Risky Biz News: Poland refuses to cooperate with the EU in spyware scandal
In other news: US charges IRGC ransomware crew; Uber discloses security breach; and Adobe gets new security execs.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Polish authorities are flat-out refusing to cooperate with EU officials in the investigation into their abusive use of advanced spyware against political rivals, the EU's PEGA committee said in a statement on Thursday.
We strongly condemn the fact that the Polish government has refused to collaborate with the Inquiry Committee by declining the invitation to the hearing and refusing to meet with the fact-finding mission next week. We believe that such meetings would give the Government opportunity to respond to reports about illegal use of intrusive surveillance against persons deemed as political opponents.
This is shocking! AN ABSOLUTE SHOCK!!!
Who would have thought that a ruling government that was caught hacking the smartphone of an opposition party leader, stealing SMS messages, and then sharing doctored images of said messages on the state-controlled TV during a disputed election race that the incumbents barely won would have anything to hide?
What we're referring to here is the infamous case of Krzysztof Brejza, a member of the Polish Senate whose phone was hacked 33 times ahead of parliamentary elections in 2019.
He is one of at least five victims that Citizen Lab and the Associated Press discovered as being targeted and hacked across Poland in 2019 with Pegasus, a spyware strain developed by sanctioned Israeli company NSO Group—whose operations Citizen Lab researchers have been tracking for years.
The other four alleged victims include Ewa Wrzosek (a local prosecutor critical of the government), Roman Giertych (a politician part of the League of Polish Families opposition party), Michal Kolodziejczak (leader of an agrarian social movement to which political party status was denied), and Tomasz Szwejgiert (an author who penned a book about the head of Poland's secret services).
Over the past year, these cases, along with similar ones discovered across Greece, Hungary, and Spain, have started to paint a grim picture that few Europeans wanted to admit—that the scourge of the Pegasus spyware has not been limited to countries far away, across the seas, with failed or abusive regimes, but has also slowly crept inside the EU, in countries with faltering democracies.
EU countries where Citizen Lab has found traces of attacks with Pegasus have all said in unison that they only bought the spyware for law enforcement purposes, to fight crime, and to investigate corruption and national security issues, and not to spy on their rivals, which is exactly what Polish officials also said earlier this year.
Following the revelations across Greece, Hungary, Spain, and Poland, the EU set up the PEGA Committee earlier this year to investigate EU governments if their explanations are actually true and hold governments accountable. Since April this year, the Committee has been holding sessions and meeting with victims, but also failing miserably at having any of the investigated governments recognize its authority.
While Poland has utterly ignored EU's PEGA, last month, Greece went as far as to question the legal authority and competence of the European Union to investigate what it sees as internal government matters.
PEGA members fought back by saying that the current unchecked use of spyware is a threat to democracy and the rule of law across Europe, hence part of many EU charters and conventions, the Committee has yet to make any progress since it most likely lacks any actual authority. PEGA is scheduled to file a report in April next year, but it's unclear how the European Parliament may treat its conclusions. The EU is famous for its bureaucracy, after all, and this may just lead to a big nothin-burger.
Breaches and hacks
New Uber hack: Uber disclosed on late Thursday night. While the company didn't say too much, the NYT found that various internal systems were down and that employees were instructed not to use the company's internal Slack.
Israeli leak: An Iranian hacking group named war_dark claims to have stolen the data of 9.5 million Israeli citizens, including Prime Minister Yair Lapid and opposition leader Benjamin Netanyahu.
Dogechain hack: Dogecoin DeFi platform Dogechain restored its service this week after it suspended operations on Sunday when a hacker exploited a vulnerability to steal $600,000 worth of currency from the platform.
Exploiter managed to mint 9.7M wDoge (~$600k), 3M still remains in his wallet and about $100k worth of USDC/ETH. #doge #dogechain #exploit https://t.co/yjDiluH1il
— Crumbs (@0xCrumbs) 11:04 AM ∙ Sep 11, 2022
General tech and privacy
Azure Code Signing: Microsoft gave software developers a preview this week of an upcoming tool named Azure Code Signing, an Azure service that makes it easier to cryptographically sign code and apps.
The service is currently in Private Preview supporting organizations with 3+ years of verifiable business history where code signed with Azure Code Signing is user mode trusted on Windows. We plan to launch into Public Preview in the next year and then work to increase our availability across the broad developer demographic.
Disable IE policy: Microsoft also released a new policy this week that will allow organizations to permanently disable the Internet Explorer browser right now and not have to wait for a future Microsoft update to do so.
Avast acquires "I don't care about cookies": Antivirus maker Avast has acquired "I don't care about cookies," a popular browser extension that hides cookie popups on internet websites.
Google and Meta fined in South Korea: The South Korean privacy watchdog agency fined Google and Meta this week for violations of its privacy law. The fines were $50 million for Google and $22 million for Meta.
Google fine stays in the EU: On the other side of the planet, Google's lawyers failed in their appeal to the EU to cancel a €4.343 billion the company received last year for its anti-competitive practices in the mobile market thanks to its control over the Android OS. More details in this PDF.
WhatsApp to let users hide their status: Meta's WhatsApp service will soon let users hide their online status from their friends. The feature is currently in beta.
Government, politics, and policy
CISA Strategic Plan 2023-2025: CISA published this week its strategic plan for 2023-2025 [PDF]. The document details four major goals and areas the agency will focus in the upcoming years: (1) enhance defensive capabilities; (2) reduce risk to America's critical infrastructure; (3) increase collaboration and information sharing; and (4) unify CISA capabilities. [Additional coverage in Federal News Network]
DOD & DOJ join FCC internet routing inquiry: The US DOJ and the DOD said this week they are joining an inquiry started by the FCC earlier this year into the security of internet routing. The inquiry is specifically looking at how foreign threat actors, such as China Telecom, have abused the BGP protocol to re-route and capture US internet traffic.
CISA cybersecurity hotline: After proposing the idea earlier this year of creating a cybersecurity emergency hotline available via the 311 phone number, CISA is considering partnering with US universities and having students taught cybersecurity fundamentals and then have them respond to hotline emergencies.
Open RAN security best practices: CISA and the NSA have published a guide with security best practices and considerations for organizations running Open Radio Access Networks (Open RAN).
New FBI PIN: The US FBI published another private industry notification [PDF] this week. The new PIN warns about cybercrime groups compromising user login credentials of healthcare payment processors to divert payments to bank accounts under their control. Estimated losses this year are in the range of millions of US dollars.
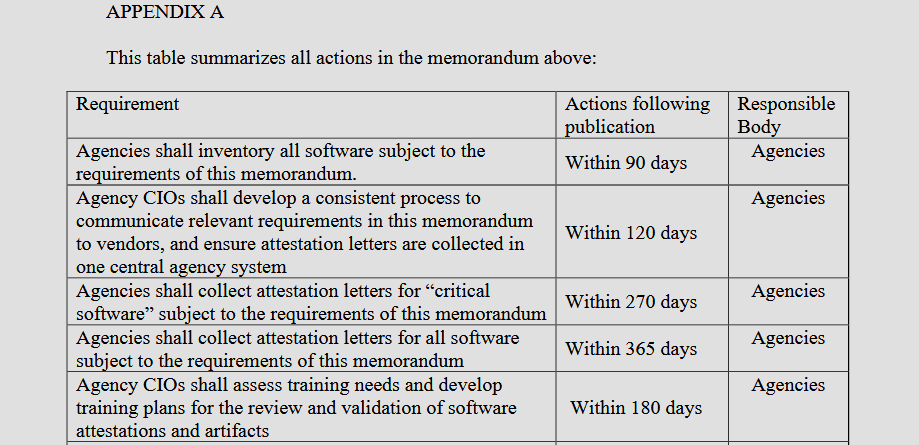
White House SBOM memoranda: The Biden administration published a new memorandum this week aimed at improving the security of software supply chains. The new directive [PDF] orders government agencies to implement a software bill of materials (SBOM) for their critical software within the next 90 days.
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. Last week, the company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
US cracks down on APT35: In a surprising move on Wednesday, the US government cracked down on members of the APT35 (Charming Kitten) Iranian cyber-espionage group. Authorities said at least three members of this group appear to have diverted from espionage operations and got involved in ransomware attacks, including against multiple US entities. As part of their response, the US DOJ has charged the three suspects, while the US Treasury levied sanctions against the three, but also the two Iranian companies where the three worked, and which appear to have been contracted by Iran's Islamic Revolutionary Guard Corps (IRGC). In addition, CISA, the FBI, and their Five Eyes partners, also released a long technical report detailing the group's malware and TTPs, so that companies across the globe can prepare and defend against their attacks. The US government's response this week was thorough but not surprising, mainly because days before the official indictment, companies like Google, Microsoft, and Secureworks published reports detailing a rise in activity from this group and their forays into ransomware attacks, something that you don't see from most classic APTs. The Secureworks report, in particular, noted that the group made OpSec mistakes, which allowed the company to identify its members by name, which would explain how the US government was able to name them in the indictment this week.
Chiffon Herring: AbnormalSec has a report out on Chiffon Herring, a BEC scam group that impersonates teachers to divert payment accounts from schools. As AbnormalSec researchers Crane Hassold wrote in a tweet, Chiffon Herring is "one of the few groups we see that actually goes after a specific industry."
The group has been active since at least March 2022 and mainly targets local school districts and universities in the United States. Their targets have ranged from large public universities to small community colleges, and from sprawling urban school districts to an individual all-girls preparatory school. Based on our research, Chiffon Herring actors are likely located in Nigeria and South Africa, both of which are typical hotbeds for BEC scammers.
More KillNet: We've had a few of these reports featured already in this newsletter, but here's another one on the KillNet pro-Russian hacktivist group—this one from Trustwave.
KISA report on lateral movement technique: The Korean Internet and Security Agency (KISA) published a report on Thursday on how attackers have been using SMB/Admin Shares as a lateral movement technique inside compromised networks.
Magniber ransomware distribution: AhnLab has a report out on the recent changes in the distribution tactics used by the operators of the Magniber ransomware, who, in the course of two months, went from MSI installers to control panel links (CPL) and now to JavaScript executable files (JSE).
WebLogic abuse: Trend Micro has a write-up available on how cryptomining gangs are still successful in abusing both old and newer Oracle WebLogic vulnerabilities to deploy their payloads across the internet—with the main suspect being the Kinsing botnet.
Edge malvertising: Malwarebytes warned this week about malicious ads appearing in the Edge browser news feed that are redirecting users to tech support scam sites.
npm malware: Phylum researchers have spotted an npm package posing as HubSpot's official Bucky Client that includes malicious code to steal developers' environment details, such as AWS access tokens. Per Phylum, the package is still active and averages around 600 installations per week.
Fast breakout times: CrowdStrike published this week a preview of its upcoming 2022 Falcon OverWatch Threat Hunting Report [PDF]. Among the report's primary findings was that the breakout time for e-crime operations remained low this year at 1 hour and 24 minutes. Breakout time is the time an adversary takes to move laterally from an initially compromised host to another host within the victim environment.
Moreover, the OverWatch team found that in 30% of those eCrime intrusions, the adversary was able to move laterally to additional hosts in under 30 minutes.
Malware technical reports
PlugX analysis: Security Joes published a report [PDF] this week on PlugX, a remote access trojan historically associated with Chinese cyber-espionage operations. A similar PlugX report was also published last week by Cybereason as well. Despite its age—being developed and first used back in 2008—both Security Joes and Cybereason have noted that PlugX is still very popular today, including with Chinese APTs but also with members of the Chinese cybercrime community.
Currently, it remains as one of the most popular tools in the Asian cybercrime community, given its flexibility and trajectory in the market; and it is still actively used by notorious threat actors such as Mustang Panda, Winnti, Gallium, DragonOK and Earth Berberoka.
Quantum ransomware: SecurityScorecard malware reverse-engineer Vlad Pasca published a technical analysis of the Quantum ransomware.
PrivateLoader: Sekoia researchers have published a report on PrivateLoader, a modular malware family that is being used to push various payloads as part of a Pay-Per-Install (PPI) scheme. Other previous reports on this threat are also available from Intel471, Zscaler, OALabs, and Walmart's security team.
YouTube self-spreading malware: Kaspersky researchers said they spotted a novel malware distribution campaign that uses YouTube videos advertising cheats for various online games that infects victims with the RedLine infostealer. The novel part is that the malware also comes with a component that hijacks the victim's YouTube account—if they have one—and posts a copy of the same "game cheats" videos in the hopes of infecting other users.
APTs and cyber-espionage
SparklinGoblin and SideWalk: ESET researchers said they discovered a new Linux backdoor malware strain named SideWalk, which they say has been created and used by SparklinGoblin, a suspected Chinese APT group.
This variant was deployed against a Hong Kong university in February 2021, the same university that had already been targeted by SparklingGoblin during the student protests in May 2020. We originally named this backdoor StageClient, but now refer to it simply as SideWalk Linux. We also discovered that a previously known Linux backdoor – the Specter RAT, first documented by 360 Netlab – is also actually a SideWalk Linux variant, having multiple commonalities with the samples we identified.
Webworm: The Symantec Threat Hunter team, part of Broadcom Software, published a report on Thursday on a new APT they are tracking as Webworm.
Active since at least 2017, Webworm has been known to target government agencies and enterprises involved in IT services, aerospace, and electric power industries located in Russia, Georgia, Mongolia, and a number of other Asian countries. [...] The group has developed customized versions of three older remote access Trojans (RATs), including Trochilus, Gh0st RAT, and 9002 RAT.
Gamaredon: Russian cyber-espionage group Gamaredon (Armageddon, Shuckworm) is still active and targeting Ukrainian government entities with information-stealing trojans, Cisco Talos said on Thursday.
On my first blog at Talos, we talk about a new campaign from #Gamaredon targetting government entities in #Ukraine and the custom tools they use to steal information. Check it out!
— Guilherme Venere (@gvenere) 4:14 PM ∙ Sep 15, 2022
BlackTech: Japan's CERT team published a report on attacks carried out by the BlackTech Chinese cyber-espionage group. The attacks took place in May this year when the group exploited CVE-2022-1388, a vulnerability in F5 BIG-IP networking devices, to breach corporate networks and install malware strains such as TSCookie and Bifrose. The report also covers a new malware strain named Hipid, linked to a distribution campaign hosted on PyPI.
Bvp47: PanguLab has published the second part of its Bvp47 malware analysis. The company says the malware has been used in the recent hack of the Northwestern Polytechnical University, which Beijing blamed on the US NSA. More on this stupid drama here.
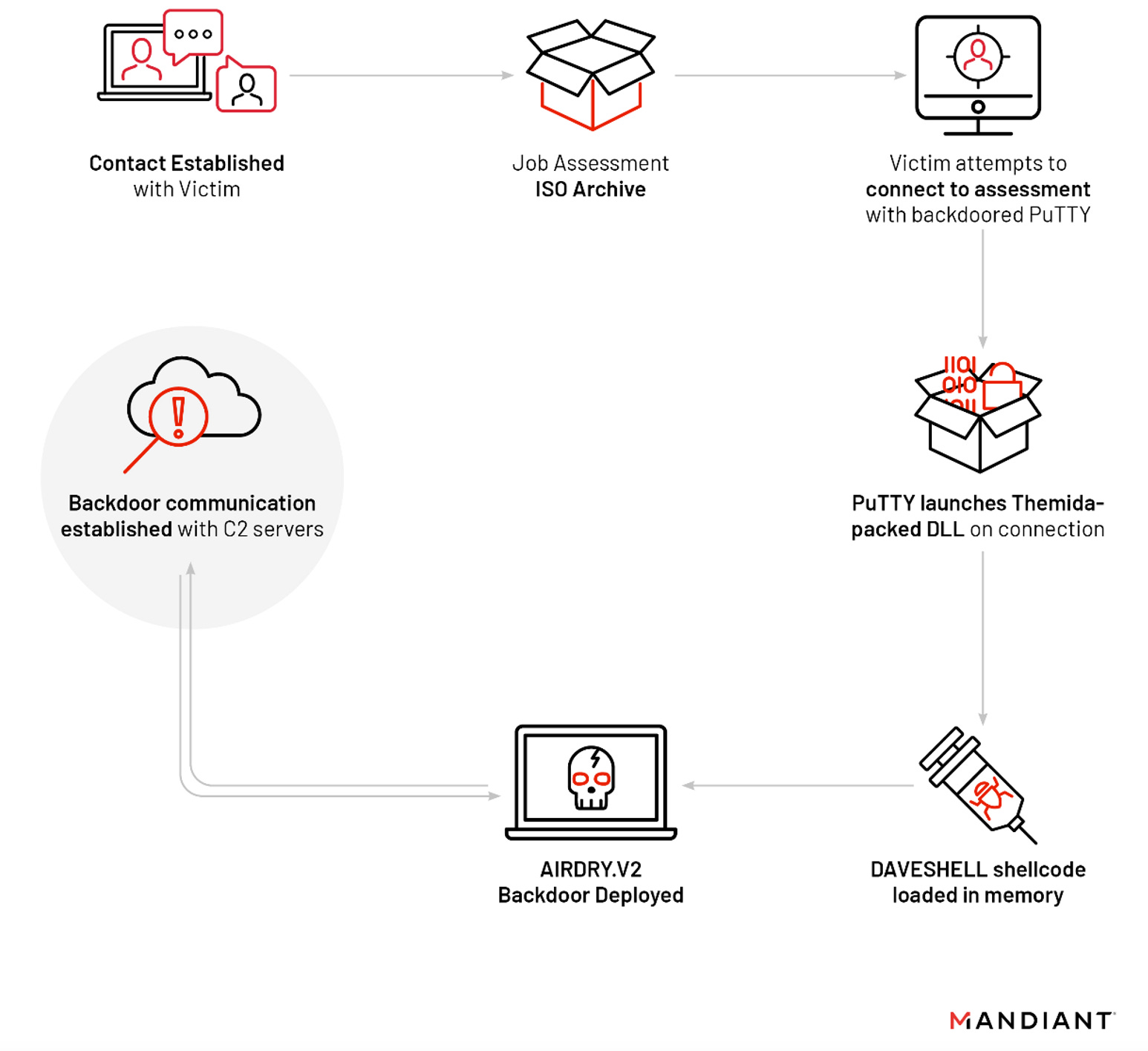
UNC4034: In a report on Wednesday, Mandiant also covered a pretty novel phishing technique employed by UNC4034, a suspected North Korean APT. The method relies on getting victims to download and use a backdoored version of the PuTTY utility.
Vulnerabilities and bug bounty
Trend Micro zero-day: Trend Micro has released a security update for its Apex One enterprise security product that fixes multiple vulnerabilities, including a zero-day that was actively exploited in the wild (CVE-2022-40139).
MSFT Teams vulnerability: Researchers from Vectra have uncovered that the Microsoft Teams desktop apps store their authentication cookies in cleartext, which means that if threat actors can steal these locally-stored files, they can easily bypass authentication and access user accounts.
Android Qualcomm TrustZone vulnerability: Security researcher Tamir Zahavi-Brunner has a write-up on CVE-2021-1961, a vulnerability in the Qualcomm TrustZone chipset fixed last year that can be used to compromise the Android kernel.
Contec vulnerabilities: Security researcher Samy Younsi has published details about vulnerabilities in Contec WiFi access points, devices primarily used in airplanes for multimedia systems. The company released fixes at the start of the month [PDF].
NETGEAR FunJSQ vulnerabilities: ONEKEY researchers have published details about a series of vulnerabilities impacting NETGEAR routers, and more particularly in FunJSQ, a third-party gaming speed-improvement service present in the majority of NETGEAR firmware images. The vulnerabilities allow arbitrary code execution attacks and received official patches last week.
Windows IKE exploit PoC: Security firm 78ResearchLab has published a proof-of-concept exploit for CVE-2022-34721, a remote code execution vulnerability in Windows' IKE protocol extensions. While this vulnerability only impacts IKEv1, all Windows Servers are affected because they accept both V1 and V2 packets.
Infosec industry
Industry profile #1: The Protocol has a profile on Katie Nickels, Director of Intelligence at Red Canary.
Industry profile #2: Similarly, Motherboard also published a profile on Katie Moussouris, the Luta Security Founder and CEO, and her efforts to close the gender pay gap in cybersecurity.
New tool—AWS SSAA: AWS engineers open-sourced last month a new project called the Self-Service Security Assessment tool that can help their customers create a point-in-time assessment of their AWS accounts. Also comes with an optional AWS ransomware checking module.
New Adobe security exces: Adobe announced this week it was bringing on board two new executives to serve in security-focused roles. The two are Maarten Van Horenbeeck, who will serve as Chief Security Officer, and Nubiaa Shabaka, who will serve as the company's Chief Privacy Officer.
LEA job: The cybersecurity division of the French Gendarmerie has three openings.
La @Gendarmerie recrute !!
— CyberGend (@CyberGEND) 5:39 AM ∙ Sep 15, 2022
3 postes d’expert de haut niveau en technologies numériques sous le statut d’officier commissionné
Missions, rémunération 👇




