Risky Biz News: New Scattered Spider group targets telcos for SIM swapping attacks
In other news: Amnesty International says it was hacked by China; EU funds Cyber Lab in Ukraine; Callisto APT so hot right now!
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Please be aware that due to a certificate rotation on our main website and audio distribution server, our podcast’s Spotify feed is currently down and won’t show any new episodes. Until this issue is resolved on Spotify’s side, you can subscribe via the RSS feed above or via any other podcatcher to get new episodes.
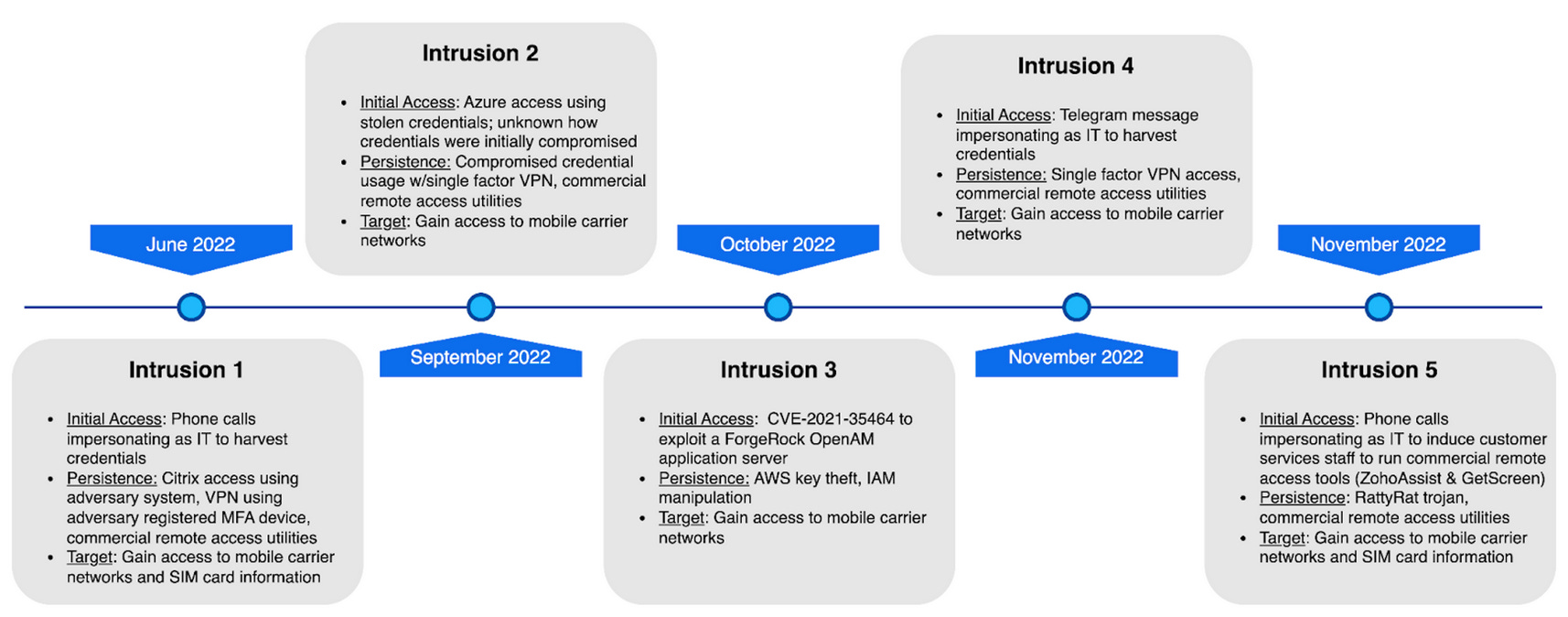
A new financially-motivated threat actor tracked as Scattered Spider has been on a rampage over the past few months, hacking into the networks of telcos and outsourcing companies in order to gain access to customer information and, in some cases, carry out SIM-swapping attacks.
The attacks have been taking place since June this year and follow a model previously made popular by the Lapsus$ gang.
The initial stages start with phone calls and text or Telegram messages to a company's employees, posing as its IT department. The calls and messages ask employees to visit a phishing site or instruct them to download a boobytrapped application.
Phished credentials and compromised systems are then used to establish a foothold inside a company's network, with the group quickly acting to move laterally across the network and create multiple persistence methods for future access.
Security firm CrowdStrike—which detailed Scattered Spider's modus operandi in a report published last Friday—described the group and its actions as "extremely persistent and brazen."
They operate using many open-source tools and across Windows, Linux, Google Workspace, AzureAD, Microsoft 365, and AWS environments, sometimes in a very noisy way.
If their intrusions are detected, Scattered Spider operators will re-access a victim's network through their backdoors and use their access to roll back security mitigations put in place by the targeted organisation. If they lose access to a network, CrowdStrike says the group immediately moves to a new target as if nothing happened.
CrowdStrike said that "swift and bold" security measures to isolate compromised environments had the best results in kicking the group out of a victim's network and making it move to a new target.
Breaches and hacks
Amnesty International hack: A Chinese APT group has breached the network of the Canadian branch of Amnesty International, the organization said on Monday. The breach was discovered in early October and was investigated and confirmed with the help of cybersecurity firm Secureworks. Speaking to reporters, Amnesty International said the hackers searched for information on China, Hong Kong, and prominent Chinese activists. The organization said there found no evidence to suggest that Chinese hackers stole information on its donors and members. In August, threat intelligence firm Recorded Future warned that a Chinese APT named RedAlpha was registering lookalike domain names impersonating various human rights organizations, including Amnesty International.
It was ransomware: Rackspace has confirmed that the major outage of its Exchange email server infrastructure that took place over the weekend was caused by ransomware.
Mercury IT ransomware incident: The New Zealand government said that a ransomware attack on Mercury IT, a major local MSP, has impacted the services of several private and public institutions. The attack took place last week on November 30. According to the NZ Herald, the incident has impacted and compromised the data of the Ministry of Justice, the Ministry of Health, the NZ National Nurses Association, health insurer Accuro, and private industry group BusinessNZ.
Helio crypto-heist: In our last newsletter, we featured a bit about the Ankr DeFi platform being exploited to steal $5 million. Apparently, as Binance was working with Ankr to prevent the hacker from stealing BNB coins, this left the door open for another attacker to exploit the Helio platform and steal $15 million. See CoinDesk's explanation for what happened. It's hard to keep track of the card castle that cryptocurrency protocols are starting to look like.
General tech and privacy
Threema's new Ibex protocol: E2EE instant messaging service Threema has launched a new cryptographic protocol suite named Ibex. The new protocol supports Perfect Forward Secrecy, and Threema said it worked with external cryptographers for more than 18 months to make the protocol "future proof." In addition to deploying Ibex, Threema said it also added E2EE support for group calls, something that very few secure messaging services currently support.
Government, politics, and policy
EU funds Cyber Lab in Ukraine: The EU has financed and delivered software and hardware equipment for the creation of a cyber lab inside the Ukrainian Armed Forces. The lab will allow Ukraine to train military cyber defense professionals in a virtual environment using real-time simulations. The lab was formally unveiled in Kyiv last week, and EU officials hope it will help Ukraine's military detect and respond to cyberattacks faster and more efficiently.
ANSSI boss leaves post: Guillaume Poupard, the director of France's cybersecurity agency ANSSI, said he's leaving his post at the end of the year after almost nine years in the role. Poupard announced his departure on LinkedIn. A day before, Arne Schönbohm, the chief of Germany's BSI intelligence service, also said goodbye to his colleagues on LinkedIn after being dismissed following a political scandal.
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
Dutch SIM swapper gets four years: A 20-year-old from the Dutch town of Eelderwolde was sentenced to four years in prison for breaking into the IT systems of Dutch mobile operator T-Mobile. Officials said the man worked with a 17-year-old and executed spear-phishing and SIM-swapping attacks to break into bank accounts and steal more than €100,000 from dozens of victims. [Coverage in Dutch in RTV Drenthe]
IRS fraudsters arrested: The US Department of Justice has announced the arrest of four suspects, three Nigerians and one UK national, on charges related to identity fraud and filing fraudulent tax returns on behalf of US citizens and businesses. US officials said the suspects used the xDedic cybercrime marketplace to buy access to servers operated by US companies, stole PII data stored on these systems, and then filed fraudulent tax returns seeking huge payouts on behalf of the victims. The suspects were detained in the UK and Sweden in November and December, and DOJ officials said they are working to have them extradited to the US.
Money launderers arrested: Europol and law enforcement across 25 countries have detained 2,469 suspects as part of an international crackdown against money mule gangs. Suspects were detained in Europe, but also in countries as far as Colombia, Singapore, and Australia. Europol said they also seized €17.5 million from the suspects and prevented the funds from being laundered.

BYOF attacks: Researchers with cloud security firm Sysdig say they're seeing attacks carried out by a new threat actor that deploys an open-source tool on infected servers to simplify cross-platform compatibility issues. Named PRoot, the tool deploys a universal filesystem that works across multiple Linux versions. Sysdig says the attacker is installing the tool on compromised systems in order to make their malware compatible with the underlying OS architecture. Sysdig called this novel technique Bring-Your-Own-Filesystem, since it allows the attacker to optimize their malware for PRoot, and then deploy across a wide variety of Linux architectures. While the threat actor appears to be focused on deploying a banal crypto-miner, Sysdig says the technique could be attractive for many other threat actors targeting Linux environments.
Groups X, Y, Z: Jscrambler researchers have an analysis of recent Magecart web skimming operations carried out by three groups they are tracking as Group X, Group Y, and Group Z.
DEV-0139: Microsoft's security team says they spotted a new threat actor they are calling DEV-0139 that has spent the past months targeting cryptocurrency organizations. The group stands out among other threat actors targeting the cryptocurrency space because they operate by impersonating representatives of known cryptocurrency platforms in order to join select and private Telegram channels dedicated to VIP clients and cryptocurrency exchanges. Once inside, Microsoft says that DEV-0139 enters conversations that seek to infect their targets with backdoor malware, typically installed via malicious Office documents.
Vice Society group: Palo Alto Networks has a profile on the Vice Society ransomware and extortion group and its obsession with the edu sector.
New npm malware: Thirteen new malicious npm packages were spotted on Monday. Check out GitHub's security advisory portal for details.
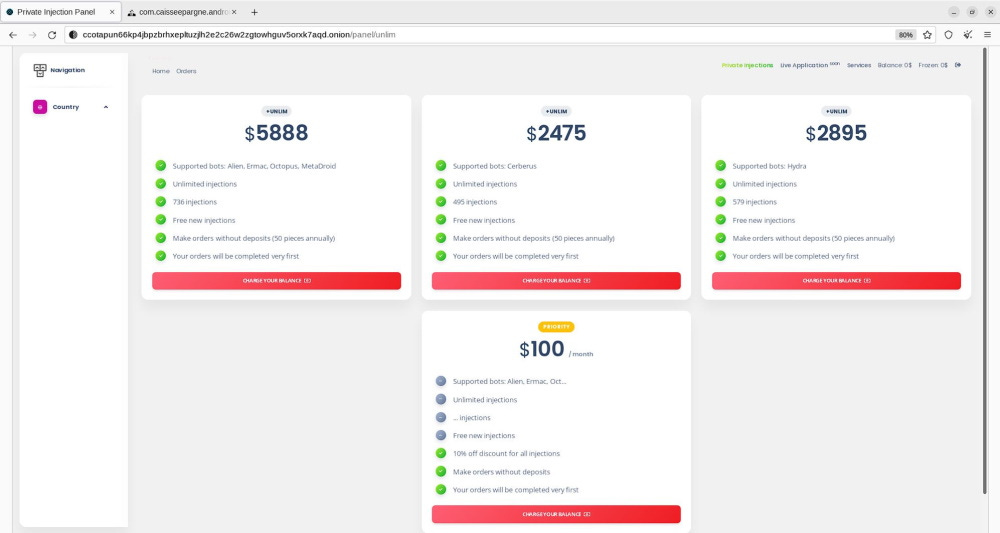
InTheBox: Threat intel analysts at Resecurity said they discovered a new underground cybercrime portal named InTheBox, where malware developers are selling templates for mobile banking login pages. Also known as webinjects, these templates can be used by a variety of Android banking trojans and prompt users to enter their banking account information after they infected their smartphones. Resecurity said the portal launched back in January 2020 and has sold webinject templates compatible with Android banking trojans such as Alien, Cerberus, Ermac, Hydra, Octopus, Poison, and MetaDroid. Different webinject templates can also be acquired, including variations that can also collect two-factor authentication codes, payment card details, or other personal information.
Malware technical reports
IoT malware evasion techniques: Nozomi researchers have a summary of recent techniques used by IoT malware strains to evade detection and reverse-engineering.
REvil ransomware: SecurityScorecard's Vlad Pasca has a technical breakdown of the old REvil ransomware.
DanaBot: Zscaler has an analysis of the DanaBot malware and its infamously advanced obfuscation techniques.
Cryptonite ransomware/wiper: Fortinet says that a ransomware building kit it tracked as Cryptonite is generating malfunctioning ransomware strains that don't provide a way to recover files. While some Cryptonite ransomware samples have been spotted in the wild, the good news is that the project has been removed from GitHub last week, which will most likely limit the damage it can cause.
ZeroBot: Fortinet has a report out on a new IoT malware strain named ZeroBot. The malware is written in Go, and its operator(s) uses exploits for n-day vulnerabilities to deploy the malware to various devices.
Cobalt Strike adoption: PAN's Unit42 research team says it spotted three malware operations that have straight out incorporated components of the Cobalt Strike pen-testing framework into their code. The three malware strains are KoboldLoader, MagnetLoader, and LithiumLoader.
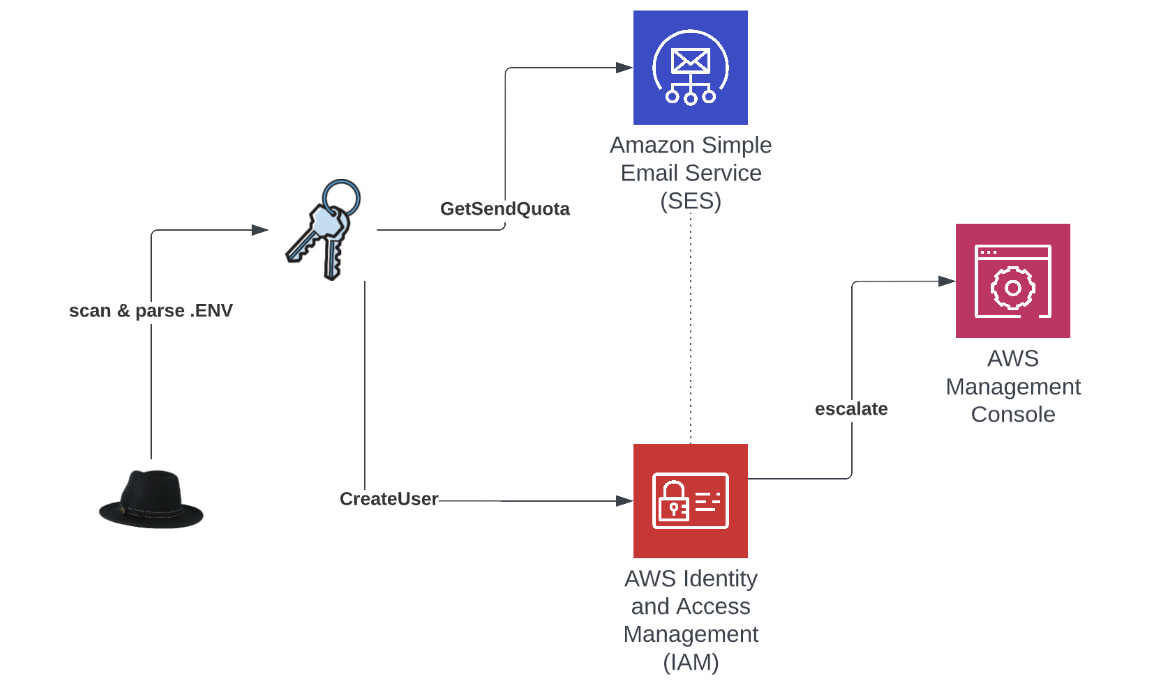
AndroxGh0st: Cloud security company Lacework says it discovered a new threat actor group named Xcatze that uses a Python named AndroxGh0st to take over AWS servers and send out massive email spam campaigns. Lacework says the malware operates by scanning web apps written in the Laravel PHP framework for exposed configuration files to identify and steal server credentials. Researchers said AndroxGh0st specifically searches for AWS, SendGrid, and Twilio credentials, which it uses to take control of email servers and accounts and send out the spam campaigns.
APTs and cyber-espionage
APT42: The Human Rights Watch activist group says that two of its staff members have been targeted in a spear-phishing campaign carried out by APT42 (or Charming Kitten), one of Iran's state-backed cyber-espionage groups. The same campaign also targeted 18 other high-profile activists, journalists, researchers, academics, diplomats, and politicians working on Middle East issues. At least three individuals were compromised, the organization said.
"For the three people whose accounts were known to be compromised, the attackers gained access to their emails, cloud storage drives, calendars, and contacts and also performed a Google Takeout, using a service that exports data from the core and additional services of a Google account."

Callisto APT: PwC's threat intelligence team published a report last week on the spear-phishing operations carried out by Blue Callisto, a Russian cyber-espionage group, throughout 2022. PwC said the campaign focused on obtaining credentials from US and European government officials and organizations linked to national security matters. In addition, since Russia's invasion of Ukraine, the group has also targeted Ukrainian entities and an international organization that investigates war crimes.
TAG-53: Recorded Future also has a report on the same Callisto group, which it tracks as TAG-53.
Callisto: So has Sekoia, and its report is very interesting since it includes the names of a large number of targeted organizations. One particular domain spotted by Sekoia suggest the group may be typosquatting on domains mimicking the Russian Taxation Service and Ministry of Interior.

Mustang Panda: BlackBerry's security team has a breakdown of a recent Mustang Panda APT spear-phishing campaign delivering the PlugX malware.
BackdoorDiplomacy: Bitdefender says they've seen the BackdoorDiplomacy Chinese APT group targeting entities in the Middle East. The attacks, which started in August 2021, exploited the ProxyShell vulnerability to compromise Exchange servers with the IRAFAU and Quarian backdoors and various open-source proxy and remote access tools.
OceanLotus: Chinese security firm Antiy has confirmed the use of the Torii botnet by Vietnamese APT group OceanLotus. Last month, both Weibu and QiAnXin said that OceanLotus operators appear to be using the Torii IoT botnet to disguise the origin of their attacks.
ScarCruft's Chinotto: Korea's CERT team has put out a report on Chinotto, a malware strain used by ScarCruft, a North Korean APT.
Kimsuky: Chinese security firm QiAnXin has a report out on a recent surge in attacks from the Kimsuky APT in light of a recent US-South Korea joint military exercise.
Transparent Tribe: Qihoo 360 researchers have a report out on recent operations of the Transparent Tribe APT that has used Android and Windows malware to target "terrorism." The Qihoo report goes out of its way to praise Pakistan for fighting "terrorism"—which in this case is espionage campaigns targeting the Baloch minority. I guess when your country puts Uyghurs in concentration camps and passes it as "fighting terrorism" and "national security," you got to praise other countries that do the same to normalize the behavior.
APT41 stole COVID relief funds: The US Secret Service says that a Chinese hacking group known as APT41 has stolen more than $20 million in US government COVID-19 relief funds. The group's activities were first highlighted in a Mandiant report published in August 2019. At the time, Mandiant said that while the group typically engages in cyber espionage for the Chinese government, its members were also moonlighting and dabbling in classic cybercrime operations for their own personal profits. [Coverage in NBC News]
Vulnerabilities and bug bounty
AMI BMC vulnerabilities: Eclypsium researchers have discovered three vulnerabilities in the firmware of AMI MegaRAC baseboard management controllers. Eclypsium says the three vulnerabilities can be exploited via the Redfish and IPMI ports for remote code execution that can grant attackers access to the superuser account on the BMC firmware. Baseboard management controllers are typically used to provide remote management of large computer fleets, and are commonly found in enterprise network setups. Eclypsium says that servers manufacturers known to use AMI MegaRAC BMCs for their products include the likes of AMD, Asus, Gigabyte, Inspur, and Qualcomm. The researchers named the vulnerabilities BMC&C.
Netgear router misconfiguration: Tenable researchers say they identified a misconfiguration in Netgear NightHawk SOHO routers. This misconfiguration allowed unrestricted access to any of the router's services via the router's internet-facing IPv6 WAN interface. This meant the router's firewall or DMZ would not block malicious connections to SSH (port 22) and Telnet (port 23) services, exposing routers to brute-forcing via IPv6. The issue was responsibly disclosed and patched.
Android security updates: ...for December 2022 are out!
Infosec industry
ChatGPT tools: Stairwell security researcher Daniel Mayer and Kaspersky researcher Ivan Kwiatkowski have released IDA Pro plugins that use the ChatGPT algorithm to explain decompiled functions. A big warning that these explanations may not be accurate, a warning that should be taken very seriously since StackOverflow has banned ChatGPT-generated answers on its platform due to the large number of inaccuracies in most posts.
New tool—SandboxSecurityTools: Microsoft has released a collection of tools that security researchers can use to test sandbox technologies the company uses for its Windows OS.
New tool—GCPGoat: Online learning platform INE has open-sourced GCPGoat, an intentionally vulnerable-by-design GCP setup that can be used by security professionals to test their skills and learn to detect misconfigurations and vulnerable systems. The company has released similar tools for Azure and AWS infrastructure as well.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




