Risky Biz News: ODNI report highlights China as the US' biggest cyber threat
In other news: Google and Meta sue South Korea's privacy agency; hackers steal data of US House members and staff; Google discontinues Chrome Cleanup Tool.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The Office of the Director of National Intelligence (ODNI) has published this week its yearly threat assessment, a report that aggregates intelligence insights on the US' main adversaries.
The 40-page unclassified report [PDF] covers a wide variety of topics ranging from military capabilities to space programs and economic threats. Cyber and influence operations were also included, which we will try to summarize here—in case you don't want to read the whole thing or watch the hearing.
China:
- ODNI views China as "the broadest, most active, and persistent cyber espionage threat to US Government and private-sector networks."
- The US says "China almost certainly is capable of launching cyber attacks that could disrupt critical infrastructure services within the United States, including against oil and gas pipelines, and rail systems."
- In the case of a major conflict, the US believes China would "almost certainly consider undertaking aggressive cyber operations" against US critical infrastructure and military assets.
- In terms of current operations, the US says China regularly targets both its own population and foreigners who criticize the regime.
- Other strategic targets include telecommunication firms, providers of managed services, broadly used software, and other targets "rich in follow-on opportunities for intelligence collection, attack, or influence operations."
- In terms of influence operations, "China is attempting to sow doubts about US leadership, undermine democracy, and extend Beijing's influence, particularly in East Asia and the western Pacific, which Beijing views as its sphere of influence."
Russia:
- ODNI notes that even if Russia's cyber operations in Ukraine fell short of expectations, Russia still remains a top-tier cyber adversary since it views "cyber disruptions as a foreign policy lever to shape other countries' decisions."
- Currently, the US sees Russia "particularly focused on improving its ability to target critical infrastructure" using cyber, including "underwater cables and industrial control systems."
- In terms of influence operations, ODNI considers Russia to be "one of the most serious foreign influence threats to the United States."
- To achieve this, ODNI says Russia uses a mix of intelligence services, websites, individuals, and organizations that appear to be independent news sources, and even US media outlets and US politicians.
"Russia and its influence actors are adept at capitalizing on current events in the United States to push Moscow-friendly positions to Western audiences. Russian officials, including Putin himself, and influence actors routinely inject themselves into contentious US issues, even if that causes the Kremlin to take a public stand on US domestic political matters."
Iran:
- As for Iran, ODNI notes the country's "growing expertise and willingness to conduct aggressive cyber operations."
- ODNI notes that most of Iran's attacks appear to be opportunistic but that the Tehran regime has shown a willingness to push back against the US in cyberspace as a way to show strength—as it recently did with a coordinated series of cyberattacks against Albania and Israel.
North Korea:
- ODNI sees North Korea's cyber forces as "mature" and fully capable of achieving a wide set of goals. It does not rule out that North Korean hackers can "cause temporary, limited disruptions of some critical infrastructure networks and disrupt business networks in the United States."
- ODNI also confirms previous US IC and UN reports that North Korea is using its military hackers to conduct cryptocurrency heists and use the funds to power its military and WMD programs.
Other topics:
- ODNI warns that centralized databases of health and genomic data will become main targets for cyber operations, with China already engaging in such attacks/thefts already.
- The proliferation of spyware and other surveillance tools "will continue to threaten US interests." ODNI says some governments have expanded the use of spyware from law enforcement investigations to going after political rivals, journalists, and dissidents—even if they reside in foreign countries, such as the US.
- ODNI warns that China has shown "willingness to enlist the aid of China-based commercial enterprises to help surveil and censor PRC critics abroad."
Breaches and hacks
DC Health Link hack: DC Health Link, the organization that provides health care plans for US House members and staff, has sent out a notification to government officials about a "significant breach." According to CNN, DC Health Link learned of the breach a day after a threat actor started selling the personal data of 170,000 DC Health Link enrollees on an underground hacking forum. NBC News reported that the FBI confirmed the hack by buying a sample of the hacked data. Hours after the breach got extensive media coverage, the forum topic advertising the stolen data was taken down, although it remains unclear why.
AT&T breach: US telecommunications provider AT&T is notifying customers of a security breach at one of its vendors that exposed the account information of some users. Only technical CNPI information was exposed. According to AT&T, no personal information was exposed. The breach impacts roughly 9 million customers.
Tender.fi crypto-heist: A hacker stole this week more than $1.59 million worth of crypto-assets from DeFi platform Tender.fi after exploiting a vulnerability in the platform's loaning contracts. A day after the hack, Tender.fi said it reached an agreement with the exploiter, who returned the stolen funds and was awarded 62 ETH ($96,500) as a bug bounty reward for "helping secure the protocol."
CommBank incident: Commonwealth Bank of Australia says that its Indonesian branch has been hit by a cyber-attack during which a threat actor managed to gain access to a web-based software application used for project management. Officials say that its Indonesian branch, known as PT Bank Commonwealth, has remained operational as they investigate the breach.
Black & McDonald incident: A ransomware attack has hit Black & McDonald, a Canadian engineering company that works as a major contractor for Canada's military and critical infrastructure sectors.
Radios in Russia hacked again: Radio stations across Russia have been hacked again to broadcast fake air raid missiles. The hacks come after a similar incident at the end of February. This time around, some TV stations were also compromised to broadcast the air raid warnings.
Acronis suspected hack: A threat actor claims to have hacked backup provider Acronis and has leaked 12GB of the company's data on an underground hacking forum. The hacker is the same individual who took credit for the Acer hack earlier this week. In a statement to Russian media, an Acronis spokesperson denied the breach, claiming "there is no leak."
Update: Acronis has reached out to say their statement was misquoted in Russian media. The company acknowledged the incident in a LinkedIn post, and provided more context to what happened. Also included below:
Based on our investigation so far, the credentials used by a single specific customer to upload diagnostic data to Acronis support have been compromised. We are working with that customer and have suspended account access as we resolve the issue. We also shared IOCs with our industry partners and work with law enforcement.
No other system or credential has been affected. There is no evidence of any other successful attack, nor there is any data in the leak that is not in the folder of that one customer. Our security team is obviously on high alert and the investigation continues.
General tech and privacy
LSA protection coming to Windows 11: Microsoft plans to add an option to protect the Local Security Authority (LSA) user login service from attacks that may dump its memory and allow malicious apps to steal secrets and credentials. The LSA protection feature will be added to Windows 11 Canary builds before being rolled out broadly to the Windows 11 userbase.
Google discontinues Chrome Cleanup Tool: Google has discontinued the Chrome Cleanup Tool, an application that was pre-installed inside the Chrome browser on Windows. The app worked by scanning for any unexpected changes to Chrome settings and could remove unwanted software that was installed via Chrome. Google says the app, which it initially rolled out in 2015, had played its role and that in recent months it was detecting an increasingly smaller number of threats with each scan. The browser maker says that with Chrome v111, released last week, users won't be able to request new scans and cleanups, and they plan to gradually disable and remove the utility from user browsers.
"To date, it has performed more than 80 million cleanups, helping to pave the way for a cleaner, safer web. For example, last month just 0.06% of Chrome Cleanup Tool scans run by users detected known UwS."
Google and Meta sue SK's privacy agency: Google and Meta have sued South Korea's privacy watchdog (the Personal Information Protection Commission) after the agency imposed massive fines against both companies last year. PIPC imposed a 69 billion won ($52 million) fine on Google and a 31 billion won ($23 million) fine on Meta for breaking the country's privacy laws by not obtaining lawful consent from users and tracking their online activity for advertising purposes. In lawsuits filed last month, the two companies are now arguing that website operators should be responsible for obtaining user consent and not their platforms, which only receive and aggregate this data. [More in local media]
GitHub 2FA reminder: GitHub has reminded users that next week, on Monday, March 13, it will start requiring that users who contribute code on the platform must use a 2FA method to secure their accounts or they won't be able to log in.
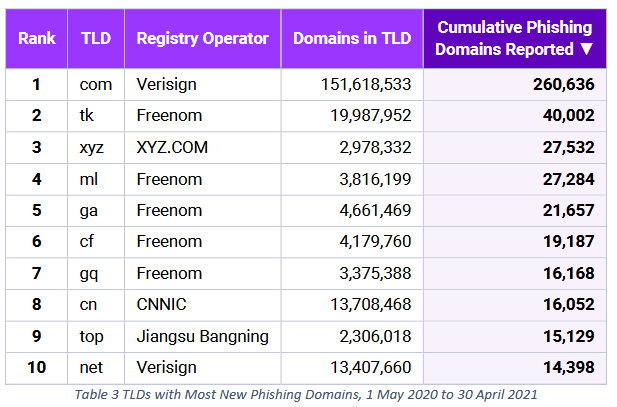
Freenom halts domain registrations: Domain registrar Freenom has halted new registrations. According to infosec reporter Brian Krebs, the move comes days after Meta sued Freenom. In court documents [PDF], Meta alleges that Freenom ignores abuse complaints and allows malicious sites to operate unimpeded, even monetizing some of the traffic. Freenom is the official domain name registry for top-level domains such as .cf (Central African Republic), .ga (Gabon), .gq (Equatorial Guinea), .ml (Mali), and .tk (Tokelau).
"The lawsuit points to a 2021 study (PDF) on the abuse of domains conducted for the European Commission, which discovered that those ccTLDs operated by Freenom made up five of the Top Ten TLDs most abused by phishers."
Government, politics, and policy
Mexican Army used Pegasus to spy on citizens: Two privacy watchdogs (R3D and Citizen Lab) have unearthed official documents confirming that the Mexican Army bought spyware tools from Israeli company NSO Group. Investigators say the recent documents confirm a report from last year that the Army used Pegasus spyware to spy on at least two journalists and a human rights defender investigating the Army killings of innocent civilians. The documents pin the blame on the Mexican Secretariat of National Defense (SEDENA), and a previously unknown and newly formed military intelligence agency.
CISA still behind the curve: A report [PDF] by the DHS Office of the Inspector General found that two years after the SolarWinds hack, the Cybersecurity and Infrastructure Security Agency (CISA) still lacks the resources, manpower, and a basic blueprint for responding to major hacks against American infrastructure. The report highlights CISA's efforts to boost its visibility and ability to respond but also notes that "until these efforts are completed, CISA may not always be able to effectively detect and mitigate major cyberattacks or meet the Government's demand for cyber capabilities that protect Federal networks and systems."
GSA lied about Login.gov security: A report [PDF] from the Inspector General of the General Services Administration has found that GSA officials intentionally misled federal agencies about the security features of Login.gov, an identity and authentication single sign-on service developed by the GSA for use across the US government. The report found that GSA claimed the system met NIST and federal cybersecurity standards even if they knew this was not the case. The Inspector General says that GSA proceeded to roll out the platform to 22 federal agencies and bill them $10 million instead of notifying them of the current issues. [Additional coverage in FWC]
New TSA cybersecurity rules: The US Transportation Security Administration (TSA) has released new cybersecurity requirements for airports and aircraft operators. The new regulation effort comes after the TSA also issued new cybersecurity rules for passenger and freight railroad carriers in October last year. Basic requirements include:
- Develop network segmentation policies and controls to ensure that operational technology systems can continue to safely operate in the event that an information technology system has been compromised, and vice versa;
- Create access control measures to secure and prevent unauthorized access to critical cyber systems;
- Implement continuous monitoring and detection policies and procedures to defend against, detect, and respond to cybersecurity threats and anomalies that affect critical cyber system operations; and
- Reduce the risk of exploitation of unpatched systems through the application of security patches and updates for operating systems, applications, drivers, and firmware on critical cyber systems in a timely manner using a risk-based methodology.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Sachkov investigation concludes: The FSB, one of Russia's intelligence agencies, says it concluded the investigation into Ilya Sachkov, the founder and former CEO of Russian cybersecurity firm Group-IB. Sachkov was detained in September 2021 on "treason charges." Many experts speculated at the time that Sachkov was detained after his company provided information on Russian hackers to foreign law enforcement agencies without the state's explicit consent (Russia likes to protect its national treasures, such as cybercriminals). RIA Novosti, which reported on the FSB investigation, didn't specify what the result of the investigation was or if Sachkov is expected to be released or go to jail.
Emotet returns (again): After more than three months of inactivity, the Emotet botnet has returned to life with new email spam campaigns originating from one of its server clusters. According to Cofense, Emotet is currently sending out emails purporting to contain tax records. The emails carry ZIP archives of 500 MB or more containing bloated Word documents, artificially increased in weight on purpose to make it harder for antivirus solutions to scan their contents and detect the Emotet payload.
OneNote malspam: Trustwave has a two-part report on how cybercrime groups are currently abusing OneNote documents to distribute malware.
Play-to-Earn games PSA: The US Federal Bureau of Investigations has published a PSA this week warning US consumers that cybercriminals are running play-to-earn games that secretly steal their cryptocurrency. The FBI says these games typically ask users to link a cryptocurrency wallet, but they also contain malicious code that empties a user's wallet after a period of time.
FSB's hand in Russia's cybercrime underground: Novaya Gazeta has an interview with Viktor Kalinin, a former Group-IB employee who's currently living in Poland, under political asylum, after having fled Russia. According to Kalinin, Russia's FSB intelligence agency is aware of "99.9%" of all hackers active on the Russian underground. (via Oleg Shakirov)
Another Israeli spyware vendor: A Haaretz investigation has uncovered another local Israeli company that sells surveillance technology overseas. The company, named NFV Systems, is believed to have sold spyware and tracking technology to multiple Gulf states. Haaretz says the company is currently under investigation by the Israeli government for skirting arms export controls.
Malware technical reports
Royal ransomware: SecurityScorecard has a technical analysis of the ESXi variant of the Royal ransomware.
IceFire ransomware returns: The IceFire ransomware gang has returned to life after months of inactivity. The gang was previously active last year, carrying out targeted ransomware attacks between March and September, before mysteriously disappearing without a word. Now, SentinelOne says it's seeing new attacks from the IceFire gang, including intrusions where the gang has deployed a new version of their ransomware that can encrypt Linux systems. SentinelOne says the IceFire ransomware gang is also the threat actor exploiting a recently-patched vulnerability (CVE-2022-47986) in IBM Aspera servers that CISA warned about last month.
iswr ransomware: AhnLab says that a decryptable version of the iswr ransomware has been spotted being distributed across South Korea.
RoadSweep wiper: Chinese security firm Rising has published a technical analysis of RoadSweep, the wiper used by Iranian hackers against the Albanian government last July.
PlugX USB worm: Sophos says it is seeing outbreaks of the new PlugX USB worm pop up in various countries around the world, such as Mongolia, Ghana, Zimbabwe, and Nigeria. PlugX is remote access trojan that was developed and initially used by Chinese cyber-espionage groups but has since leaked and been adopted by many other Chinese threat actors as well. A variant of this malware that included a USB worming feature was first spotted earlier this year.
Prometei botnet: Cisco Talos researchers say they have spotted v3 of Promotei, a crypto-mining botnet that has been active since 2020. Cisco says that after managing to sinkhole the botnet's DGA domains for a week in February, they believe the botnet is currently controlling more than 10,000 infected devices. Cisco says that one of the major changes in the Prometei code appears to be a change in the list of "excluded countries where the malware won't run. While previous versions would exclude infections in CIS countries, v3 only blocks infections in Russia.
ScrubCrypt: After Perception Point's report on the new ScrubCrypt malware crypter, Fortinet has also published its analysis on the service.
Sponsor Section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
APTs and cyber-espionage
SonicWall attacks: Google's Mandiant division has discovered a suspected Chinese threat group engaging in attacks on SonicWall Secure Mobile Access (SMA) servers. Mandiant says the group, which they are currently tracking as UNC4540, focuses on planting malware on unpatched SonicWall SMA servers and "maintaining long term persistence." Mandiant says UNC4540 deploys a variant of the TinyShell backdoor, whose primary purpose appears to be to steal hashed credentials from all users logged in on the SonicWall device. Researchers say they tracked down some UNC4540 attacks as far as 2021 and that their malware "has persisted through multiple firmware updates."
Cobalt Illusion: Secureworks researchers have identified a phishing campaign that targets researchers who document the suppression of women and minority groups in Iran. The group, which Secureworks tracks as Cobalt Illusion, was seen impersonating a member of the Atlantic Council to reach out to victims, build rapport, and then lead targets to phishing sites. Cobalt Illusion is a group also known as Charming Kitten, APT42, Phosphorous, TA453, and Yellow Garuda.
Vulnerabilities and bug bounty
Fortinet updates: Fortinet has published 15 security bulletins this week to address various security flaws, including CVE-2023-25610, a bug that can lead to DOS or unauth RCEs. Although RBN learned of some rumors last week that Fortinet was looking into this as a possible zero-day, the company said it found no evidence it was abused in the wild.
HomeAssistant auth bypass: HomeAssistant, a popular open-source home automation software, has released a security update to patch a severe vulnerability in its product. Tracked as CVE-2023-27482, the vulnerability can allow allowed threat actors to bypass authentication and gain control over HomeAssistant systems. HomeAssistant released the security update on March 1, and a third of its userbase already installed the patch.
CorePlague vulnerabilities: AquaSec researchers have discovered a chain of vulnerabilities in the Jenkins open-source automation server. Tracked as CVE-2023-27898 and CVE-2023-27905, but collectively known as CorePlague, the two bugs allow unauthenticated remote code execution attacks on Jenkins servers, even if the servers are not directly accessible to the attackers. The Jenkins team patched both issues (and others) in an update this week.
PwnAgent: Security researcher Zion Leonahenahe Basque has published details about PwnAgent (CVE-2023-24749), a one-click remote code execution bug in the WAN interface of Netgear RAX routers. The bug was used during the Pwn2Own 2022 hacking contest.
Imposter commits: Chainguard has a report on a new type of threat to Git repositories, namely, a technique called imposter commits.
Joomla under attack: Threat actors are exploiting a recently-patched vulnerability in the Joomla CMS. Tracked as CVE-2023-23752, the vulnerability allows unauthorized access to a site's endpoints, which can lead to the exposure of a site's Joomla database username and password.
KEV update: CISA has updated its KEV database with three new vulnerabilities that are currently being actively exploited. All three are vulnerabilities reported and patched last year but which only now have come under active exploitation. The first is CVE-2022-28810, an RCE in Zoho ManageEngine ADSelfService Plus. The second is CVE-2022-33891, a bug that was first exploited in July last year (it took a while for CISA to add this one). The third is CVE-2022-35914, an RCE in the Teclib GLPI IT inventory management app.
CISA KEV blind spot: Vulnerability intelligence company VulnCheck says it identified 42 vulnerabilities that were exploited in the wild in 2022 and which were not added to CISA's KEV catalog of actively-exploited bugs. VulnCheck says that three-quarters of the 42 vulnerabilities were used by threat actors to gain initial access to unpatched systems. The vast majority were used by botnet operators.




