Risky Biz News: Ransomware attacks increase hospital mortality rates
In other news: Europol takes down ~600 Cobalt Strike servers; new Kirin BGP attack; ransomware gang apologizes to Indonesian government and gives out free decryption key.

This newsletter is brought to you by Rad Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

A whitepaper published last year by academics from the University of Minnesota's medical school has looked at the aftermath of ransomware attacks on US hospitals and found evidence to suggest that mortality rates typically increase by around 20%.
The study looked at hospital admissions before, during, and after a ransomware attack, at the hospital's profits, and reported patient deaths.
Researchers said the most affected category were patients who were already hospitalized at the time of the ransomware attack, compared to patients who were admitted after, where hospital staff could adjust procedures to take into account for unavailable IT systems.
The study—although not peer-reviewed—has finally put some estimated numbers on a topic that has been at the heart of many conversations in the infosec community.
Cybersecurity experts have sometimes too eagerly chased the storyline that a "ransomware attack has killed people," sometimes without proper evidence and even jumping to conclusions.
In hindsight, pinning one person's death on a ransomware attack is somewhat of a ridiculous concept. Unless the ransomware has encrypted a defibrillator, direct blame can never be proven or directly assigned.
As the research team wrote in an article about their paper for healthcare news outlet STAT last year, the outcomes of ransomware attacks are similar to other types of incidents, such as natural disasters and pandemics, which impact hospital productivity and time of response, delivering degraded care that increases mortality rates for patients who would have normally survived.
"It's not hard to imagine how a ransomware attack translates into harm for patients. Without access to the EHR, a care team might not know what medications a patient is on or what they’re allergic to. Without imaging, clinicians are flying blind as they make diagnoses. When lab results have to be hand-delivered (instead of uploaded to a patient’s chart), treatment is delayed. Without electronic monitoring equipment, nursing staff might not be able to monitor patients’ condition without physically being in the room. If an ER has to activate ambulance diversion protocols, patients may spend precious time traveling to an alternative facility before they receive care for time-sensitive conditions. This is especially concerning for urgent conditions like heart attack and stroke, where time to treatment has well-documented implications for survival."
According to the paper, mortality rates were even higher for patients at hospitals experiencing the most severe ransomware attacks (mortality rate increase of 36-55%) and for patients of color (mortality rate increase of 62-73%).
The team adds:
"In normal times, roughly 3 in 100 hospitalized Medicare patients will die in the hospital. During a ransomware attack, that number goes up to 4 out of 100. From 2016 to 2021, we estimate that ransomware attacks killed between 42 and 67 Medicare patients."
It's a rough estimation, but researchers say the numbers are more likely higher if another team would analyze data from patients with other types of health insurance coverage, and not just Medicare.
As Professor Alan Woodward from the University of Surrey points out, the study puts out estimates, but the conclusion to be taken from the research is that the number of deaths caused by ransomware is "greater than 0."
In the discussion section of their paper, the research team hopes their work will be used to drive policy action to reduce the incidence and effects of ransomware attacks on hospitals, such as adopting incident planning playbooks or minimum hospital cybersecurity standards.
Breaches, hacks, and security incidents
Bittensor crypto-heist: A hacker has stolen $8 million worth of assets from blockchain platform Bittensor. The platform suspended transactions shortly after the attack earlier this week. Bittensor says the hack took place after the private key of one of its hot wallets leaked online. Bittensor is a provider of ML-based solutions for cryptocurrency owners. [Additional coverage in CoinDesk]
Roll20 breach: Tabletop gaming platform Roll20 suffered a data breach at the end of last month. The company says that a hacker gained access to one of its admin accounts and stole user data. Roll20 says the hacker did not gain access to password information, but they were able to view the last four digits of user credit card numbers.
FIA breach: The FIA, the Formula 1 government body, has fallen victim to a phishing attack. The federation says attackers gained access to two accounts and stole the personal data of some of its members.
Ethereum breach: A threat actor has gained access to the official mailing list of the Ethereum blockchain project and sent out phishing emails to more than 35,000 users. The incident took place on June 26 and allegedly impacted the project's account on the SendPulse email marketing platform. The phishing email redirected users to a phishing kit specialized in draining cryptocurrency wallets. Ethereum admins say the attacker imported their own email addresses into the mailing list in order to reach more targets through its official domain. Blockchain data suggests no users lost money through in the scam.
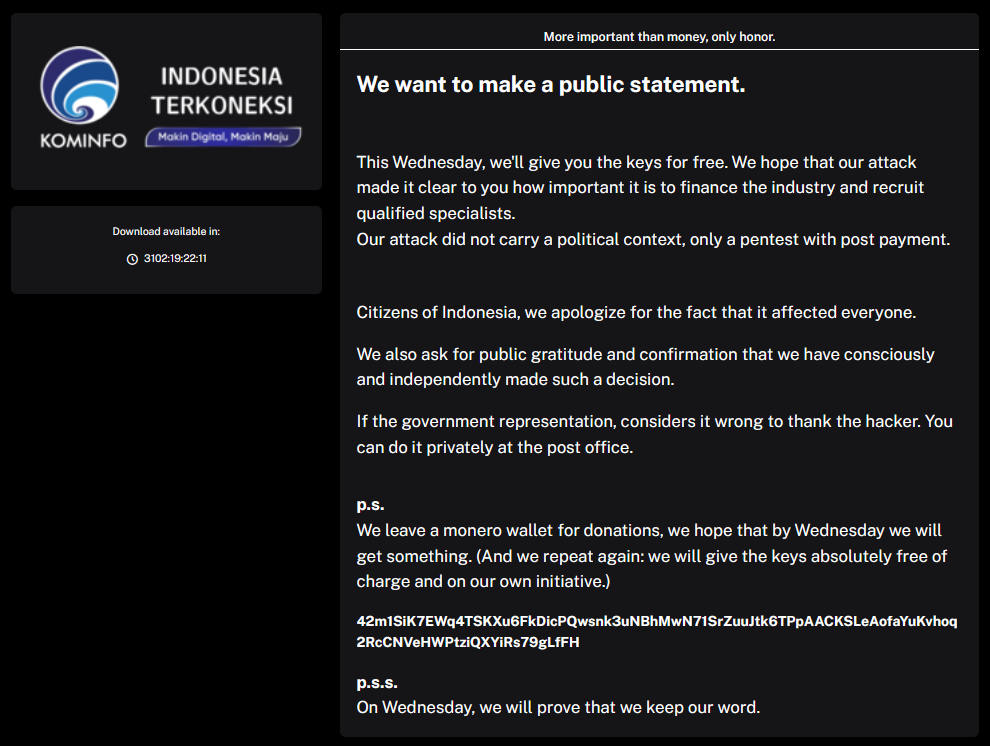
Indonesia ransomware attack update: The group behind a ransomware attack on the Indonesian government's national data center has apologized for their intrusion and promised to provide a free decryption key. Indonesian officials previously stated they would not pay a ransom demand of $8 million. The free decryption key is a godsend for the Indonesian government. Officials previously said they expected to permanently lose most of the encrypted data since it was not backed up anywhere else and was unrecoverable. The government blamed the attack on its "stupidity," and several officials have tendered their resignation following the June 20 attack. [Additional coverage in the ABC]
General tech and privacy
Proton Docs: Proton has launched a so-called "privacy-focused" version of Google Docs.
Entrust drama: Entrust's leadership has promised to fix all the issues that got its certificates booted out of Google Chrome's root store.
Government, politics, and policy
Intellexa sanctions: A CyberScoop report claims that US sanctions on the Intellexa surveillance alliance appear to be working and that activity around the group and its Predator spyware appears to be diminishing.
Russia's VoIP ban: The FSB has ordered Russian telecom providers to block VoIP calls from foreign IP addresses and local web hosting providers. Only VoIP calls originating from major Russian telco networks will be allowed. The order comes as Russian officials are trying to crack down on the rise of telephony-based scams. The schemes involve criminals renting virtual phone numbers to place calls to Russian citizens. [Additional coverage in RBC]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Jimmy Mesta, CTO and Co-Founder of Rad Security (formerly KSOC). Jimmy explains how Rad Security has replaced signature-based detections with a new concept the company calls "behavioral fingerprints" or "verified runtime fingerprints," which can detect malicious activity in cloud environments using a wider set of indicators.

Cybercrime and threat intel
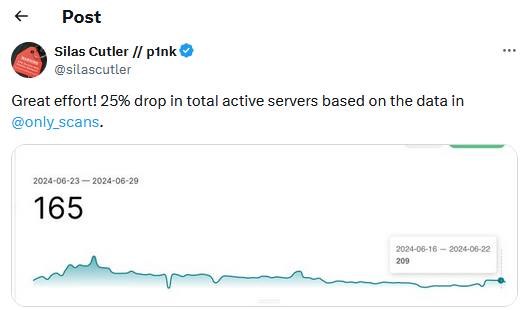
Operation Morpheus: Europol has taken down almost 600 Cobalt Strike servers used by cybercrime groups to control malware operations. Officials say the takedown is the result of a three-year investigation that began in September 2021. Servers were identified and taken down with the help of multiple cybersecurity firms. According to security researcher Silas Cutler, the Europol operation appears to have taken down a quarter of known malicious Cobalt Strike servers.
Student arrested for hacking teacher: South Korean authorities have sentenced a teenager to one year in prison for hacking one of their teachers and leaking answers for an upcoming test. Officials say the teenager and a friend broke into a school staff room and planted malware on the teacher's laptop. The incident took place in 2022. The teen's accomplice was also sentenced to 10 months in prison. [Additional coverage in the Yonhap News Agency]
Vishing squad detained: Spanish and Portuguese authorities arrested 54 individuals suspected of stealing €2.5 million from elderly people using vishing (voice phishing) scams. The group operated by contacting victims via phone and posing as bank employees. They convinced targets to reveal banking credentials or hand over savings to a courier showing up on their doorstep. The stolen money was then laundered through the group's network of bank accounts.
x999xx profile: Cybersecurity reporter Brian Krebs has tracked down a well-known initial access broker to a 30-year-old Russian man from the city of Ozersk. Krebs says that Maxim Kirtsov has been active in hacking forums for almost 15 years under the name of x999xx. The hacker is known for breaching corporate networks and selling access to ransomware gangs. Kirtsov confirmed Krebs' investigation via email.
Polyfill supply chain attack update: Two weeks after the Polyfill supply chain attack was discovered, Censys says that more than 384,000 websites still load code from the polyfill[.]io domain. Some of these sites are associated with Hulu, Mercedes-Benz, and Warner Bros.
New phishing groups: Menlo Security has discovered three new cybercrime groups engaged in complex phishing campaigns targeting the world's top companies. The new LegalQloud group impersonates legal firms and has targeted governments and investment banks in North America. The Eqoop group uses the NakedPages phishing toolkit capable of bypassing MFA, and has primarily targeted executives across ten different industry verticals globally. The last Boomer group uses an advanced custom-made phishing kit and focuses on targets in the government and healthcare sectors.

Malware technical reports
Mekotio: Trend Micro has published new IOCs for Mekotio, a Windows banking trojan that targets Latin America.
GootLoader: Palo Alto Networks has published a report looking at recent GootLoader changes and how to reverse-engineer the malware.
TgRat: DrWeb has published a report on the Linux version of TgRat, a remote access trojan first spotted in 2022 targeting Windows that used Telegram for C&C comms.
Mallox ransomware decryptor: Security firm Uptycs has found a way to retrieve free decryptors from the admin panel of the Mallox RaaS. It's probably gonna be patched now!
Eldorado ransomware: A new ransomware group named Eldorado claims to have hit at least 15 targets in attacks carried out over the past few months. The group launched in March this year and has advertised its services on the dark web. According to security firm Group-IB, Eldorado is one of the 23 ransomware platforms that have posted ads on hacking forums throughout 2022 and 2023. The group claims to have encrypters for Linux and Windows systems, and its code appears to be original and written from scratch. Group-IB says Eldorado is a small operation and seems to be the work of Russian-speaking developers.
Sponsor Section
This week's sponsor, Rad Security, takes a look at how security products have evolved from older signature-based detection technologies to a more modern behavioral-based approach over the past decade.
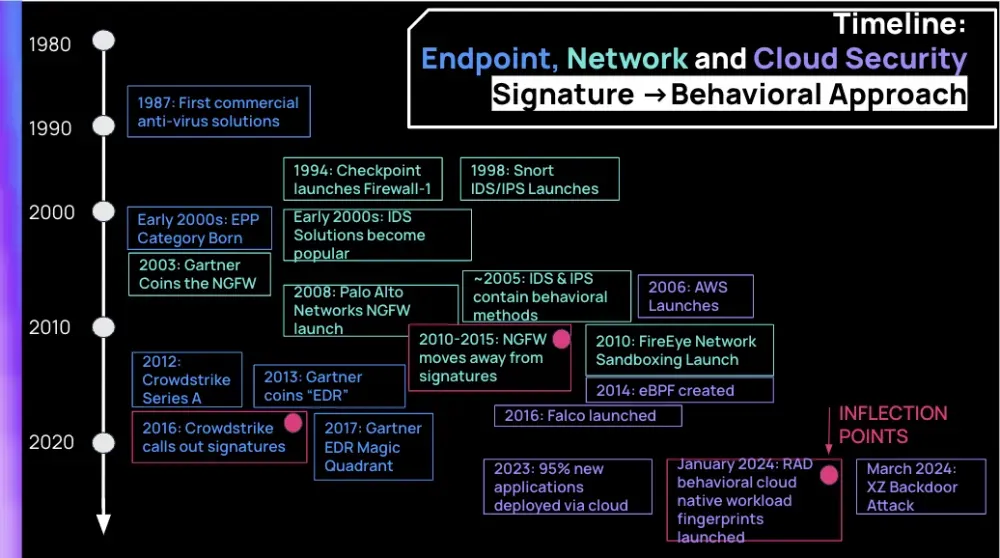
APTs, cyber-espionage, and info-ops
Nothing in this edition.
Vulnerabilities, security research, and bug bounty
Ghostscript vulnerability: Codean's Thomas Rinsma has found a major security flaw (CVE-2024-29510) in the Ghostscript rendering and text processing engine. The bug is a format string vulnerability that can allow attackers to bypass the engine's sandbox and gain code execution capabilities. Rinsma says the vulnerability has a significant impact since modern web apps use Ghostscript to convert or preview office documents. In May, Rinsma found a similar bug in Mozilla's pdf.js PDF rendering engine.
RoguePuppet vulnerability: Security researcher Adnan Khan has found and helped patch a major vulnerability in the Puppet infrastructure-as-code service. The vulnerability could have allowed threat actors to push malicious code to Puppet Modules hosted on the PuppetForge portal. The attack was possible just by creating a pull request in Puppet's official repository, adding malicious API commands, and closing the pull request minutes later. Khan says Puppet's GitHub Actions read the pull request and executed the API commands with no other verifications. Puppet fixed the issue in April this year. The company's services are used by dev teams at some of the world's largest companies.
Xerox WorkCentre vulnerabilities: Positive Technology researcher Arseniy Sharoglazov has found two unauthenticated remote code execution issues that impact Xerox WorkCentre multifunctional printers.
Gogs unpatched vulnerabilities: SonarSource researchers have discovered four vulnerabilities in the Gogs open-source self-hosted Git server. Three of the four vulnerabilities can be used to run malicious code on Gogs servers and hijack private source code repositories. SonarSource says the issues are still unpatched after the project's admins stopped communicating with its researchers. According to Shodan, there are more than 7,400 Gogs servers currently connected to the internet.
WebRTC DoS: Enable Security has found a critical denial-of-service (DoS) vulnerability impacting media servers that support WebRTC and DTLS.
"This vulnerability arises from a race condition between ICE and DTLS traffic and can be exploited to disrupt media sessions, compromising the availability of real-time communication services. Mitigations include filtering packets based on ICE-validated IP and port combinations. The article also indicates safe testing methods and strategies for detecting the attack."
Traeger grill vulnerabilities: Bishop Fox researchers have found a vulnerability in the WiFi controller of Traeger smart cooking grills. The vulnerability could be used to obtain information on every grill registered with the vendor.
Silent 7-Zip patch: The 7-Zip file archiving software has shipped a silent patch in its beta version to fix two vulnerabilities discovered by security researcher Maxim Suhanov.
Rejetto HFS exploitation: Security firm AhnLab has discovered attacks against Rejetto web file servers. The attacks are exploiting a vulnerability (CVE-2024-23692) patched at the end of May. The bug allows attackers to inject malicious HTML templates into Rejetto and run malicious code to hijack the server. AhnLab says the bug is being exploited to drop crypto-miners, backdoors, and infostealers. According to Arseniy Sharoglazov, the researcher who initially found the bug, there are more than 2.3 million Rejetto servers connected to the internet, most running on Windows.
Kirin BGP attack: A team of security researchers has put together a new attack that can flood routers with large BGP announcements and crash entire networks. The new attack is named Kirin, and its name stands for Killing Internet Routers in IPv6 Networks. As the name explains, Kirin takes advantage of the new IPv6 protocol to create oversized BGP route announcements. Researchers say these announcements can be timed in coordinated attacks to exhaust router memory. Tests showed a Kirin attack would only cost threat actors less than €500 to rent out attack infrastructure.
Infosec industry
New tool—EDRPrison: Security firm 3Nails Infosec has released EDRPrison, a driver to prevent EDR agents from sending telemetry back home.
New tool—CSPT: Security firm Doyensec has released CSPT, a new Burp extension to find and exploit Client-Side Path Traversal vulnerabilities.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about why governments have failed to protect the private sector from state-backed cyber espionage.
In this podcast, Tom Uren and Patrick Gray talk about how South Korean internet regulations inadvertently encouraged a large ISP to hack their own customers to cut down on torrent traffic.
Abhishek Agrawal is the CEO and co-founder of Material Security, an email security company that locks down cloud email archives. Attackers have been raiding mailspools since hacking has existed, and with those mailspools now in the cloud with services like o365 and Google Workspace, guess where the attackers are going?




