Risky Biz News: NIST NVD stopped enriching CVEs a month ago
In other news: LockBit member sentenced to prison; CIA runs anti-China info-op; new GhostRace side-channel attack.

This newsletter is brought to you by Yubico. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

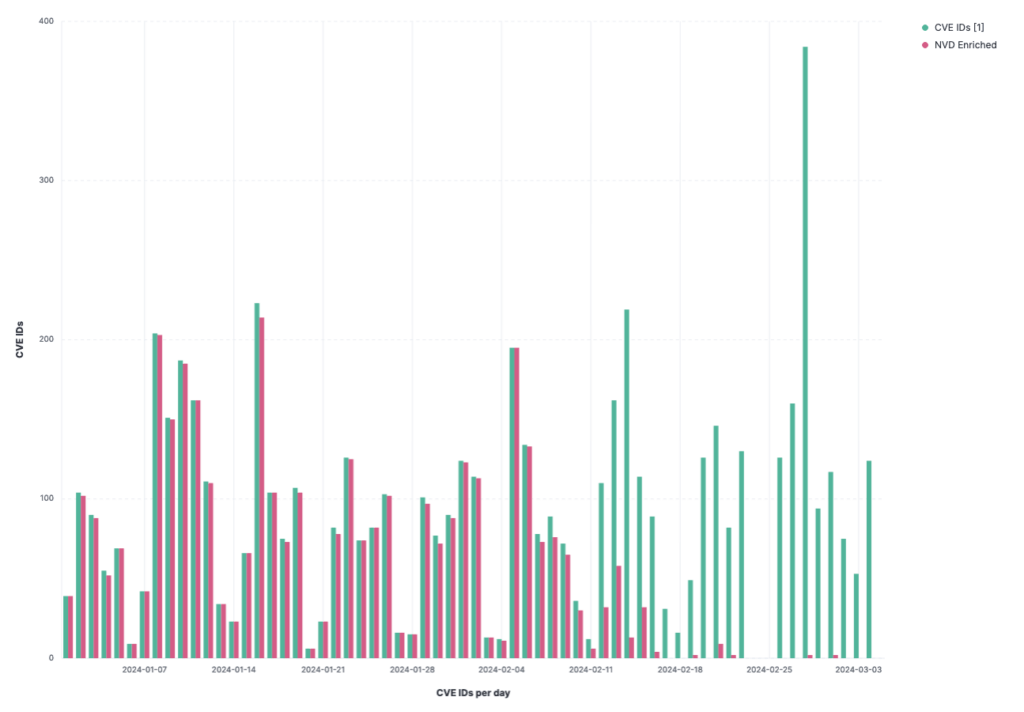
For more than a month, staff at the US National Institute of Standards and Technology (NIST) has stopped enriching CVE vulnerability data added to the National Vulnerability Database (NVD).
More than 2,100 CVE entries have been published without crucial metadata information—a process called "enrichment."
Enrichment data is crucial to anyone viewing the NVD. It provides basic details such as the name of software products impacted by the CVE, the vulnerability's CVSS severity scores, CVE and CWE data, a basic description of the bug, and patching status.
The lack of such information has left the NVD a mere husk that just lists CVE identifiers with no background or context, making the database nearly useless for infosec professionals.
An example is CVE-2024-2193 (snapshot), a vulnerability disclosed this week known as GhostRace, which impacts processors from all the major chipmakers. Absolutely no information is provided on its NVD page except the CVE ID itself.
The issues began around February 15, when NIST put a banner on the NVD website announcing delays in publishing information on current CVEs.
NIST announced delays in analysis efforts as it was working on establishing a consortium to revamp its normal operations.

While NIST foresaw delays, the cybersecurity community did not expect what turned out to be an almost full shutdown of the agency's activity.
Since February 15, when the banner was put on the NIST website (per the Wayback Machine), NIST has enriched just 59 CVE entries since February 15, leaving 2,152 vulnerabilities without any description or context—according to data compiled this week by security firm Anchore and Cisco's Jerry Gamblin.
Since the start of the year, 42% of all new CVEs have not been enriched with metadata. Only 3,625 of 6,171 total CVEs are currently listing metadata.
It is unclear what is happening behind NIST's closed doors, but Chainguard's Dan Lorenc perfectly summarizes the chaos that is currently spreading across the entire vulnerability management space and the government sector alike.
"Scanners, analyzers, and most vulnerability tools rely on the NVD to set these fields so they can determine what software is affected by which vulnerabilities. This is a massive issue and the lack of any real statement on the problem is troubling."
"In true government fashion, FedRAMP Rev. 5 was also just released, requiring pretty much any company that wants to do business with the Federal Government to use the NVD as a source-of-truth and remediate all known vulnerabilities inside it. It feels like NIST is somehow trying to wind this program down or hand it off, while other areas of the government are forcing it's adoption. What is going on here?"
The chaos from NIST's sudden leave of absence from managing the NVD is not restricted to CVE enrichment backlogs. The NVD API has also been having issues as well—and worse than before.
This has led VulnCheck to release what it calls VulnCheck NVD++, a free and more reliable clone of the NVD API, so some automation tools can continue to work until NIST is ready with its "consortium."
VulnCheck says it is working on adding its own enrichment data to the newer CVEs, but no timeline has been set for its launch.
Until then, all eyes are on NIST on how and when all this all ends.
Breaches, hacks, and security incidents
Change Healthcare investigation: The US Department of Health has launched a formal inquiry into UnitedHealth over its Change Healthcare hack. The AlphV ransomware gang breached Change Healthcare in mid-February. The incident is still impacting billing, prescription services, and basic healthcare at pharmacies and hospitals across the US. The investigation will look at how UnitedHealth dealt with the attack and its aftermath.
Alabama DDoS attacks: Alabama state government websites have come under DDoS attacks this week. [Additional coverage in APR]
Meduza DDoS attacks: Independent Russian news site Meduza says it is under heavy DDoS attacks from Russian authorities. The organization says the attacks "increased simultaneously with the murder of Alexei Navalny" and are the largest it has faced so far. Meduza also received multiple warnings from Google that state-sponsored hackers had tried to access its accounts.
Moscow subway DDoS: The IT Army of Ukraine claimed responsibility for a DDoS attack that took down the IT systems of Moscow's subway system. The attack hit the Troika fare payment system.
Acer data breach: Taiwanese hardware maker Acer has confirmed a data breach at its Philippines branch after the personal data of its local employees was stolen from a third-party contractor. The data was later leaked on a hacking forum. [Additional coverage in the Manilla Bulletin]
Leicester cyberattack: The British city of Leicester has suffered a cybersecurity incident. The attack impacted the city's IT systems and phone lines. Officials say they are working with the UK NCSC to investigate the incident. They expect the outage to last several days.
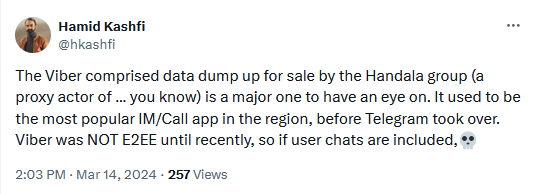
Viber hack: A pro-Palestinian hacktivist group named Handala Hack claims to have breached the Viber instant messaging service. In a Telegram post, the group claimed it stole over 740GB of data from the company's servers, including Viber's source code. Viber was founded in 2010 in Israel and was acquired by Rakuten in 2014.
General tech and privacy
Firefox old add-ons: Mozilla says it plans to continue supporting older add-ons built on the old Manifest V2 extension API, even if it now supports the newer and more neutered V3.
Google SIMA: Google has launched a new generative AI named Scalable Instructable Multiworld Agent (SIMA) that can follow natural language instructions and render 3D and video game assets.
Real-time Safe Browsing: Google is enabling real-time Safe Browsing for Chrome users.
"Previously, the Standard protection mode of Safe Browsing used a list stored on your device to check if a site or file was known to be potentially dangerous. That list is updated every 30 to 60 minutes — but we’ve found that the average malicious site actually exists for less than 10 minutes. So now, the Standard protection mode for Chrome on desktop and iOS will check sites against Google’s server-side list of known bad sites in real time."
Microsoft Copilot for Security: Microsoft has announced that its Copilot for Security service will be generally available on April 1. The service is a generative AI solution for cybersecurity teams.
Government, politics, and policy
US Houses passes TikTok ban: The US House of Representatives has passed a bill that would force TikTok to divest its Chinese parent company or get banned in the US. The bill has advanced to the Senate floor. TikTok said it would exhaust all legal avenues to block the bill. President Biden said he would sign the bill if it passed. [Additional coverage in NBC News]
Chinese safe/lock backdoors: US Senator Ron Wyden has urged the National Counterintelligence and Security Center to issue a security advisory about Chinese-made safes and smart locks. The Senator claims these products may contain backdoor code that can open the locks. Sen. Wyden claims threat actors could abuse these backdoors to steal sensitive information from US companies, such as trade secrets and other intellectual property.
CISA secure software development attestation form: CISA has rolled out an attestation form that requires federal contractors to detail minimum required security standards used in software that interacts with government systems.
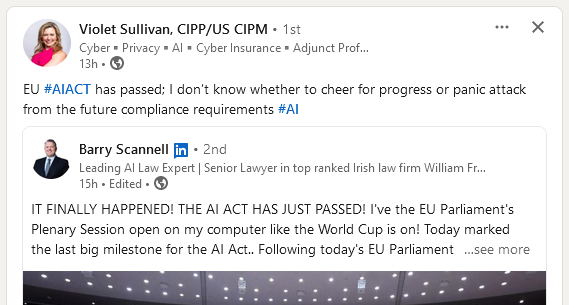
EU AI Act: The European Parliament passed the Artificial Intelligence Act, the world's first major act to regulate the use of AI. The act passed with 523 out of 618 votes. The new legislation bans the use of AI applications that threaten citizens' rights. This includes biometric categorization, emotion recognition, and predictive policing systems. The EU's AI Act includes exemptions for the use of biometric identification systems by law enforcement agencies under strict conditions. [Additional coverage in the BBC]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Derek Hanson, Yubico's VP of Solutions Architecture and Alliances. Derek covers the different reasons organizations are investing in passkeys, what organizations need to know to deploy them successfully, and warns that too often, current deployments are too focused on authorization rather than looking at the end-user holistically.

Cybercrime and threat intel
LockBit member sent to prison: A Canadian judge has sentenced a member of the LockBit ransomware group to four years in prison. Russian-Canadian Mikhail Vasiliev was arrested in November 2022 for LockBit attacks as far back as 2020. Vasiliev pleaded guilty in February this year. He also consented to his extradition to the US, where he also faces charges for LockBit attacks. [Additional coverage in CTV News]
Russian cryptominer sent to prison: A Russian court has sentenced a young man to three years of restriction of freedom. Officials say Alexey Murzin infected local computers at local internet cafes with a cryptominer. He visited the cafes as a client, bypassed security controls, and deployed the T-Rex mining program. He worked with an accomplice and allegedly made almost $220,000. As part of his sentence, Murzin must regularly report to police, observe a curfew, and be banned from attending public events. [Additional coverage in 66.ru]
Malware coder sent to jail in Belarus: A Belarusian judge has sentenced a young boy to five years in a correctional colony for developing malware. Officials said the malware was used in phishing attacks to steal money from Belarusian citizens. The boy shared the malware online, which was then used by more than 700 other individuals. The teen is a minor and a student at a Minsk school. [Additional coverage in TVR]
Tech support companies fined: The FTC has fined two tech support companies $26 million for tricking consumers into buying computer repair services. Restoro and Reimage lured users to websites that showed fake Microsoft pop-ups claiming computers were infected with malware. The companies then sold software to remove the malware for fees that ranged from $27 to $58. The FTC says the two companies made tens of millions of dollars from the scheme, which primarily targeted the elderly. Both companies are based in Cyprus. More on Restoro's tactics can be found here.
Tech support scam seizure: The US government has seized $1.4 million worth of cryptocurrency from tech support scammers.
Bitcoin Fog admin convicted: A federal jury has convicted a Russian-Swedish national on money laundering charges for running the Bitcoin Fog cryptocurrency mixer. Officials say Roman Sterlingov laundered more than $400 million worth of Bitcoin between 2011 and 2021. In an interview with Wired, Sterlingov's lawyer attacked blockchain tracking company Chainalysis, which helped US law enforcement identify and arrest his client. He called the company's tools "junk science" and described Chainalysis as the "Theranos of blockchain analysis." Sterlingov faces tens of years in prison.
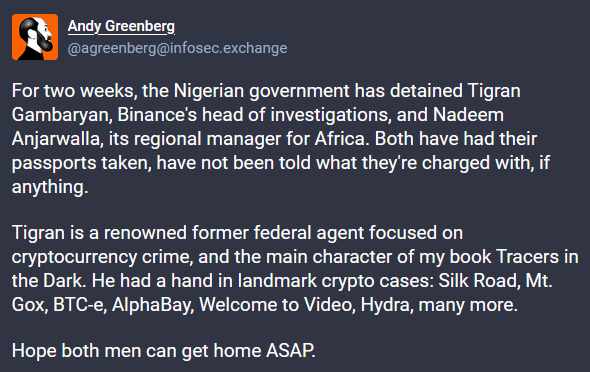
Nigeria detains Binance execs: Nigerian officials have detained two Binance executives since February 26. Officials have not filed official charges. The two were placed under house arrest and had their passports seized. One of them is Tigran Gambaryan, a former US federal agent specialized in crypto crimes, who now leads Binance's criminal investigations team. [Additional coverage in Wired]
Fake investment platform: Netcraft's security team looks at one of the many fake investment platforms that are currently plaguing social media networks with their crappy yet very effective ads.
Chinese malvertising: Kaspersky has published a report on a malvertising campaign targeting Chinese-speaking users with boobytrapped text editors.
Residential proxies market: Orange and Sekoia's threat intel team has published a top-down overview of the residential proxy market where threat actors can redirect malicious traffic through home PCs infected with malware or other types of shady apps or SDKs.
DDP abuse: Cisco Talos looks at how threat actors are abusing digital document publishing (DDP) sites for phishing and credential theft. DDPs are online platforms that allow users to host documents online. Examples of DDP sites abused in the wild include Publuu, Marq, FlipSnack, Issuu, FlippingBook, RelayTo, and SimpleBooklet.
eSIM swapping: Russian security firm FACCT claims it discovered what appears to be first SIM swapping incidents that impact owners of electronic SIMs (eSIMs). Details are scarce, but the company claims the attackers tried to steal money from Russian bank accounts.
Threat/trend reports: Some infosec reports covering industry threats and trends came out from Red Canary, Claroty, Arete, and Kaspersky.
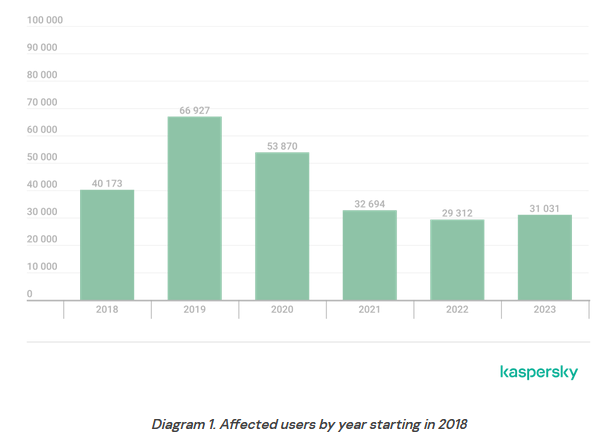
2023 spyware numbers: More than 31,000 users were infected with stalkerware apps in 2023. The number is more than half the peak stalkerware apps saw in 2019 when they were found on more than 66,000 devices. The most prevalent threat last year was an app named TrackView that Kaspersky researchers have spotted on more than 4,000 devices. According to Kaspersky, stalkerware is more common on Android devices.
Malware technical reports
FakeBat: The Malwarebytes team looks at FakeBat, a malware family (still) distributed via malicious Google ads.
RisePro: G DATA researchers look at a campaign that abuses GitHub repositories claiming to host cracked software but which infect users with the RisePro malware.
VCURMS: Fortinet researchers have published a report on VCURMS, a new Java-based RAT that is currently being distributed in the wild in campaigns together with the more well-known STRRAT.
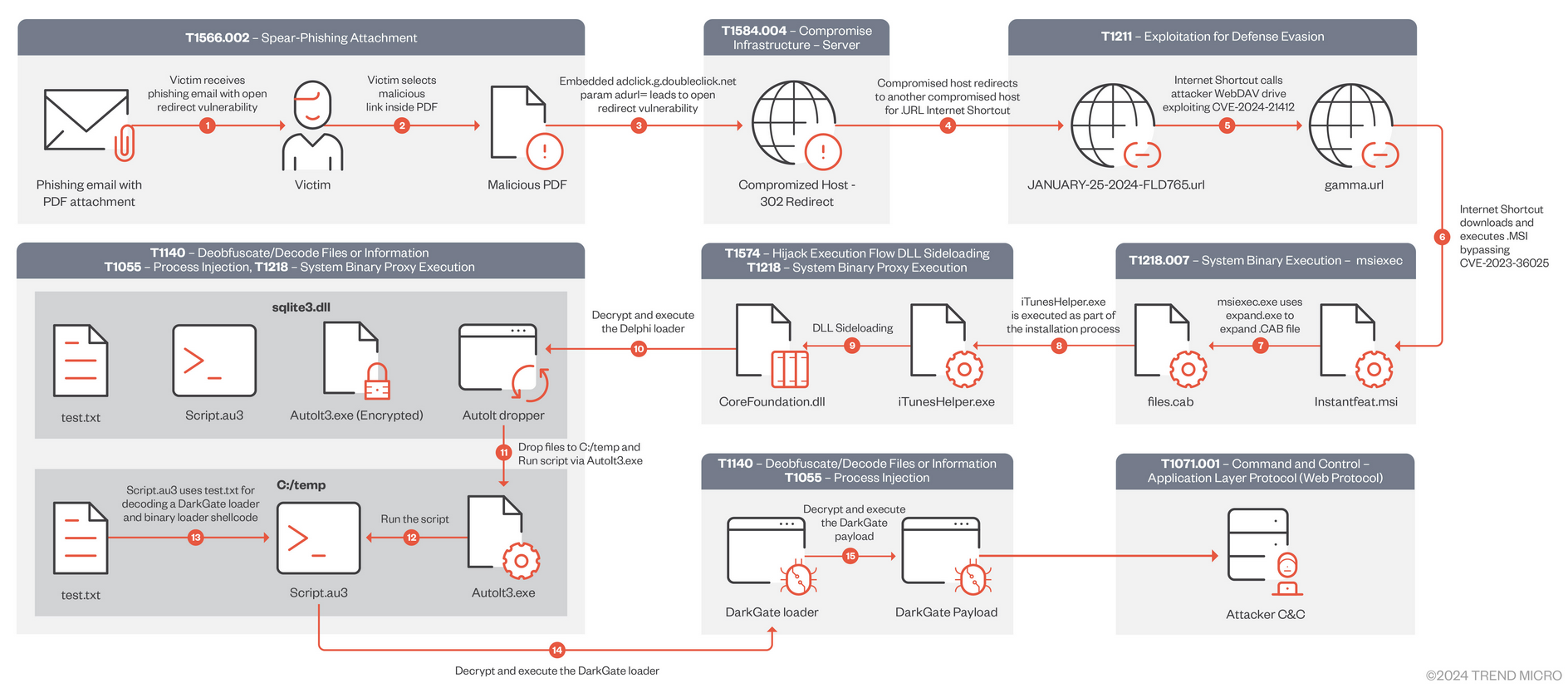
DarkGate zero-day abuse: The operators of the DarkGate malware have exploited a Windows zero-day vulnerability in attacks that began in January this year. The zero-day (CVE-2024-21412) allowed the group to bypass the Windows Defender SmartScreen and run malicious internet shortcut files on targeted systems. Microsoft patched the zero-day as part of its February Patch Tuesday. DarkGate is the second threat actor that abused the zero-day before it was patched. The first was Water Hydra, a group also known as Evilnum.
Donex ransomware: ShadowStackRE has published a report on Donex, a new ransomware gang that began launching attacks this month.
Sponsor Section
YubiKeys slashes exposure to security breaches from phishing and credential thefts by 99.9% and reduces administrative overhead. Create your own customized Forrester Consulting Total Economic Impact™ study tailored for your organization here: Yubi.co/TEI.
APTs, cyber-espionage, and info-ops
CIA info op: Former US President Donald Trump ordered the CIA to launch a covert influence operation against China in 2019. The campaign took place on Chinese social media and spread negative narratives about Xi Jinping and the country's government. CIA operatives spread rumors that Chinese officials were hiding money overseas and that China Belt and Road Initiative was corrupt and wasteful. US officials told Reuters that the campaign's narratives were based on facts despite being carried out by intelligence operatives. [Additional coverage in Reuters]
DPRK returns to Tornado Cash: North Korean hackers have laundered more than $12 million worth of assets stolen from HTX in November of 2023. The funds were laundered through the remnants of the Tornade Cash mixing service. According to Elliptic researchers, this marks the first time North Korean hackers used the service since August 2022, when it was sanctioned by the US. Elliptic says hackers used the Sinbad service but were forced back to Tornado Cash after US authorities seized Sinbad at the end of last year.
Blind Eagle: A threat actor tracked as Blind Eagle has shifted operations and is targeting businesses across North America. According to eSentire, the group targeted Spanish-speaking users in the North American manufacturing sector. The group is believed to operate out of South America, and most of its past attacks have targeted Colombia and other Latin American companies.
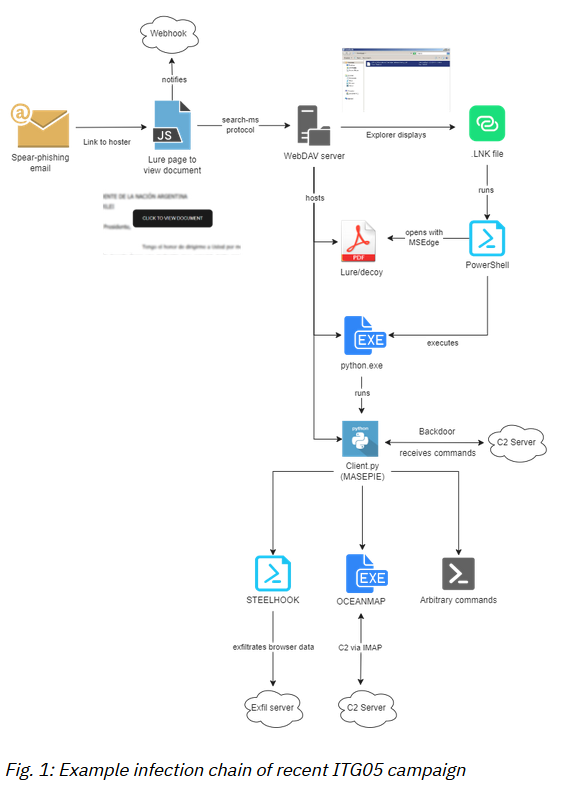
ITG05: IBM's X-Force team has published a report on ITG05 (APT28) and its latest malware arsenal consisting of malware such as STEELHOOK, OCEANMAP, MASEPIE, and CREDOMAP.
Vulnerabilities, security research, and bug bounty
Cisco security updates: Cisco has released or updated seven security advisories for IOS XR.
Jenkins vulnerability: Security researcher Guillaume Quéré has published a technical report on CVE-2024-23897, a major bug in the Jenkins CLI component that allows attackers to hijack Jenkins installs. The bug was patched in January this year and has seen exploitation in the wild.
Fortinet vulnerabilities: Horizon3 researchers have published details on a batch of vulnerabilities in Fortinet's Wireless LAN Manager (WLM) component. Horizon3 says it reported nine issues to Fortinet but only seven got patched.
Confluence exploitation: GreyNoise looks at recent attacks targeting CVE-2023-22527, a template injection vulnerability in Atlassian Confluence servers that was patched in January. GreyNoise says the bug is being used to deploy cryptominers and worms.
Irish disclosure drama: It took two years for a bug in Ireland's COVID-19 vaccination platform to finally come out. The bug allegedly leaked the personal data of more than one million Irish citizens. [Additional coverage in TechCrunch]
ChatGPT security flaw: Salt Security has discovered vulnerabilities in ChatGPT that can grant attackers access to third-party accounts if users had connected ChatGPT to other services via GPT plugins.
FileCatalyst PoC: Nettitude has published a technical analysis and PoC for a directory traversal vulnerability (CVE-2024-25153) in Fortra FileCatalyst file transfer solutions that allows for unauth RCE attacks. The vulnerability was patched in August of last year, just four days after its discovery.
GhostRace: Academics have developed a new side-channel attack that can be used to leak data from modern CPUs. The attack is named GhostRace, and researchers describe it as a speculative race condition (SRC). GhostRace (CVE-2024-2193) impacts all the major CPU vendors, such as Intel, AMD, ARM, and IBM. The attack requires physical or privileged access to a targeted system. On some platforms, GhostRace attacks can be prevented with the older Spectre mitigations.
Infosec industry
New tool—LTair: NCC Group has developed a tool named LTair to test if telcos have deployed correct implementations of the LTE standard. It's not yet open source, though.
New tool—Scrutineer: Software engineer Raphael Sprenger has released Scrutineer, a CLI tool for signing and verifying git commits. It also has a companion web app that can be used to monitor the expiration of TLS certificates via RSS.
New tool—Ludus: Bad Sector Labs has open-sourced a tool named Ludus. It is a system for building cyber environments for testing and development, aka cyber ranges.
New tool—Misconfiguration Manager: SpecterOps has released Misconfiguration Manager, a central hub for common Microsoft misconfigurations that can be abused in cyberattacks and their respective mitigation guidance.
Acquisition news: Zscaler has acquired Israeli risk management startup Avalor for $350 million.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at recent efforts to disrupt ransomware gangs and discuss what could make these efforts more effective.




