Risky Biz News: OPERA1ER group hits African banks for $30 million
In other news: Twitter takes down six info-op bot networks; Black Basta ransomware linked to FIN7 group; supply chain attack hits 250+ US news sites.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Over the past decade, banks have not escaped the rising tide of ever-increasing sophisticated cyberattacks, and many of them have been hacked and lost billions of US dollars in serious intrusions, with the most famous threat actors that pulled off successful bank heists including the likes of Carbanak and the Lazarus Group North Korean APT.
The common thread across all recent major bank cyber-heists was that they usually targeted organizations in North America and Europe before attackers switched their targeting to Asia and Latin America. But as banks elsewhere have seriously upgraded their network defenses, threat actors are now turning their eyes toward Africa, a region that has been left relatively unscathed in previous years.
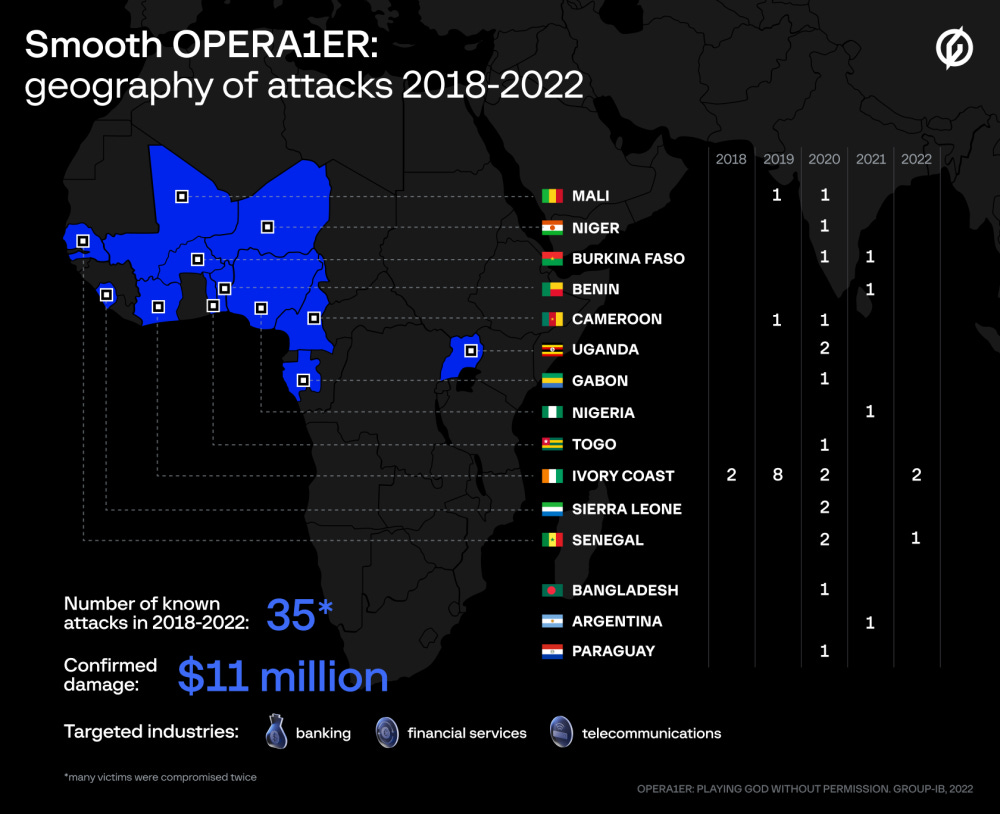
According to a joint report published this week by security firm Group-IB and Orange's CERT team, a French-speaking cybergroup group tracked as OPERA1ER (also known as Common Raven or the DESKTOP-group) has been wreaking havoc across the continent for four years, between 2018 and 2021.
Researchers said they linked the group to 35 intrusions at different organizations across 15 countries, with most of the attacks targeting African banks.
Group-IB and Orange researchers said that while the group used basic phishing attacks and off-the-shelf remote access trojans to gain an initial foothold in their victim's networks, OPERA1ER has exhibited both restraint and patience.
Some intrusions lasted months, as the group moved laterally across bank systems while they observed and mapped the internal network topology before springing their attack.
Rustam Mirkasymov, Head of Group-IB's Threat Research in Europe, told RiskyBizNews that the group typically waited and sought to identify and compromise bank systems that handled money transfers.
Once they reached these sensitive systems, the group would work with a network of around 400 money mules to orchestrate a coordinated transfer of funds from bank accounts to mule accounts, with the money mules withdrawing the stolen funds from their accounts via ATMs in a coordinated ATM cash-out before bank employees could react.
Mirkasymov said they linked OPERA1ER intrusions to bank heists totaling $11 million, but the group is suspected of stealing more than $30 million, although not all incidents have been formally confirmed.
Breaches and hacks
Ransomware attack cripples 75 German schools: Seventy-five schools across Bavaria—with 55 schools in Munich alone—have been cut off from their internal databases after a ransomware attack hit a server operated by the Munich-Land province. Officials said they discovered the ransomware attack as soon as it happened, after a mysterious server restart, and shut down the affected system until remediation. Officials believe the attacker gained access to the server after phishing one of their employees.
Ransomware cripples Polish hospital: A ransomware attack this week has crippled the activity of a major hospital in Lodz, Poland's third-largest city. According to local media, the attack took down the hospital's entire IT network, forcing doctors to issue prescriptions on paper. Tomographs, magnetic resonance imaging, and other computerized testing equipment have been down since the attack, but officials hope to have everything back up by the end of the week. The attack comes two weeks after the Polish government made more than 200 million zlots (~$41.5 million) available to healthcare organizations as a cybersecurity upgrade fund.
Boeing subsidiary ransomware attack: Jeppesen, a wholly owned Boeing subsidiary that builds aircraft navigation databases and flight planning applications, also appears to be dealing with a ransomware attack.
Deribit crypto-heist: Cryptocurrency exchange Deribit said it was hacked this week after a threat actor hacked its hot wallet and stole $28 million worth of cryptocurrency. [Additional coverage in Decrypt]
Skyward crypto-heist: DeFi platform Skyward Finance confirmed on Wednesday a report that a hacker exploited a vulnerability in its smart contract and stole $3 million worth of cryptocurrency. [Additional coverage in CoinTelegraph]
General tech and privacy
IP addresses as spoils of war: At the RIPE85 conference held last week in Belgrade, members of the RIPE organization—which manages the IP address space of European countries—have decided to impose a "temporary freeze" on the transfer of Ukrainian IP addresses to new owners, especially to Russian companies. According to a report from Techaint and a message sent via the organization's mailing list, the request to impose this block came from Ukrainian IT companies in areas occupied by the Russian Army, who have had IP address blocks stolen and then illegally transferred to Russian network operators. [Videos of the RIPE 85 conference are available in this YouTube playlist]
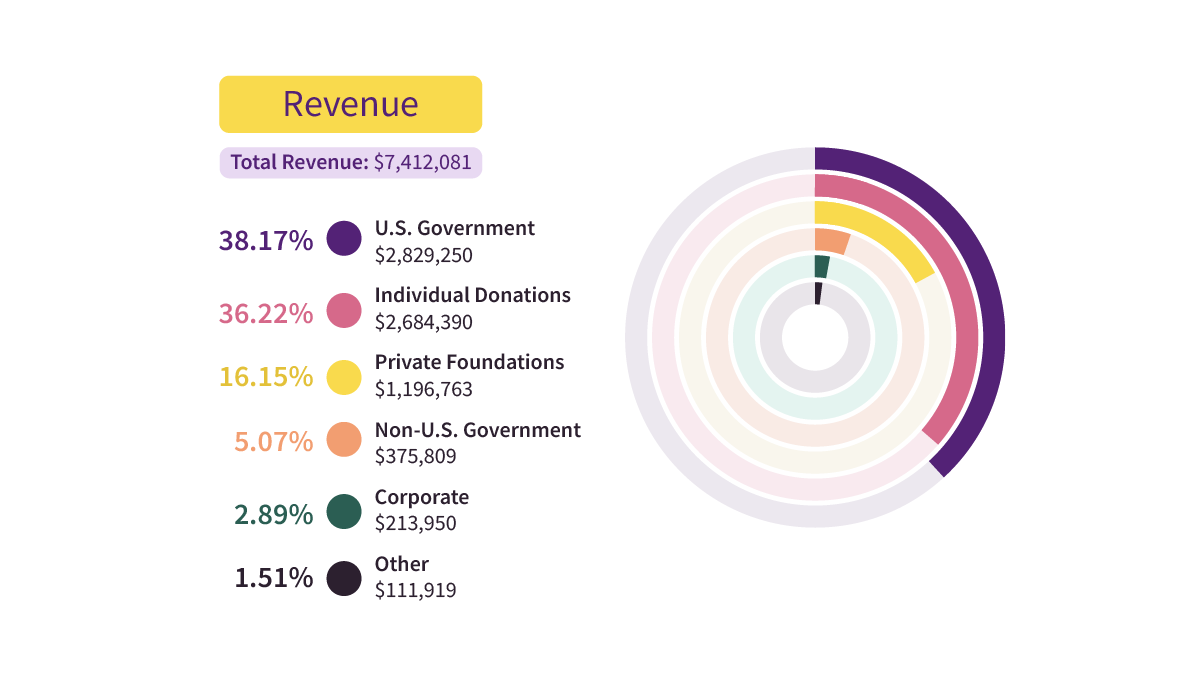
Tor Project funding: The Tor Project shared its financial statement for the Fiscal Year 2020-2021, and the organization said that funds from the US government accounted for only 38.17% of its total revenue over the period, down from 53% over the previous fiscal period.
Government, politics, and policy
Twitter InfoOps: Analysts from the Digital Forensic Research Lab and the Stanford Internet Observatory have published details about six Twitter bot networks—five from China and one from Iran—that tried to sway the discourse about the upcoming US 2022 Midterm Elections and various geopolitical issues, such as the Russia-Ukraine war and America's foreign policy on China. Researchers said the networks used follow-back practices in an attempt to integrate themselves into "highly-active" Twitter communities on both right- and left-leaning US political groups. All six networks tried to pose as US citizens, but despite this, they failed to garner any online following or visibility for their content.
"The networks did not appear to achieve significant engagement from the online public or strong infiltration within American political-activist networks on Twitter; the most-engaged tweet had 31,303 engagements, and of the 705,864 tweets spanning the six sets, 592,333 had zero likes. While these inauthentic accounts at times participated in conversations alleging fraud in 2020, and commented about concern for the integrity of the midterms, these conversations remain dominated by authentic activity from political influencers, politicians, and the American public. Nonetheless, we present our findings to help inform the American public's understanding of foreign influence activities, and additionally observe here that the diligence of Twitter's integrity team ensured that these networks were disrupted before they managed to obtain significant reach. "
Killnet attack on US Treasury: Speaking at a financial services conference this week, a representative for the US Treasury said the agency successfully defended a "pretty low-level DDoS" attack launched by Russian pro-hacktivist group Killnet last month.
Microsoft extends help to Ukraine: Microsoft announced Thursday it was extending its pledge to help the Ukrainian government with IT services throughout Russia's invasion with another $100 million, bringing the company's total commitment so far to $400 million worth of covered costs. This help includes providing hosting for the Ukrainian government's IT systems on its cloud servers to avoid physical compromise by Russian troops and cybersecurity protection and incident response services in the face of a wave of cyberattacks from Russia's numerous state-sponsored threat groups.
Russia's search for a Windows replacement: The Russian Ministry of Digital Development ran a survey among the country's biggest IT firms to identify the best replacement for the Windows OS across Russian government and private-sector networks. According to Kommersant, all three are Linux-based operating systems, named Astra Linux, ALT OS, and Red OS, respectively. The Russian government is seeking a replacement after Microsoft pulled out of Russia, stopped delivering security updates to Russian systems, and started blocking Russians' access to Windows installation files.
Red Cross digital emblem: The International Committee of the Red Cross said Thursday that it was looking into creating a digital version of its red cross and red crescent emblems that could be added on existing websites or networks to signal hackers that they have accessed systems and networks of medical facilities, humanitarian aid, or Red Cross agencies. Yeah, good luck with that! I've heard threat actors care about those things. Especially the ones from authoritarian regimes hunting down minorities for genocide and forced labor camps.
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
Tax fraud ring indicted: The US DOJ charged eight suspects this week for a massive tax fraud scheme that took place between 2015 through 2019. DOJ officials said the group purchased credentials from the dark web to the internal networks of several Certified Public Accounting (CPA) companies across the US. Officials said the group accessed CPA networks, stole the tax returns of "thousands of taxpayers," created six tax preparation businesses in south Florida, and used those companies to file more than 9,000 fraudulent tax returns in the victims' names, hijack tax refunds towards their own accounts.
Russian hacker released from prison: Vladimir Drinkman, a Russian hacker who stole more than 160 million credit card numbers from several US payment processors in the late 2000s, was released from prison this week after serving a 12-year sentence, according to RadioFreeEurope.
Adware explosion: Antivirus maker Avast said it observed an explosion in adware activity in Q3 2022, following distribution campaigns specifically aimed at Central, South, and Eastern Europe. In addition, the company also noted that despite cryptocurrency exchange rates crashing this quarter, illegal cryptomining operations remained at a steady pace, decreasing by only 4% from the previous quarter.
ENISA threat landscape: ENISA, the EU's cybersecurity agency, published this week its threat landscape report, covering a reporting period starting from July 2021 up to July 2022. Some of the most interesting stats include:
- More than 10 TBs of data are stolen monthly in ransomware attacks.
- More than 60% of affected organizations appear to have paid the ransom demand.
- 66 zero-day vulnerabilities were disclosed in the reporting period.
- The DDoS landscape reached its all-time activity peak in July 2022.
- Third-party incidents, such as supply chain attacks, accounted for 17% of all reported intrusions in 2021, up from only 1% in 2020.
Malicious PyPI packages: DevOps security firm Phylum said it found 29 newly published PyPI packages that tried to install a version of the W4SP Stealer on developer's devices.
SocGolish on media sites: Proofpoint also detected this week a compromise of the infrastructure of a media company, through which malicious code linked to the SocGolish operation was deployed on more than 250 news sites across the US. [Additional coverage in DarkReading]
Proofpoint Threat Research has observed intermittent injections on a media company that serves many major news outlets. This media company serves content via #Javascript to its partners. By modifying the codebase of this otherwise benign JS, it is now used to deploy #SocGholish.
— Threat Insight (@threatinsight) 5:55 PM ∙ Nov 2, 2022
P2P botnets: Qihoo 360's Netlab network security division has a review of today's most active IoT P2P-based botnets. The list, based on botnet size and activity, includes Pink, Hajime, Mozi, FritzFrog, and Panchan.
Black Basta linked to FIN7: In a report on Thursday, SentinelOne researchers linked the Black Basta ransomware operation, which launched in April 2022, to the FIN7 cybercrime cartel. Previously, in a report last year, Microsoft said that a FIN7 subgroup—named Elbrus— created and ran the Darkside and BlackMatter RaaS operations as well.
Robin Banks moves to Russia: Cybersecurity firm IronNet said that after they exposed a new phishing-as-a-service (PhaaS) platform named Robin Banks earlier in July, the service had to relocate servers to a Russian hosting provider after Cloudflare booted the gang off its infrastructure.
Crimson Kingsnake BEC gang: Abnormal Security said it observed a BEC gang they have codenamed as Crimson Kingsnake target organizations across the globe by impersonating law firms. The security firm said that based on its investigation, "at least some of the actors associated with Crimson Kingsnake may be located in the United Kingdom."
Pre-orders reach the dark web: Hoo-ray for innovation, I guess!
More customer-friendly updates in the cybercrime ecosystem: the Russian Market marketplace has recently introduced a "preorder logs" feature, allowing cybercriminals to track compromised URLs of their interest and easier purchase sensitive credentials.
— KELA (@Intel_by_KELA) 2:46 PM ∙ Nov 2, 2022
Malware technical reports
IcedID: Elastic's security team has a breakdown of the command and control infrastructure of the IcedID trojan and how defenders can track.
OrcusRAT: The ANY.RUN team has a report out on the Orcus remote access trojan, first released in 2016 by a Canadian coder, but still active even today.
BlueFox: Sekoia researchers have analyzed BlueFox, a new information stealer they spotted in September that is being offered to the cybercriminal underground as a new Malware-as-a-Service portal.
Raccoon Stealer v1: Team Cymru's S2 research team published a report on Thursday on the infrastructure used by the first iteration of the Raccoon Stealer malware. Researchers said that based on their analysis of the malware's infrastructure, they tracked Raccoon's server infrastructure to the city of Kharkiv, Ukraine, and also found that payment card data stolen from user systems through the Raccoon malware was sold on CC2BTC, an underground carding marketplace operated by the Raccoon gang themselves. CC2BTC went down in March, just like the entire Raccoon v1 operation, when one of its core devs, a Ukrainian national, was detained in the Netherlands.
Elbie and Surtr ransomware: AhnLab warned this week about a campaign distributing the Elbie ransomware across South Korea disguised as an IE add-on (out of all the stupid distribution lures). They also published a second warning about a campaign distributing the Surtr ransomware.
Well-known in security circles, much ransomware refuses to run if it detects you're in Russia.
— SwiftOnSecurity (@SwiftOnSecurity) 1:27 AM ∙ Nov 2, 2022
Surtur, rented by gangs, will literally display a message "WARNING. Surtr does not run in this country if you do it again you will be banned."
(Via @nscrut_)
Welcome back, Emotet: After stopping operations back in June, the Emotet botnet is back at its old tricks, sending out new email spam waves in search of new victims. [Additional coverage in BleepingComputer]
🚨Emotet back in Distro Mode🚨 - As of 0800 UTC E4 began spamming and as of 0930 UTC E5 began spamming again. Looks like Ivan is in need of some cash again so he went back to work. Be on the lookout for direct attached XLS files and zipped and password protected XLS. 1/x
— Cryptolaemus (@Cryptolaemus1) 1:04 PM ∙ Nov 2, 2022
APTs and cyber-espionage
Torii and Ocean Lotus: In a report on Wednesday, Chinese IT company Weibu claimed that OceanLotus, a Vietnamese cyber-espionage group, is behind Torii, an IoT botnet that was first seen back in 2018. Weibu researchers say that OceanLotis, also known as APT32, has been using systems infected by Torii to hide their operations, such as attacks and command-and-control traffic.
Lazarus attacks on South Korea: Researchers from Chinese security firm Antiy have a report out on a series of Lazarus APT attacks against South Korean organizations. AhnLab has one too.
APT36: Zscaler has a report on APT36, a Pakistan-based threat actor, and its operations targeting the Indian government (obviously).
RomCom: BlackBerry's security team has a technical report on a suspected nation-state operation that appears to be using a backdoor typically employed by the cybercrime ecosystem to go after targets in Ukraine and the United Kingdom. This campaign, first spotted by CERT-Ukraine, is using cloned websites for popular enterprise software tools like SolarWinds Network Performance Monitor, KeePass Open-Source Password Manager, and PDF Reader Pro, to host boobytrapped versions of the respective tools, backdoored with a version of the RomCom RAT.
"Given the geography of the targets and the current geopolitical situation, it's unlikely that the RomCom RAT threat actor is cybercrime-motivated."
Think of the malware here as a service being provided to various parties doing their own phishing.
— Tyler McLellan (@tylabs) 5:50 PM ∙ Oct 23, 2022
Vulnerabilities and bug bounty
Next.js vulnerability: A vulnerability in the IPX component of Netfify's Next.js JavaScript framework allows a persistent cross-site scripting (XSS) and full-response server-side request forgery (SSRF) attack on any website that relies on the framework, including many of today's JS-based static site generators and many cryptocurrency portals.
Beware of leaks to URLscan.io: German security firm Positive Security published a very interesting blog post this week on how security tools and online services could accidentally leak URLs for private or sensitive web pages to URLscan.io, a service integrated by many tools and websites and used to scan for malicious URLs. GitHub knows how painful this is. kek
Infosec industry
Intel 471 acquires SpiderFoot: Threat intelligence giant Intel 471 announced it acquired this week SpiderFoot, a provider of open-source intelligence, attack surface management, and digital investigations resources.
HUMAN acquires clean.io: HUMAN Security (formerly White Ops) announced it acquired clean.io, a service for protecting websites against malvertising and e-commerce fraud.
New tool—openssl-tools: DevOps security firm JFrog has published scanners to test your apps and see if they are vulnerable to the recently patched OpenSSL vulnerabilities CVE-2022-3602 and CVE-2022-3786.
RIP Vitali: The US Coast Guard announced on Wednesday they recovered the body of security researcher Vitali Kremez after the AdvIntel CEO went missing on Sunday during a scuba diving trip. Infosec news outlet DarkReading has an obituary on Vitali's storied career. May he rest in peace!
#UPDATE5/#FINAL Mr. Vitali Kremez's body was recovered by local authorities Wednesday.
— USCGSoutheast (@USCGSoutheast) 4:02 PM ∙ Nov 2, 2022
"We'd like to express our deepest condolences to the loved ones of Mr. Kremez," said CWO Edgardo Insignares, a Sector Miami command duty officer. #SAR




