Risky Biz News: Pro-Russian hacktivists offer cryptocurrency for DDOS attacks on Ukraine and western targets
In other news: Bangladesh government bought loads of Israeli surveillance tools; npm libraries delete user files; malware found preinstalled on T95 Android TV boxes.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
A pro-Russian hacktivist group going by the name of NoName057(16) has carried out DDOS attacks against Ukrainian entities, NATO countries, and anyone who they deem as "anti-Russian."
The group emerged in March 2022, shortly after Russia's invasion of Ukraine, and according to early reports, they appear to have created a custom botnet named Bobik to launch their DDOS attacks.
Its initial DDOS activity was hit-and-miss and typically went under the radar, but NoName got more attention last fall after they launched DDosia, a project through which they offered to pay volunteers to download their DDosia app and participate in DDOS attacks against their targets.
Throughout the past year, the group has targeted countries and private companies that showed any kind of public support for Ukraine and its fight against Russia's invasion.
For example, the group targeted Finnish government websites shortly after the country announced its intention to join NATO and Lithuanian railways shortly after they blocked Russian goods transiting to Russia's Kaliningrad exclave.
Other targets included Ukrainian newspapers and schools, and entities across Norway, Estonia, and Poland.
According to reports published this week by Avast and SentinelOne, their more recent attacks targeted the websites of the Polish government in late December last year, Danish banks earlier this week, and the websites of 2023 Czech presidential election candidates, attacks that are still ongoing.
NoName057(16) joins the ranks of KillNet and XakNet as one of today's most active pro-Russian hacktivists groups, although its classification as a "hacktivist group" remains in question, especially after previous reports have drawn connections between KillNet and XakNet activity and past Russia's intelligence services.
Currently, the group continues to orchestrate new attacks via their Telegram channel after being kicked off GitHub in mid-December.
Breaches and hacks
Royal Mail cyber incident: The Royal Mail postal and courier service halted international shipping services on Wednesday following a severe IT disruption that the company says was caused by a "cyber incident." No details were provided about the nature of the attack, and Royal Mail has asked customers to stop sending letters and parcels to overseas destinations until it resolves the issue. Internal UK shipping was not affected, the company said.
Twitter denies breach: After almost three weeks of radio silence, Twitter has finally addressed rumors of two recent data breaches. The company says that claims that threat actors had collected details of 400 million users and then leaked details for 235 million did not live up to reality and that they found "no evidence" that the information being sold and leaked online was the result of threat actors exploiting its systems. Instead, Twitter says the data is "likely a collection of data already publicly available online through different sources" and not something that originated from its own systems. HudsonRock researcher Alon Gal, who discovered both breaches, responded to Twitter's statement claiming they stand by their assessment that the leaked data contained non-public information.
Japan insurance companies leak: A threat actor has breached a US company that provides IT services for two Japanese insurance providers and has stolen the personal details of more than two million Japanese citizens. The incident was discovered earlier this week after the threat actor posted the stolen data online. According to Japanese media, affected insurance companies include Aflac and Zurich. Aflac says the information of 1.32 million cancer insurance policyholders was stolen, while Zurich says more than 750,000 automobile insurance policyholders had their data leaked online.
SweepWizard leak: SweepWizard, an app used by US law enforcement to coordinate multi-agency raids, exposed the exact location of upcoming raids along with sensitive details about both suspects and police officers alike. According to tech news outlet Wired, data on 200 raids, 5,700 suspects, and hundreds of police officers, mainly from California, leaked via the app. Since the leak, ODIN, the company behind SweepWizard, has taken down the app's website and iOS and Android store listings.
"Ken Munro, an ethical hacker and founder of the UK-based security research firm Pen Test Partners, says that based on how we described being able to access SweepWizard data, the error was likely caused by a simple authorization oversight. While SweepWizard was taken down before he had a chance to examine the app, Munro says that, typically, when an individual logs in to a website or app, they are assigned an access token that gets checked by the app every time their device requests data from it. According to Munro, SweepWizard was likely not checking each request for these access tokens and was simply providing data to any device that asked."
General tech and privacy
TikTok fine: France's privacy watchdog CNIL has fined Chinese social media network TikTok €5 million for not offering users a way to refuse tracking cookies on their official website.
Rust coming to Chromium: Google's Chrome security team has published a clear guideline on how they plan to integrate more Rust code into the Chromium open-source web browser project. The move comes after Rust also began playing a more important role in Firefox, Windows, Linux, and Android.
Government, politics, and policy
Spyware in Bangladesh: The Bangladesh government has bought spyware and surveillance tools from four Israeli companies using intermediaries in Cyprus, Singapore, and Switzerland. According to Israeli newspaper Haaretz, the buyers included the country's Interior Ministry, internal security agency, and armed forces. The tools, which included systems to monitor and intercept mobile and internet traffic and were worth almost $13 million, were bought through intermediaries because Bangladesh is one of 28 countries that don't recognize Israel as a state. [Haaretz/non-paywalled link]
- Passitora: Mobile phone interception system worth $5.7 million.
- Prelysis: WiFi interception system worth $3 million.
- U-TX Technologies: "Web Intelligence" system and a cellular tracking system worth $2.5 million.
- Coralco Tech: Active mobile phones monitoring system worth $1.6 million.
US to investigate its own use of NSO tools: The US House Intelligence Committee has sent out letters to several government agencies and inquired about their use of foreign-made spyware. [More in the NYT]
Ransomware down in France: French officials say they opened 420 cases related to ransomware attacks in 2022, a number that went down from 496 investigations started a year before in 2021, the Paris prosecutor's office told ZDNet France. In an episode of the Gatewatcher podcast, magistrate Johanna Brousse, the head of the cyber unit of the Paris public prosecutor's office, noted the pivotal nature of 2020, when her unit saw an "explosion of cybercrime cases," going from 65 in 2019 to 409 that year.
iPhones approved in South Korea for govt use: South Korea's National Intelligence Service says that iPhone, iPad, and Apple Watch devices have passed security requirements and are now allowed to be used on government networks. The move comes after Apple updated its MDM software to include new security features that previously prevented NIS from giving Apple devices the go-ahead. The agency said it plans to publish a technical guide on how government IT staff can set up their MDMs servers for correct enrollment of Apple devices.
Sponsor section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Pig butchering call centers: Europol says that together with law enforcement from Bulgaria, Cyprus, Germany, and Serbia, they've cracked down on multiple call centers that engaged in pig butchering scams, tricking social media users into depositing cryptocurrency as part of fraudulent investment schemes. Authorities estimated losses in this scheme at around €2 million.
Scattered Spider: A financially-motivated hacking group known as Scattered Spider has been spotted installing old Intel networking drivers on compromised systems in order to exploit bugs in the old code and elevate privileges and avoid EDR solutions. The new attacks were spotted by security firm Crowdstrike, the same company that discovered the group's existence last year after Scattered Spider hit several telcos in order to use their infrastructure to carry out SIM-swapping attacks and bypass MFA.
npm library deletes user files: Researchers at Mend and Checkmarx say they discovered several npm packages created to work as dependencies and modules for the Vue Admin Better project that will delete sensitive folders on users' devices if they use a pirated version of the project. Researchers say they found eight libraries and modules that contain code that will delete directories that store a developer's source code, npm modules, and configuration settings for Git, Subversion, and Visual Studio environments. The destructive behavior does not trigger if users use an open-sourced version of the same project but only if users pirated a version of the commercial version of Vue Admin Better. The project's author justified the presence of the destructive code in the eight packages via a statement posted on GitHub, where they explained that they were merely trying to fight back against the illegal use of their software after someone leaked the full version of the Vue Admin Better project on GitHub without their approval.
KEV update: CISA has updated its KEV database with two new vulnerabilities that are currently being actively exploited. The two are both Windows vulnerabilities. The first is CVE-2023-21674, a zero-day that Microsoft patched earlier this year in this month's Patch Tuesday, and the second is CVE-2022-41080, an Exchange vulnerability patched in November, also known as OWASSRF, and the vulnerability used to breach and deploy ransomware on the infrastructure of cloud hosting giant Rackspace late last year.
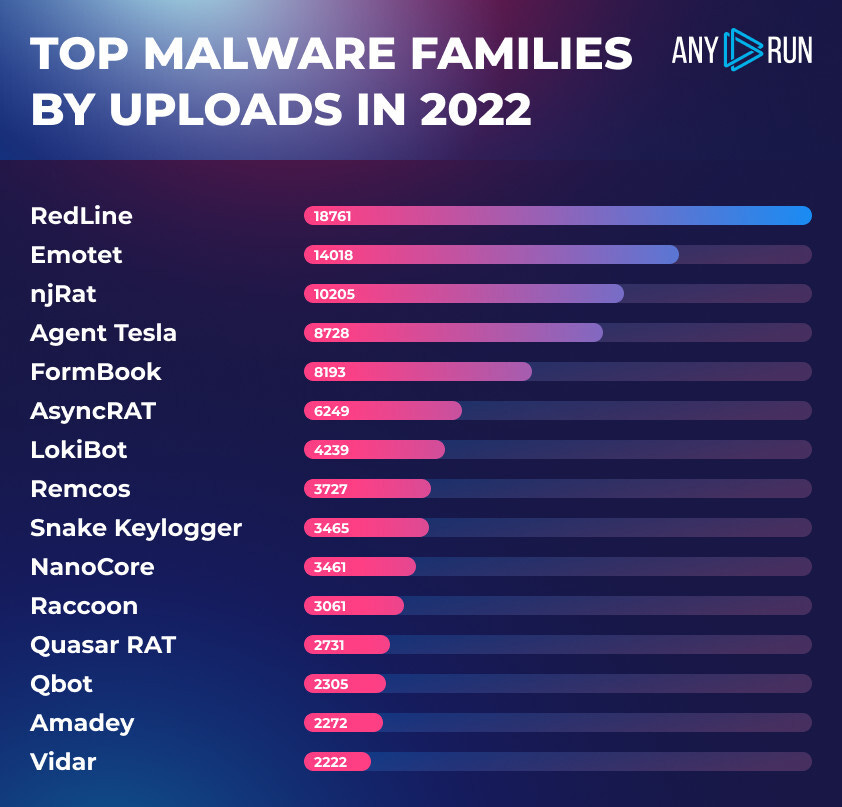
RedLine was king in 2022: Malware analysis service ANY.RUN says that the RedLine infostealer was the most popular malware family uploaded on its platform last year, followed by the likes of Emotet, njRAT, and Agent Tesla.
Malware technical reports
Malware on Android TV boxes: Daniel Milisic, an IT engineer from Toronto, Canada, has found that some models of T95 Allwinner Android-based TV boxes come preinstalled with malware. While Milisic was not able to analyze the malware in great depth, the researcher says the malicious code resembles an older threat named CopyCat that was first spotted in 2017 and is known to root devices and hijack them in adware-like schemes. Milisic has published removal instructions for any affected users in this GitHub repo.
Gootkit Loader: Trend Micro has a report out on recent Gootkit Loader campaigns that have leveraged poisoned search engine results to redirect users to a website peddling a malicious VLC player download that infects users with the group's malware.
NeedleDropper: Antivirus maker Avast has discovered a new malware dropper strain named NeedleDropper that appears to have been used in the wild since at least October 2022. Avast says the malware is being sold on underground hacking forums via a classic MaaS offering. Experts anticipate seeing more detections of this new threat as the tool gains popularity.
Hive ransomware: Rapid7 researchers have a technical report looking at the Hive ransomware and its use of EDR bypass techniques.
IcedID: Cybereason researchers have broken down a recent killchain used by the IcedID trojan, also known as BokBot.
APTs and cyber-espionage
EyeSpy: Bitdefender researchers have discovered a malware campaign that uses trojanized installers for Iran-based VPN service 20Speed to infect Iranian users with SecondEye, a legitimate monitoring application. The campaign, which Bitdefender attributed to the EyeSpy group, started in May 2022 and continued throughout the year, with detections peaking in August and September.
GroupA21: Researchers from cybersecurity Weibu have published a report on GroupA21, an India-based APT group also known as BabyElephant. The company has studied its recent operations and concluded that the group often imitates SideWinder, another suspected Indian APT.
Lazarus APT: Chinese security firm Qihoo 360 has published a report on recent attacks carried out by the Lazarus APT group (aka APT-C-26). The campaign was a spear-phishing operation that used cryptocurrency wallet promotions to deliver malicious ISO files that tried to install the NukeSped backdoor.
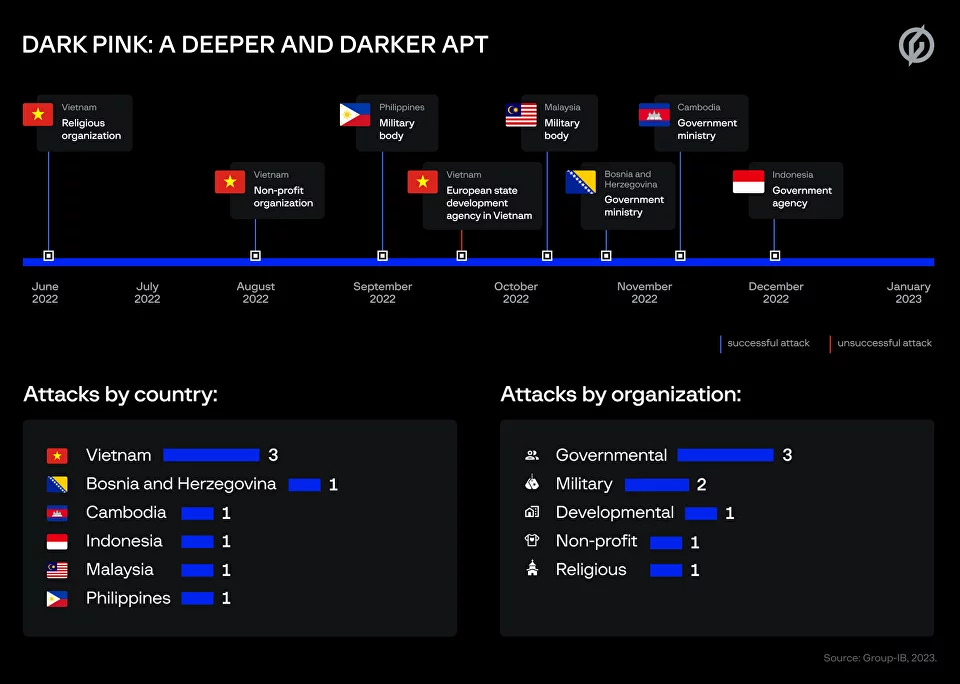
Dark Pink APT: Security researchers from Group-IB have discovered a new APT group named Dark Pink that appears to have begun operations in mid-2021 and intensified attacks in mid-to-late 2022. Researchers say the group focuses on espionage activities and has hit at least seven targets based on the evidence they discovered. Confirmed victims include two military bodies in the Philippines and Malaysia, government agencies in Cambodia, Indonesia, and Bosnia and Herzegovina, and a religious organization in Vietnam. Group-IB says Dark Pink is what Anheng researchers documented earlier this month in their report as the Saaiwc Group.
Vulnerabilities and bug bounty
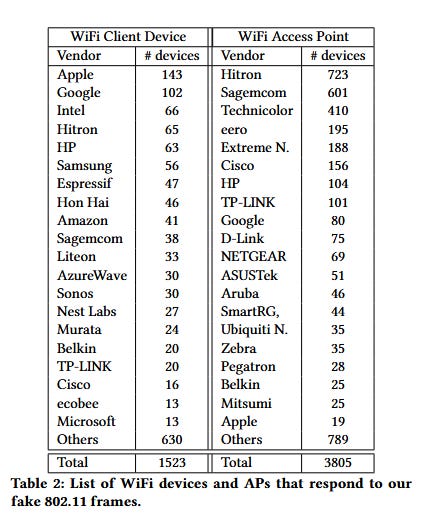
New WiFi attack: Academics from universities in Canada and the US have found a new way to attack WiFi devices and trick them into draining their own batteries. Researchers say the attack works because many WiFi devices will respond to certain packets from devices that are not on their own networks. If these packets are crafted in a certain manner, they can keep a device awake and force it to use its battery power until the device shuts down—a situation that may lead to security breaches when the device is used for surveillance purposes, such as security cameras.
"Our evaluation of over 5,000 devices from 186 vendors confirms that these are widespread issues. We believe these loopholes cannot be prevented, and hence they create privacy and security concerns. Finally, to show the importance of these issues and their consequences, we implement and demonstrate two attacks where an adversary performs battery drain and WiFi sensing attacks just using a tiny WiFi module which costs less than ten dollars."
Fortinet zero-day: Fortinet has published an analysis of CVE-2022-42475, an unauthenticated RCE in the FortiOS operating system that runs on the company's SSL-VPN devices and which was exploited as a zero-day last year in December. The zero-day was first spotted exploited in the wild by French security firm Olympe, and some reports claimed it was also used to deploy ransomware. However, following its investigation, Fortinet says the vulnerability was also used to go after "government-related targets" in what appears to be the work of an "advanced actor." The company hinted in its conclusion at the possibility that the zero-day might have been the work of a Chinese APT, known for their love of networking gear zero-days.
"The discovered Windows sample attributed to the attacker displayed artifacts of having been compiled on a machine in the UTC+8 timezone, which includes Australia, China, Russia, Singapore, and other Eastern Asian countries. The self-signed certificates created by the attackers were all created between 3 and 8 AM UTC. However, it is difficult to draw any conclusions from this given hackers do not necessarily operate during office hours and will often operate during victim office hours to help obfuscate their activity with general network traffic."
CVE-2022-46169: SonarSource researchers have published a detailed write-up on CVE-2022-46169, an unauth RCE in Cacti, an open-source, web-based monitoring solution. The bug, which received a 9.8/10 severity score, was patched on the same day it was discovered last month. The vulnerability came under active attacks last week. Censys says there are roughly 6,400 Cacti servers currently available over the internet, many of which may be vulnerable.
CVE-2022-43473: Chinese security researcher Da22lec has published a technical analysis of CVE-2022-43473, an XXE vulnerability that Zoho patched in its ManageEngine system at the end of last year.
CVE-2022-41034: Uptycs researchers have a technical analysis of CVE-2022-41034, an RCE vulnerability in Visual Studio Code that Microsoft patched last October.
CVE-2022-44877: Security firm CloudSEK has a technical analysis of CVE-2022-44877, an unauth RCE in the Centos Web Panel 7, a popular utility used by web hosting companies. Security firms Greynoise and the Shadowserver Foundation said the vulnerability has come under exploitation after proof-of-concept code was published online last week.
CVE-2022-20452: Proof-of-concept code and an in-depth analysis were published this week on GitHub for CVE-2022-20452, a privilege escalation vulnerability in the Android OS that can allow locally installed apps to gain SYSTEM access. The vulnerability was patched in the Android OS in November of last year.
MacDirtyCow: Proof-of-concept code for both macOS and iOS has been released for MacDirtyCow, a Mac version of the DirtyCow Linux exploit. The vulnerability can be used to get root on macOS and jailbreak iOS devices. Apple patched MacDirtyCow, also known as CVE-2022-46689, in mid-December 2022.
SymStealer: Imperva researchers have published details about SymStealer (CVE-2022-3656), a vulnerability in Chromium-based browsers that was patched last October and which researchers say can be used to extract sensitive files from affected browsers, such as crypto wallets and cloud provider credentials.
Cisco security updates: Cisco published 12 security updates on Wednesday.
TikTok 2FA bypass: TikTok has fixed a 2FA bypass in its web and Android app that would have allowed any threat actor who had a user's correct password to bypass 2FA challenges. A threat actor could have exploited this issue by repeatedly logging into a TikTok account until the 2FA challenges stopped appearing. The researcher was awarded $1,000 for their finding.
Pwn2Own Vancouver 2023 rules: ZDI has published the program for the 2023 edition of the Pwn2Own hacking contest. The spring edition of the contest focuses on hacking products in categories such as desktop software, servers, enterprise products, and smart cars. The top reward at this year's edition is a $600,000 bounty for anyone who manages to successfully hack a Tesla Model 3 or Model S, either via Bluetooth, WiFi, their tuner, or modem. Other top awards include $200,000 rewards for hacking the ICS BIND DNS software suite, Windows Exchange email servers, or the Windows RDP service.
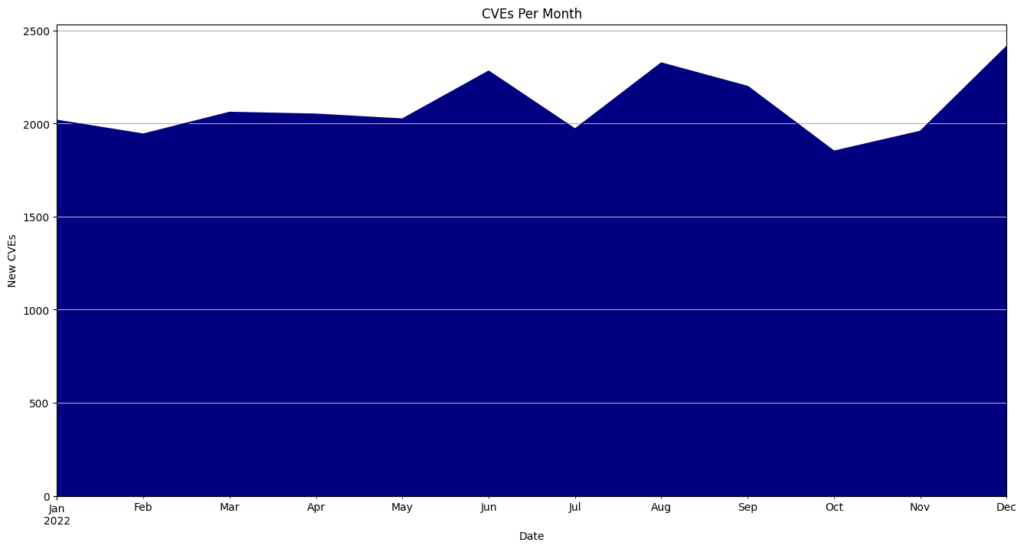
CVEs in 2022: Security researcher Jerry Gamblin has a statistical view of all the CVEs published in 2022, which saw 25,093 reported vulnerabilities, a 24.51% increase over 2021, and the highest number for a year so far.
Infosec industry
PHDays 2022: In an article for Brookings think tank, Atlantic Council's Justin Sherman has analyzed the impact of Russia's invasion of Ukraine on Positive Hack Days (PHDays), the country's largest cybersecurity conference. PHDays saw its largest attendance since its first edition back in 2011, but the topics of the day were dominated by the war, political speech, and discussions on Russia's tech isolation.
Tool update—TriOp: Security researcher Jan Kopriva has updated his TriOp tool this week to allow it to use Shodan to discover devices that may be exposed to attacks via vulnerabilities listed in CISA's KEV database.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




