Risky Biz News: New router malware intercepts traffic to steal credentials
In other news: Dropbox discloses data breach; US government drops degree requirements for cyber jobs; Kaseya hacker sentenced to 13 years in prison.

In other news: Dropbox discloses data breach; US government drops degree requirements for cyber jobs; Kaseya hacker sentenced to 13 years in prison.
This newsletter is brought to you by Socket, a developer-first security platform that prevents vulnerable and malicious open-source dependencies from infiltrating software supply chains. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Reports on interesting and puzzling malware strains are quite rare in infosecland, where most of the time, you're bound to read about cryptominers, Mirai clones, and the same 5-6 malware loaders and infostealers over and over again.
This week, Lumen's Black Lotus Labs team published a report on a new malware strain named Cuttlefish that they found on both SOHO and enterprise-grade routers.
The interesting part about the report was that Cuttlefish appears to have been designed to work as a traffic interception system on the infected devices.
It scans network traffic and looks for text markers in URLs that reference passwords, keys, tokens, and other authentication-related items.
According to a list pulled by Black Lotus researchers from the malware's source code, Cuttlefish actively scans for 126 markers, with many referencing cloud services like Ali Cloud, AWS, Digital Ocean, CloudFlare, BitBucket, Ansible, and others.
Seeking authentication details for cloud-based resources could allow the attacker to move laterally across networks or even perform supply chain attacks from that infrastructure.
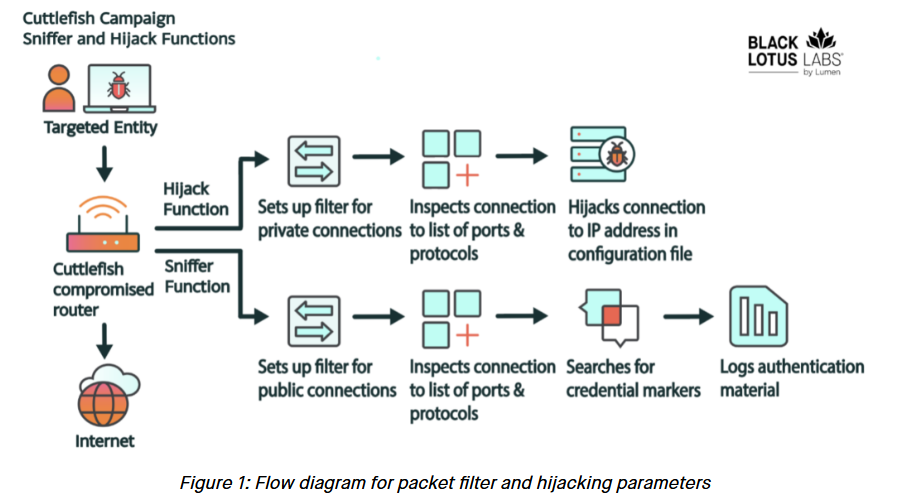
The filters are also active for tens of ports and not just web traffic.
Once the malware identifies and extracts authentication material from a connection, it starts up a VPN tunnel and sends the data to a remote server.
Additional code also suggests Cuttlefish can be used to execute DNS and HTTP hijacking inside a router's internal network.
While we've seen IoT malware botnets infect corporate networks to steal credentials, they've usually done it by extracting the credentials from local sources, not on the fly from internet traffic.
All evidence suggests this may be a cyber-espionage campaign, although Black Lotus has not yet attributed the malware.
Researchers—and this newsletter's author—believe this is a very advanced piece of malware. Black Lotus described its DNS and HTTP hijacking feature as "the next generation in malware capabilities."
"[T]he ability to eavesdrop and perform DNS and HTTP hijacking has seldom been observed – the few publicly identified campaigns include ZuoRat, VPNFilter, Attor, and Plead. However, this is the first instance where we have seen rules specifically designed to seek out private IP connections to hijack."
The victimology also points to a targeted attack, and most likely an APT operation.
"The infection pattern was unique as 99% of infections occurred within Turkey, mainly stemming from two telecommunications providers. These two telecom firms accounted for roughly 93% percent of infections – 600 unique IP addresses. The handful of non-Turkish victims included IP addresses of likely clients associated with global satellite phone providers, and a potential US-based data center."
Infections with the new Cuttlefish malware have been seen as far back as July of last year, so this campaign has managed to go under the radar for several months.
Black Lotus Labs says it wasn't able to determine how the routers were initially compromised and infected with the malware.
Breaches, hacks, and security incidents
Dropbox breach: Dropbox says that hackers accessed its IT infrastructure and stole the data of some of its users. The incident impacted only Dropbox Sign, a Dropbox service for sharing and digitally signing documents. The threat actors stole usernames, email addresses, and even hashed passwords. API keys and OAuth tokens were also exposed for some users. Dropbox says it discovered the breach last week and found no evidence that hackers accessed customer accounts and data.
Marriott lied about encryption: Marriott has confirmed that it lied about its data encryption practices in the aftermath of its 2018 data breach. In a court hearing last month, the company said its data was not encrypted but only hashed with the SHA-1 algorithm. The company previously stated that its data was encrypted with the AES-128 algorithm. According to a report from CSO Online, the company silently back-edited its data breach disclosure page.
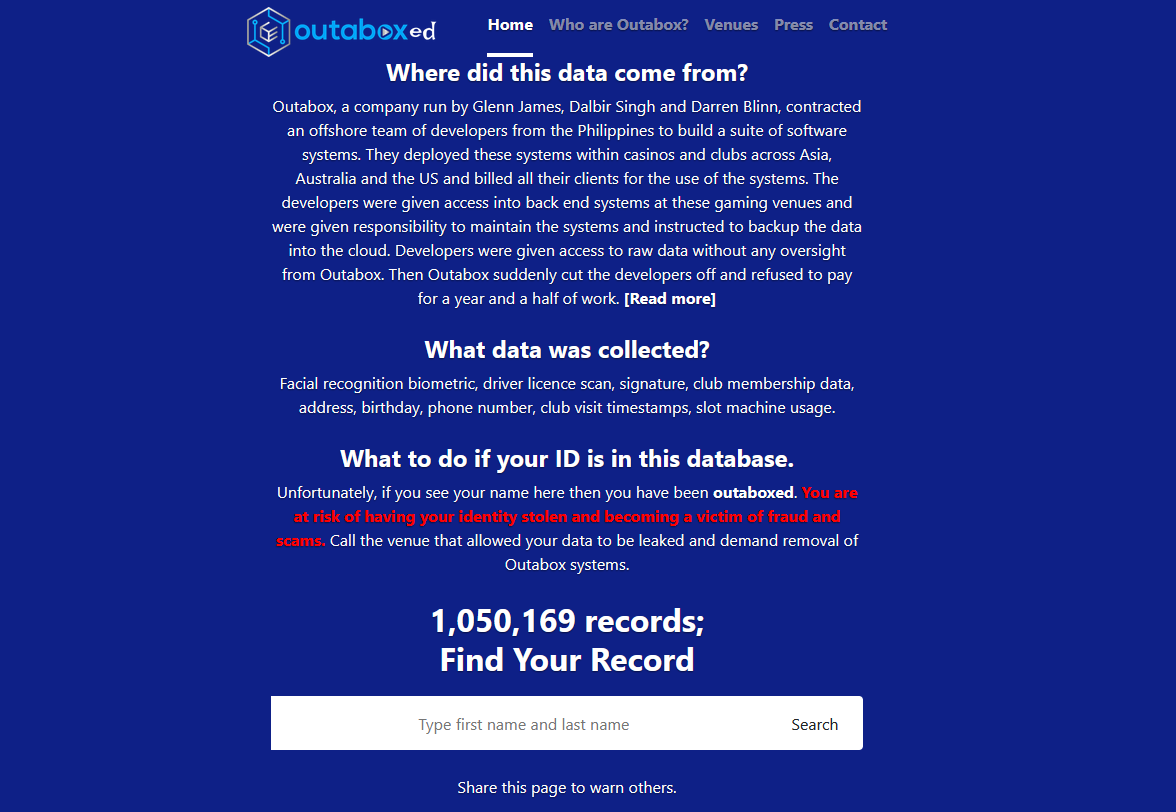
Outabox breach & arrest: Australian police arrested a Sydney man over an alleged data breach of IT provider Outabox. Officials believe the man created a website that allowed anyone to search through Outabox data. The website claimed to contain details on more than 1 million users, such as personal details, driver's license scans, signatures, and facial recognition data. Police have charged the 46-year-old suspect with blackmail. [Additional coverage in The Guardian]
La Nacion cyberattack: Argentina's largest newspaper, La Nacion, was the victim of a cyberattack. [Additional coverage in Clarin]
Qantas leak: Australian airline Qantas has fixed an issue in its mobile app that customers the details of other passengers. [Additional coverage in ABC]
Pike Finance crypto-heist: A threat actor has stolen $1.9 million worth of crypto-assets from DeFi platform Pike Finance. The hack took place across two phases. The attacker stole $300,000 on April 26 and then another $1.6 million on April 30. Pike said both attacks exploited the same vulnerability in one of the platform's smart contracts. The company is now offering a bounty of 20% for the return of the stolen funds. [Additional coverage in CoinTelegraph]
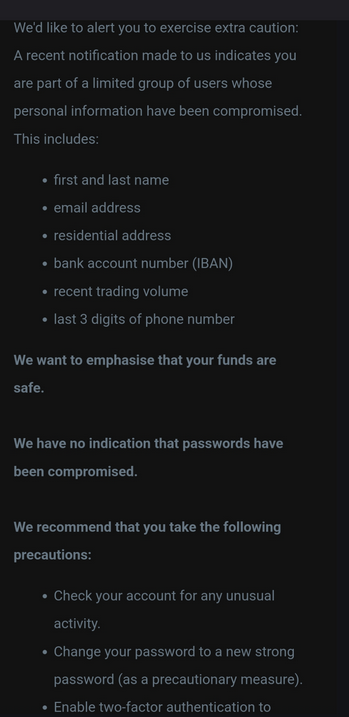
Bitvavo breach: Dutch cryptocurrency exchange Bitvavo is notifying users of a security breach.
General tech and privacy
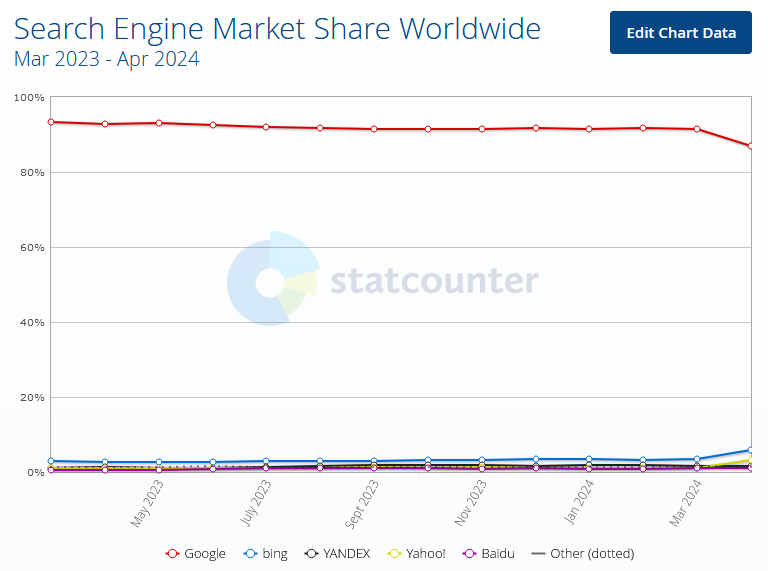
Google Search market share: Google has lost search market share for the first time in God-knows how many years. The company hit a low 86% after hovering around 91% for years. The drop is worse in the US, where market share hit 77%.
Google passkey usage: Google says that more than 400 million user accounts have used or are currently using a passkey.
OpenSSL moves to GitHub: The OpenSSL project has moved its development and download mirrors (exclusively) to GitHub.
Thunderbird 20-year bug: Mozilla has finally fixed a 20-year-old bug in its Thunderbird email client that only showed the "sender name" in emails. Now, the sender's email address will also show up.
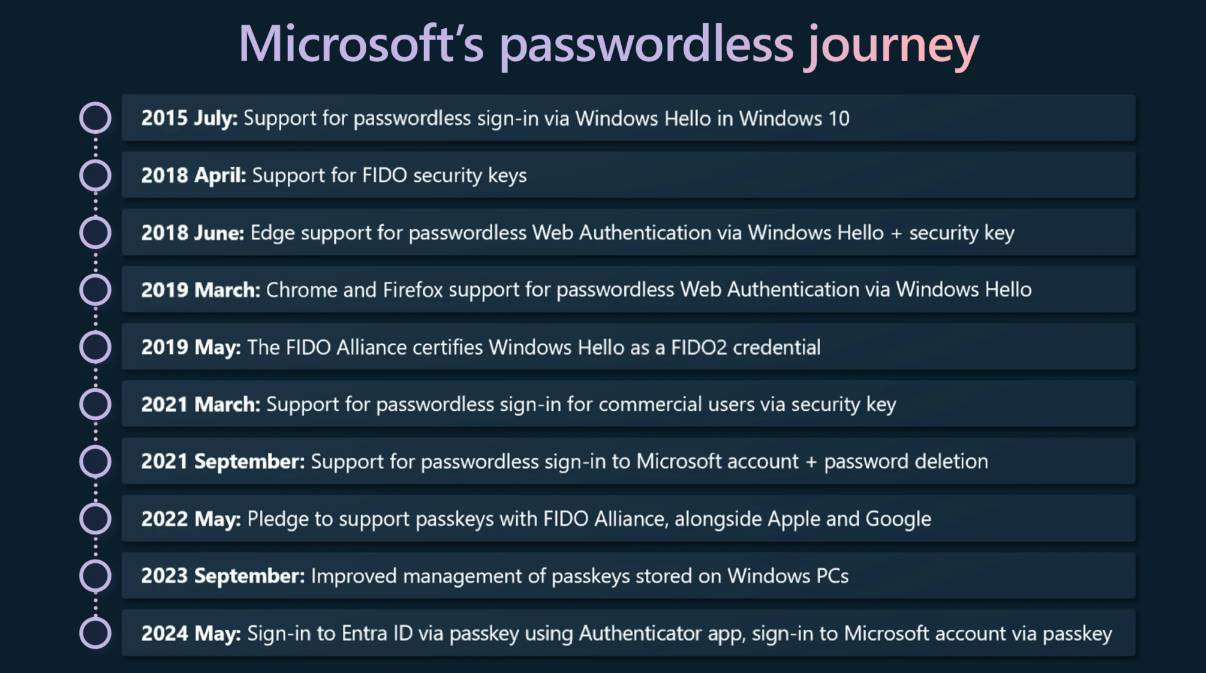
Microsoft adds passkey support: Microsoft is rolling out passkey support for all the company's consumer accounts. All users will be able to generate a passkey and use it to log into their operating systems and Microsoft online services. The company expanded passkey support after first launching the feature for Windows 11 users last year. Passkeys have been described as a replacement for passwords. Microsoft made the announcement on World Password Day.
Government, politics, and policy
FBI FISA searches drop: The FBI has cut down by almost half on its searches of the FISA surveillance program database. In its annual transparency report, the Office of the Director of National Intelligence says the FBI conducted 57,094 searches last year, compared to 119,383 the previous year. The FBI attributed the drop in the number of searches to new internal procedures. Congress delayed Section 702 renewal for months, citing the FBI's broad searches of the FISA database. [Additional coverage in The Record]
US drops degree requirement for cyber jobs: The White House has overhauled the hiring process for government cyber roles. Officials have encouraged federal agencies to hire IT staff based on their skills and removed requirements for years of experience and degrees. National Cyber Director Harry Coker Jr. hopes that relaxing hiring requirements will help the government hire experts on crucial tech roles that are still unfilled because of stringent hiring requirements. The government currently has nearly 100,000 open tech jobs. The changes will also apply to contractor positions. [Additional coverage in the FederalNewsNetwork]
CNMF warning: Officials from the US Cyber National Mission Force, part of Cyber Command, fear that the recent Volt Typhoon operations designed to infiltrate US critical infrastructure in preparation for destructive attacks might inspire other threat actors to do the same. [Additional coverage in C4ISRNET]
CISA SbD alert: CISA has released another one of its Secure-by-Design alerts—this one targeting directory traversal vulnerabilities.
Texas surveillance: Two US counties on the Southern Mexico border are using a surveillance product named TraffiCatch that can collect and track wireless and Bluetooth signals emitted by modern devices. Contracting records suggest the technology is used to collect in-vehicle wireless signals, merge intelligence with license plate records, and track vehicle movements. [Additional coverage in NOTUS]
Ukraine dismisses cyber chief: Ukrainian President Volodymyr Zelensky has formally dismissed Illia Vitiuk, the former head of the SBU's cyber division. The SBU suspended Vitiuk and reassigned him to a unit on the front last month while they conducted an anti-corruption investigation. Vitiuk was suspended after a news outlet discovered that he and his wife bought expensive real estate despite not having the financial means to do so. Reporters also claimed they were harassed by SBU staff after publishing their article. [Additional coverage in The Record]
Spyware in Indonesia: An Amnesty International investigation found that the Indonesian government bought and is using surveillance tools from commercial spyware vendors. The organization found tools from NSO Group, Candiru, FinFisher, Wintego, and Intellexa. Customers included the Indonesian National Police, the National Cyber and Crypto Agency, and the State Intelligence Agency.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to CEO and founder of Socket, Feross Aboukhadijeh about the open source software and supply chain security. Feross says the software ecosystem has evolved in ways that make it more vulnerable to trust-based attacks (such as seen in XZ Utils) and discusses what can be done to defend against this type of supply chain subversion.

Cybercrime and threat intel
Kaseya hacker sentenced: The US has sentenced a Ukrainian national to 13 years and seven months in prison for his role in the Kaseya ransomware incident. Yaroslav Vasinskyi was a member of the REvil ransomware group, where he operated under the name of Rabotnik. In July 2021, Vasinskyi exploited a vulnerability in the Kaseya VSA software to breach more than 50 MSPs and then installed ransomware on their customer networks. Officials say Vasinskyi was responsible for more than 2,500 ransomware attacks across the globe and tried to extort over $700 million from victims. Vasinskyi was arrested four months later while traveling to Poland. He received the biggest sentence for a ransomware attack to date. He was also ordered to pay over $16 million in restitution.
Cybersecurity consultant detained for extortion: The FBI has arrested a cybersecurity consultant for allegedly trying to extort an IT company for $1.5 million. Officials claim that Vincent Cannady from El Dorado Springs, Missouri, threatened to publish sensitive and proprietary files unless the company paid him the demanded money. Cannady allegedly took the files while contracted by the victim company a year before. Prosecutors say the suspect allegedly tried to disguise the extortion as "discrimination and emotional distress claims."
BEC scammer convicted: A jury has convicted a Nigerian national for his role in a BEC gang that stole $6.3 million.
DDoS on Sweden: Netscout says it's seeing a steady wave of DDoS attacks targeting Sweden since the country's NATO membership.
Okta credential-stuffing attack: Permiso has published some IOCs on the waves of credential-stuffing attacks that targeted Okta last month.
OT cyber threats: CISA and nine other government agencies have published a joint advisory on the threats posed to OT infrastructure by pro-Kremlin faketivist groups.
Microsoft Graph API abuse: Broadcom's Symantec team has published an analysis of how various threat actors are now abusing the Microsoft Graph API to attack Azure-hosted infrastructure. These types of attacks were on an upward spiral, and are likely to increase in popularity.
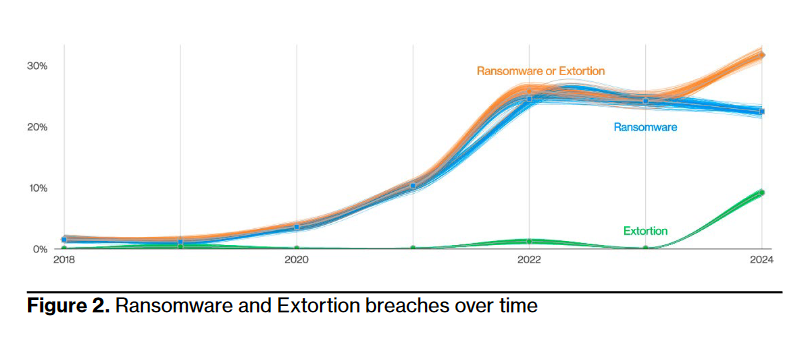
Threat/trend reports: Chainguard, the Cyber Threat Alliance, Lab539, New Relic, and Verizon have recently published reports covering infosec industry threats and trends. Of these, the Verizon DBIR report for 2024 is the most interesting, being one of the seminal reports of the infosec industry. Some of the highlights below:
- Vulnerability exploitation surged by nearly 3X (180%) last year.
- Ransomware and the meteoric rise of extortion techniques accounted for a third (32%) of all breaches.
- More than two-thirds (68%) of breaches involve a non-malicious human element.
- 30,458 security incidents and 10,626 confirmed breaches were analyzed in 2023—a two-fold increase over 2022.
Malware technical reports
TargetCompany: South Korean security firm has linked the TargetCompany threat actor to old attacks against MS-SQL servers that deployed the Tor2Mine coinminer and the BlueSky ransomware. The group is currently known for deploying the Mallox ransomware on unpatched and unsecured MS-SQL databases.
INC Ransomware: Huntress has published a report describing a recent intrusion that abused LOLBins to deploy the INC ransomware.
Remcos RAT: Elastic's security team has published part two of its analysis of the REMCOS RAT. Part one is here, while Elastic appears to have (accidentally) pre-published part three as well.
Goldoon botnet: Fortinet has spotted a new IoT botnet. Named Goldoon, this one is currently exploiting a 2015 vulnerability in D-Link routers. Attacks will most likely to other devices as the botnet matures.
Sponsor Section
This podcast episode is brought to you by Socket Security. Socket makes a security platform for developers that protects their software from vulnerable and malicious open-source dependencies. Find them at Socket.dev.
The `xz` package backdoor is just the tip of the iceberg.
— Feross (@feross) March 30, 2024
There's a CONSTANT low-level stream of malware and spyware being uploaded to npm, PyPI, and Go registries.
I want to share a few examples from the 20,000+ malicious packages we detected so far: pic.twitter.com/f0FqCeUPqC
APTs, cyber-espionage, and info-ops
DPRK alert: The NSA, the FBI [PDF], and the State Department have urged US organizations to secure email servers with correct DMARC policies to prevent abuse from North Korean hackers. The three agencies say North Korean APTs have exploited misconfigured DMARC policies to spoof official domains as part of their social engineering operations. The group that uses this tactic is Kimsuky, also known as APT43 and Velvet Chollima.
APT42: Google's Mandiant division has published a report on Iranian APT group APT42 (Mint Sandstorm, Charming Kitten, TA453), its main three clusters, recent attacks, and its recent malware arsenal.
ArcaneDoor: Censys has published its own view of the ArcaneDoor campaign that targeted Cisco ASA devices with recent zero-days. While Cisco Talos never attributed the attacks, Censys says it found links to a Chinese threat actor.
Sandworm's Acid wipers: Trellix researchers have published a technical deep dive of AcidRain and AcidPour, two wipers used by the Sandworm APT in the attacks against Viasat and various other Ukrainian targets.
Sandworm's Kapeka: On the same note, LogPoint has published a report on Kapeka, Sandworm's new backdoor used in recent spear-phishing operations across Europe.
PwnStorm's MooBot survives takedown attempt: Russian state-sponsored hackers have continued to abuse the Moobot botnet even after US authorities took down a part of the botnet in February. Security firm Trend Micro says the takedown only affected a part of the Moobot botnet comprised of Ubiquiti EdgeRouters. The group has continued to abuse a smaller Moobot botnet of infected Raspberry Pi devices and VPS data center servers. The botnet is currently estimated to be around 350 infected devices. Trend Micro says some of these systems were used during spear-phishing operations in Ukraine.
VoE disinfo update: The pro-Russian government of Slovakia has granted temporary protection to a Ukrainian and Israeli citizen sought by Czechia for his role in Voice of Europe, a pro-Kremlin propaganda network that operated from Prague. [Additional coverage in Reuters]
Vulnerabilities, security research, and bug bounty
Browser cookie theft: Google has published a blog post detailing how security firms can detect when a threat actor steals authentication cookies from locally installed browsers. The technique is pretty universal and relies on Windows Event Logs.
Chrome bug: ZDI has published an analysis of CVE-2024-2887, a Chrome bug that helped security researcher Manfred Paul win this year's Pwn2Own hacking competition.
Cisco IP phone vulns: Cisco has patched three vulnerabilities in its IP phones that allowed for unauth remote attacks.
Aruba security updates: HPE's Aruba Networks has pushed patches for 10 vulnerabilities across several products. Four of them are critical vulnerabilities that can be exploited without authentication and have a CVSSv3 score of 9.8/10. [h/t Screaming Goat]
Jenkins security updates: The Jenkins project has announced security updates for four of its most popular plugins.
GitLab abuse: CISA has added a new entry to KEV, its database of actively exploited bugs. The vulnerability is CVE-2023-7028, a bug that can allow threat actors to abuse the password reset feature and hijack admin accounts.
Xiaomi vulnerabilities: Security firm Oversecured has found 20 vulnerabilities impacting several Xiaomi apps that can allow root access to the device, theft of user data, and more. Xiaomi fixed all issues within days after receiving the report.
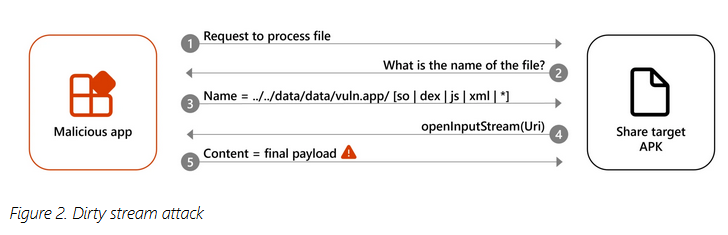
Dirty Stream vulnerability: Microsoft has discovered a new attack that can allow malicious Android apps to overwrite files in another app's folders. The attack is named Dirty Stream and can allow malicious apps to install malware inside legitimate apps. Microsoft says that many popular Android apps can be hijacked via a Dirty Stream attack. The vulnerable apps have more than 4 billion combined downloads.
Infosec industry
GoTo spins off Lastpass: GoTo has spun Lastpass into its own company six years after acquiring it (GoTo was known as LogMeIn back then).
Acquisition news: Threat intelligence platform Intel471 has acquired threat-hunting startup Cyborg Security.
New tool—Bogus CVEs: Security researcher Vin01 has published a list of bogus or controversial CVEs—currently, at 27 entries.
New tool—QCSuper: P1 Security has open-sourced QCSuper, a tool to capture raw 2G/3G/4G (and for certain models 5G) radio frames from Qualcomm-based devices.
Tool update—PolarProxy: Netresec's PolarProxy tool has now reached a stable v1.0 version.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the life cycle of zero-days, dissect the conventional wisdom, and talk about how zero-days are never truly "burnt."




