Risky Biz News: NVD backlog unlikely to get addressed by September
In other news: The CrowdStrike lawsuits are coming; ESXi servers targeted in ransomware wave; crypto-exchange to "socialize" hack losses among all users.

This newsletter is brought to you by no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

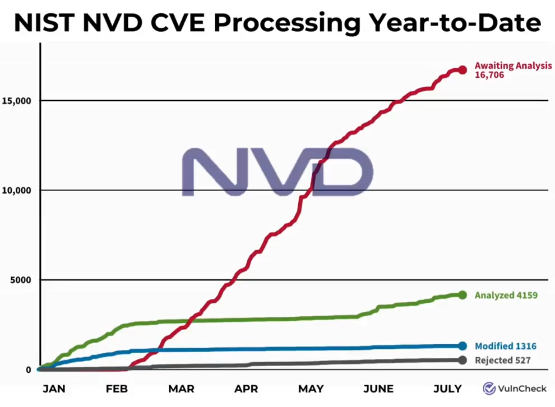
New numbers released at the end of last week suggest that US NIST is unlikely to make any significant progress in addressing a backlog of unprocessed vulnerabilities at the National Vulnerability Database (NVD).
The backlog began in February when NIST analysts slowed down the rate at which they were processing and enriching NVD entries, releasing many CVEs with little to no information about the nature of the security flaw, severity scores, and fixed or vulnerable software versions.
The slowdown had a major impact on the vulnerability management section of the cybersecurity community, which was relying on these entries to help inform customers about which bugs to patch first.
Several software companies and security researchers began a public effort to have the government step in and help the agency.
At the end of May, NIST announced that it hired a new contractor to help with the backlog, with a stated goal of clearing the backlog by the end of September.
This has not materialized into anything tangible. New numbers released by Fortress and VulnCheck show that the NVD backlog has grown to a whopping 17,000 vulnerabilities still awaiting processing.
The research also shows that the number of unprocessed vulnerabilities has steadily increased since the May announcement.
With two months left, NIST is extremely unlikely to address the backlog in due time.
According to Fortress, if left like this, the NVD backlog is expected to hit almost 30,000 unprocessed vulnerabilities by the end of the year.
Breaches, hacks, and security incidents
KDIC hack: The South Korean government is investigating a leak of sensitive data that exposed the identities of undercover agents operating abroad. The leak took place at the Korean Defense Intelligence Command (KDIC), the country's military intelligence agency. Reports in local media claim the leaked data contained information on agents and operations related to North Korea. Officials say they've identified the source of the leak as one of its employee's laptops. It's unclear if the device was hacked or if the employee was the one who intentionally shared the data.
Electoral Commission hack: The UK ICO has publicly reprimanded the UK Electoral Commission for its 2021 security breach. The incident exposed the data of approximately 40,000,000 voters. The ICO says the hack took place because of several unpatched vulnerabilities, including one in a Microsoft Exchange Server known as ProxyShell.
HealthEquity breach: American healthcare provider HealthEquity has disclosed a security breach that exposed the data of 4.3 million patients.
Avanpost hack: A pro-Ukrainian hacker group named the Cyber Anarchy Squad has hacked Russian security firm Avanpost. The group claims it breached the company over the weekend and encrypted more than 400 virtual machines hosting employee workstations. The hackers claim to have destroyed more than 60 TB of data and also leaked 390 GB following the attack. Avanpost confirmed the incident on Sunday. [Additional coverage in The Record]
WazirX to "socialize" hack losses: Indian cryptocurrency exchange WazirX says it plans to "socialize" the losses from a recent mega-hack. The company intends to spread a $230 million loss across all customer accounts in a move that has been intensively criticized by its users. WazirX was hacked two weeks ago and has yet to resume operations. The company refused to answer questions on why it was not tapping its own profit reserves to make customers whole or at least lessen their losses. [Additional coverage in TechCrunch]
Casper breach: Cryptocurrency platform Casper Networks has suspended operations after disclosing a mysterious security breach.
General tech and privacy
CrowdStrike in legal trouble: Delta Airlines has hired a prominent law firm to seek financial damages from CrowdStrike and Microsoft in the aftermath of a major security outage earlier this month. The outage was caused by a buggy update to a CrowdStrike kernel driver that caused Windows systems to crash. Delta estimated it lost between $350 million and $500 million in the outage that forced flights to be grounded all over the world. Insurer Parametrix estimates that financial losses from the CrowdStrike IT outage could reach around $15 billion globally. [Additional coverage in CNBC]
More CrowdStrike outage stats: Ookla, the company behind DownDetecter, says the CrowdStrike outage generated more than 5 million user reports on its platform.
DigiCert revocation: DigiCert is revoking certificates for roughly 0.4% of its customer base after it learned of an issue in its domain control verification procedures. Only certificates verified through CNAME DNS entries are affected. The procedure relies on customers adding a new DNS CNAME record with a random string as a subdomain. This string is supposed to be prefixed using an underscore character. The company says it found a bug where the random verification string did not include the mandatory underscore character, breaking industry rules. DigiCert is now revoking all certificates verified through the faulty procedure.
Meta Texas lawsuit settlement: Meta has agreed to pay $1.4 billion to settle a 2022 lawsuit filed by Texas officials accusing the company of illegally capturing user facial scans for its facial recognition feature without authorization.
W3C calls for third-party cookies deprecation: Technical experts from the World Wide Web Consortium (W3C) have called on browser makers to remove support for third-party cookies. The organization has made its position clear after Google reneged on its promise to deprecate third-party cookies last week. The W3C Technical Architecture Group says Google undermined the work of other browsers and technical experts when it went back on a promise it made back in 2020.
OpenAI in trouble: A report from The Information claims OpenAI is in deep financial problems and is expected to report $5 billion in losses this year. Sources say the company may file for bankruptcy.
Cheap Azure logging: Microsoft has launched this week an inexpensive Azure logging plan designed for companies with lower budgets that need to comply with security and risk management requirements. The new plan is called Auxiliary Logs and is currently in public preview. It will be the lowest tier in the Azure Monitor logging service, below Basic Logs and Analytics Logs.
- Auxiliary Logs – Our new, inexpensive log plan that enables ingestion and management of verbose logs needed for auditing and compliance scenarios. These may be queried with KQL on an infrequent basis and used to generate summaries.
- Basic Logs – Improved to support even richer troubleshooting and incident response with fast queries while saving costs. Now available with a longer retention period and the addition of KQL operators to aggregate and lookup.
- Analytics Logs – This plan is designed for frequent, concurrent access and supports interactive usage by multiple users. This plan drives the features in Azure Monitor Insights and powers Microsoft Sentinel. It is designed to manage critical and frequently accessed logs optimized for dashboards, alerts, and business advanced queries.
Government, politics, and policy
Malaysia to require a social media license: Malaysia has passed new legislation that will require all social media sites with over 8 million registered users to obtain a license from the government. Officials say the licensing process will require companies to commit to fighting internet crime, such as scams, online fraud, cyberbullying, and CSAM. The new law will enter into effect at the start of next year. [Additional coverage in The Star]
Malaysia to develop internet "kill switch": The same Malaysian government is also working on a law that will create an internet "kill switch" mechanism designed to shut down the internet across the country. The new law will be tabled for discussions in the Parliament in October. As usual with these laws, the government claims it's to enhance online security and tackle cybercrime, and absolutely not for censorship and oppression. It makes perfect sense to shut down the internet for the entire country just because of a phishing campaign. [Additional coverage in The Strait Times]
Roskomnadzor to get new powers: The Russian government is working on giving its communications watchdog the legal power to take over and manage network traffic on behalf of local ISPs. Russian prosecutors will be able to flag "prohibited information" and order Roskomnadzor to remove it right away instead of having Roskomnadzor relay the orders to ISPs and wait for them to implement the ban. The new law effectively cuts out misbehaving or unruly ISPs from the process. Several Russian telecommunication providers have quietly opposed the country's fall into a complete dictatorship by delaying or misimplementing internet censorship orders. [Additional coverage in TASS]
Russia restricts SIM access: The Russian government passed new legislation that limits citizens from owning more than 20 phone numbers or SIM cards. The limit will be 10 phone numbers for foreign citizens. The new law also introduces new rules for the sale of SIM cards designed to prevent anonymous card registrations. Foreigners who want to buy a SIM card are now required to visit a telecom operator's store to have their biometrics collected. [Additional coverage in Interfax]
Warrants required for US border searches: A judge has ruled that US border agents need a warrant before performing device searches for people crossing the border, regardless if the traveler is American or a foreign citizen.
Combating Money Laundering in Cyber Crime Act: A Senate bill is seeking to expand and modernize the Secret Service's ability to combat transnational cybercrime and investigate suspicious transactions related to digital assets. [Additional coverage in CyberScoop]
ECB cyber stress test: The European Central Bank says it concluded a cyber resilience stress test of major European banks. The test launched in January this year and included 109 participants. The ECB tested how banks can recover from a cyber-attack that severely affected their core database systems. The test didn't target the banks' ability to prevent the attack but recover from a catastrophic event (CrowdStrike says "Hi!"). The results were not made public and will be included in the ECB's 2024 Supervisory Review and Evaluation Process.
Australia's Cyber Security Act: The Australian government is working on a law that would require companies to disclose when they pay ransom to hackers. Companies that fail to disclose a payment will face possible fines. The purpose of the new Australian Cyber Security Act is to help the government map the scale of ransom payments. According to the ABC, the Australian government appears to have given up on the idea of a ransomware payment ban.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Thomas Kinsella, co-founder and Chief Customer Officer of Tines, about figuring out what AI is really good for and taking advantage of it in automating workflows.

Cybercrime and threat intel
Coinbase phisher sentenced: UK authorities have sentenced a 24-year-old man to three-and-a-half years in prison for computer crime offenses. Elliott Gunton pleaded guilty to phishing over 500 Coinbase users and stealing more than $900,000 from their accounts. The offenses took place back in 2018 and 2019 when Gunton was aged 17 and 18. Gunton was previously sentenced to 20 months and released on time served for hacking British ISP TalkTalk in April 2018. [Additional coverage in the Norwich Evening News]
Fake wallet password leaks: Kaspersky warns that threat actors are using fake leaks of crypto-wallet passwords to entice users into downloading malicious files and infecting themselves with malware.
Influencers held for ransom: A Bloomberg report claims that threat actors are using Meta's copyright protection tools to extort Middle East influencers, asking for ransoms by threatening to have content removed from their accounts.
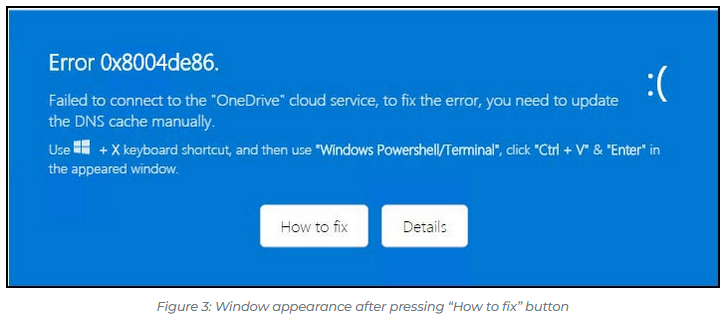
OneDrive pastejacking: Trellix looks at a phishing campaign that uses social engineering to trick users into copy-pasting and running malicious Powershell commands. Trellix says the attackers used lures of malfunctioning OneDrive files to trick users into running the commands.
New DISPOSSESSOR RaaS: DataBreaches.net has a look at a new Ransomware-as-a-Service platform that launched over the past two weeks named DISPOSSESSOR. The platform appears to be a LockBit clone and is run by two groups named RADAR and DISPOSSESSOR.
UNC4393 (Black Basta): Google says that a threat actor they are tracking as UNC4393, is the primary affiliate of the Black Basta ransomware and responsible for over 40 attacks since early 2022. The group has almost exclusively used the QakBot botnet for initial access until its takedown last year. Since then, Google says the group has switched to the newer DarkGate service. Once inside networks, UNC4393 typically deploys a custom backdoor named SILENTNIGHT to help with data exfiltration and the deploying of the Black Basta encryptor.
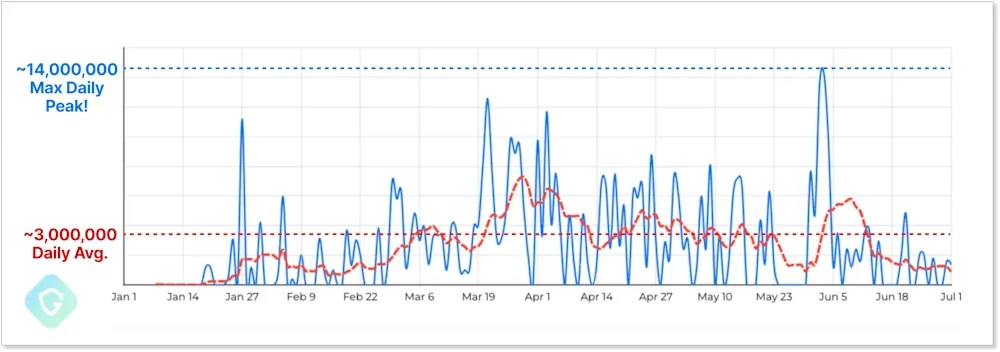
EchoSpoofing campaign: A threat actor has abused a now-fixed Proofpoint vulnerability to send millions of spoofed emails. Named EchoSpoofing, the campaign lasted between January and June this year. The attacker exploited Proofpoint infrastructure to send emails with proper SPF and DKIM signatures that appeared to come from Proofpoint's known customer list. The campaign peaked at 14 million spoofed emails in early June before the issue was fixed. Proofpoint confirmed the attacks and said the root cause was "a modifiable email routing configuration feature on Proofpoint servers to allow relay of organizations' outbound messages from Microsoft 365 tenants, but without specifying which M365 tenants to allow."
Malware technical reports
Mandrake: Kaspersky says it found a version of the old Mandrake Android spyware that managed to sneak past Google's defenses back onto the Play Store. The malicious app was downloaded ~32,000 times.
Oyster backdoor: Malwarebytes says it's seen the Rhysida ransomware gang using the Oyster backdoor as an initial access vector for recent attacks.
ModiLoader: ESET has published a report on ModiLoader, a malware loader recently used in a phishing campaign that targeted Polish SMBs.
Mint Stealer: CyFirma looks at a new MaaS renting a new infostealer named Mint Stealer to cybercrime groups. The new stealer is advertised through Telegram and a few dedicated websites.
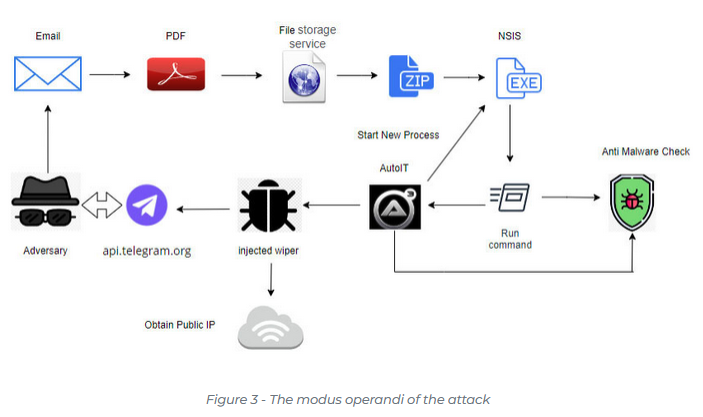
Handala wiper attacks: A pro-Palestinian hacktivist group named Handala Hack is using the recent CrowdStrike outage to lure Israeli companies into running a data wiper on their systems. Handala claimed on Twitter to have successfully wiped terabytes of data at several dozens of Israeli organizations. The group emerged in December of last year when it was using a fake F5 security update to trick Israeli organizations into running the same wiper.
Sponsor Section
In this demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to RiskyBiz host Patrick Gray.
APTs, cyber-espionage, and info-ops
Nothing in this edition.
Vulnerabilities, security research, and bug bounty
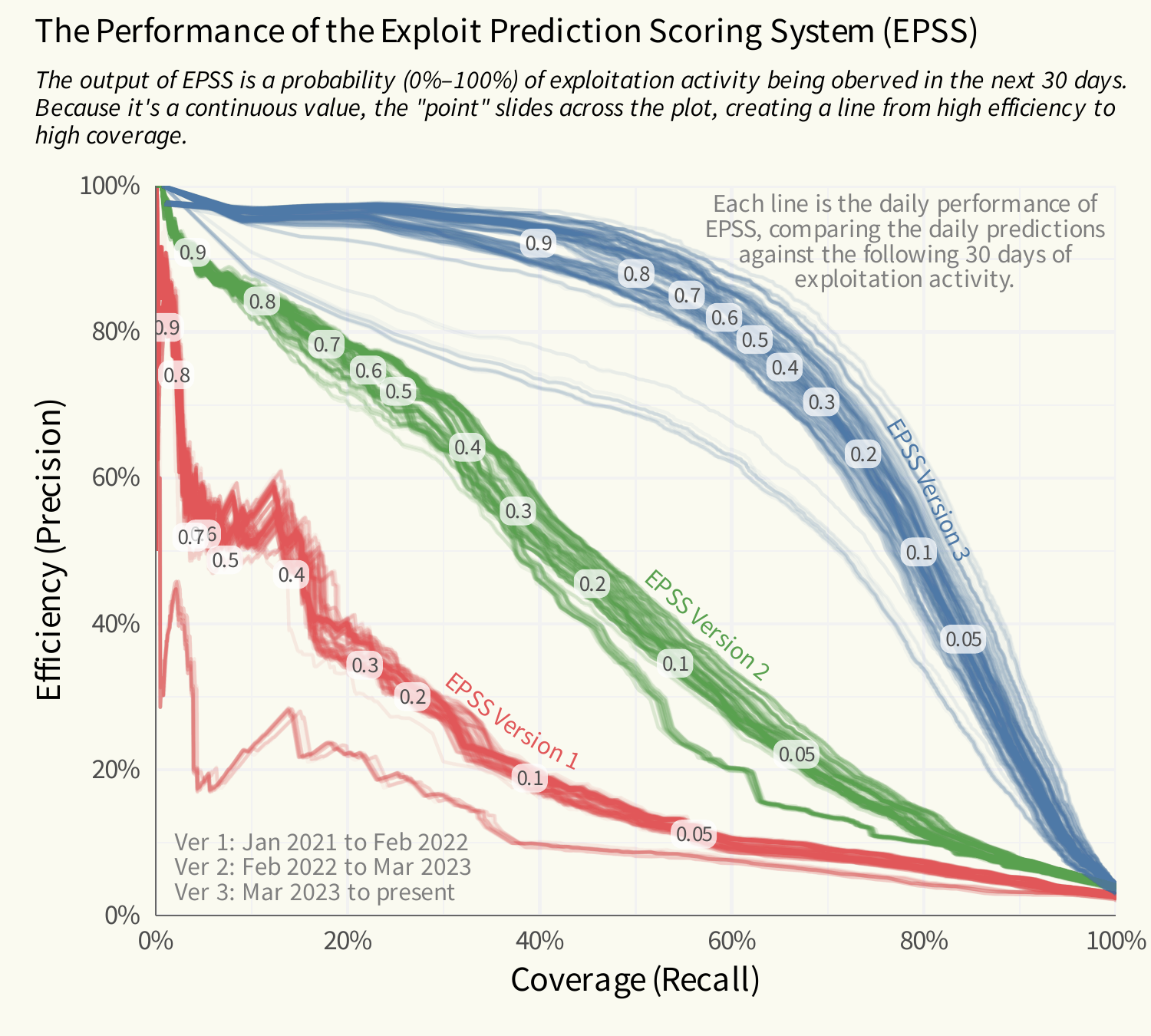
EPSS study: Tenable, Cyentia, and FIRST have published a joint study confirming that the Exploit Prediction Scoring System (EPSS) has shown good results in predicting in-the-wild exploitation.
Apple security updates: Apple has released security updates for all its major products. No zero-days this time.
Zoho security updates: Zoho has released two security updates for its ManageEngine software to fix two post-auth SQL injections in the Exchange Reporter Plus add-on. [h/t ScreamingGoat]
MOVEIt security updates: Progress has released a security fix for its MOVEit file-transfer server. [h/t ScreamingGoat]
Hotjar XSS: Salt Security has published details about an XSS vulnerability in the Hotjar service that could have allowed access to user data across a long list of major online services.
Homebrew security audit: Security firm Trail of Bits has published a security audit of the Homebrew macOS package manager. The audit found 25 issues, with most being patched already.
CosmicSting PoC: Several exploits for the CosmicSting Magento vulnerability are now publicly available. The bug entered active exploitation earlier this month.
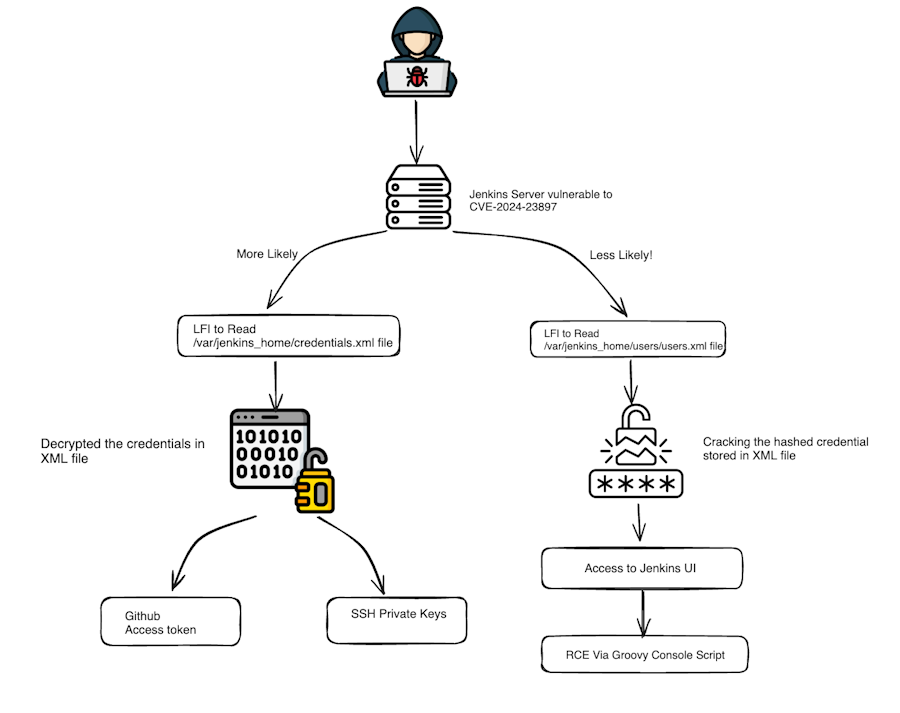
Jenkins exploitation: Indian security firm CloudSEK says it has seen threat actors exploiting a Jenkins vulnerability tracked as CVE-2024-23897 and then pivoting to companies' GitHub accounts by stealing GitHub access tokens stored on the server.
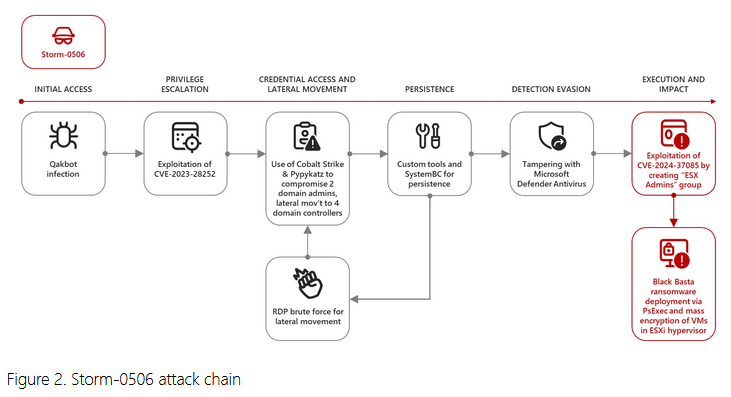
VMware ESXi zero-day exploitation: Several threat actors have abused a VMware ESXi zero-day to deploy ransomware in attacks targeting corporate environments. Microsoft's security team discovered the attacks and worked with VMware to have the issue patched at the end of June. The zero-day (CVE-2024-37085) resided in the ESXi Active Directory integration. It allows threat actors to bypass authentication and create admin users on domain-joined ESXi servers. Microsoft says at least four threat actors (Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest) have exploited the zero-day to deploy ransomware, such as Akira and Black Basta. From a Rapid7 write-up on the bug.
"The premise of the vulnerability is that domain-joined ESXi will automatically check for a certain Active Directory group. If the group name exists, all members of that group will be granted admin privileges over the ESXi server. An attacker with the ability to create AD groups or change the name of an existing AD group can set up the group, resulting in all AD group members gaining administrator privileges over the ESXi server."
Infosec industry
New tool—Dioptra: NIST has released Dioptra, a software test platform for assessing the trustworthy characteristics of artificial intelligence (AI). The project is available on GitHub.
New tool—Specula: Security firm TrustedSec has open-sourced Specula, a tool that converts Outlook into a command-and-control server for malware operations.
New Securonix CEO: Security firm Securonix has appointed Kash Shaikh as its new President and Chief Executive Officer.
BSides Canberra 2023 videos: Talks from the BSides Canberra 2023 security conference, which took place last September, are now available on YouTube.
Threat/trend reports: Coveware, HUMAN Security, IBM, NCC Group [PDF], Rapid7, Sophos, Sucuri, Tenable, Thinkst, Transmit Security [PDF], and Zscaler [PDF] have recently published reports covering infosec industry threats and trends. From the IBM report:
"IBM's recent Cost of a Data Breach Report 2024 found the global average breach hit a record $4.88 million. That's a 10% increase from 2023 and the largest spike since the pandemic."
From the Zscaler report [h/t Dissent Doe]:
"Findings in the report uncovered an 18% overall increase in ransomware attacks year-over-year, as well as a record-breaking ransom payment of US$75 million – nearly double the highest publicly known ransomware payout – to the Dark Angels ransomware group."
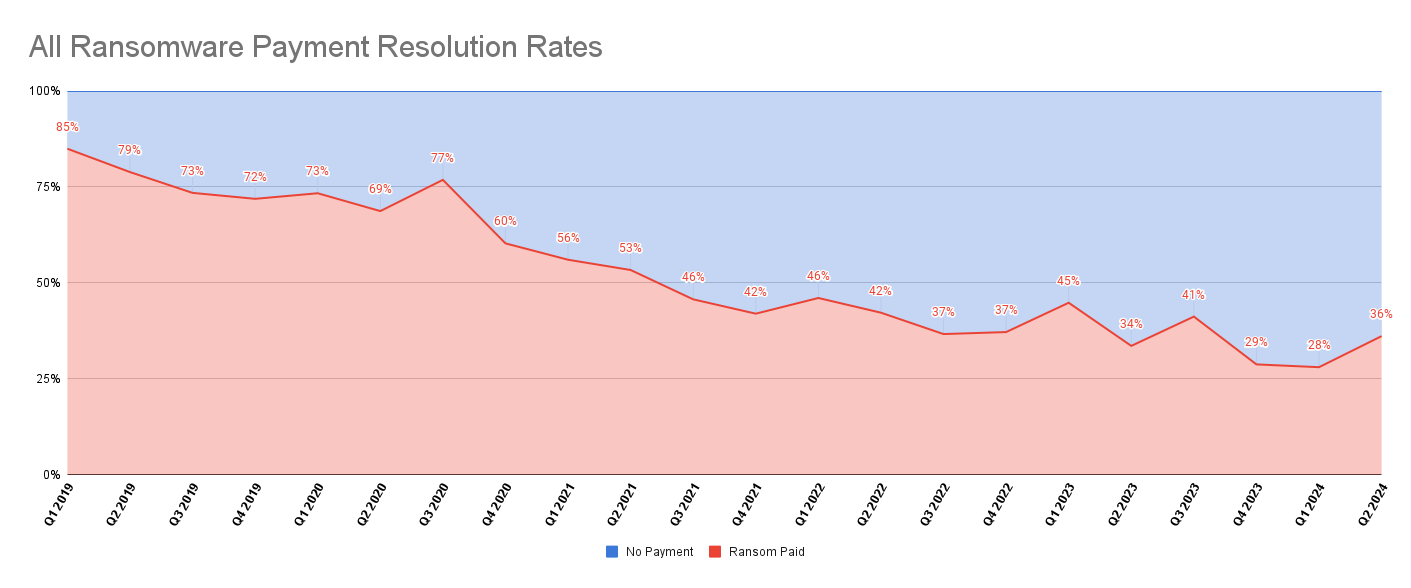
And a chart from the Coveware report:
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what the widespread disruption caused by CrowdStrike's faulty update tells us about how useful cyber operations are for war.
In this podcast, Tom Uren and Patrick Gray discuss the wild story of a Chinese illegal gambling operation that involves human trafficking, shell companies, money laundering, hundreds of thousands of websites, and sponsorship of European football teams.
This Soap Box edition of the show is with Mike Wiacek, the CEO and Founder of Stairwell. Stairwell is a platform that creates something similar to an NDR, but for file analysis instead of network traffic. The idea is you get a copy of every unique file in your environment to the Stairwell platform, via a file forwarding agent. You get an inventory that lists where these files exist in your environment, at what times, and from there, you can start doing analysis.




