Risky Biz News: North Korean hackers behind supply chain attack on 3CX
In other news: Lumen discloses two security breaches; UAE users targeted with zero-days from Spanish vendor; VulkanFiles leak exposes Russian military hacking tools.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
A threat actor has compromised VoIP software development company 3CX and has trojanized its macOS and Windows desktop clients with malware.
The incident was discovered by cybersecurity firm CrowdStrike, and the company believes this may be the work of a North Korean state actor tracked as Labyrinth Chollima, also known as the Lazarus Group or Hidden Cobra.
Current evidence suggests the group infiltrated the company months before and hid malware in the company's macOS and Windows desktop clients around the start of the month. Customers who downloaded the apps were infected. The malware was also installed on some systems via the app's built-in updating feature—if this was enabled.
Security researchers who investigated the incident following Crowdstrike's initial disclosure say the malware went under the radar for weeks until the past few days when it started aggressively reaching out to a number of domains suspected of being controlled by the Labyrinth Chollima group.
The current thinking is that the North Korean operators saw recent posts on the 3CX forum from customers complaining about the trojanized Windows client triggering antivirus warnings and decided to exploit their access while they still had it and before security vendors realized what was actually happening.
In addition to beaconing activity, CrowdStrike says that in some cases, its security tools also detected the deployment of second and third-stage payloads and, in a small number of cases, even "hands-on-keyboard activity"—where the hackers connected to the compromised systems and ran malicious commands manually.
SentinelOne says the final payload is "a previously unknown infostealer meant to interface with browser data." Stealing passwords from 3CX customer networks to enable future intrusions seems to be the end goal here.
macOS security researcher Patrick Wardle confirmed the compromise of the 3CX macOS desktop client, although he was unable to find what payloads were being dropped on macOS systems. Probably something similar.
Both SentinelOne and Sophos confirmed the supply chain attack, but only CrowdStrike attributed the operation to North Korea. Volexity, Sophos, Trend Micro, and Huntress also have technical reports on the incident and the malware.
The incident is as bad as it gets, primarily because of the popularity of 3CX solutions.
The company's products include hosted and on-premise telephony VoIP IPBX servers. Employees in companies with 3CX VoIP IPBX servers can either use a VoIP phone or install the 3CX softphone on their devices to make and receive calls or host video conferences via a desktop or mobile app. It's these macOS and Windows desktop apps that were trojanized.
It's unclear how many users downloaded the trojanized desktop clients or how many received the malicious update for existing clients, but 3CX's customer base is huge. The company claims on its website to serve more than 600,000 companies and more than 12 million daily users. Per its website, 3CX serves some of today's largest corporations.

A Shodan search returns more than 245,000 3CX VoIP IPBX servers, just to give you an idea of how popular the 3CX system is.
As for 3CX, well, it's not good. At all. First, they didn't detect the intrusion for months. Second, when several antivirus products started detecting their clients as malicious, they repeatedly claimed it was just false positives, over and over again, without investigating further. When 4-5 different vendors see the same thing, it's probably a indicator you should look at your app. Third, some customers said that when they went to 3CX's customer support with CrowdStrike's findings, they were asked to "open a support ticket at £75 per incident." That's just... not what people wanted to hear.
The company did eventually confirm the incident in a blog post and promised to release new clean desktop client versions. Until then, 3CX recommended that customers use its web-based PWA app instead.
Breaches and hacks
Lumen discloses two security breaches: Lumen Technologies, one of the largest US telcos and infrastructure providers, has disclosed in an SEC filing that it suffered not one but two security breaches. The first was a ransomware attack that hit servers part of the company's hosting infrastructure. Lumen says the incident is degrading the operations of a small number of enterprise customers. The second incident is more severe. Lumen described the attacker as "a separate sophisticated intruder" that managed to gain access to some of its internal systems, where it conducted reconnaissance, installed malware, and extracted "a relatively limited amount of data."
Russian pilots doxxed: Pro-Ukraine hacktivist group Cyber Resistance has hacked into the personal accounts of the Russian pilots who bombed civilian infrastructure in the city of Mariupol at the start of the Ukrainian war. The hackers publicly identified the commander of the unit responsible for the bombings and leaked his inbox. They also say they handed over the entirety of the stolen files to the International Criminal Court so the pilots could be trialed for war crimes.
Safemoon cyber-heist: DeFi service Safemoon lost $8.9 million worth of cryptocurrency assets after an attacker exploited a bug in its platform.
NTS investigates ransomware attack: The South Korean National Tax Service is investigating a possible security breach after the LockBit ransomware gang listed its name on its dark web leak site. [Additional coverage in Daily Secu]
Climate activists targeted by cyber mercenaries: A Wall Street Journal [non-paywall] piece takes a look at the case of an Israeli private detective and his connections to BellTroX, an Indian hacker-for-hire company. The piece covers attacks targeting climate change activists, and appear to have benefitted oil giant Exxon.
General tech and privacy
Open letter on AI research: A group of AI researchers and technology experts has signed an open letter asking tech giants to pause large-scale testing and development of AI systems, such as Chat-GPT. They cited the dangers of AI being used to replace human jobs and flood social networks with propaganda at scale. Signatories include the likes of Apple co-founder Steve Wozniak, Pinterest co-founder Evan Sharp, Elon Musk, and others.
Twitter Blue research: A researcher has been analyzing the profiles of Twitter Blue subscribers, and to nobody's surprise, almost half of Blue users have less than 1,000 followers. The research suggests that accounts that post often, generate content for Twitter, and gain a following through organic growth are not subscribing to Twitter Blue.
Disinformation comes to Mastodon: Since that right-wing and political propaganda site Twitter is obviously dying a slow and hilarious death, some disinformation peddlers are gradually testing the Fediverse. This week, one of the largest disinformation clusters was seen setting up a Mastodon server.
Government, politics, and policy
US govt pays for Costa Rica's SOC: The US government plans to send $25 million to the Costa Rica government as aid to help the country recover and strengthen its digital infrastructure following a massive ransomware attack that crippled the Central American country in May of last year. US officials say the funds will be used for cybersecurity training, the acquisition of secure hardware equipment and software licenses, and the creation of a Security Operations Center (SOC) within Costa Rica's Ministry of Science, Innovation, Technology, and Communications. [Additional coverage in Wired]
FSB wants access to taxi databases: A bill has been proposed in the Russian Parliament that would grant the FSB intelligence service round-the-clock access to the databases of Russian taxi companies. According to Forbes Russia, the FSB will have extrajudicial access to customer databases, real-time location data, and payment information. The bill was proposed by FSB officials and is expected to pass and enter into effect later this year.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Infraud members get no prison time: Four Russian hackers received suspended sentences from a Russian judge and will see no jail time despite their long-time involvement in a giant carding operation. The four suspects were detained in Moscow in January of last year. They were accused of being part of the Infraud cybercrime cartel, where they ran the UniCC carding forum for ten years, since 2012. TASS reports that the case judge justified handing out suspended sentences after the four admitted their guilt.
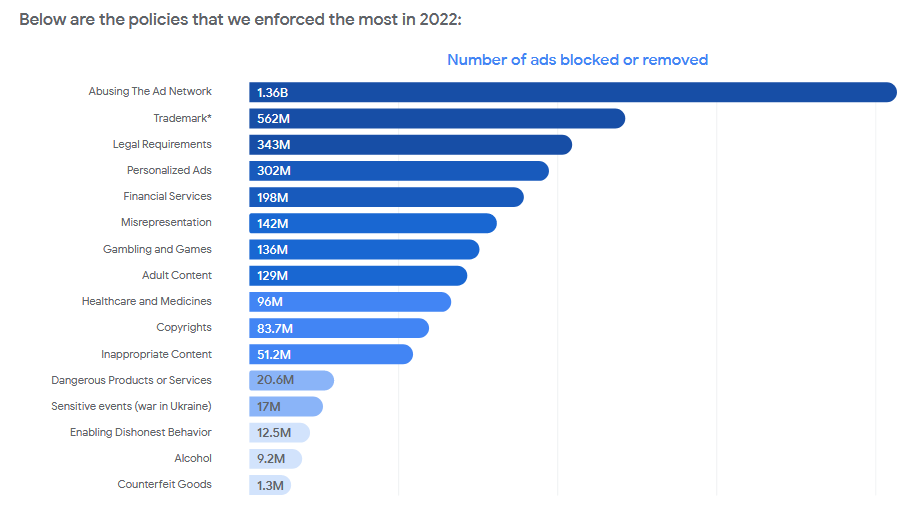
Google blocks SEO/SERP poisoning campaign: Google says it took action against a coordinated campaign that used ads on its search engine to promote links to thousands of malicious websites. These sites posed as legitimate or open-source software but spread trojanized apps that would infect users with malware. Google says the coordinated campaign (which we covered here) lasted for about a month, from the end of 2022 into the new year, and involved "tens of thousands of malicious advertisements." Google confirmed its takedown in its yearly Ads Safety Report. All in all, Google says it blocked more than 5.2 billion malicious ads last year because of malware, disinformation, trademark infringement, and other reasons.
Silver Fox group: Chinese tech giant Weibu Online says it's tracking a threat actor named Silver Fox that is currently targeting Chinese companies with malware. The group uses SEO techniques to make its phishing sites rank first in Chinese search engines. Once it phishes an employee and gets access to a company's network, the group sends trojanized files to other employees via WeChat groups. The files contain a copy of the Gh0st remote access trojan. Weibu says it has seen Silver Fox target companies in the Chinese finance, securities, and education sector.
New PSWmarket infostealer: Security researchers have spotted a new infostealer named PSWmarket. The malware appears to be managed by a Russian-speaking threat actor.
Bassterlord retires, allegedly: Bassterlord, one of the most active LockBit affiliates, has allegedly "retired."
OpIsrael review: Radware has a report on past OpIsrael attacks from the past decade and new attacks planned for this year and the anti-Israel hacktivist groups that might be involved, such as AnonGhost, Mysterious Team, Anon Cyber Vietnam, WSHPCZ3, Cyber Army of Vietnam, Muslim Cyber Army, Cyber KEX, and Ghost Clan.
Trojanized Tor Browser in Russia: Kaspersky reports that there are trojanized versions of the Tor Browser installers being spread online in the Russian internet space that contain a clipboard hijacker targeting cryptocurrency users. The campaign was very effective because of the Russian government's Tor ban and because of the increasing censorship avoidance appetite of Russian internet users.
Zero-day campaign targeting Android and iOS: Google's security team says it discovered a threat actor using Android and iOS zero-day exploit chains to target users located in Italy, Malaysia, and Kazakhstan. The campaign took place last year and involved SMS messages containing links to websites hosting the exploits. Google didn't link the campaign to any specific threat actor.
New Variston operations: Amnesty International and Google have identified a hacking campaign targeting UAE users. The attack consisted of SMS messages containing one-time temporary URLs. The links redirected users to malicious websites that hosted exploit chains for the Samsung Internet Browser. If successful, victims would be infected with Android spyware. Google's security team has linked both the exploits and the websites in this campaign to Heliconia, an exploit toolkit developed by Variston IT, a company from Barcelona, Spain. Google previously spotted the Heliconia framework last year, but this marks the first real-world case where the toolkit was used in the wild.
Hacked Bitrix servers used in phishing ops: Cybersecurity firm PIXM is seeing hacked Bitrix CRM servers hosted in Russia being used to host phishing pages. Bitrix servers were heavily exploited at the end of last year using a vulnerability tracked as CVE-2022-27228.
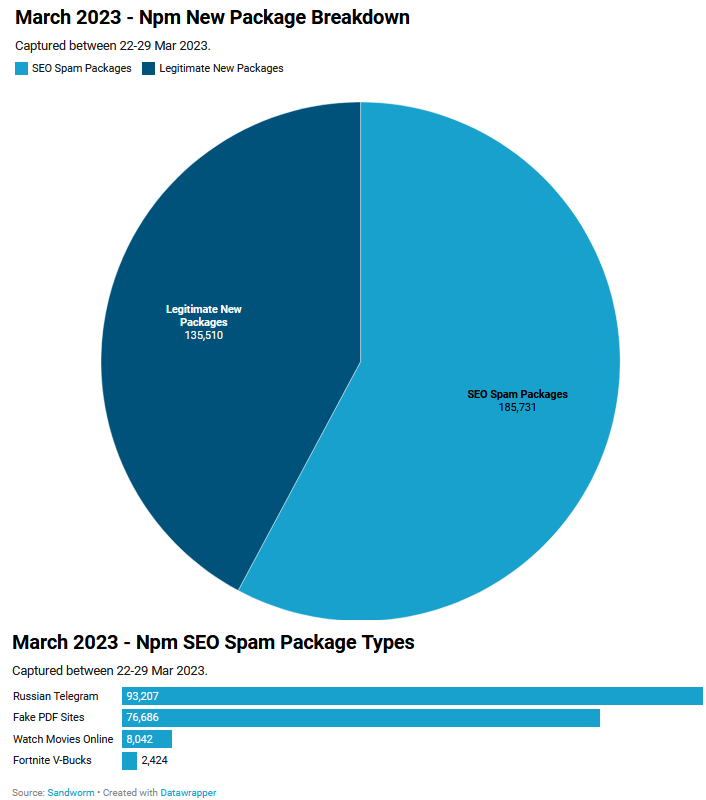
npm spam attack: The spam attack that flooded the npm repository earlier this week is actually larger than everyone thought. According to DevSecOps firm Sandworm, more than half of the JavaScript libraries uploaded on the npm portal this month have been SEO spam. If the spam doesn't bother you, then beware of actual npm malware.
"Out of the ~320k new npm packages or versions that Sandworm has scanned over the past week, at least ~185k were labeled as SEO spam. Just in the last hour as of writing this article, 1583 new e-book spam packages have been published."
Malware technical reports
Lumma Stealer: SecurityScorecard's Vlad Pasca has published a report on Lumma Stealer, a new infostealer used in campaigns earlier this year.
MacStealer: Trend Micro published a report on MacStealer, a macOS infostealer that can exfiltrate data to a remote Telegram channel. The malware is currently being sold via underground hacking forums and distributed via play-to-earn (P2E) games. A similar report on MacStealer is also available from Uptycs.
Mélofée: ExaTrack researchers have discovered Mélofée, a new rootkit targeting Linux systems. ExaTrack believes the malware is the work of Chinese state-sponsored hackers.
OpcJacker: Trend Micro has identified a new infostealer named OpcJacker. The malware has been distributed in the wild since the second half of 2022 and is typically distributed via malvertising promoting VPNs installers and cryptocurrency-related apps. In some instances, OpcJacker was also seen deploying more powerful RATs such as NetSupport and hVNC.
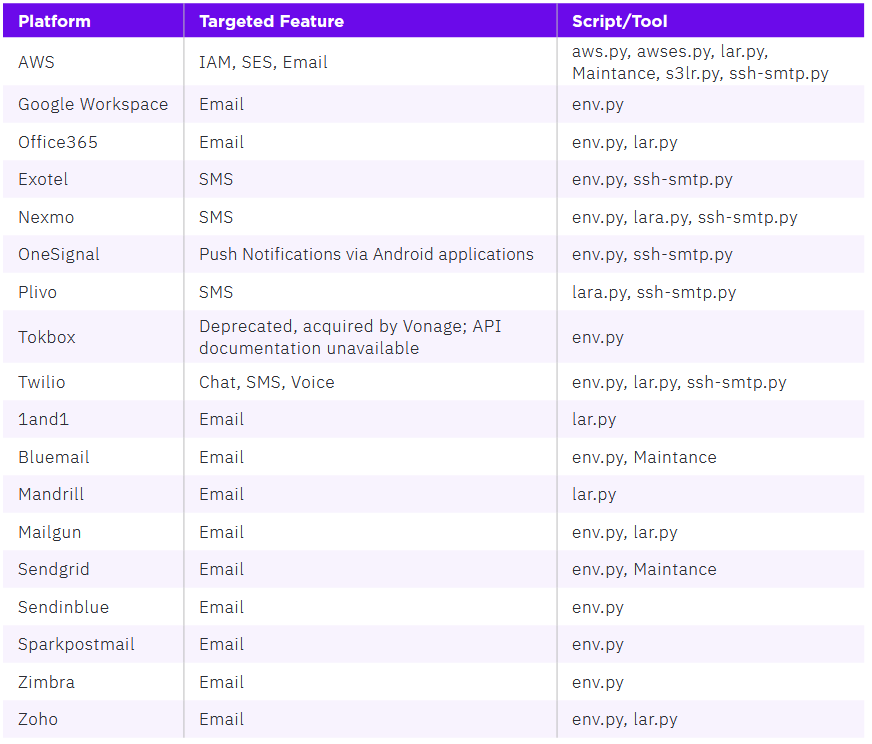
AlienFox toolkit: SentinelOne has a report on AlienFox, a collection of tools for extracting credentials, API keys, and secrets from multiple cloud service providers. The toolkit is currently being distributed via underground Telegram hacking channels. Threat actors who gain access to a website, web app, or server through various means can deploy AlienFox to scan the compromised environment for sensitive data and automatically extract it. The collected information can then be used to compromise further systems and move laterally inside a company's cloud infrastructure.
Sponsor Section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
APTs and cyber-espionage
TA473: Proofpoint says it has seen an APT group it tracks as TA473 is targeting NATO-aligned governments in Europe. The group is leveraging a Zimbra vulnerability (CVE-2022-27926) in publicly facing webmail portals to gain access to the email mailboxes of government entities. Some of TA473's attacks also targeted US elected officials and their staffers. Proofpoint says it believes TA473, also known as Winter Vivern and UAC-0114, to be a Russia-aligned group active during the ongoing Russian-Ukrainian war.
North Korean hackers abuse authentication software: North Korean hackers are exploiting a vulnerability in a popular software app used by banks and government agencies across South Korea. South Korea's intelligence agency NIS says hackers have compromised 210 computers at 60 organizations since the start of the year. While authorities did not name the company, ZDNet South Korea identified the vendor as Initech and the software as INISAFE Cross Web EX, an app used for authenticating users via electronic signatures. South Korean officials say they worked with the company and released patches in January and are now urging South Koreans and companies to patch their authentication software. Kind of a silly security alert if you don't say which software to patch!
VulkanFiles: German and French reporters have obtained access to a collection of documents from Vulkan, a private firm contracted by the Russian Ministry of Defense to develop offensive cyber weapons. The leaked files contain information on three projects. The first is Amezit, a system meant to manage intercepted communications in a certain geographical area. It can handle tasks such as redirecting users to "desired" content and can also be used for influence operations. The second is a platform named Scan-AS, a system to map adversary networks through different types of internet scans and open collection sources. The third is Krystal-2B, a training platform for exercising coordinated IO/OT attacks against transportation and utility industries using Amezit. Security firm Sekoia, which helped LeMonde reporters during the investigation, also has an analysis of the leaked files. So has Mandiant, which says Scan-AS appears to have been contracted for use by the Sandworm APT.
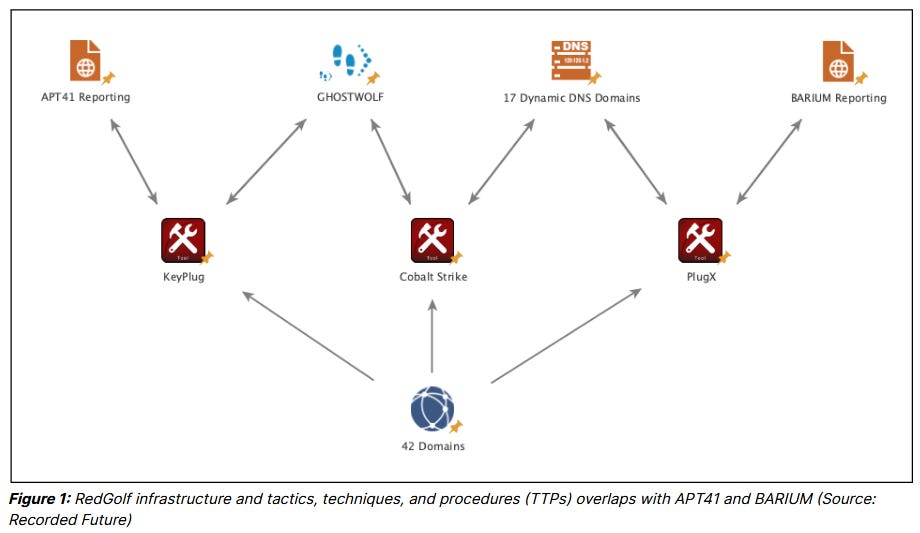
RedGolf: Recorded Future has a report on the recent campaigns of the RedGulf APT group (aka APT41, Barium) and its use of KeyPlug, a Windows and Linux backdoor.
Vulnerabilities and bug bounty
DBX revocation list problem: ESET says that two vulnerable UEFI binaries were incorrectly revoked last year and can still be abused to this day for UEFI Secure Boot bypass attacks. The incident was blamed on Microsoft, which blocked the binaries' SHA256 hashes instead of their PE Authenticode hashes.
Super FabriXss: Orca Security has published a report on CVE-2023-23383, an XSS vulnerability in the Azure Service Fabric Explorer (SFX) that enables unauthenticated remote attackers to execute code on a container hosted on a Service Fabric node. The bug was fixed in this month's Patch Tuesday.
BingBang: Cloud security firm Wiz has identified a misconfiguration in Microsoft's Azure Active Directory service, a cloud-based identity and access management service. The vulnerability allows a threat actor to use their own AAD account to bypass authentication and access apps created via the Azure App Services or Azure Functions services by other customers. Wiz says that based on their scans, nearly 25% of multi-tenant Azure applications appear to be vulnerable. Wiz confirmed the attack by hijacking the Azure app that Microsoft uses to manage some of Bing's search results. Researchers modified search results and even added XSS payloads that would steal Office 365 credentials from Bing users (see video below). Microsoft fixed the issue and awarded Wiz $40,000 for their report. It also issued guidance on how to avoid these types of misconfigurations.




