Risky Biz News: Prigozhin troll farms in limbo following Wagner mutiny
In other news: Free decrypter released for Akira ransomware victims; Russian satellite operator DoZoR will need up to two weeks to recover from cyberattack; and Japan scolds Fujitsu over 2022 hack.
This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Several Russia-based news outlets are reporting that Yevgeny Prigozhin is shutting down his Patriot media company in the aftermath of his failed mutiny at the head of the Wagner PMC last month.
The Patriot media group is a holding company for a dozen of Russian-language propaganda and fake news sites, such as RIA FAN, Politika Segodnya (Politics Today), Ekonomika Segodnya (Economics Today), Nevskiye Novosti (Nevsky News), and Narodnye Novosti (People's News). It is also the holding company for the Internet Research Agency—Russia's infamous "troll farm" linked to multiple instances of election interference across the world.
Prigozhin has allegedly fired all employees and plans to shut down all news sites. All this information comes from Patriot media group insiders, and Prigozhin has not made a formal statement or has been seen or heard from since leaving Russia for Belarus.
News of the Patriot group's collapse is not surprising and was to be expected in light of Prigozhin's mutiny last month.
Russian telecommunications watchdog Roskomnadzor has been blocking access to all Patriot news sites inside Russia since the day of Prigozhin's Wagner rebellion on June 23.
There have also been reports that police forces raided some of Patriot's Sankt Petersburg offices on the same day.
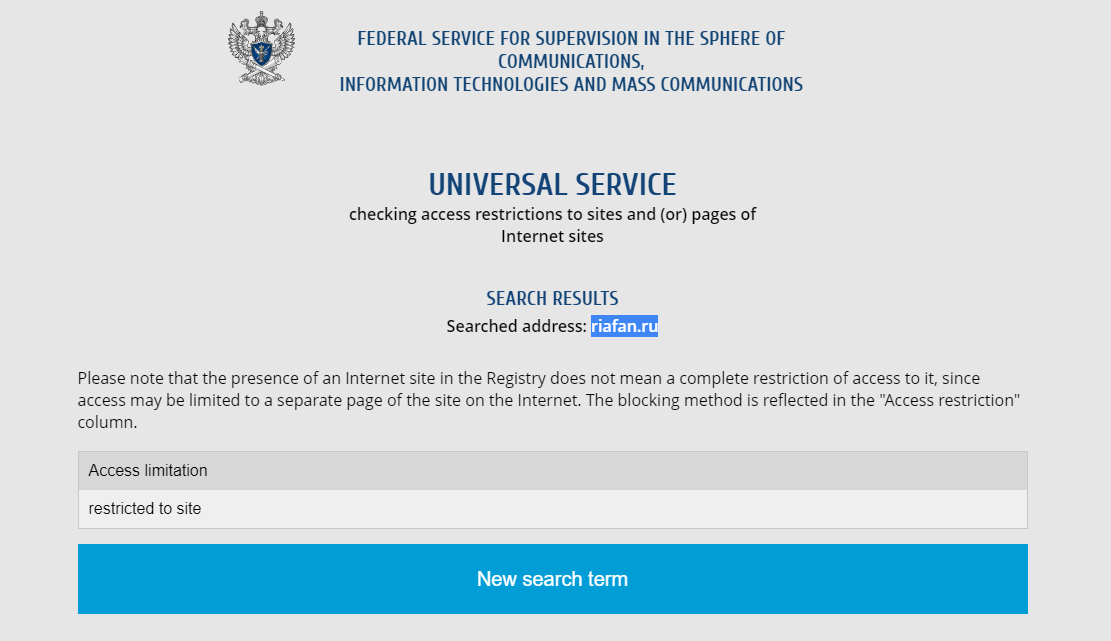
Rumors also emerged the group might change ownership, with Yury Kovalchuk, the owner of the National Media Group (NMG), being the favorite to take over the Patriot group.
Despite the shutdowns, a change of ownership might very well happen since all it takes is moving some domains from one DNS to another. The Russian government will surely not give up on a program that has been so incredibly successful. If assets are moved to a new media group or if a new organization is built from the ground is irrelevant. Regardless, at this point, it is safe to say Prigozhin's time as the head of Russia's propaganda machine is 100% over.
Prigozhin was previously charged in 2018 in the US for his role in running the Internet Research Agency and meddling in the 2016 US Presidential Election. He initially denied any association with the IRA but admitted and later gloated about the organization's success after Russia's invasion of Ukraine.
Back in March 2023, a consortium of investigative journalists published an analysis of the Wagner Leaks, a collection of files stolen from Prigozhin's many public companies. The leaks covered the Wagner PMC, the IRA, and the Concord group of consulting companies.
Breaches, hacks, and security incidents
TSMC denies ransomware attack: Taiwanese chipmaker TSMC has denied suffering a ransomware attack after the LockBit gang listed the company on its dark web leak site. The company says LockBit hit one of its suppliers, and its IT network is safe. LockBit had asked for a $70 million ransom payment. That's definitely not gonna happen any time soon. [Additional coverage in SecurityWeek]
DoZoR confirms hack: Russian satellite communications operator DoZoR-Teleport has confirmed a destructive cyber-attack that hit its systems last week. The company says the incident impacted infrastructure hosted with one of its cloud service providers, but did not name the operator. Dozor-Teleport general director Alexander Anosov says it may take up to two weeks to restore affected services. The company provides satellite connectivity to some of Russia's largest organizations, such as Gazprom, Rosatom, the FSB, and Moscow's regional government.
Japan scolds Fujitsu: The Japanese government has publicly criticized Fujitsu for failing to detect a data breach for more than eight months. The incident impacted the company's FENICS service, a cloud platform used by the Japanese private sector and government agencies. The platform was compromised in March 2022 after attackers discovered a misconfiguration in some of its services. It took Fujitsu months to spot the intruder's backdoors, with the company disclosing the breach in December. Japanese officials believe the hack was the work of Chinese state-sponsored hackers, making it the third time they targeted a Fujitsu product over the last two years. [Additional coverage in Nikkei]
Huobi incident: Huobi, one of the world's largest cryptocurrency exchanges, quietly fixed a major security breach that could have granted an attacker access to the company's cloud infrastructure. Researchers say the company leaked a set of AWS credentials that could have allowed an attacker to gain write privileges to all of their S3 buckets. Now, that's quite the fail!
"An attacker exploiting Huobi's mistakes would have had the opportunity to carry out the largest crypto theft in history. The company has previously reported handling over a billion dollars a day in trading volume."
USAA incident: The United Services Automobile Association has disclosed a security breach caused by an employee sharing their USAA credentials with a third party. USAA says the breach lasted between December 20, 2022, and May 18, 2023 [See data breach notification letter here/PDF].
Poly Network crypto-heist: A threat actor has stolen $4.39 million worth of crypto-assets from cross-chain platform PolyNetwork. The company has suspended operations in the aftermath of the recent attack. This marks the second time the platform has been hacked. It previously lost $610 million worth of crypto-assets in August 2021 in one of the biggest crypto-heists of all time. [Additional coverage in CoinDesk]
General tech and privacy
Twitter implosion (part 48,109): Twitter has announced it will limit the number of tweets users see per day to only 1,000 for normal users and 10,000 for Blue accounts. The move comes after the site also auth-walled its entire website, blocking access to its content to non-registered users, and also crippling its TweetDeck app. Its CEO says the site is experiencing dAtA sCrApInG & sYsTeM mAnIpUlAtIoN. It's not, and he's lying as usual. They self-DDoSed themselves. Guess that happens when you fire all your engineers before Christmas for not going hArDc0r3eEE3EEE.
Mozilla's warning about France's dumb bill: Mozilla is sounding the alarm about a new French bill that would force browsers to implement a blocklist in their code to allow the French government to block certain websites for French users.
Gmail CSE: Google has published a deep dive into its new Gmail client-side encryption mechanism.
Chrome security update: Google patched four security updates in Chrome last week.
Chrome supports post-quantum key exchanges: Chrome 115 beta now supports post-quantum key exchanges for post-quantum secure communications. The feature is hidden behind the "TLS 1.3 hybridized Kyber support" Chrome flag.
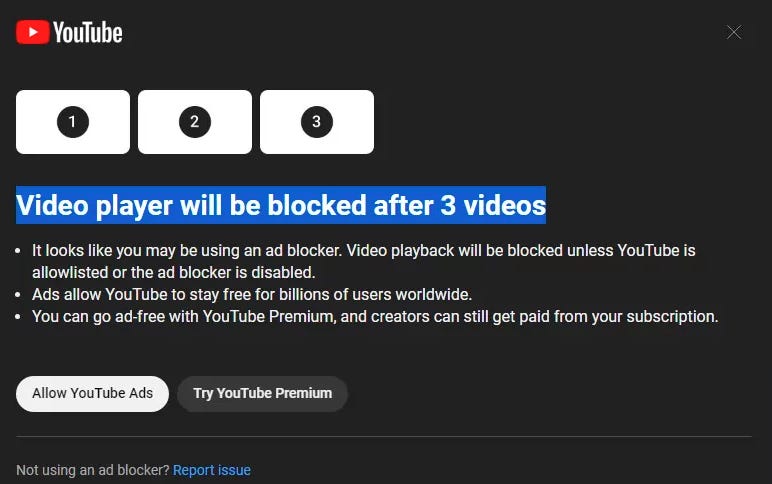
YouTube ad-blocking experiment: YouTube is testing a new feature that will block users who use an ad-block from viewing more than 3 videos on the site unless they disable their ad blockers so they can be bombarded with low-quality ads.
Government, politics, and policy
New Election Security Team head: CISA has appointed US Army veteran Cait Conley as the new head of its Election Security Team. Prior to her appointment, Conley served as Senior Advisor to CISA Director Jen Easterly. She also previously served as the Executive Director of the bipartisan Defending Digital Democracy Project, based out of Harvard University's Belfer Center.
FBI swatting database: The FBI has formed a national online database to facilitate information sharing between police departments and law enforcement agencies across the country relating to swatting incidents. The database was set up in May and is already used by hundreds of PDs and law enforcement agencies. [Additional coverage in NBC News]
UK NCSC first-ever APT response: The UK National Cyber Security Centre (NCSC) says the first-ever state-sponsored cyber-attack that targeted the UK government took place 20 years ago, in June 2003. The agency didn't reveal who was behind the attack but says the operation was a phishing campaign carried out by a foreign state. The incident was investigated by the Communications-Electronics Security Group of the GCHQ and is what eventually led the UK government to form a dedicated cybersecurity arm within the agency years later.
Danish gaming police: The Danish police force is running a special unit tasked with investigating crimes taking place in online gaming communities. The 10-strong unit was established in April 2022 after reports of criminal activity related to video games increased following the COVID-19 lockdown. The unit is currently active in games like Counter-Strike, FIFA, and Fortnite. Officials say they've already opened and are investigating 65 cases related to the sexual grooming of children, online harassment, and online scams. [Additional coverage in Yahoo News]
Sponsor section
This week’s sponsor is RunZero. In this Risky Business News sponsor interview Tom Uren talks to RunZero’s CEO Chris Kirsch about how the company has evolved from offering an active scanning product to one that can now discover assets on OT and cloud environments using both active and passive scanning approaches:
Cybercrime and threat intel
Singapore arrests: Authorities in Singapore have detained 13 suspects for their suspected involvement in a banking-related malware operation. The group allegedly operated Android malware that collected credentials from banking apps and the Singpass system. [Additional coverage in The Star]
Nigerian BEC scammer pleads guilty: Nigerian national Hibundu Joseph Anuebunwa has pleaded guilty in the US to participating in BEC operations that defrauded US businesses. Two of Anuebunwa's co-conspirators also pleaded guilty and were sentenced to 41 and 60 months in prison, respectively.
Umbreon interview: DataBreaches.net has published an interview with Umbreon, a user on the now-defunct RAID and Breached forums. His real name is Pepijn Van der Stap—a 21-year-old from the Netherlands. He was detained in January and is currently awaiting sentencing.
New npm malware: Fifteen new malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
KEV update: CISA has updated its KEV database with eight new vulnerabilities that are currently being actively exploited. Two are D-Link router bugs from 2019, while the rest are Samsung 2021 vulnerabilities.
CISA DDoS alert: CISA has issued an alert about DDoS attacks targeting various industry verticals.
Akira ransomware decrypter: Avast has released a free decrypter for the Akira ransomware, allowing victims to recover their files without paying the attackers. The Akira ransomware launched operations in March 2023 and has versions of both Windows and Linux. The free decrypter only covers Windows variants, and Avast says it's working on a Linux decrypter as well. In the meantime, Avast says files encrypted on Linux hosts can be moved to a Windows machine and have them decrypted there using its Windows decryption toolkit.
Proxyjacking campaign: Akamai researchers have uncovered a cybercrime operation where a threat actor has been hacking into vulnerable servers and secretly enlisting them into peer-to-peer (P2P) proxy networks in order to monetize their bandwidth for personal profits. The intrusions take place via misconfigured SSH services, and that compromised servers are typically enrolled in services such as Peer2Proxy or Honeygain.
Malvertising campaign: Trend Micro says it has seen BlackCat ransomware infections originating from malvertising campaigns promoting a malware-laced version of the WinSCP app. We're so glad Google Ads is living up to its full potential.
GuLoader campaigns: Morphisec and SANS have some good write-ups on the recent malspam campaigns spreading GuLoader.
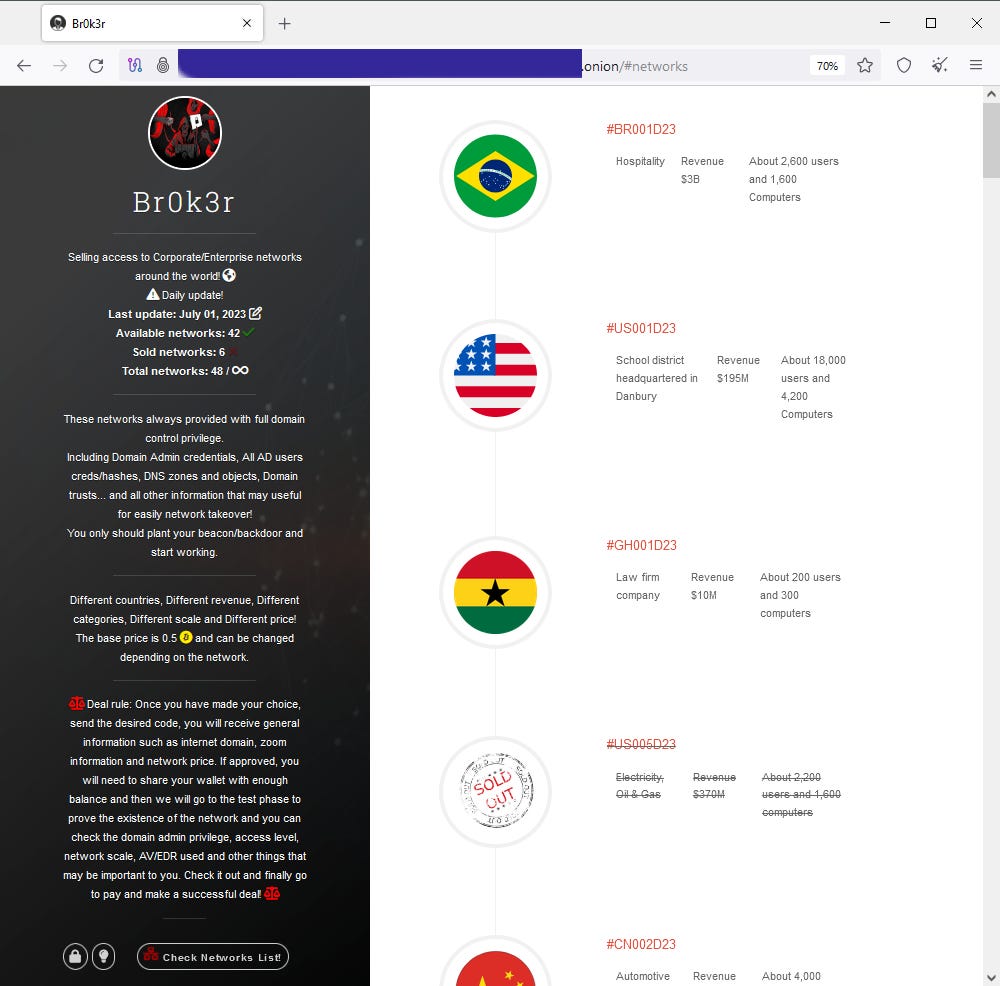
New Br0k3r group: A threat actor going by the name of Br0k3r is auctioning off the data of more than 40 companies on the dark web. The minimum asking price is 0.5 bitcoin/network or $15,000/network. None of the companies listed on Br0k3r's site have been named, most likely to avoid victims booting the group off their network and re-securing their systems. The group appears to have launched operations this month.
Malware technical reports
JokerSpy: SentinelOne has published its own analysis of the JokerSpy macOS malware. Similar reports have been previously published by BitDefender and Elastic.
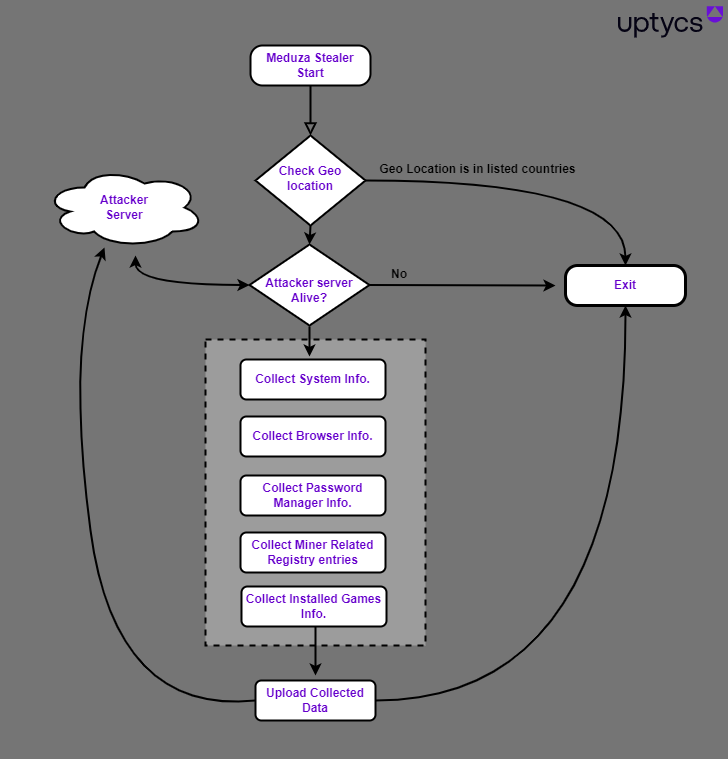
Meduza Stealer: Researchers with Uptycs and eSentire have published a breakdown of the Meduza Stealer infostealer.
Sponsor Demo
RunZero (formerly Rumble Network Discovery) is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
APTs and cyber-espionage
BlueNorOff's RUSTBUCKET: Elastic's security team has published a technical deep-dive on a new variant of the RUSTBUCKET macOS malware, previously used in BlueNorOff operations. Elastic says the malware was used "for sustained operations at a cryptocurrency payment services provider." The new RUSTBUCKET variant comes with a built-in persistence mechanism.
Vulnerabilities, security research, and bug bounty
WP plugin exploitation: Wordfence is seeing a threat actor launch active attacks against WordPress sites running the Ultimate Member plugin. The plugin is installed on more than 200,00 WordPress sites. Wordfence says the attacker is exploiting an older vulnerability that was not adequately patched.
D-Link PoC: Andisec researchers have published details and a PoC for CVE-2023-26615, a password-reset vulnerability in D-Link DIR-823G routers. The vulnerability allows unauthorized attackers to reset the password for the router's web management panel.
Citrix XSS: Assetnote researchers have published details on an XSS vulnerability (CVE-2023-24488) in the Citrix Gateway. More than 50,000 such devices are currently available online. Citrix patched this back in May.
GitLab vulnerability: Juniper has published a detailed write-up on CVE-2023-2825, a 10/10 vulnerability that GitLab patched back in May. A PoC for this was released back in May.
VMWare Aria vulnerability: ZDI has published a detailed technical write-up on CVE-2023-20864, an insecure deserialization vulnerability in VMware Aria Operations for Logs. ZDI likened the bug to CVE-2023-20887, another bug in the same software that is currently exploited in the wild.
XORtigate patch status: Security firm BishopFox says it developed an internal exploit for a recent Fortinet zero-day known as XORtigate (CVE-2023-27997). The company says it found more than 490,000 affected SSL VPN interfaces exposed on the internet, of which roughly 69% are still unpatched for the XORtigate vulnerability. The company previously released a tool that could scan FortiGate SSL VPN instances and see if they are vulnerable to XORtigate.
Attack on MongoDB Queryable Encryption: A team of academics from ETH Zurich has devised an attack technique that can recover plaintext data from encrypted MongoDB databases. The attack targets Queryable Encryption, a new feature launched last year that allows a MongoDB database to run queries on encrypted data. Researchers say the attack exploits the current interaction between MongoDB's QE feature and the database's logging system. The team notified MongoDB of their findings. The company said they would not be fixing any issues since the QE feature was in preview and would eventually change in future versions, invalidating the attack. Researchers said the attack still worked in February 2023 when they last tested it. More in the research team's paper [PDF].
Risky Business Podcasts
In this podcast, Patrick Gray and Tom Uren talk about the US Securities Exchange Commission warning SolarWinds executives that it is planning to bring enforcement actions against them. This is a big deal and really signifies that the SEC wants companies to be much more open about cybersecurity incident disclosures.




