Risky Biz News: Palo Alto Networks scrambles to push zero-day patch
In other news: FISA S702 reapproval passes through the House; Roku forcibly enables 2FA for all users after waves of credential-stuffing attacks; ex-Amazon engineer gets 3 years in prison for crypto-heist.

This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

[Editor's note: Catalin's gone to bed, but Palo Alto have since put out patches for the latest releases of PAN-OS, and announced a roll out schedule for the rest]
Palo Alto Networks has scrambled over the weekend to release a software patch for its firewall devices. The patch is intended to fix a zero-day (CVE-2024-3400) in the GlobalProtect VPN feature of PAN-OS, the firmware that runs on Palo Alto's firewalls.
Security firm Volexity discovered the attacks, which the company attributed to a group it tracks as UTA0218. Palo Alto tracks this as Operation MidnightEclipse.
Volexity described the group as a state-backed threat actor but did not link the group to any country.
"Volexity assesses that it is highly likely UTA0218 is a state-backed threat actor based on the resources required to develop and exploit a vulnerability of this nature, the type of victims targeted by this actor, and the capabilities displayed to install the Python backdoor and further access victim networks."
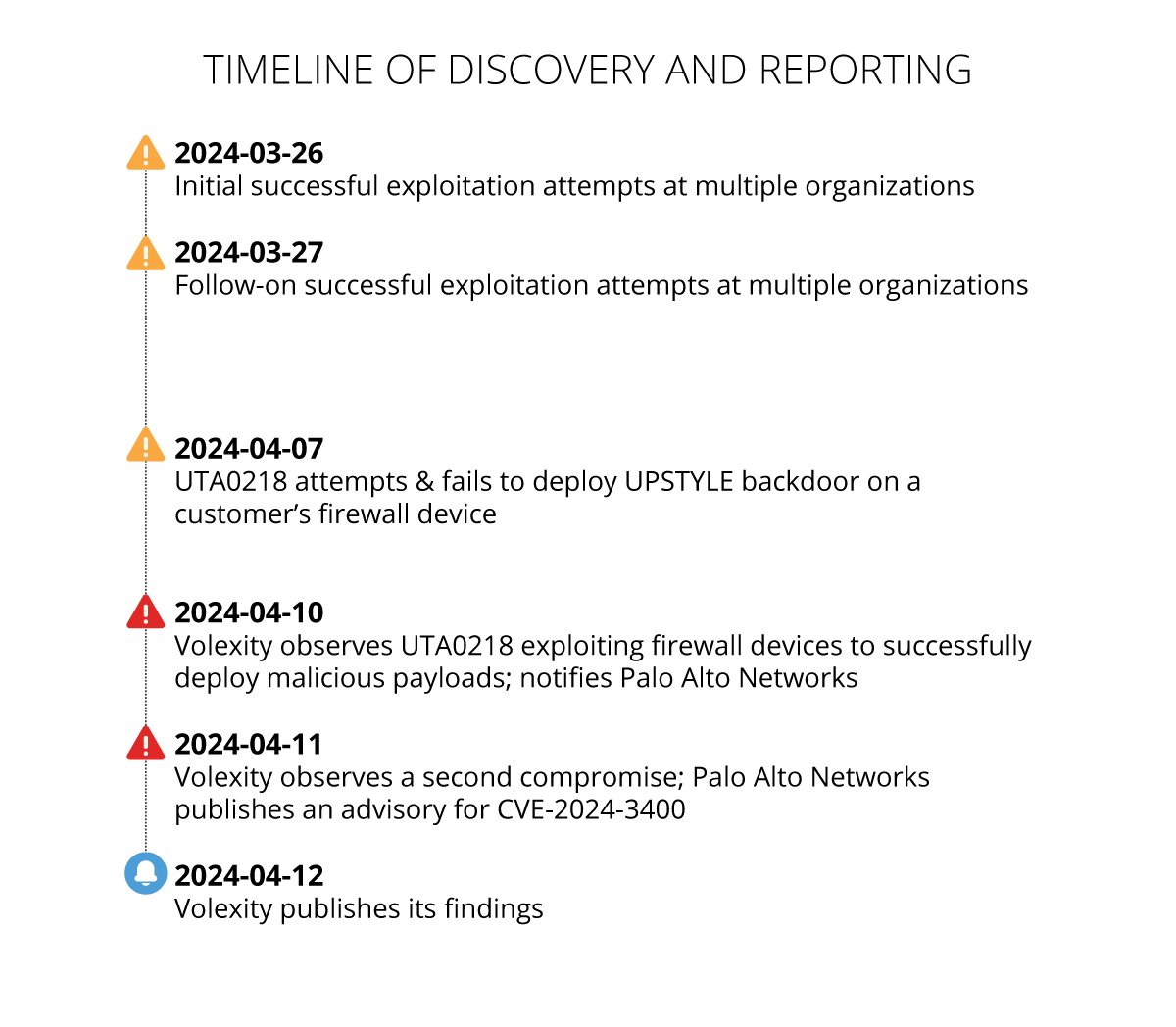
According to a timeline published by Volexity, the attacker appears to have developed and tested the zero-day at the end of March.
Actual attacks began last week when UTA0218 started deploying a Python-based backdoor named UPSTYLE on compromised devices.
The group used the backdoor for hands-on-keyboard activity, to download additional tools, and move laterally on the hacked networks.
After UTA0218 polished its exploit and post-compromise, everything moved extremely quickly (see timeline graph below), with Volexity detecting the attacks and working with the vendor to fix the root cause.
Palo Alto Networks described the zero-day as a command injection vulnerability that does not require attackers to authenticate on its devices. Because the vulnerability has a CVSS severity rating of 10/10, it's most likely trivial to exploit—although details are still being kept private, and for good reasons.
Because Palo Alto Networks is a major vendor for the US federal space, the zero-day got an immediate response from US authorities, with CISA publishing an advisory late Friday afternoon—just in time to ruin everyone's weekends yet again (hello, XZ backdoor fans)!
The impact is quite something. The number of potentially vulnerable devices ranges from 40K (Shodan) to 133K (Censys). 😲 That's quite the numbers!
Perusing the Shodan and Censys search results, the victims are a list of who's who across several major industries.
Volexity says it can't accurately estimate the size of the attacks, but it believes the use of the zero-day was "limited and targeted." For now, of course!

Breaches, hacks, and security incidents
Nexperia ransomware attack: Dutch chipmaker Nexperia has fallen victim to a ransomware attack. The incident took place at the end of March, and the investigation is still ongoing. A threat actor known as Dunghill or DarkAngels took credit for the attack. The group claims it stole hundreds of gigabytes of sensitive materials, including chip designs and trade secrets. It also claimed to have data on Nexperia's customers Apple, IBM, and Huawei. [Additional coverage in RTL Nieuws]
Roku data breach: Hackers have broken into more than 576,000 Roku accounts following a wave of credential-stuffing attacks. Roku confirmed the hacks last week and reset passwords for all affected users. This is the second wave of credential stuffing attacks Roku has faced this year. Threat actors also gained access to 15,000 accounts at the end of February. As a result of the hacks, Roku is now forcingly enabling email-based 2FA for all users. Roku has more than 80 million active users.
OraSure breach: US medical device maker OraSure Technologies disclosed a security breach in SEC filings last week. [h/t Kevin Beaumont]
Giant Tiger hack: A threat actor has leaked the personal data of 2.8 million customers of Canadian discount store chain Giant Tiger. The company has confirmed the breach. It says the data was taken from a third-party vendor that handles customer communications and engagement. [Additional coverage in CyberNews]
Heritage Foundation cyberattack: Conservative US think tank, the Heritage Foundation, has fallen victim to a cyberattack. [Additional coverage in TechCrunch]
AEP leak: The Romanian government has disclosed a data breach at its Permanent Electoral Authority (AEP). Officials say that for several hours AEP servers leaked the personal data of more than 1,300 individuals. The victims were individuals who are eligible to be named presidents for voting sections in this year's upcoming elections. Officials described the leak as an error. [Additional coverage in HotNews]
New Trump hacking scandal: Investment firms led by the former CEO of the SPAC that merged with Donald Trump's media company allege that their files were hacked and stolen by a current member of the media company's board of directors. [Additional coverage in CNBC]
LastPass deepfake incident: LastPass says that a threat actor used a deepfake recording of its CEO in an attempt to trick one of its employees. The company says the employee did not fall for the scam because the request came via WhatsApp, an uncommon business channel. The incident was immediately reported to the company's security team.
General tech and privacy
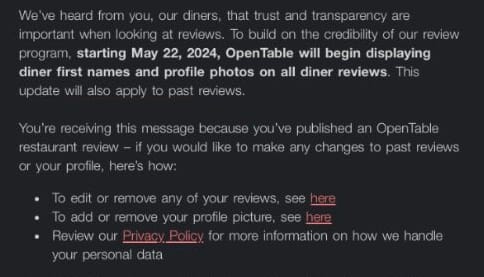
OpenTable to dox all its users: Restaurant reservation and review service OpenTable will add the real names and photos of its users to past reviews without their consent. The change will take place on May 22, and users can't opt out. OpenTable has given users the option to edit or remove past reviews—in what appears to be a shady way of protecting itself from the lawsuits of angry restaurant owners.
Government, politics, and policy
House passes FISA S702 extension: The US House of Representatives has passed an extension of Section 702 of the Foreign Intelligence Surveillance Act. The US surveillance program was extended for two years instead of the customary five. The Section 702 extension came two days after a first attempt failed following pressure from former US President Donald Trump. The bill now moves to the Senate floor where it needs to pass before April 19. [Additional coverage in CNN]
Ransomware and Financial Stability Act: US lawmakers have put forward a bill that would require financial institutions to notify the Treasury Department of any ransomware payments. The bill also bans financial institutions from paying ransomware demands of over $100,000 without approval from a law enforcement agency. The new bill is named the Ransomware and Financial Stability Act and was proposed by the US House Financial Services Committee.
US sanctions Hamas cyber actor: The US Treasury Department has imposed sanctions on a Hamas member responsible for the group's cyber influence operations. US officials say Hudhayfa Samir Abdallah al-Kahlut has been the leader of the al-Qassam Brigade's cyber influence department since 2007. The al-Qassam Brigades is the military wing of Hamas that operates in Gaza.
SIMs linked to biometrics: In the aftermath of the Crocus City Hall ISIS attack, Russia wants to link SIM cards bought by foreigners to their biometrics and their device's IMEI code. [Additional coverage in Vedomosti]
Russian HIBP: The Russian National Coordination Center for Computer Incidents (NKTsKI) has launched its own version of the Have I Been Pwned service. The agency launched the service after Ukrainian hacktivists leaked the data of millions of Russians over the past two years. The NKTsKI is a CERT-like organization created by the Russian Federal Security Service (FSB) in 2018. The service is available online here.
Ukraine Cyber Police interview: TechCrunch has published an interview with Yevhenii Panchenko, the head of Ukraine's Cyber Police department.
"[Russia] uses social media to sometimes take pictures and publish them on the internet, as it was usual in the first stage of the war. When the war first started, probably for three or four months [Russian soldiers] published everything: videos and photos from the cities that were occupied temporarily. That was evidence that we collected."
Spyware in Poland: Poland's National Prosecutor's Office has officially confirmed that the former ruling government has targeted Polish Member of the European Parliament Krzysztof Brejza with the Pegasus spyware. The former government repeatedly targeted and infected Brejza on multiple occasions. Brejza coordinated the opposition political strategy for the Polish parliamentary elections last year. CitizenLab researchers say that Brejza was targeted with "unrelenting, orchestrated disinformation" after he learned of the hacks last year.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Daniel Schell and David Cottingham, the CTO and CEO of Airlock Digital. They discuss the security standard that drove innovation and the genesis of Airlock Digital and also how to make sure that standards don’t become box-checking exercises.

Cybercrime and threat intel
Ex-Amazon engineer gets 3 years in prison: US authorities have sentenced a former Amazon security engineer to three years in prison. Shakeeb Ahmed exploited vulnerabilities in blockchain contracts to steal funds from cryptocurrency platforms. He stole $9 million from Cream Finance and another $3.6 million from Nirvana Finance. Officials say Ahmed disguised the hacks as vulnerability research. He conditioned the return of stolen funds for large "bug bounties." Nirvana Finance stopped operations when it couldn't agree with Ahmed on the return of its stolen assets.
"Nirvana offered AHMED a “bug bounty” of as much as $600,000 to return the stolen funds, but AHMED instead demanded $1.4 million, did not reach agreement with Nirvana, and kept all the stolen funds. The $3.6 million AHMED stole represented approximately all the funds possessed by Nirvana, which as a result shut down shortly after AHMED’s attack."
Firebird/Hive RAT dev arrested: The US has detained and charged a 24-year-old from California for allegedly developing and selling malware. Edmond Chakhmakhchyan allegedly created the Firebird remote access trojan (RAT) in 2020. He later renamed the malware to Hive RAT and sold it on hacking forums under the pseudonym of Corruption. Australian police detained one of the suspect's alleged accomplices. Chakhmakhchyan pleaded not guilty and will face trial in June.
Hackers detained in Russia: Russian authorities have detained three men for allegedly hacking and selling trade secrets from one of Russia's largest IT companies.
Pokemon hacker: Japanese authorities have arrested a 36-year-old man for selling hacked rare Pokemon characters. Officials say the suspect has been selling hacked game save files since December of last year for as much as $30. Hacking and editing game save file data in Japan is a violation of the Unfair Competition Prevention Act. [Additional coverage in NHK]
Sextortionist arrested: The US has arrested a Delaware woman for her alleged role in a sextortion scheme. The suspect allegedly worked with an accomplice from the Ivory Coast and targeted thousands of victims throughout the United States, Canada, and the United Kingdom. Hadja Kone allegedly recorded victims performing sexual acts during live video chats. She would then threaten to release the footage to their family and friends if victims didn't pay a ransom. Kone and her accomplice made almost $1.7 million over two years. The accomplice was arrested in the Ivory Coast in February.
REvil case in Russia: The prosecution of REvil ransomware group members detained in Russia in January 2022 is still underway in Sankt Petersburg. No big news yet as the case is moved from the regular court to a military court back and forward. [Additional coverage in TASS]
World Cybercrime Index: Academics from the University of Oxford have published what they call the world's first-ever World Cybercrime Index. There is literally no surprise Russia is #1. Seeing Romania on #6 is, though, since North Korea is #7—you know, the country that stole over $3 billion in crypto and has been the bane of the SWIFT system for years.

Road tolls scams: The FBI is seeing an increase in complaints about road toll fee collection scams. Victims report receiving smishing texts about unpaid road toll fees that try to collect their financial data. The FBI says it has received more than 2,000 complaints about the scam since the start of March.
XWorm campaign: eSentire researchers have published details on a malspam campaign delivering the XWorm malware using the good ol' and timely tax season lures.
SolarMarker campaign: The same eSentire team also published a report on a malspam campaign delivering the SolarMarker malware, also known as Jupyter or Yellow Cockatoo.
New npm malware: Fifty malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Threat/trend reports: Norma Cyber, Qihoo 360, and Red Alert have recently published reports covering infosec industry threats and trends.
Malware technical reports
XZ backdoor: It's been two weeks since the XZ backdoor incident, and security firms are now publishing the "good" reports. We've had one from SentinelOne and now other good ones from Binarly and Kaspersky.
Pikabot: Zscaler researchers look at the recent changes to Pikabot's string obfuscation techniques.
New card skimmer: Sucuri has discovered a new card skimmer in the wild. The novel thing about this one was that it was hidden in a script imitating the Facebook Pixel analytics service. You usually see these things disguised as Google scripts or the jQuery library and its plugins.
Fuxnet: Claroty has attempted a "visual" analysis of Fuxnet, the malware used by BlackJack Ukranian hacking group in data-wiping attacks against Russian entities.
Sponsor Section
Airlock Digital CEO David Cottingham shows Patrick Gray how Airlock's execution control and allowlisting solution works.
APTs, cyber-espionage, and info-ops
LightSpy is back: The LightSpy cyber-espionage group is back with a new campaign that targeted individuals in India and Southern Asia. The suspected Chinese group hadn't been seen in the wild for several months. BlackBerry's security team says the group now operates a new mobile spyware framework named F_Warehouse. The framework allows LightSpy operators to infect mobile devices, steal data from popular apps, recover browsing histories, and record audio.
New Kimsuky malware: Security researcher somedieyoungZZ has published a report on a new malware strain used by the Kimsuky group.
Vulnerabilities, security research, and bug bounty
Security updates: Citrix and Juniper have released security updates for some of their products.
Fortinet exploitation: Forescout has published a report on a recent campaign that exploited a Fortinet SQLi vulnerability (CVE-2023-48788) to target companies across the world. The company says the threat actor behind the attacks has been active since at least 2022 and is using both Vietnamese and German language in their infrastructure.
Windows Telephony Server vulnerability: Security researcher k0shl, of Cyber Kunlun, has published a detailed write-up of CVE-2024-26230, an EoP in the Windows Telephony Server that Microsoft patched last week.
Outlook RCE: Akamai researcher Ben Barnea has published a write-up on CVE-2023-35628, an RCE in the Windows MSHTML component used with Outlook. Microsoft patched the bug back in December.
IP.Board RCE and SQLi: SSD has published a write-up on two bugs (CVE-2024-30162 and CVE-2024-30163) in the IP.Board forum software.
ZeroMQ bug: Software engineer Fang-Pen Lin has published a write-up on how she "accidentally" found a 9.8/10 critical vulnerability impacting the ZeroMQ messaging library back in 2019. The vulnerability is tracked as CVE-2019-13132.
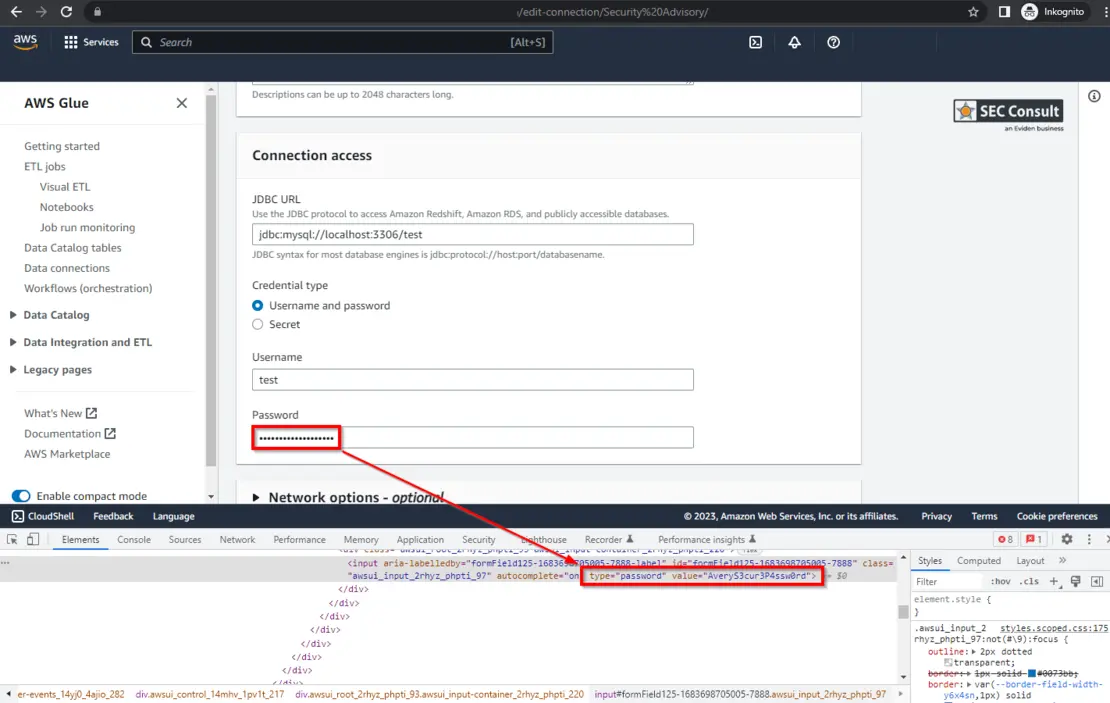
AWS Glue password leak: SEC Consult researchers have discovered that the AWS Glue platform leaks database passwords via server responses. The leak occurs when a staff member accesses the Edit Connections page. The password is masked on the page with asterisks but loaded in cleartext inside the HTML page.
IBM QRadar vulnerability: WatchTowr researchers have published a write-up on how IBM has failed to update its QRadar SIEM, which is now vulnerable to an old Apache web server bug (CVE-2022-26377).
"[T]his would allow threat actors (or watchTowr's automation) to assume the session of the user and take control of their QRadar SIEM instance in a single request."
Delinea patches auth bypass: Software company Delinea took its PAM platform offline over the weekend to fix a major security flaw. The vulnerability allows threat actors to bypass authentication and access data on the PAM platform, known as the Delinea Secret Server. The data can then be used to abuse privileged accounts and move across a victim's internal network. Delinea released emergency patches after security researchers published details about the vulnerability online. Researchers say they couldn't reach or get a response from the company for two months. Delinea has also released patches for on-prem versions of the Delinea Secret Server. [Additonal coverage via Kevin Beaumont]
Lighttpd vulnerability still around: Intel and Lenovo have declined to fix a vulnerability in some of their older base management controllers (BMCs). BMC firmware from both companies contains a vulnerability in their built-in web server. Both vendors declined to fix the issue because the vulnerable products recently hit end-of-life status. The real fault in this incident resides with the maintainers of the Lighttpd web server. According to Binarly, the project silently fixed a bug in 2018 without an associated CVE identifier. Runzero has published a list of BMCs and other devices known to have used vulnerable versions of the Lighttpd server.
Infosec industry
New tool—hauditor: Antonio De Turris of Secure Network has released hauditor, a tool designed to analyze the security headers returned by a web page and report dangerous configurations.
Acquisition news: Cybersecurity firm Zscaler has acquired Airgap Networks, a developer of agentless segmentation technology.
MITRE ATT&CK update: MITRE will add two new exploitation techniques to the ATT&CK framework later this month. Both techniques have been widely used by North Korean actors in past operations. The first technique is Transparency, Consent, and Control (TCC) manipulation, and the second is phantom DLL hijacking. [Additional coverage in Dark Reading]
RIP Sophia d'Antoine: Sophia d'Antoine, the founder of cybersecurity startup Margin Research, has died after she was struck by an SUV last week. D'Antoine was only 30. [Additional coverage in the Daily Mail]
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the tradecraft used in the compromise of the XZ open-source data compression project.




