Risky Biz News: New side-channel attack disclosed in Intel and AMD processors
In other news: Uniswap users lose $8 million in phishing attack; loads of new ransomware gangs are popping up; and Microsoft says VBA macro block reversal is only temporary.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Academics from ETH Zurich published details on Tuesday on a new side-channel attack that impacts modern CPUs from Intel and AMD. The research, named Retbleed, is the latest in a long line of side-channel attacks impacting speculative execution, a feature of modern CPUs where the processors perform data computations in advance as a way to gain processing speed.
In early 2018, academics from different organizations revealed the first two vulnerabilities that take advantage of speculative execution operations by looking at the data that gets processed or discarded during this process, data that can sometimes contain sensitive secrets.
Other side-channel attacks were subsequently discovered, but those initial vulnerabilities, known as Meltdown and Spectre, changed how all major chipmakers looked at CPU design and data security.
One of the defenses that chipmakers and software vendors came up with at the time was a new technique called Reptoline that effectively tried to replace indirect jump and call instructions in the CPU with return instructions since, at the time, return instructions were considered safe from Meltdown and Spectre-like side-channel attacks.
But in their Retbleed research published this week, the ETH Zurich team says they were able to carry out a side-channel attack against modern CPUs through return instructions for the first time, leaking kernel memory containing password hashes from Linux systems.
The researchers said they tested the Retbleed attack in practice on AMD Zen 1, Zen 1+, Zen 2, and Intel Core generation 6–8, but, in theory, AMD CPU families 0x15–0x17 and Intel Core generation 6–8 are all likely affected. In layman's terms, this means that Intel CPUs 3 to 6 years old, and AMD processors 1 to 11 years old, are likely to be affected.
The good news is that since the original Meltdown and Spectre disclosures, chipmakers and OS vendors now have protocols established for dealing with bugs like this in a more timely manner. While fixing Meltdown and Spectre took months and several tries, the ETH Zurich team said that patches for Retbleed have already been prepared and went out during the July 2022 Patch Tuesday, via both OS and cloud infrastructure updates from all the major providers. Compared to the uncertainty during the Meltdown and Spectre days, all users have to do these days is update their operating system.
Retbleed patches for AMD processors are tracked as CVE-2022-29900, while the Intel fixes are CVE-2022-29901, with additional mitigation information from Intel being available through their blog as well.
ETH researchers noted that installing these patches will have an impact on the CPU's performance metrics between 14% and 39%, and another issue they found in AMD processors that they named Phantom JMPs (CVE-2022-23825) might even come with a 209% performance overhead.
Concerns about this performance hit will most likely result in many people not installing the patches to protect themselves against "exotic attacks" that are unlikely to be seen in the wild, at least yet.
In some ways, this side channel research is similar to the first cryptography attacks from the 90s and early 2000s, all of which broke smaller pieces of various cryptographic operations, with each new research building on top of the previous work until. At a certain point, major cryptographic algorithms started falling.
And the true risk here is difficult to assess since detections for side-channel attacks don't really exist. It's easy to say something isn't in the wild when you're not looking for it.
So, while the side-channel attacks of today may seem "exotic" and "impractical" to some, this type of research tends to be cumulative. Eventually it'll have enough weight for attackers to bother with it. Meanwhile, we'd do well to pay attention to this sort of work and use it to move the needle on CPU design and security.
Breaches and hacks
Uniswap phishing campaign: Customers of the Uniswap crypto-exchange have lost millions of US dollars worth of cryptocurrency following a phishing campaign that took place over the past few days. According to early estimates from blockchain security firm SlowMist, the losses are currently estimated to be around 7,500 ETH, worth more than $8 million, The Record and Check Point reported.
ECB incident: The European Central Bank said on Tuesday that its president, Christine Lagarde, was targeted in an attempted cyberattack. The ECB said it quickly identified and stopped the attack and that no information was compromised as a result. According to a report, Mrs. Lagarde was allegedly contacted by the attacker via an SMS message that appeared to come from former German Chancellor Angela Merkel, asking her to initiate a conversation via WhatsApp. Mrs. Lagarde discovered the ruse after calling the real Mrs. Merkel to confirm.
General tech and privacy
Microsoft clarifies VBA macro block rollback: After getting blasted by literally everyone in the cybersecurity industry last week, Microsoft said that its decision to roll back a security-related change (the blocking of VBA macros in Office apps) is only a temporary solution and that the company intends to eventually re-enforce the VBA macro block—although the company did not say when. [Additional coverage in The Record]
Windows Autopatch: Microsoft has formally launched its Windows Autopatch service, a feature for its enterprise customers that could be used to automate the installation of Windows updates on large fleets of PCs. Windows Autopatch is now available for Microsoft customers with E3 and E5 licenses.

IBM knee-caps Rumble & RT: US tech giant IBM has pulled its services for US right-wing video portal Rumble. The company moved to deplatform Rumble after an inquiry from Cyberscoop's AJ Vicens, who asked why IBM was helping RT air its propaganda through its Rumble accounts.
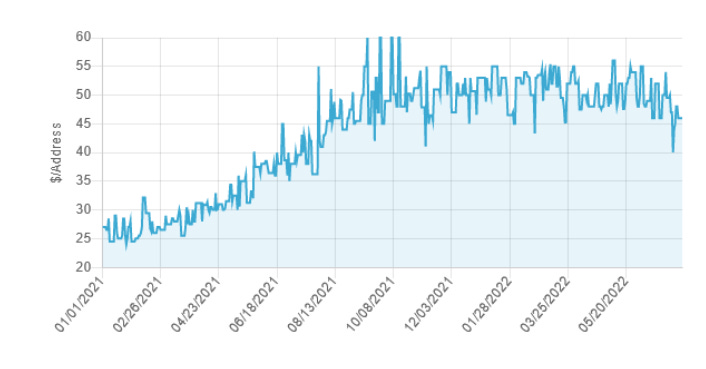
IPv4 address price doubles in a year: The price of an IPv4 address has almost doubled over the past year, according to SIDN, the Netherlands' official domain registrar. Prices have gone up from only $5/IP in 2015 to $25-$30 last year and $50-$60 today, showing the growing scarcity in the IPv4 market.
Government, politics, and policy
Germany rethinks its approach to cybersecurity: The German Federal Ministry of the Interior has published its plan to revamp the country's approach to cybersecurity. Among the proposed changes are initiatives to move the responsibility for the country's cyber-security defense from local state governments to the federal government's BKI agency, as well as giving German agencies the power to respond to cyberattacks. The new plan will go under public debate and needs to pass through the German Parliament.
US has an outdated view of the internet: A report published by the Council on Foreign Relations this week urges the US government to confront and rethink its current view of the global internet as a fragmented network controlled by multiple aggressive states and not the global utopian collaboration network the US government first envisioned 40 years ago. The CFR argues that the internet has become a haven for corporate and government espionage, political manipulation through disinformation and misinformation campaigns, and various criminal activities. CFR officials urge Washington to work with allies to protect as much as possible the openness of the current internet while also cracking down on its negative parts, with some proposals like:
- Adopt a shared policy on digital privacy, interoperable with the EU's GDPR.
- Resolve outstanding issues on US-European Union (EU) data transfers.
- Create an international cybercrime center.
- Declare norms against destructive attacks on election and financial systems.
- Negotiate with adversaries to establish limits on cyber operations directed at nuclear command, control, and communications (NC3) systems.
- Develop coalition-wide practices for the Vulnerabilities Equities Process (VEP).
- Adopt greater transparency about defend-forward actions.
- Hold states accountable for malicious activity emanating from their territories.
- Clean up US cyberspace by offering incentives for internet service providers (ISPs) and cloud providers to reduce malicious activity within their infrastructure.
- Address the domestic intelligence gap, and more.
China to enforce new data export rules: The Chinese government passed new legislation last week that introduced new rules for companies that send the data of Chinese citizens to servers abroad. Any Chinese tech company that has sent the data of more than 100,000 Chinese citizens abroad will be subject to audits and security audits by the Chinese Cybersecurity Authority (CAC). The CAC will primarily check if companies took steps to protect the exported data against hacks, interception, or tampering. The new law will enter into effect on September 1, 2022, but will apply retroactively to all companies that have exported user data abroad after January 1, 2021.
Cybercrime and threat intel
BianLian ransomware group: Threat intelligence company BetterCyber has discovered a new ransomware group named BianLian, which also operates a leak site on the dark web, where it publishes data from victims who refuse to pay.
A new #ransomware group named #BianLian claims to have hacked #Mooresville Schools (@MrsvlPioneers), a public school district in Indiana, 🇺🇸. The group claims to have stolen ~4,200 student records containing phone numbers, email addresses, and social security numbers...
— BetterCyber (@_bettercyber_) 8:49 PM ∙ Jul 11, 2022
Lilith: Another new ransomware gang that made its presence felt this month is a group called Lilith. This is now the sixth new major ransomware gang that has popped up on the scene in the past month after Cheers, Yanluowang, 0mega, RedAlert, and BianLian.
Leak site for the new Lilith ransomware gang. No victims listed yet.
— Catalin Cimpanu (@campuscodi) 10:01 PM ∙ Jul 12, 2022
NWGEN: A new threat actor calling itself NWGEN appears to have split from the LAPSUS$ gang and is carrying out new attacks. According to Microsoft's Christopher Glyer, the group uses the same tradecraft used by the original LAPSUS$ gang, which should make it easier to detect and mitigate possible attacks on targeted organizations. Per Kevin Beaumont, NWGEN appears to be dabbling in ransomware too, which is super bad news for some orgs.
Remember LAPSUS?
— Kevin Beaumont (@GossiTheDog) 12:26 PM ∙ Jul 11, 2022
Read this blog and pay attention to it. People are back doing attacks for actual deployed ransomware this time.
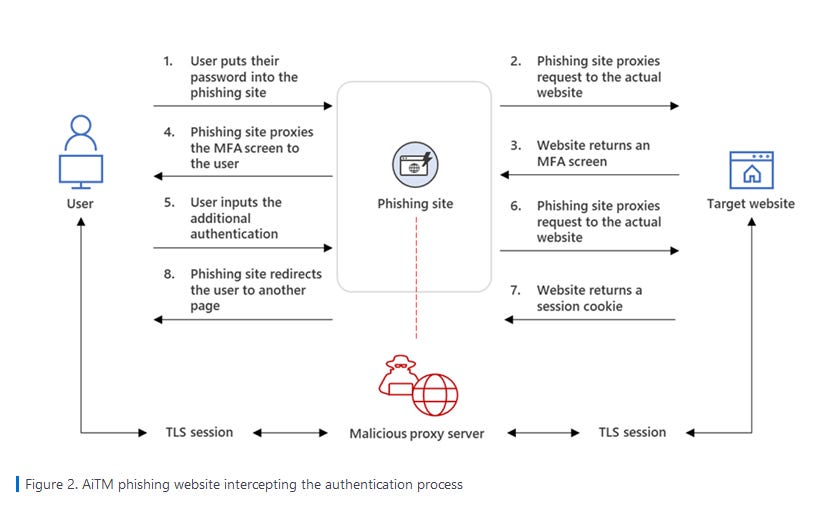
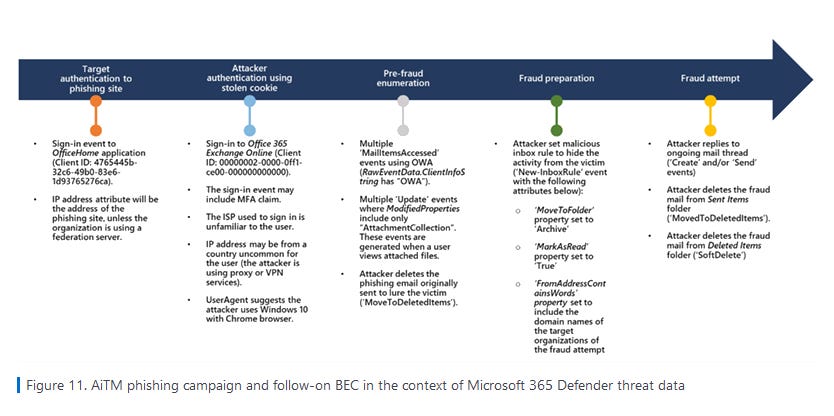
Reverse proxy phishing: Microsoft has published a report on a large-scale phishing campaign that used reverse proxy servers for its phishing sites. This technique, also known as adversary-in-the-middle (AiTM) phishing, allowed the threat actors to obtain not only credentials from victims but also the authentication cookies that are generated after victims go through a legitimate 2FA challenge. Microsoft said this campaign has been running since September 2021, has hit more than 10,000 organizations, and has been linked to several BEC attacks.

Nigerian threat actor: The team at DomainTools published a report this week on the activities of a Nigerian threat actor, which they linked to an extensive campaign to impersonate medical institutions in the US with the aim of fraudulently procuring medical equipment from the manufacturers in the name of hospital systems.
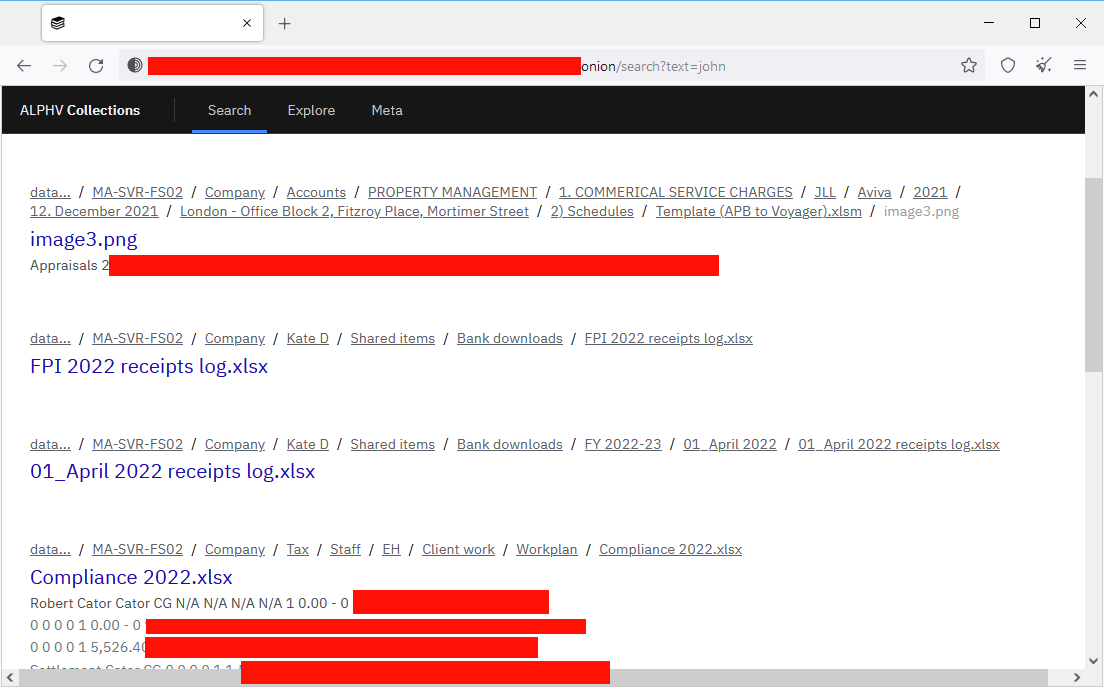
AlphV evolves: The operators of the AlphV (BlackCat) ransomware have launched a dedicated section on their leak site that allows anyone to search through all the data they stole and leaked from past victims. More in this Resecurity report.
Threat actor impersonates cybersecurity firms: Crowdstrike said it identified a threat actor carrying out a phishing campaign that impersonated various prominent cybersecurity companies. Crowdstrike wasn't able to specifically identify the threat actor behind this operation but says various operational details suggest this threat actor uses tactics similar to those of the Wizard Spider (Conti) group.
Hagga group: Team Cymru published a report on the backend infrastructure of Hagga, a threat actor that has been known to distribute infostealers since the start of 2020 [1, 2, 3, 4]. The group is also known as Aggah in some reports.
Malware technical reports
Coinminers targeting MSSQL servers: The DFIR Report team published a technical analysis on Monday on a brute-force campaign targeting the admin accounts of MSSQL database servers. The researchers said the goal of this campaign is to compromise databases and then deploy a cryptocurrency-mining app to generate profits for the attackers.
Coinminers abuse GitHub Actions and Azure VMs: A report we missed from last week is one from Trend Micro, which uncovered a coinminer gang abusing GitHub Actions to mine cryptocurrency using Azure VMs on compromised cloud infrastructure.
Hive v5 decrypter: A security researcher named reecDeep has released a free tool that can help victims that had their files locked by version 5 of the Hive ransomware recover their files. Previously, South Korea's cyber-security agency KISA released decrypters for the first four versions.
ChromeLoader: Palo Alto Networks published a report on Tuesday on ChromeLoader (also known as Choziosi Loader and ChromeBack), a malware strain that appeared in January this year and which works by infecting the settings of Chrome browsers to hijack search queries and redirect users to malicious sites. Another report on this threat is also available from Red Canary.
APTs and cyber-espionage
UAC-0056: In a security alert published on Monday, Ukraine's CERT team said that it detected a new spear-phishing operation carried out by a Russian threat group known as UAC-0056. This campaign is being carried out from hacked Ukrainian government accounts and aims to infect recipients with Cobalt Strike beacon backdoors.
Disinformation efforts in May: The Google TAG team has published its actions against disinformation efforts that took place on Google services in the month of May 2022. TAG said actions were taken against accounts linked to threat groups operating out of China, Iran, and Russia.
New Intrusion Truth revelations coming: Intrusion Truth, the mysterious group that has doxed the identities and real-life affiliations of at least four Chinese cyber-espionage groups, hinted on Tuesday that they have a new report coming out soon.
It’s been a while....Stay tuned over the coming days....
— Intrusion Truth (@intrusion_truth) 11:47 AM ∙ Jul 12, 2022
#youhavebeenwarned
Vulnerabilities and bug bounty
New AWS IAM Authenticator vulnerability: Gafnit Amiga, a security researcher with Lightspin, discovered a new authentication bypass in the AWS IAM service, a vulnerability that could be used to access AWS customers' Kubernetes instances. In a security bulletin on Monday, AWS said it fixed the issue at the end of June when it rolled out fixes for all impacted servers. The vulnerability is currently tracked as CVE-2022-2385.
Microsoft Patch Tuesday: The Microsoft Patch Tuesday security updates for the month of July 2022 are officially out. This month, Microsoft fixed 86 vulnerabilities across several products, including CVE-2022-22047, an elevation of privilege vulnerability that was exploited in the wild before the company's patches.
Bad Azure vulnerability: Among the fixes included in this month's Patch Tuesday is also a vulnerability in Azure Site Recovery, a service that provides disaster recovery options for cloud resources. Tenable says that this bug—tracked as CVE-2022-33675—can allow threat actors to gain SYSTEM-level privileges on cloud instances where this service is installed. Microsoft said it released Azure Site Recovery 9.49 to address this and other security issues.
MitM on FreshWorks: Vulnerability researchers from Visma's Red Team have uncovered a serious zero-interaction vulnerability in the FreshService inventory management software. The vulnerability makes it possible for malicious third parties to perform a man-in-the-middle attack on FreshService inventory management agents and deploy malicious updates that can run with administrative privileges on the affected systems.
Kubernetes NGINX Ingress Controller vulnerabilities: The team at Lightspin has published an overview of four recent vulnerabilities in the Kubernetes NGINX Ingress Controller that have been disclosed since October last year. One of the vulnerabilities, CVE-2021-25742, also came under active exploitation.
Other security updates: Besides Microsoft, other companies that recently released security updates also include the Android project, Cisco, Intel, Adobe, VMWare, Citrix, and SAP.
Android zero-day: Unfortunately, a vulnerability in the Android kernel used on Google smartphones that was disclosed on Twitter last week did not receive a patch. According to Android Police, Google didn't patch the issue because they didn't know about it, as the researcher did not notify the company before their tweet.
The latest Google Pixel 6 pwned with a 0day in kernel! Achieved arbitrary read/write to escalate privilege and disable SELinux without hijacking control flow. The bug also affects Pixel 6 Pro, other Pixels are not affected :)
— Zhenpeng Lin (@Markak_) 5:55 PM ∙ Jul 5, 2022




