the systems he found to be vulnerable to this vulnerability was the UN's Docmosis server. The vulnerability was fixed, and patches are out.
Gladinet CentreStack vulnerability: White Oak Security has published details on a vulnerability in the Gladinet CentreStack file-sharing server. The vulnerability is an authentication bypass and an arbitrary file upload resulting in remote code execution.
CVE-2022-44645 (Apache Linkis): Numen Cyber Labs has published an analysis and PoC code for CVE-2022-44645, a deserialization vulnerability with possible remote code execution impact in the Apache Linkis database middleware project. A patch was released at the end of January.
CVE-2023-21608 (Adobe Acrobat Reader): HackSys researchers have published a detailed write-up and PoC code for CVE-2023-21608, an EoP vulnerability in the Adobe Acrobat Reader app, patched in January 2023.
CVE-2022-47986 (IBM Aspera Faspex): Security firm AssetNote has published details about CVE-2022-47986, a pre-auth RCE in IBM's Aspera Faspex file-exchange application.
Infosec industry
New tool—PipeViewer: Cybersecurity firm CyberArk has open-sourced a new tool called PipeViewer that shows detailed information about named pipes in Windows. CyberArk researchers created the tool as part of their work in discovering CVE-2022-25365, a privilege escalation in the Docker Desktop for Windows tool.
New tool—NETWIRE configuration extractor: Elastic's security team has released a new tool that can extract information from the encrypted config file of the Netwire RAT.
Jigsaw layoffs: Google has laid off roughly 60% of Jigsaw worforce, the company's cybersecurity division that creates and runs services to protect civil society from cyberattacks and surveillance. The layoffs were part of Google's larger layoff wave that hit 6% of the tech giant's workforce. According to Forbes, Jigsaw has been reduced from 50 to around 20 employees. Jigsaw is behind tools like Project Shield, which provides DDoS protection to small news outlets and activist groups, and the Outline VPN open-source server.
Free course: Cambridge Professor of Security Engineering Ross Anderson plans to upgrade a free course he published back in 2015 on the economics of cybersecurity. The new course is expected to be ready by May this year and will be hosted by Cambridge University. The old one still remains hosted by Delft University. (via The Grugq, whose newsletter has been scientifically proven to increase your cyber intelligence by up to 33.333%. That's almost a third!)
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




