Risky Biz News: Norwegian government hacked with MobileIron zero-day
In other news: TETRA encrypted radio traffic can be decrypted; Apple patches another Triangulation zero-day; and Zenbleed vulnerability leaks passwords and encryption keys from AMD Zen CPUs.
This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
A threat actor has exploited a MobileIron zero-day to breach twelve Norwegian government agencies, the country's security service said on Tuesday.
The identity of the attacker, the dates of the intrusions, and the names of the compromised agencies have not been revealed.
Norwegian authorities say the zero-day targeted a piece of software named the Ivanti Endpoint Manager Mobile (EPMM), previously known as MobileIron Core. The platform is used to manage mobile devices used by government employees and grant remote access to government systems and applications.
In a blog post, Ivanti confirmed the zero-day and said it was aware of "a very limited number of customers that have been impacted," which is also what this newsletter heard from a source—that more organizations besides the Norwegian government were breached.
At a technical level, Ivanti described the vulnerability (CVE-2023-35078) as a bypass of the EPMM API authentication system that can allow an attacker to make remote changes to an EPMM management server, changes that can technically be limited only by an attacker's imagination.
Because of the level of access an MDM platform like the EPMM has, the vulnerability can be used to collect data from user devices or deploy malicious payloads.
The Norwegian National Security Authority (NSM) and the Norwegian Government Security and Service Organisation (DSS) took credit for discovering the zero-day.
The NSM said it withheld information about the zero-day and the attacks until Ivanti released a patch. The NSM said it was afraid the vulnerability would be exploited in both Norway and abroad if they disclosed details too early.
Judging by the fact the zero-day received a severity rating of 10/10, it is likely easy to exploit and requires little technical know-how to do so.
Several cybersecurity agencies across the EU and US have already released advisories, urging their private and public sector organizations to patch.
More than 500 Ivanti EPMM systems are currently exposed on the internet, according to Shodan.
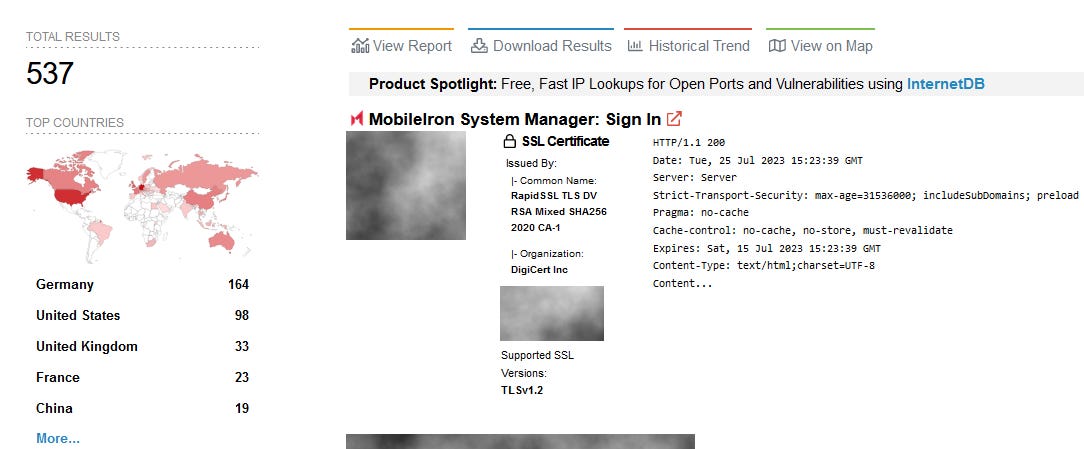
Breaches, hacks, and security incidents
Yamaha breach (sort of): Yamaha's Canadian music division has had its network breached and data stolen. Multiple ransomware gangs are taking credit—with both Akira and BlackByte taking credit. [Additional coverage in The Record]
AlphaPo hack update: Losses from the AlphaPo hack have grown from $23 million to $60 million.
Palmswap crypto-heist: The Palmswap platform lost $900,000 in crypto-assets after a hacker exploited a vulnerability in its blockchain smart contract.
Spyhide hack: A misconfiguration has exposed the development environment and the source code of Iranian spyware maker Spyhide. The exposed systems were discovered by Swiss computer hacker Maia Arson Crimew (formerly known as Tillie Kottmann, deletescape, and antiproprietary), who analyzed the code and later developed an exploit to access the spyware's backend panel and dump its data. The data contained information on Spyhide customers and information collected from infected Android smartphones. TechCrunch reviewed the Spyhide data and said it found information on 4,000 customers who deployed the spyware on more than 60,000 devices across the world over the past seven years.
General tech and privacy
AI at the NYC subway: The New York City subway administration is using AI to spot people dodging fares. The system has been live since May in seven stations across the city and is scheduled to expand to more than two dozen more stations. [Additional coverage in NBC News]
Ubisoft to suspend accounts: Gaming giant Ubisoft plans to suspend and then delete long-inactive accounts, regardless if they own paid-for games or not. Continues the trend of tech companies doing whatever they want regardless of consumer and privacy laws. [Additional coverage in Eurogamer]
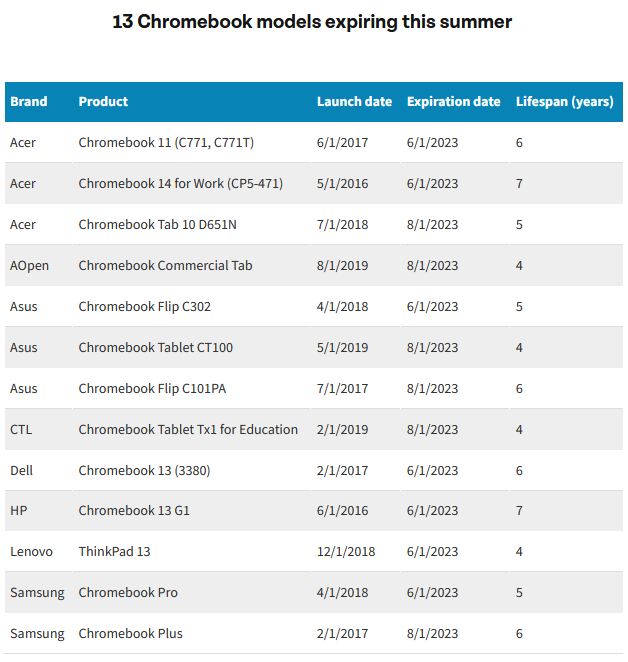
Google plea: A coalition of K-12 professionals, environmentalists, consumer advocates, and more than 10,000 members of the US Public Interest Research Group have asked Google in an open letter to extend the life of millions of Chromebooks that are set to reach end-of-life this summer. The signees say that Chromebooks hardware and software expire too quickly and the devices need to be replaced too often, creating unnecessary e-waste and costs to schools and students. They say Google could continue to ship software updates and extend the life of 13 Chromebooks that are set to expire this summer and keep millions of students online and capable of accessing school systems.
"Chromebooks come with an Automatic Update Expiration date, after which software support ends. The lack of software support can block essential uses such as accessing state testing websites and make devices vulnerable. Google could extend the life of these models, most of which are still available for purchase online."
Government, politics, and policy
National Cyber Director: The Biden administration has formally nominated Harry Coker to serve as the next National Cyber Director. Coker will be set to replace Chris Inglis, who left the post in February. Kemba Walden served in a temporary National Cyber Director role over the past months, but the White House refused to nominate her for the role citing personal debt issues. [Additonal coverage in CyberScoop]
BRICS propaganda: Representatives from China and Russia, two countries that need a national firewall to prevent their citizens from criticizing their supreme leaders, claim the US is using the internet for "neo-colonial ambitions" and argue that BRICS countries should have more say in how the internet is run for a more "fair, open, safe and vibrant" cyberspace. Yes! Countries that jail citizens for criticizing their leaders and "special military operations" should have more control over the internet because they claim the US has "cYbEr HeGeMoNy" and they should have more control instead. God, reading all this state propaganda for the sake of this newsletter is gonna melt my brain!
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Airlock Digital founders Daniel Schell and David Cottingham about vulnerable drivers, BYOVD attacks, and the problem with driver-based attacks.
Cybercrime and threat intel
Phisher detained in the Netherlands: Dutch authorities have arrested a 21-year-old from Amsterdam for orchestrating several large-scale phishing and smishing operations. The targets of his attacks included customers of banks in Spain, Ireland, Germany, and the Netherlands. Officials say the suspect made more than €400,000 from cybercrime and online fraud.
Dutch data broker arrested: Dutch Police have detained a 32-year-old man who spent tens of thousands of euros buying hacked login credentials from the Genesis Market underground portal. Officials say the suspect is the largest Dutch user of the Genesis Market and one of the Top 10 most active users worldwide. US authorities seized the Genesis Market in April this year, and the 32-year-old man is the 18th suspect detained in the Netherlands in connection to the Genesis Market takedown.
Phone spoofing gang detained in South Korea: South Korean police have detained 25 suspects that were part of a cybercrime gang that spoofed South Korean telephone numbers as part of an online scamming operation. The group is believed to have stolen more than $280,000 from its victims. Authorities say that while the gang had local members, it was led by Taiwanese and Chinese nationals. [Additional coverage in Hankyung]
GeoMetrix: A Perception Point report delves into GeoMetrix, a new Brazilian threat actor that has been behind several phishing campaigns that have targeted banking and crypto users in Brazil and Spain. The group operates their own tools, which they also rent out to other threat actors.
Login with Apple abuse: We have a first case of a malicious iOS app abusing the Login with Apple feature for phishing and malicious purposes. [via CodeColorist]
MOVEit attacks: Kroll has published information on an additional data exfiltration method (a Python script) used by the Clop gang during its recent MOVEit servers hacking spree.
SVG smuggling: More details are available on SVG smuggling, a new technique used in phishing campaigns and obviously based on the good ol' HTML smuggling.
Malware technical reports
Ripper DDoS botnet: QiAnXin researchers have published a breakdown of Ripper, a new DDoS botnet based on the Mirai strain that has already reached a third version. The botnet has been very active earlier this month, targeting devices with weak Telnet passwords.
Akira ransomware: CloudSEK researchers have a report on the recent Akira ransomware operation.
Glubteba: OALABS has published IOCs for new Glubteba samples.
Qakbot: Zscaler has published an in-depth report of several phishing campaigns that have distributed the Qakbot malware over the past few months.
Casbaneiro: Sygnia researchers have taken a look at the recent changes in the operations of Casbaneiro, a gang operating a banking trojan that targets users in the Americas.
NemesisProject: Walmart's security team has published an analysis of NemesisProject, a backdoor framework and its plugins. Among the framework's customers is the FIN7 cybercrime group.
Decoy Dog: Infoblox is reporting a rise in usage of Decoy Dog, a malicious toolkit that helps threat actors set up command and control mechanisms for their malware operations via DNS. The company first saw the malware back in April.
Realst Infostealer: SentinelOne has discovered Realst, a new macOS infostealer written in Rust that appears to be geared towards stealing crypto wallet data and user passwords from infected systems. While macOS infostealers have been spotted before, the most interesting part about this new threat is that its authors have already prepared versions to target macOS Sonoma, the next major release of Apple's Mac operating system, set to be released this fall. The early bird gets the worm!
HookBot leak: The source code of the HookBot Android malware strain has leaked online and is now available in a GitHub repository. HookBot was first spotted online in January this year. The malware is a fork of the older Ermac banking trojan, with additional remote-access capabilities to enable more advanced fraud schemes. The repo is being hosted by a security researcher, who modified and restricted certain files to prevent the malware's use for malicious purposes. [h/t Rohit Bansal]
Sponsor Demo
Airlock Digital CEO David Cottingham shows Patrick Gray how Airlock's execution control and allowlisting solution works.
APTs and cyber-espionage
UAC-0006: Ukraine's CERT says the country's government agencies are getting hammered with SmokeLoader campaigns linked to the UAC-0006 group. Three different campaigns were spotted in ten days.
SideCopy: Qihoo 360 has published a report on recent SideCopy phishing campaigns delivering the AllaKoreRAT and ReverseRAT.
Lazarus IIS campaign: The Lazarus APT is hacking IIS servers to host watering-hole attacks that try to exploit a former zero-day in INISAFE Cross Web EX, a South Korean app used for authenticating users via electronic signatures. Users, where this app is present, are infected with one of Lazarus' backdoors.
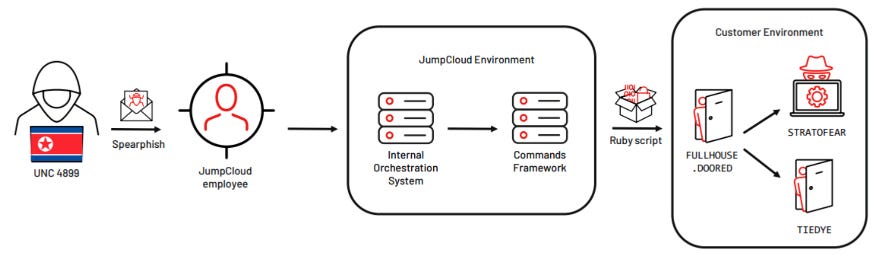
JumpCloud incident: Adding to reporting from this newsletter, CrowdStrike, and SentinelOne, Mandiant has also linked the JumpCloud intrusion to a North Korean APT. Mandiant attributed the attack to UNC4899, aka TraderTraitor, aka Jade Sleet. According to previous reporting, the group pivoted from JumpCloud's infrastructure to five of its customers in the cryptocurrency vertical.
Chinese info-op: ASPI researchers have identified Twitter accounts operated by a criminal group promoting casino scams that were also used to spread CCP propaganda across Australia and Southeast Asia.
"The threats we face as a society are no longer limited to violence, espionage and interference conducted in person—whether by individuals, state entities or criminal groups—but are increasingly enabled by digital personas, inauthentic accounts and coordinated networks that can reach anyone globally and instantly."
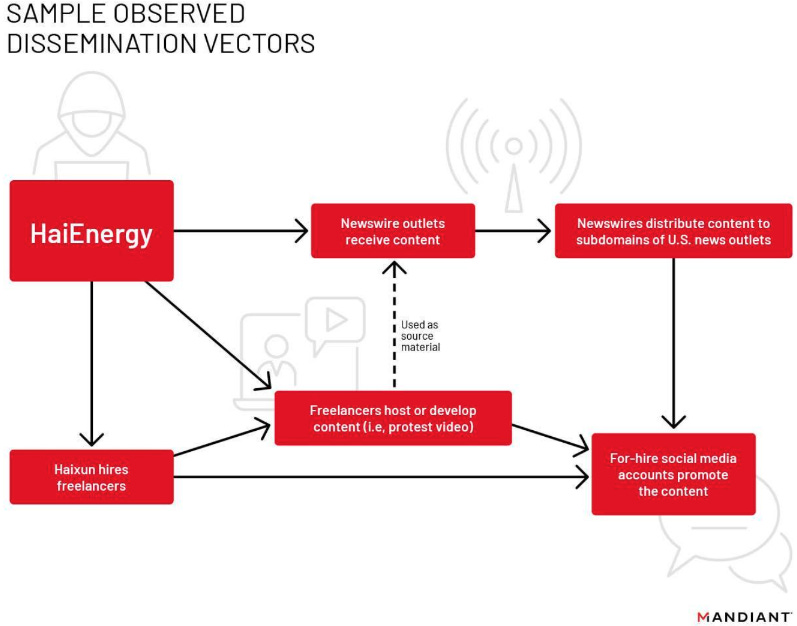
China's PR agency: Google's Mandiant division reports that a Chinese marketing firm named Haixun Press has been operating a network of at least 72 websites that claim to be independent news outlets but spend their time amplifying Chinese propaganda. The websites operate in different regions of the world and publish content praising the successes of the Chinese economy while being critical of US politicians, academics, and other critics of the Beijing regime. Haixun also operates a newswire at CloudQuote.io through which they distribute their articles, some of which have been picked up by legitimate news outlets, including the likes of the Arizona Republic and the Pittsburgh Post-Gazette. Mandiant says the articles got little interaction compared to articles published by Beijing's state media outlets.
"Finally, and perhaps most noteworthy, we have evidence to suggest the campaign may have financed at least two staged in-person protests in Washington, DC. The campaign then used the protests as source material in HaiEnergy-linked operations that promoted narratives surrounding highly divisive US domestic issues and messaging critical of a June 2022 decision by the US Government to ban all goods produced in China's Xinjiang region."
Vulnerabilities, security research, and bug bounty
Apple patches another Triangulation zero-day: Apple has released security updates to patch two iOS zero-days, including one (CVE-2023-38606) that was exploited in a campaign known as Operation Triangulation. This marks the third zero-day from Operation Triangulation attacks that Apple has patched this year. Operation Triangulation targeted Russian government officials, foreign diplomats working in Russia, and Kaspersky employees. Russia's FSB intelligence service attributed the attack to the US National Security Agency and claimed Apple cooperated with the American spy agency. The FSB didn't provide any evidence to support that claim, and Apple has denied it.
Apple-Chrome zero-day drama: Security researcher Martin Radev has published a timeline of the recent Chrome zero-day drama surrounding CVE-2023-3598. This is a vulnerability that was exploited in the Chrome browser during a CTF contest. It was found and used by an Apple security engineer named "Leonardo," but it was Radev who reported it to the Chrome VRP and received a bounty for it. Radev's blog post tries to address accusations that he stole the zero-day from his fellow researcher.
Car battery tracker collects your location: A security researcher known as HaxRob has published a three-part series on how a Chinese-made SDK named AMap was secretly collecting GPS, WiFi, and cell phone tower data collection from apps where it was installed and sending it back to China. The SDK and its behavior were initially found in a Bluetoo h-based car battery tracking device and app named BM2.
ASUS PoC: Proof-of-concept exploit code has been posted for CVE-2023-35086, an RCE in ASUS routers. However, the PoC only achieves DoS.
Apache OpenMeetings RCE: SonarSource researchers have published a detailed write-up on three vulnerabilities in the Apache OpenMeetings video conferencing software. Chained together, the vulnerabilities allow a self-registered user (enabled by default) to take over an admin account and gain remote code execution. All vulnerabilities were fixed with Apache OpenMeetings 7.1.0.
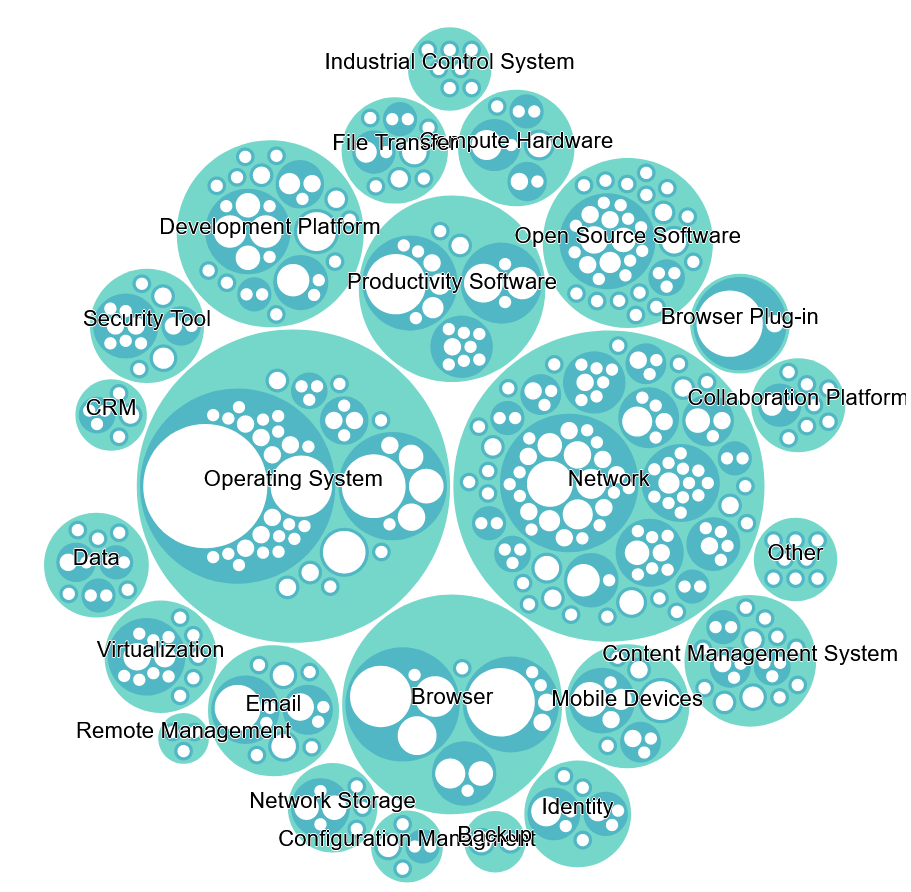
CISA KEV breakdown: Nucleus Security has published a breakdown and interactive chart of the CISA KEV database, broken down per vulnerability category. Vulnerabilities in operating systems (235) and network devices (182) reign supreme.
MikroTik vulnerability: Hundreds of thousands of MikroTik routers are vulnerable to a security flaw that can allow threat actors to get root access and take full control of unpatched devices. Although the vulnerability (CVE-2023-30799) is not directly exploitable and requires authentication, security firm VulnCheck says that many MikroTik routers still have their factory admin account enabled, which could be abused to bypass this requirement. VulnCheck says that of the 900,000 MikroTik devices connected to the internet, around 60% still have the default admin account present, leaving routers exposed to attacks unless patches are applied.
Zenbleed vulnerability: Google security researcher Tavis Ormandy has discovered a vulnerability in AMD Zen 2 processors that can allow threat actors to retrieve sensitive data from the CPU, such as encryption keys and passwords. Named Zenbleed (CVE-2023-20593), Ormandy says the attack is fast enough to be viable in real-world scenarios. Proof-of-concept code has also been released. AMD has released firmware patches. Affected CPU models include several Ryzen desktop consumer series and Epyc Rome data center processors.
TETRA:BURST vulnerabilities: Security researchers have identified five vulnerabilities in the Terrestrial Trunked Radio (TETRA) standard used by law enforcement, military, and critical infrastructure operators across the globe. Collectively referred to as TETRA:BURST, the vulnerabilities impact most TETRA equipment and networks. Researchers say that based on infrastructure and device configurations, the vulnerabilities can allow real-time decryption, harvest-now-decrypt-later attacks, message injection, or user deanonymization. Firmware patches have been released for some of the TETRA:BURST vulnerabilities.
"The deanonymization issue (CVE-2022-24403) is primarily relevant in a counter-intelligence context, where it enables low-cost monitoring of TETRA users and their movements in order to allow a state or criminal adversary to avoid covert observation or serve as an early warning of impending intervention by special forces."
Infosec industry
2023 data breach costs: Data breach costs rose to $4.45 million per incident in 2023, a 15% increase over the past three years, according to this year's edition of IBM's Data Breach Report. The figure grew due to increases in costs associated with detection and incident response operations, a direct result of more complex data breach investigations. IBM reports a 42% jump in detection and IR costs from March 2022 and March 2023. The most common type of data stolen in breaches remained customer and employee personal information, involved in half of all 2023 incidents.
Security professionals on the board: Only five companies in the Fortune 100 list a security professional, like a CISO or CSO, in leadership roles. The five are BestBuy, Cigna, Coca-Cola, Disney, and Walmart. Other companies obviously also have CISOs and CSOs, but they are not listed in leadership or board positions. [Additional coverage in KrebsOnSecurity]
Isosceles: Former Google Project Zero team lead Ben Hawkes has launched a new cybersecurity consulting company named Isosceles.
"Isosceles will focus on high-end technical services including security reviews, automation, and research for companies that are investing in a strategic, long-term security posture for their products."
Acquisition news: French IT giant Thales will acquire Israeli cybersecurity company Imperva from Thoma Bravo for $3.6 billion. Thoma Bravo acquired Imperva in 2019 for $2.1 billion.
New tool—Twitter Archiver: Darius Kazemi has published a tool called Twitter Archiver that lets Twitter expats host their Twitter archives and tweets online, far away from Musk's far-right cancer.
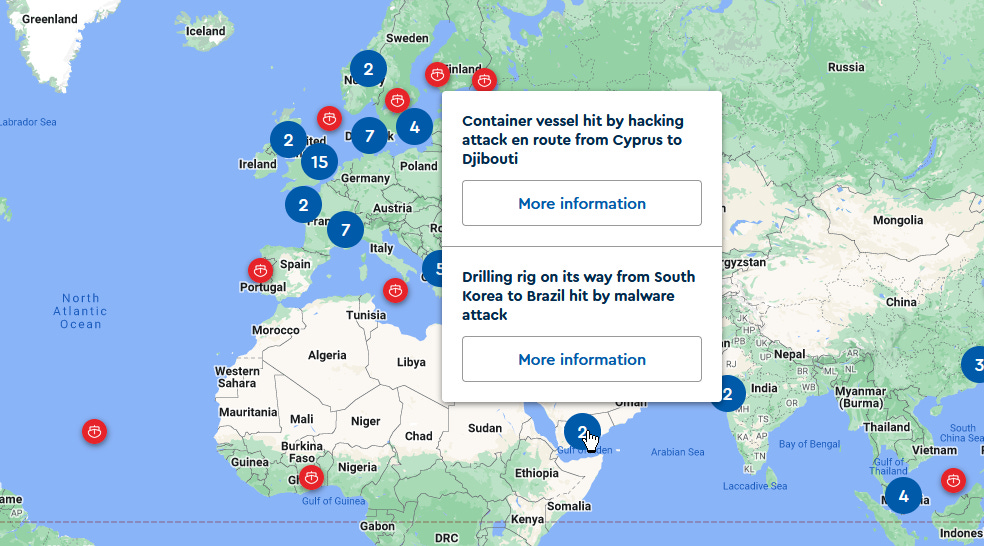
New tool—MCAD Maritime Cyber Attack Database: Dutch academics are maintaining a database of known cyberattacks that have hit the international maritime sector over the years. The database holds information on more than 160 cyber incidents and is open to submissions.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at when it makes sense for governments to invest in building their own secure phones.




