Risky Biz News: New Russian ICS malware cuts heat to 600 Ukrainian apartment buildings
In other news: Telegram fixes zero-day; FCC to investigate "surveillance pricing;" Google will not deprecate third-party cookies after all.

This newsletter is brought to you by Socket, a developer-first security platform that prevents vulnerable and malicious open-source dependencies from infiltrating software supply chains. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

In January this year, Russian hackers used a novel piece of ICS malware to cut the heating and hot water to over 600 apartment buildings in the city of Lviv, Ukraine.
The incident is believed to have impacted apartment blocks in Lviv's Sykhiv residential area. More than 100,000 people are believed to have been left without heating for almost two days as one of the city's heating providers, Lvivteploenergo, restored service.
The attack used a malware strain named FrostyGoop, according to a report released by industrial security firm Dragos this week.
Dragos says it learned of the attack from the Ukrainian Security Service (SBU) in April and was able to track down a sample used in the attack.
While there's no concrete evidence, the security firm believes the hackers broke into Lvivteploenergo's network by exploiting vulnerabilities in its MikroTik routers.
Dragos says the provider's network was not segmented, and the hackers easily pivoted to compromise Lvivteploenergo's internal network.
The attackers compromised a Windows system and deployed FrostyGoop. The malware then sent commands via the internal Ethernet network to ENCO controllers, which the provider was using to manage boilers and heating pumps.
The malicious ENCO commands contained instructions for the MODBUS protocol, which the controllers were using to interface with the heating pumps. Dragos says the MODBUS commands caused "inaccuratemeasurements and system malfunctions," bringing some of Lvivteploenergo's operations to a halt.
Dragos says the incident is of note because FrostyGoop is the first ICS malware strain that was centered around abusing MODBUS, one of the most popular industrial control protocols used in the wild.
The security firm did not link the incident to any specific Russian group, but this looks like the work of Sandworm, a Russian military cyber unit that has been terrorizing the Ukrainian power grid for a decade.
In June, the International Criminal Court announced it began an investigation into Russian cyberattacks on civilian infrastructure as possible war crimes.
The ICC did not share any details about what attacks, but this one is the most clear-cut example of such a crime—by leaving non-combatant civilians without heat during January winter subzero temperatures.
Breaches, hacks, and security incidents
KnowBe4 DPRK incident: Security firm KnowBe4 says that a recently hired engineer was a fake IT worker from North Korea. The company says it detected the attack after a Mac workstation the company sent the worker was immediately infected with North Korean malware. KnowBe4 says the worker's address turned out to be an "IT mule laptop farm" where the worker was VPNing from North Korea. The company says it's now working with the FBI and Mandiant to investigate the incident. The FBI previously warned on multiple occasions that North Korean programmers are applying to US IT jobs as a way to generate revenue for the regime and facilitate hacks and thefts.
LA court ransomware attack: One of the largest courts in the US has been the victim of a ransomware attack. The Superior Court of Los Angeles County has been closed since last Friday after internal servers and its case management system went down. The incident took place on Friday, on the day of the CrowdStrike global IT outage. The court says it detected the incident right away and was able to prevent most of the damage by shutting down systems.
Suffolk County ransomware attack: Officials from Suffolk County in New York say recovery costs from a ransomware attack are expected to go over the $25 million mark. The county fell victim to a ransomware attack in September 2022. The AlphV group took credit for the attack and eventually leaked more than 400 GB of data, including the personal details of 1.5 million residents. Officials said AlphV breached their network using the Log4Shell vulnerability and spent eight months inside before encrypting its systems. The county's former IT director says the figure is inflated and that the county had already paid over $5 million for a forensic investigation and the restoration of its IT services. [Additional coverage in Newsday/ Older coverage by The Record]
ETHTrustFund rug-pull: The developer of a cryptocurrency project named ETHTrustFund appears to have taken all deposited funds ($2 million) and shut down the project.
Hamas IDF data trove: A joint report from four Austrian, German, and Israeli news outlets has discovered a data trove compiled by Hamas that holds profiles of Israeli Defence Force soldiers and their families. Investigators believe the data was compiled over the years through leaks and hacks.
Globes cyberattack: Israeli newspaper Globes says it's been the victim of a major cyberattack. The incident took place last week and limited the staff's access to computers. The newspaper described the event as an "economic terror attack by a sophisticated international criminal gang." It's unclear if the incident was a data wiper or ransomware attack.
Red Art Games cyberattack: French gaming studio Red Art Games has suffered a cybersecurity breach. The company says hackers gained access to customer information. Red Art has shut down its public websites to investigate the incident. The studio believes hackers stole customer personal information and has advised users to change their account password once its services are restored. The company is known for games such as Have A Nice Death, Nuclear Blaze, and Promenade.
General tech and privacy
CrowdStrike outage update: CrowdStrike says that "of the approximately 8.5 million Windows devices that were impacted, a significant number are back online and operational." The company says it developed a new recovery technique that will help speed up remediation. CrowdStrike says it's in the process of getting opt-ins from affected customers before rolling it out.
Google refuses to deprecate third-party cookies: Google will NOT deprecate third-party cookies inside its Chrome browser. Safari and Firefox have already blocked third-party cookies by default since 2020. Google has promised to do the same but has postponed the decision several times over the past years as it worked on a replacement. The company says it will continue to develop its Privacy Sandbox API and provide users with the choice between using the two. Third-party cookies have been used over the past decade to track users online and show relevant ads. The Privacy Sandbox API was supposed to replace them, but experts criticized the new tech as giving Google an unfair advantage over other ad companies. Polish privacy researcher Lukasz Olejnik has posted his thoughts on the move here, detailing an interesting theory.
Oracle privacy lawsuit settlement: Oracle has reached a $115 million settlement in a class-action lawsuit over the company's advertising business. The plaintiffs sued Oracle for violating privacy laws by collecting the personal data of hundreds of millions of individuals without their consent. The lawsuit claims Oracle created digital dossiers on each tracked individual and then sold access to the data to online marketers. Oracle shut down its advertising business last month after seeing a severe loss in profits. [Additional coverage in National Technology News]
FCC caps phone rates for prisoners: The FCC has put a cap on phone and video call rates for US incarcerated prisoners after some prices had gotten out of hand, growing enough to put some people in bankruptcy.
FCC-TracPhone settlement: The FCC has reached a $16 million settlement with TracPhone Wireless over the company's insecure API. The FCC sued TracPhone last year after the Verizon-owned carrier leaked sensitive customer information via unprotected APIs. The carrier suffered three security breaches between January 2021 and January 2023. According to the settlement's terms, the carrier must take a series of steps to secure its API, train personnel and contractors on security measures, and submit to annual security assessments.
Government, politics, and policy
FTC to investigate "surveillance pricing": The FTC has started an investigation into eight companies that are offering "surveillance pricing" services. The practice refers to using personal financial records and browser history to set different prices for each buyer in order for companies to overcharge customers and maximize profits. The FTC will investigate eight companies that provide such services for retailers. The biggest names include Accenture, Mastercard, and JPMorgan Chase.
DDoS on legs: 404 Media reports the DHS has acquired a robot dog that can be deployed inside targeted areas and carry out a DDoS attack on nearby IoT and smart devices.
Ofcom to look at telco Global Titles: UK telecom watchdog Ofcom has launched a public consultation on the use of Global Titles, the addresses used to interconnect mobile networks. For years, surveillance vendors have used legally or illicitly acquired Global Titles to secretly track the locations of smartphones and people around the globe. As a way to combat this practice, Ofcom is considering banning telecom operators from leasing Global Titles on UK phone networks.
Dutch MIVD notification lapses: The Dutch government says that its military intelligence agency (MIVD) has failed to honor legal obligations to notify individuals who inadvertently had their communications intercepted during its operations.
Russia to punish phone use on the frontlines: The Russian government is working on a law to prohibit and punish the use of smartphones by soldiers on the frontline. Officials say smartphone location data can be used to track troop movements and their location on the battlefield. The new law comes after a report that Russia itself has used smartphone location data to go after Ukrainian soldiers over the past few months. [Additional coverage in CNN]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Feross Aboukhadijeh, CEO and Founder of Socket, about how open-source repositories are riddled with horrible software. Feross explains why it makes a difference if a package is vulnerable, malicious, or just unwanted and how current transparency mechanisms such as CVEs and the NVD just aren't suitable for the challenge of open-source repositories.

Cybercrime and threat intel
Pentagon hacker case dropped: A Kuwaiti court has dropped a case against an individual accused of hacking the Pentagon. The suspect is a 28-year-old man who was accused of defacing and leaking data from 200 American websites. The court argued the crimes were committed between 2010 and 2012, and had passed the country's statute of limitations. According to DataBreaches.net, the suspect was detained in London and extradited to Kuwait last year. [Additional coverage in Ashark Al Awsat/ h/t DataBreaches.net]
DigitalStress infiltration: The UK NCA has infiltrated and disrupted a DDoS-for-hire platform named DigitalStress. Officials say they covertly accessed the platform's communications channels where customers were discussing launching DDoS attacks. The Police Service of Northern Ireland has also detained a suspect linked to the service earlier this month.

Dutch malware coder sentenced: A Dutch court has sentenced a 26-year-old man from Assen to three years in prison on cybercrime-related charges. Officials say the man developed a multi-functional tool that could send phishing campaigns and then steal funds from compromised accounts. According to court documents, Dutch police used an IMSI catcher to identify and arrest the suspect. They linked traffic from his iPhone to the tool's management backend. They also linked his movements to locations where he picked up packages bought with stolen funds.
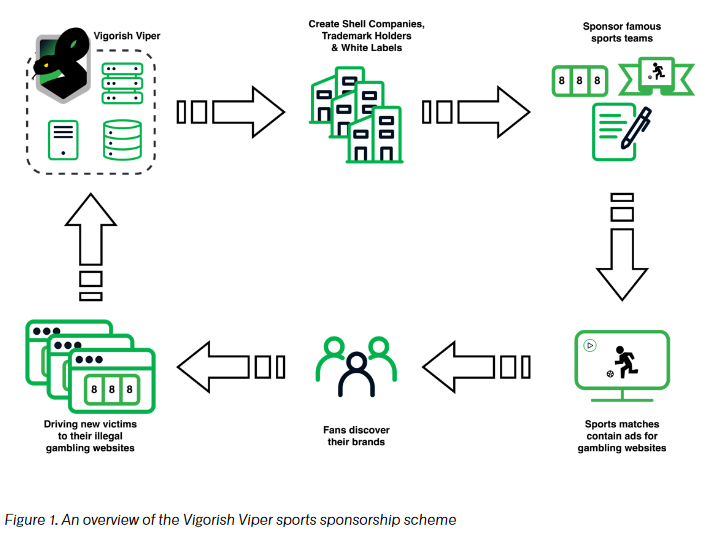
Vigorish Viper: Infoblox claims that a threat actor named Vigorish Viper is behind a massive server network that drives traffic to illegal Chinese gambling sites. The security firm says the threat actor appears to be connected to Yabo, a notorious Chinese cybercrime syndicate linked to money laundering, human trafficking, and scam call centers.
SmartScreen bypass abuse: Fortinet looks at campaigns that leverage a Windows SmartScreen bypass (CVE-2024-21412) to deliver infostealers such as Meduza, Water Hydra, and Lumma Stealer.
7777-Botnet linked to BEC gang: Sekoia researchers have published an analysis of 7777, or Quad7, a botnet that has been used since last year to conduct slow-paced brute-forcing attacks against Microsoft Azure infrastructure. Sekoia says that despite online rumors, it didn't find any evidence to link the botnet to an APT group. Instead, the company believes the botnet is linked to BEC activity.
Fake-DMCA-takedowns-as-a-service: Qurium researchers have published a profile on an Indian company that provides a service that files fraudulent copyright claims on demand to remove legitimate information from the internet. Its services have been used to remove legitimate journalistic work that exposed corruption and crime.
Malware technical reports
Daolpu: CrowdStrike warns that threat actors are using malicious versions of its driver crash recovery manual to distribute a new infostealer named Daolpu. Initially spotted by Zscaler.
RA World: PAN looks at RA World, a rebranded version of last year's RA Group RaaS platform. Trend Micro and Cisco Talos also have reports on the group.
Sponsor Section
Come meet the Socket team at BlackHat and DEF CON! We're sponsoring some fun networking events, and we would love to see you there.

APTs, cyber-espionage, and info-ops
Daggerfly: Broadcom's Symantec has discovered new evidence to suggest that Chinese APT group Daggerfly (Evasive Panda) is using a shared framework to create Windows, Linux, macOS, and Android threats.
UAC-0063 (APT28): Russian cyber-espionage group APT28 (UAC-0063) is behind recent attacks exploiting a vulnerability in Rejetto file-sharing servers. Ukraine CERT says the group used the vulnerability to break into Rejetto servers across Ukraine in June this year. The attacks started a month after the vulnerability was patched in May. South Korean security firm AhnLab spotted the attacks in July but did not link them to Russian hackers. CISA added the Rejetto vulnerability (CVE-2024-23692) to the KEV database shortly after. According to the researcher who initially found the bug, there are more than 2.3 million Rejetto servers connected to the internet.
Vulnerabilities, security research, and bug bounty
JNDI RCE: Source Incite researchers have published details about a remote code execution technique that abuses the Java Naming and Directory Interface (JNDI) API.
BIND security updates: The BIND DNS resolver has released security updates to patch four vulnerabilities [1, 2, 3, 4].
Telegram zero-day: Telegram has fixed a zero-day vulnerability in its Android mobile application. The zero-day was advertised and later sold through an underground hacking forum. It allowed threat actors to share malicious payloads disguised as video files. Security firm ESET says it discovered exploits in the wild that were used to trick users into installing malicious video players. Telegram fixed the vulnerability via a patch on July 11.
Infosec industry
Reuters cyber reporter job: Reuters is hiring a new cybersecurity reporter in the US.
Wiz leaves Google deal: Israeli cybersecurity startup Wiz is said to have walked away from a Google acquisition deal valued at around $23 billion. According to CNBC, Wiz cited antitrust and investor concerns as reasons for abandoning the deal. The cloud security firm has allegedly already told employees it plans to seek an IPO instead. If it had gone through, the Wiz deal would have been Google's largest-ever acquisition.
New tool—Altitude: Alphabet's Jigsaw division has released Altitude, an open-source content moderation tool to help online platforms protect their communities from terrorist and violent extremist content.
New tool—CODASM: Security firm NVISO has open-sourced CODASM, a tool to "to encode arbitrary data into pseudo ASM instructions and compile them into the .text section of binaries."
New tool—API Threat Landscape: API security firm Escape has released a free database of API-related security incidents.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss whether the rise of cloud computing has been a boon or a curse for cyber espionage agencies.
In this podcast, Tom Uren and Adam Boileau talk about how countries are using cyber security reports and advisories to win friends and influence people; why having gaping holes in US federal government security is situation normal; and efforts to make up for the disappearance of Twitter's trust and safety team.
This Soap Box edition of the show is with Mike Wiacek, the CEO and Founder of Stairwell. Stairwell is a platform that creates something similar to an NDR, but for file analysis instead of network traffic. The idea is you get a copy of every unique file in your environment to the Stairwell platform, via a file forwarding agent. You get an inventory that lists where these files exist in your environment, at what times, and from there, you can start doing analysis.




