Risky Biz News: One month later, the Profanity vulnerability is still making new victims
In other news: New Chrome zero-day; Liz Truss phone compromised by Russian hackers; timing attacks on privacy IM services.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
More than a month after 1inch Network disclosed a severe vulnerability in Profanity, a tool to generate vanity (customized) Ethereum addresses, cryptocurrency platforms are still getting hacked and losing funds to a vulnerability everyone told them to take seriously.
The latest platform to add its name to the list of Profanity victims is DeFi platform FriesDAO, which confirmed on Friday that it lost $2.3 million worth of cryptocurrency tokens after an attacker took control over one of its smart contracts through "a profanity attack vector."
FriesDAO joins the likes of Wintermute (which lost $160 million), QANplatform (lost $2 million), Indexed Finance (lost $3.3 million), and REFI (lost $300,000).
The Profanity tool allows users to generate Ethereum addresses that contain custom text in the public address. The tool was typically used for branding purposes, to generate addresses that contained a person or company's name, either at the start, middle, or end of the address.
Profanity did this by rotating and computing through millions of private encryption keys until it found one that generated a public Ethereum address of a user's liking.
The user would then take this public address and use it to store funds or smart contracts and use the private key to authenticate themselves as the owner of that address or smart contract.
Explained in layman terms, the Profanity vulnerability allows a threat actor to reproduce this process and determine the private key of a vanity Ethereum address that was generated in the past through the app.
This entire process is pretty fast and simple, according to reports, and all an attacker has to do is identify vanity addresses on the Ethereum blockchain.
For cryptocurrency platforms, scanning their own infrastructure for vanity addresses should be pretty simple since, well, it's their own infrastructure, and they should know what exactly they are running. But as new hacks come to light, it's apparently something that the cryptocurrency community can't be bothered with these days.
1/ We confirmed that both @paraswap deployer address (0x490ce4616672e93b1c8f5e43aa80312fd73dee8c) and @Curve deployer address(0x07a3458ad662fbcdd4fca0b1b37be6a5b1bcd7ac) are vulnerable to the profanity vulnerability. The private keys can be recovered.
— BlockSec (@BlockSecTeam) 9:43 AM ∙ Oct 11, 2022
Breaches and hacks
Amazon server leak: Amazon said there was a "deployment error" with one of its Amazon Prime analytics servers that was left exposed online without a password for more than two weeks and leaked 215 million entries containing pseudonymized user data. According to TechCrunch, which first reported on the leak, the leaked data contained the name of the show or movie that a user was streaming, on what device it was streamed, Prime subscription details, and network quality.
Aurubis attack: Aurubis, the second-largest copper producer in the world, disclosed a cybersecurity incident on Friday in what the company described as "apparently part of a larger attack on the metals and mining industry." The company said the incident didn't impact its production or environmental protection systems at smelter sites.
General tech and privacy
Telegram gets a one-day block in Russia: Russia's telecommunications watchdog, the Roskomnadzor, blocked Telegram's t.me short URL on Saturday after a copy of a video was uploaded on the platform containing instructions on how Russian soldiers could surrender to the Ukrainian Armed Forces, once deployed in Ukraine. The URL was not in Roskomnadzor's blocklist on Sunday, suggesting the block was lifted after only one day.
Government, politics, and policy
Liz Truss phone compromised: The personal smartphone of Liz Truss, the former UK Prime Minister, was compromised by Russian state hackers. According to a Daily Mail report, the hack took place over the summer while Truss was still Foreign Secretary, and the incident was suppressed by Boris Johnson's cabinet to maintain her chances at becoming the next Prime Minister. According to the newspaper, the incident was considered so severe that UK security services took Truss' phone and locked it in a secure location. Truss was also forced to change the number she had been using for the last ten years.
CIA agent under investigation: The Associated Press reported that the FBI started an investigation of Kevin Chalker, a former CIA agent who worked for the Qatar government and allegedly orchestrated a hacking and spying operation against officials from rival soccer federations bidding for the 2022 World Cup.
Poland and Slovakia: In a series of DDOS attacks, Pro-Russian hacktivist groups have targeted the IT networks of the Parliaments of Poland and Slovakia. The attacks targeting Poland's Parliament came after the government passed a resolution recognizing Russia as a terrorist state and brought down the Senate's website. The attack targeting Slovakia's Parliament systems was far more severe, and the body had to suspend its voting session on Thursday due to the IT system being down.
US DDOS guidance: CISA, the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) have published a joint advisory [PDF] on dealing with and reducing the impact of distributed denial of service (DDOS) attacks.
Threat to Canada: The Canadian Centre for Cyber Security, Canada's technical authority on cyber security, published an assessment of potential cyber threats its citizens and the government would most likely face through the next years, in 2023 and 2024. Among the listed threats are ransomware (because of course, ransomware), the threat to critical infrastructure because of the increased internet-connectivity of OT networks, increased state-sponsored activity, influence operations trying to degrade trust in online spaces, and the emergence of new disruptive technologies like machine learning automation and quantum computing.
US military cyber team's defense of Ukraine: The BBC has a profile on a team of US military cybersecurity experts that have been helping the Ukrainian government protect their network.
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
DiDW arrest: German police detained a 22-year-old student for managing "Deutschland im Deep Web" (Germany on the Dark Web), the largest dark web marketplace catering to German-speaking users. The portal has been online since 2013 and has been known to sell drugs, weapons, and ammunition, being the website from where the perpetrator of the 2016 Munich terrorist attack also procured his weapons.
Old vulnerabilities are still everyone's favorites: An F5 Labs report citing data from their network of honeypots shows that the vast majority of malicious scanning and exploitation targeted older vulnerabilities dating as far back as 2017 and 2018, rather than new, recently-disclosed ones, with the most targeted one being CVE-2018-13379, a directory traversal issue in Fortinet SSL VPNs.
New ransomware strains: Fortinet researchers have a summary of new low-tier ransomware samples that have been observed in the wild over the past month, including some classic "seized by FBI" garbage and two new strains calling themselves Wise Guys and Pyschedelic.
Droppers on the Play Store: ThreatFabric researchers have published a report on the recent tricks used by Android droppers to bypass the new Android 13 security features and deploy their malware on the Play Store. The company is reporting on campaigns that infected at least 130,000 users with bankers like Sharkbot and Vultur.
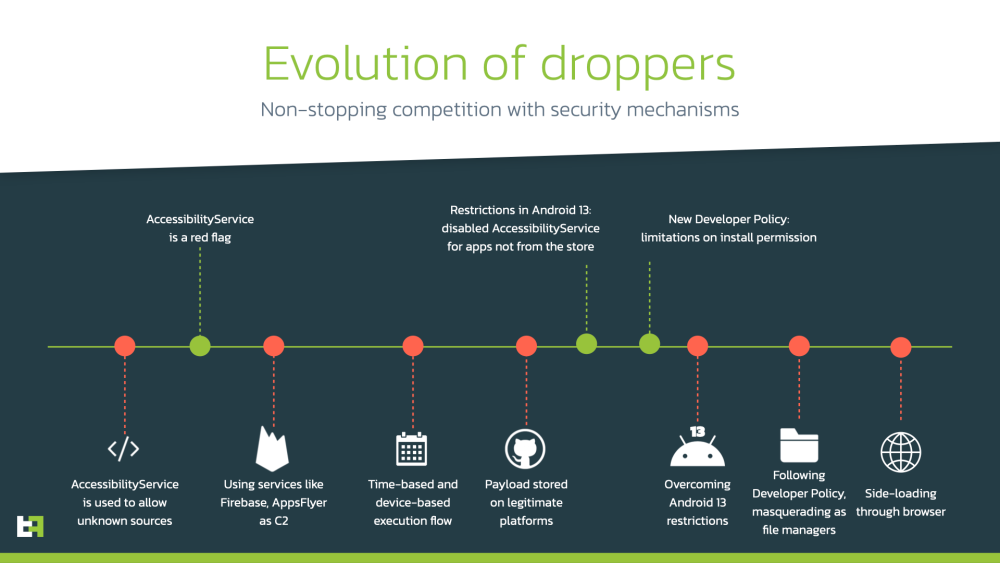
Malware technical reports
Guloader: Palo Alto Network's Unit 42 has taken a deeper look at the recent defenses added to the Guloader malware meant to protect its code from security sandbox analysis and human security researchers trying to analyze its code.
Emotet: Elastic's security team has published an analysis of Emotet's new encoding format the malware uses to store and protect its configuration.
QAKBOT: Trend Micro has a report out on the QAKBOT trojan and its use of valid certificates to sign some of its modules, a technique the botnet has used all summer long.
"A look at the abused certificates also reveals that they were not issued to non-existent organizations for abuse, but rather valid certificates issued to real existent organizations through proper process."
APTs and cyber-espionage
APT-Q-36: QiAnXin researchers have published a report on a recent campaign carried out by the APT-Q-36 threat actor, also known as PatchWork or White Elephant. The final payload in this attack was a malware strain known as the BADNEWS trojan.
Cranefly: Broadcom's Symantec team published a report last week on a recent trick used by the Cranefly APT, which uses the logs of IIS servers to send commands to infected servers.
ShadowPad C2 servers: In a report last week, the VMware security team said they found more than 80 command and control servers for ShadowPad, a backdoor trojan typically used in intrusions by Chinese state-sponsored hacking groups. VMware said it identified the servers after it analyzed the ShadowPad command and control protocol for new ways to fingerprint the malware's network traffic.
GFI report: Cybersecurity research group Hacker's Choice has published an analysis of the Great Firewall of Iran (GFI), the Iranian government's internet censorship system, which has been glowing red for more than a month since the onset of the Mahsa Amini protests.
Influence operations: Google's TAG security team has published a summary of the coordinated influence operation campaigns terminated on Google platforms in Q3 2022. Campaigns linked to China and Russia were taken down, but also operations linked to the US, Vietnam, Turkey, Iran, Sudan, North Macedonia, and Myanmar.
Vulnerabilities and bug bounty
Chrome zero-day: Google released Chrome v107.0.5304.87 to fix CVE-2022-3723, a zero-day vulnerability exploited in the wild. This is the seventh Chrome zero-day patched this year.
ConnectWise RCE: Managed service provider ConnectWise released a critical security update on Friday to address a remote code execution vulnerability in two of its backup server solutions that could be used to take over vulnerable and unpatched systems. Details about the vulnerability are still kept private, at least until Monday, when Huntress Labs CEO Kyle Hanslovan promised to release more details. At least 4,800 ConnectWise servers are still exposed online and most likely are still vulnerable, as the patch came late on Friday, and very few administrators learned of it in time to roll out the fix.
Galaxy Store XSS: An anonymous researcher said he found an XSS vulnerability in the Samsung Galaxy Store that can allow a threat actor to cause the store to install and/or launch any desired application, leading to situations where malicious apps can be remotely installed on users' devices.
Juniper vulnerabilities: Octagon Networks published details on six vulnerabilities in Juniper's SSL VPN products, including a pre-auth RCE tracked as CVE-2022-22241.
Windows zero-day analysis: Zscaler researchers have published part two of a technical analysis of CVE-2022-37969, a zero-day vulnerability in the Windows OS that they spotted exploited in the wild. Microsoft patched the vulnerability in the September 2022 Patch Tuesday. Part one link here.
MotW bypass micropatch: ACROS Security has released a micropatch for a recently discovered bypass for Microsoft's Mark of the Web (MotW) security feature.
Timing attacks on IM services: A team of academics identified a timing attack that can be performed on the read/delivery status notification feature of modern instant messaging services that can allow an attacker to distinguish different receivers and their locations by sending them instant messages. The attack works with 80% accuracy, and researchers successfully tested it against privacy-first services like Signal, WhatsApp, and Threema.
"While making use of this side channel is mostly limited to people who are in each others' contact lists and have already started a conversation before, it yet comprises an unexpected and privacy-infringing act with low technical requirements that is equally hard to detect and to mitigate for a potential victim."
Infosec industry
New tool—Legitify: DevOps security firm Legit Software has open-sourced this month a new tool called Legitify that can detect and remediate misconfigurations, security, and compliance issues across GitHub assets.
New tool—Dastardly: Security firm PortSwigger open-sourced a new Burp Suite extension named Dastardly that can scan your CI/CD pipeline for possible vulnerabilities in your code.
New tool—Spartacus: Software giant Accenture has open-sourced a new tool called Spartacus, a tool for discovering DLLs vulnerable to hijacking.




