Risky Biz News: New EvilCorp sanctions and LockBit arrests drop on Counter Ransomware Initiative summit week
In other news: NIST backlog still there; Cambodia arrests journalist who exposed scam compounds; FCC fines T-Mobile for neverending data breaches.

This newsletter is brought to you by Zero Networks. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

This week, the Counter Ransomware Initiative is holding its yearly summit in Washington, and the US-led coalition decided to celebrate its fourth anniversary with a crackdown on everybody's "favorite" cybercrime groups—LockBit and EvilCorp.
Announcements included new LockBit arrests and server seizures, and more sanctions on newly uncovered EvilCorp members—including a former FSB Spetsnaz officer who has been quietly protecting the group from local authorities.
New LockBit ransomware arrests, server seizures, indictments
We knew something was up over the weekend when the former LockBit dark web leak site was propped up back online with new countdown timers for several announcements timed for Tuesday.
These turned out to be the arrests of two people linked with a LockBit affiliate in the UK, a LockBit affiliate in France, and an individual in Spain who provided bulletproof hosting services for the LockBit gang.
The latter arrest also allowed authorities to seize new servers linked to old LockBit infrastructure.
The individual arrested in France was detained while visiting the country on vacation—because, apparently, some ransomware operators did not get the memo about not vacationing in NATO countries after spending years ransoming their hospitals, governments, and private corporations.
The UK's National Crime Agency says it detained the two suspects in the UK after analyzing LockBit backend data that was initially seized back in February during their first disruption of the gang. In May, the NCA said it had files and was working to track almost 70 of the group's past affiliates.
On top of that, the UK agency also published a technical post that looked at the LockBit backend source code and could now 100% confirms that the LockBit gang never deleted stolen files from their servers, even after victims paid their ransoms.
New EvilCorp indictment and a whole lot of sanctions
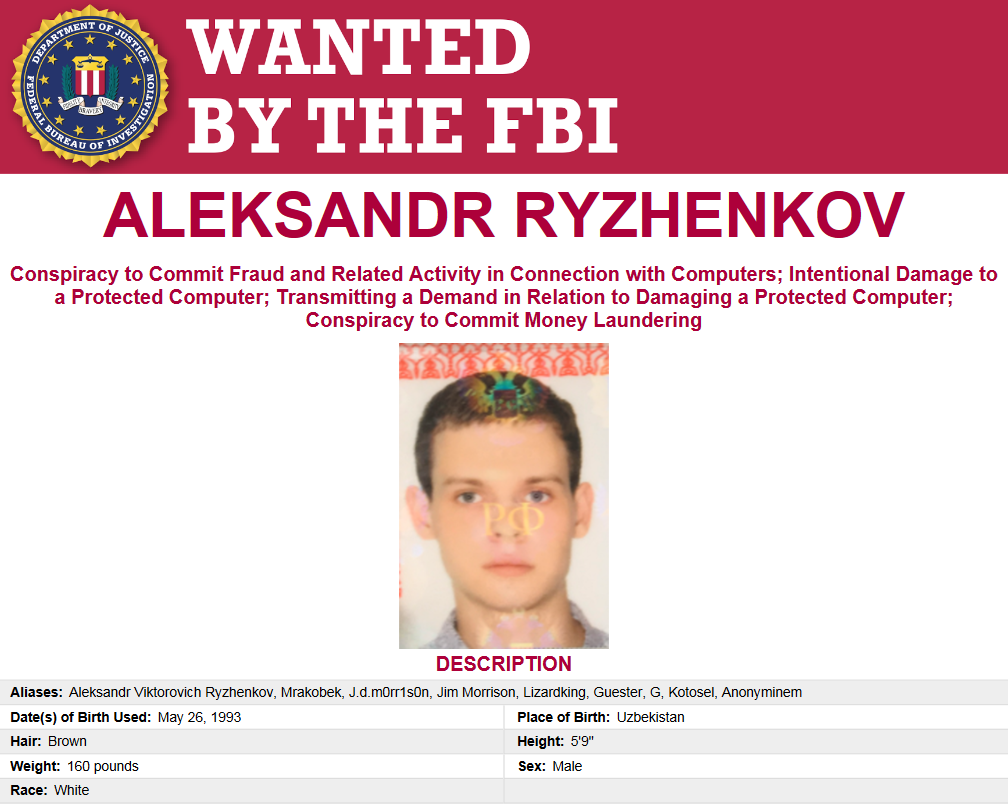
It's the NCA's sleuthing work that also linked another LockBit affiliate known as "Beverley" to a Russian national named Aleksandr Ryzhenkov.
It turned out that Ryzhenkov had a long history in the ransomware world, having previously involved in attacks that deployed the BitPaymer ransomware. He was indicted for some of those attacks by US authorities on Tuesday and made his way onto an FBI Cyber Most Wanted poster.
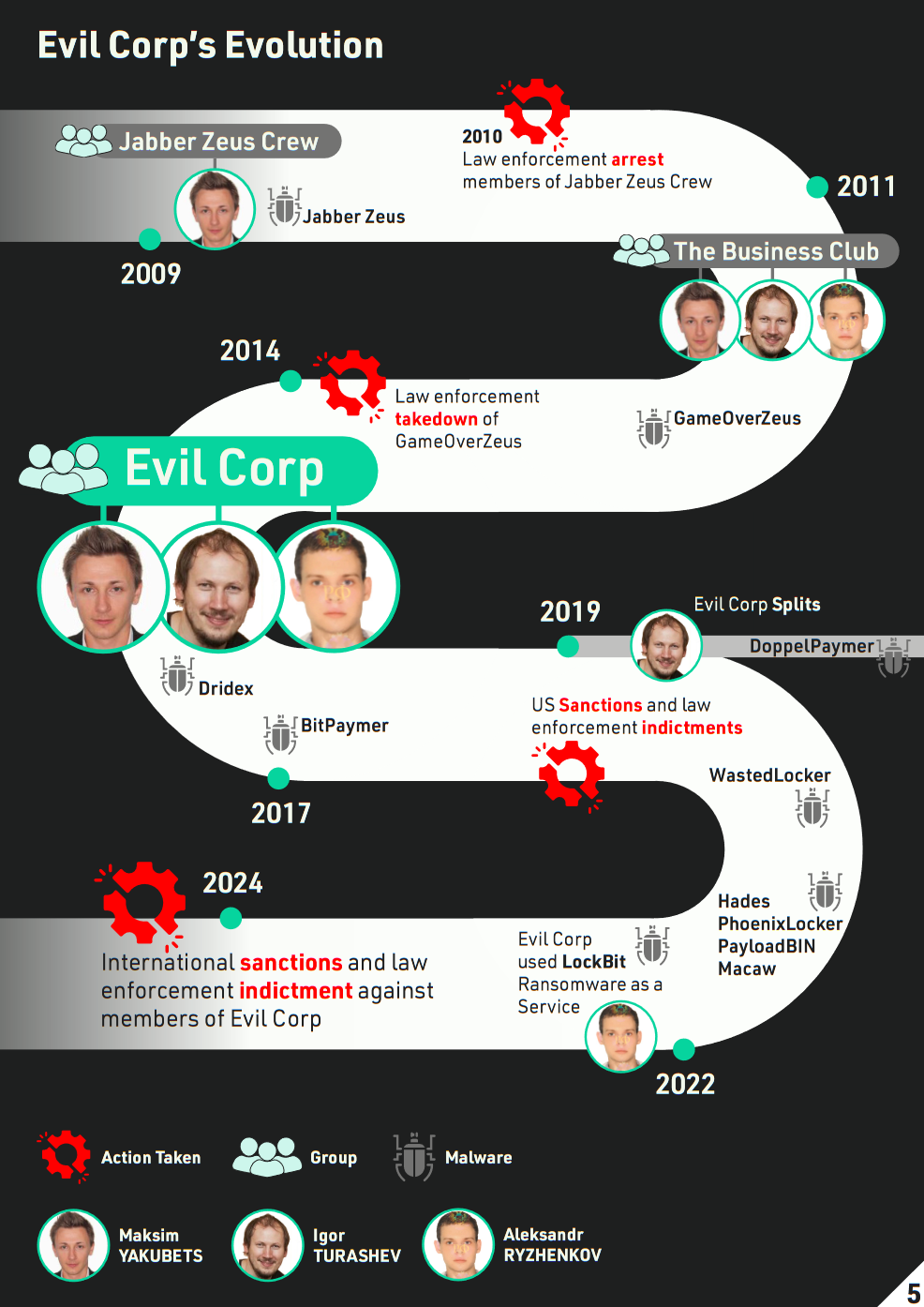
But for those who know their cybercrime history, BitPaymer is not some random Ransomware-as-a-Service platform. It was a privately developed ransomware strain that was used solely by members of EvilCorp, a massive cybercrime cartel that has ties to all sorts of malware operations, such as Dridex, Necurs, Locky, and many more.
When the US first sanctioned EvilCorp back in December 2019, it killed BitPaymer operations since no victim would pay, fearing they'd violate US sanctions. That's what drove many EvilCorp members to become affiliates for other RaaS platforms instead of using their own ransomware strains.
According to US authorities, Ryzhenkov was not only a member of EvilCorp but was the group's second-in-command and one of their main malware developers.
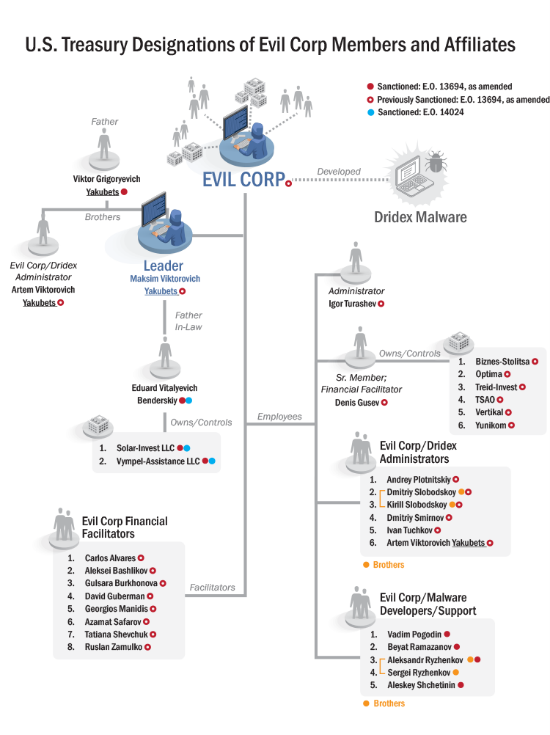
Ryzhenkov was one of the seven new EvilCorp members sanctioned by the US Treasury on Tuesday in a second round of sanctions against the group.
Authorities in the UK have also announced they're mirroring the US EvilCorp sanctions and have sanctioned 16 individuals associated with the gang. Australia is expected to pick up the sanctions as well—although no official press release was public when this newsletter had to go out.
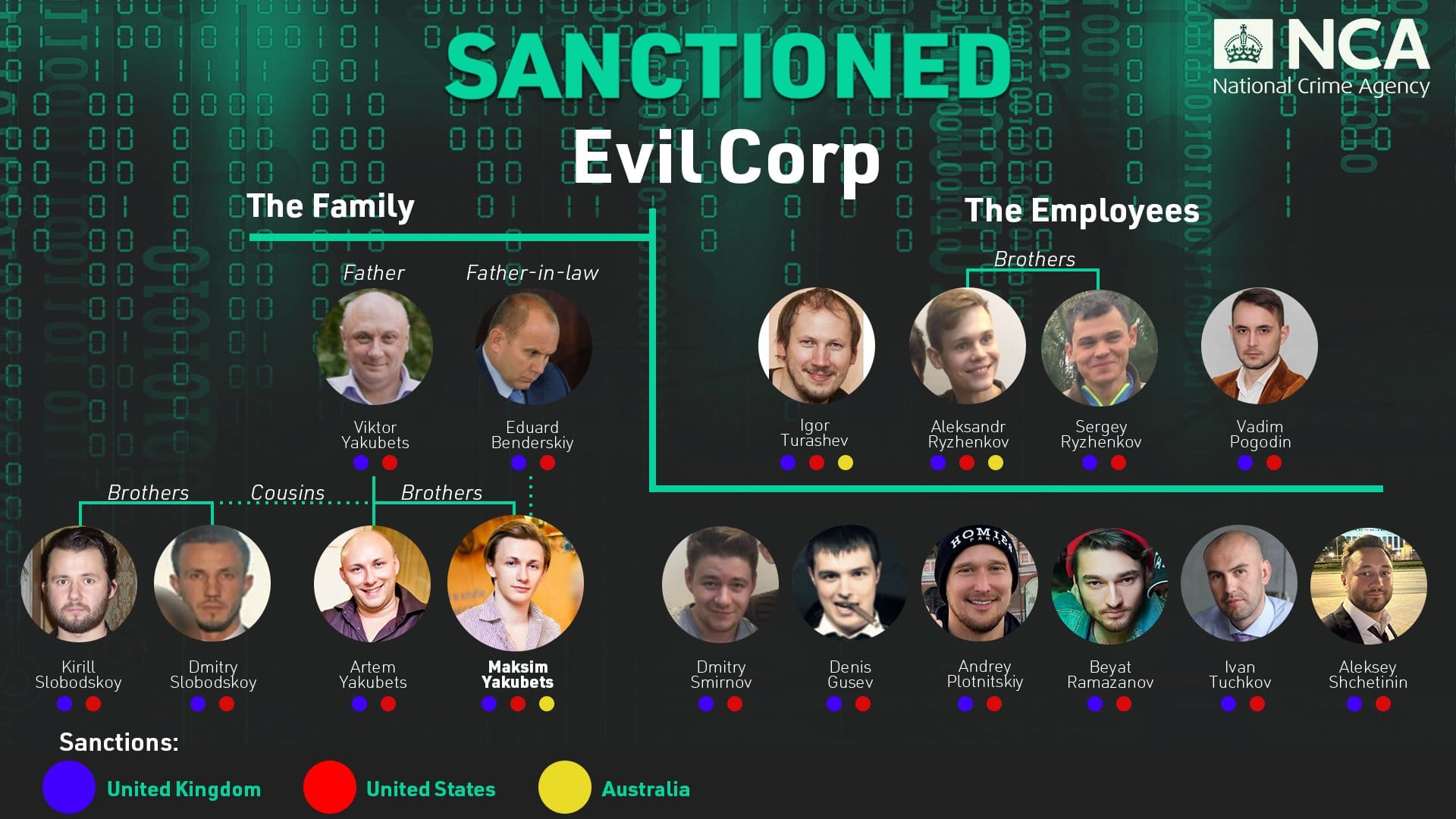
The new sanctions also reveal interesting details about how EvilCorp has operated all these years. The main takeaway is that EvilCorp was an Italian-style mafia organization run by the Yakubets family.
US and UK officials have identified Maksim (son) as the leader, while his father, brother, and two cousins were also involved in the group's daily operations.
A crucial role was played by Eduard Benderskiy, Maksim's father-in-law, and former high-ranking Spetsnaz officer inside Russia's FSB intelligence service.
"Benderskiy leveraged his status and contacts to facilitate Evil Corp's developing relationships with officials of the Russian intelligence services. After the December 2019 sanctions and indictments against Evil Corp and Maksim, Benderskiy used his extensive influence to protect the group."
US officials say Benderskiy played a key role in safeguarding the group from Russia's internal services. UK officials suggest EvilCorp paid for the state's protection by participating in cyber attacks and espionage operations against NATO allies—which is exactly what many threat analysts have been saying behind closed doors for years and is something that Russia's invasion of Ukraine has also helped expose.
Breaches, hacks, and security incidents
Lebanon airport hack: There's some unconfirmed reports that the Israeli military hacked the communications system of the Beirut control tower and warned an Iranian plane not to land there. [Additional coverage in The Times of Israel]
Services Australia breaches explode: The number of account compromises at Services Australia saw a 440% increase over the past year. Officials blame the rise on Australians reusing passwords across multiple online accounts. [Additional coverage in The Guardian]
Rackspace hack: A threat actor has used a zero-day in the ScienceLogic IT operations platform to breach cloud hosting provider Rackspace. The hack took place last week on September 24 and went undisclosed for a week. Rackspace says it disabled its monitoring solution as soon as it discovered the attack and has begun rotating credentials used in the environment. ScienceLogic says it has since deployed a fix. [Additional coverage in The Register]
General tech and privacy
FCC fines T-Mobile: The Federal Communications Commission has reached a $31.5 million settlement with T-Mobile over multiple security breaches that took place between 2021 and 2023. Half of the settlement is a civil fine, while the other half is a mandatory investment T-Mobile must make in its cybersecurity program. The company has also agreed to adopt a zero trust architecture, robust identity and access management, and improve its corporate governance model to include regular cybersecurity and business risk reports.
Verizon outage: Verizon had an outage on Monday, and it had quite an impact on security operations.
Trump threatens Google: Former US President Donald Trump said he'll seek to prosecute Google because—in his toddler view of the world—the company only displays bad news about him. [Additional coverage in Reuters]
Thunderbird Android app: Mozilla has launched the first beta of its Thunderbird Android app.
Windows 11 24H2: Microsoft is rolling out Windows 11 24H2, the latest version of its Windows operating system. The new release comes with support for SHA-3, WiFi 7, Rust in the Windows kernel, and an LSA update to protect against the theft of login secrets and credentials. The new Windows 11 also comes with Personal Data Encryption, a new feature that lets users encrypt known Windows folders such as Documents, Desktop, and Pictures—to safeguard their data against theft.
Defender unsecured WiFi detection: Microsoft has added a new feature to its Defender antivirus that will notify users when they connect to unsecured WiFi networks. This includes public WiFi networks that have no passwords and use weak security encryption. The new feature will encrypt the user's traffic and route it through Microsoft VPN servers. The feature is available for Defender for Android, iOS, and Windows and will soon come to macOS as well.
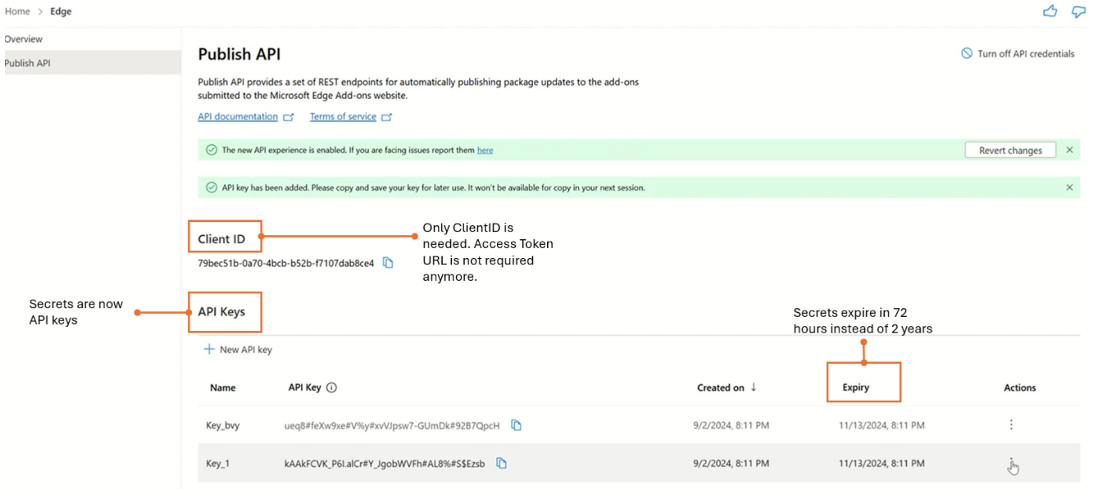
Microsoft overhauls Edge extension dev dashboard: Microsoft is rolling out upgrades to its official Edge extensions store as part of its company-wide security overhaul. The company is rolling out a new API and dashboard for extension developers. The new dashboard will help extension developers manage extensions through API keys that expire every 72 days. Microsoft says the shorter extension API life span will help mitigate the impact of compromised or malicious extensions.
Government, politics, and policy
More ransomware disruptions needed: White House officials say they need to increase the frequency of ransomware disruptions to achieve better results and disrupt ransomware operations permanently. Speaking at the Counter Ransomware Summit this week, US officials said they also plan to make funds available to allies to help fight off ransomware attacks. The Counter Ransomware Initiative was founded two years ago and currently has 68 members. [Additional coverage in CyberScoop]
California car remote access bill: California Governor Gavin Newsom has signed a bill into law that requires carmakers to allow drivers to cut off remote access to their cars. The new disconnect feature is meant to allow victims of domestic abuse to prevent their abusers from accessing their cars to track or sabotage the vehicle. The law also prevents car manufacturers from monetizing the new feature.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Benny Lakunishok, CEO and cofounder of ZeroNetworks, about network microsegmentation, why it is important, how to do it, and what the NSA gets wrong about it.

Cybercrime and threat intel
Smisher detained in Australia: Australian authorities have arrested a Chinese national for an SMS phishing operation that sent millions of text messages to Australian citizens. Jiahui Liu allegedly sent almost 5 million messages pretending to be Centrelink, Medicare, Australia Post, Commonwealth Bank, Transurban, and Linkt. Officials seized over 1,200 SIM cards and a SIM box capable of sending mass text messages. He was denied bail because of his crimes and for living in Australia on an expired visa.
India dismantles cybercrime syndicate: Indian authorities raided call centers across four major Indian cities for their role in an online scam operation. Officials questioned 170 and detained 26 individuals as part of Operation Chakra-III. The suspects allegedly called victims and tricked them into thinking their systems were compromised or their identities stolen. The individuals worked to move a victim's funds into "safe" accounts and then demanded payment for their services in cryptocurrency or gift cards. [Additional coverage in the Times of India]
Cambodia arrests reporter who exposed scam compounds: Cambodian authorities have arrested and imprisoned an independent journalist who exposed local cyber scam compounds. Award-winning independent journalist Mech Dara was intercepted and arrested on Monday while driving to Cambodia's capital Phnom Penh. He was charged with inciting social disorder for a Facebook post last month that criticized a quarry over damage to a local monastery. [Additional coverage in the Associated Press]
Cybercrime suspect indictment: The US has charged a California man for failing to pay taxes on tens of millions allegedly obtained from cybercrimes. [Additional coverage in KrebsOnSecurity]
Data brokers sentenced: A US judge has sentenced two former executives of a US marketing firm to prison for illegally selling the data of millions of Americans. Robert Reger and David Lytle of Epsilon Data Management took data from the company and sold it to fraud groups specializing in mass-mailing schemes. The data contained the names and home addresses of 100 million US households and was used to send scam letters to Americans over a period of 10 years. The Justice Department says the two execs often worked with scam groups to compile lists of consumers more likely to respond to the scams, such as elderly and financially vulnerable groups. Reger was sentenced to 120 months in prison, while Lytle received 48 months.
JPCERT detecting ransomware resource: Japan's CERT team has published a guide on how to detect human-operated ransomware intrusions automatically through Windows event logs.
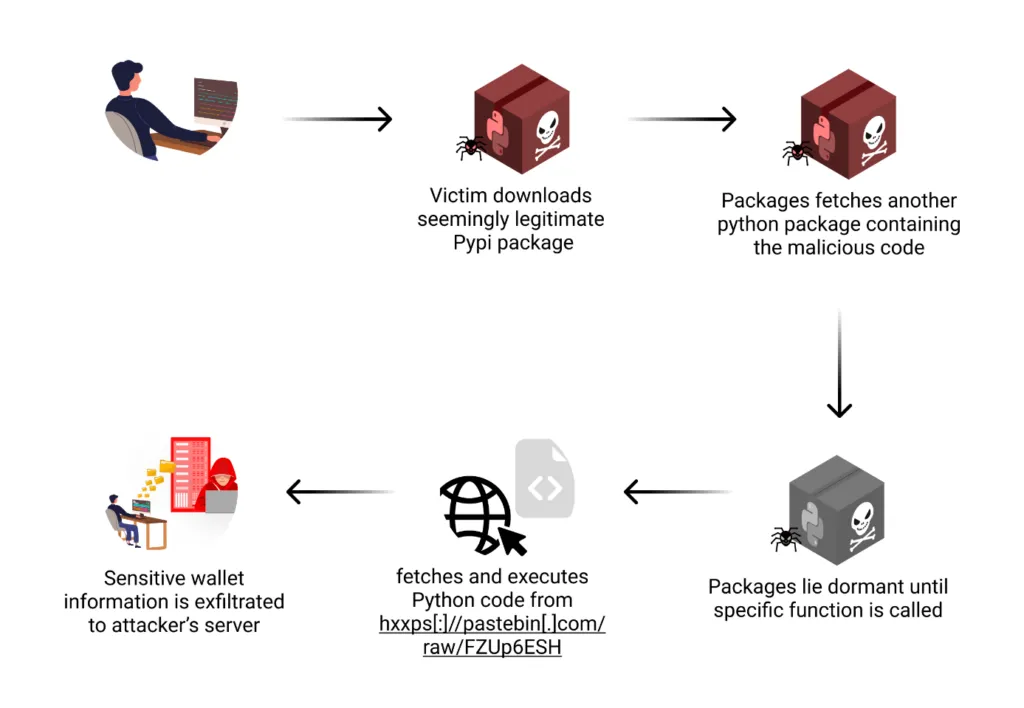
Crypto stealers on PyPI: Checkmarx researchers have found four malicious Python libraries that steal sensitive cryptocurrency wallet data. The packages posed as legitimate tools for decoding and managing wallet data but contained hidden code that stole private keys and mnemonic phrases. According to Checkmarx, the main packages were clean, but the malicious code was hidden in one of their dependencies.
CosmicSting campaigns: Seven different threat actors have hijacked 5% of all Magento and Adobe Commerce stores over the past three months. More than 4,200 sites were hacked, including online stores at Cisco, Ray Ban, National Geographic, Whirlpool, and Segway. The attacks exploited a vulnerability known as CosmicSting (CVE-2024-34102), which Adobe patched in early June.
New Hunters International domain: The Hunters International data extortion group has a new site at huntersinternational[.]su. Let me express my skepticism that Russian authorities will take down the domain any time soon. [h/t Dominic Alvieri]
New Nitrogen ransomware: A new ransomware gang launched its dark web leak site this week. They go by Nitrogen and currently list only six victims on the site. [h/t Dieter D.]
Malware technical reports
More_eggs backdoor: Trend Micro has published an analysis of More_eggs, a JScript backdoor that belongs to the Golden Chickens malware-as-a-service (MaaS) toolkit. It's been used in the past by groups such as FIN6 and the Cobalt Group.
XWorm: Netskope's threat intel team has published a report on the XWorm malware and its newer stealth and evasion techniques.
Latrodectus: OALABS has published some Latrodectus IOCs.
Hadooken and K4Spreader: Sekoia has published an analysis of Hadooken and K4Spreader, two new malware strains deployed in attacks by the 8220 Gang.
Joker: Poland's CERT has published a technical analysis of recent versions of the Joker Android malware.
Nitrogen to BlackCat: The DFIR Report team has dropped a report on Nitrogen malware infections leading to BlackCat ransomware attacks.
Key Group ransomware: Kaspersky has published an analysis of Key Group, a ransomware group that launched in early 2022 and primarily targets Russian companies.
GorillaBot: NSFOCUS researchers have discovered a new IoT botnet that launched over 300,000 DDoS attacks over just three weeks in September. Named GorillaBot, the botnet is built on the leaked source code of the old Mirai malware. The botnet's main targets have been organizations in critical infrastructure across the world. Chinese organizations accounted for a fifth of all victims.
Sponsor Section
Founded in 2019, Zero Networks is a unified zero-trust platform for network segmentation, identity segmentation, and secure remote access. Zero Networks' microsegmentation module is automated, agentless, and segments all network assets to stop lateral movement and block ransomware with a firewall and just-in-time MFA.
APTs, cyber-espionage, and info-ops
MuddyWater's BugSleep: Security researcher Nikhil Hegde has published an analysis of MuddyWater's BugSleep backdoor.
Russian influence ops: Thomas Rid has published an overview of Russia's propaganda efforts and their impact on the West and Russia itself.
"In short, the SDA did not keep running campaigns and receiving funding despite being repeatedly exposed. It was able to keep running campaigns precisely because its work was exposed by its adversaries."
Vulnerabilities, security research, and bug bounty
KEV update: CISA has updated its KEV database with four vulnerabilities that are currently exploited in the wild. The list includes a 2019 SAP Commerce bug, a 2020 DrayTek Vigor router command injection, a 2021 Motion Spell GPAC bug, and a 2023 D-Link DIR router bug.
Office NTLMv2 vuln write-up: PrivSec's Metin Yunus Kandemir has published a write-up and PoC for CVE-2024-38200, a new NTLM relay attack affecting Office apps. This was patched in mid-August after Kandemir's DEFCON talk.
PHP bug write-up: LEXFO's Charles Fol has published the third part of his analysis of CVE-2024-2961, a Glibc vulnerability (CVE-2024-2961) that can be used for remote code execution attacks on PHP-based applications and websites. Parts one and two are here. This was disclosed and patched back in May.
SolarWinds Serv-U exploitation: GreyNoise has published details of recent attacks targeting a June SolarWinds Serv-U vulnerability tracked as CVE-2024-28995.
TeamCity security updates: JetBrains has released 20 security updates for its TeamCity CI/CD server.
US court system vulnerabilities: Security researcher Jason Parker has found vulnerabilities in 19 platforms used by US federal and local government agencies. The systems are used by hundreds of courts, voting agencies, and other agencies. Parker warns that threat actors could have used these now-patched vulnerabilities to alter voter registration databases and meddle in future elections. [Additional coverage in ArsTechnica]
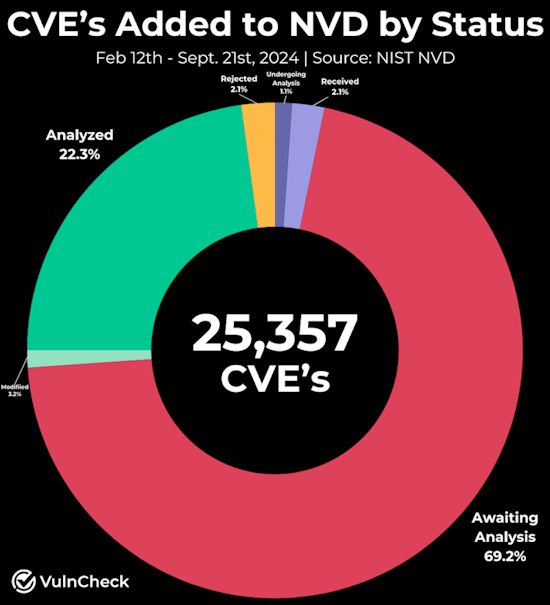
NIST backlog still there: US NIST has failed to address a backlog of unprocessed vulnerabilities at the National Vulnerability Database (NVD). The agency announced in May that it would hire a contractor to clear the NVD backlog by the end of September. According to VulnCheck, the NVD backlog has seen a continuous rise and has now reached more than 23,000 unprocessed vulnerabilities. Reports from July anticipated that NIST would fail to address the backlog. Security firm Fortress estimated that the backlog would reach more than 30,000 entries by the end of the year.
Infosec industry
Acquisition news: ICS security firm Dragos has acquired Network Perception, the maker of NP-View, a network visualization platform for OT networks.
Industry moves: Kevin Mandia has joined SpecterOps as chair of its board of directors.
New tool—LOLESXi: BlueTeamOps has published a new project named LOLESXi (Living Off The Land ESXi). The project lists binaries and scripts that are natively available in VMware ESXi that have been used by threat actors in their attacks in the past. The project is similar to other initiatives that track benign tools that can be abused for attacks on Windows (LOLBAS, LOLDrivers, and LOFLCAB), Linux (GTFOBins), macOS (LOOBins), and CI/CD pipelines (LOTP).
New tool—capa Explorer Web: Google's Mandiant team has released a web version of its capa malware analysis toolkit.
New tool—WhoYouCalling: Security researcher Hannes has released WhoYouCalling, a new networking monitoring tool that uses Windows Event Tracing (ETW) and Full Packet Capture (FPC).
New tool—IllusiveFog: Chaitanya Haritash has released IllusiveFog, a Windows implant with Socks5 proxy support.
New tool—FaceDancer: Black Hills Information Security's Matt Eidelberg has released FaceDancer, an exploitation tool aimed at creating hijackable, proxy-based DLLs.
Threat/trend reports: AppViewX, CISA, Dr.Web, Ping Identity, Sucuri, and Trend Micro have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about various Southeast Asian countries investing in cyber forces, the drivers behind these decisions, and what kind of actions make sense.
In this podcast, Tom Uren and Patrick Gray talk about the possibility of deterring Volt Typhoon, the Chinese group that is compromising US critical infrastructure to enable future disruption operations in the event of a conflict with the US. Tom thinks it is not possible to deter Volt Typhoon, but things might work the other way. If the US can neuter Volt Typhoon and take away the PRC's magic cyber bullet, it could make conflict less likely.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!






