Risky Biz News: New DNS attack impacts a quarter of all open DNS resolvers
In other news: EU MP targeted with Candiru spyware; Meta suspends Nigerian scammer accounts; US charges Andariel member for ransomware attacks.

This newsletter is brought to you by Socket, a developer-first security platform that prevents vulnerable and malicious open-source dependencies from infiltrating software supply chains. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

A team of Chinese academics has discovered a new type of DNS attack that impacts almost a quarter of all open DNS resolvers running on the internet.
Named TuDoor, the attack uses malformed DNS packets to trigger logic errors inside DNS software. The attack specifically targets the part of the DNS resolver that prepares DNS responses for user queries.
Academics say they can use a quick succession of malformed packets to poison a DNS resolver's cache, cause a denial of service, or increase a server's resource consumption.
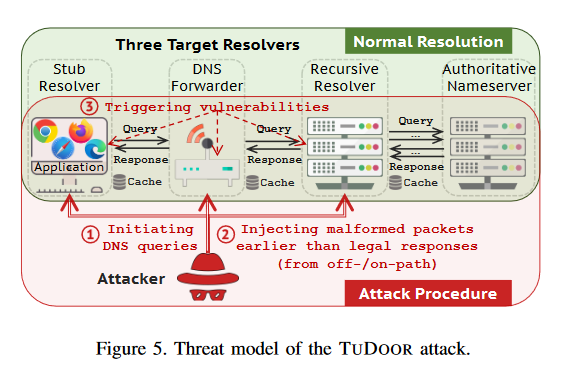
The research team says it tested 28 mainstream DNS services and software and found 24 to be vulnerable to one of the three TuDoor attack variations.
Eighteen of the 24 projects have acknowledged the research team's work and have issued 33 CVEs for tracking the patching for TuDoor attack variations.
So far, patches have been released by Google, Microsoft, Cloudflare, BIND, Knot, AdGuard, and others.
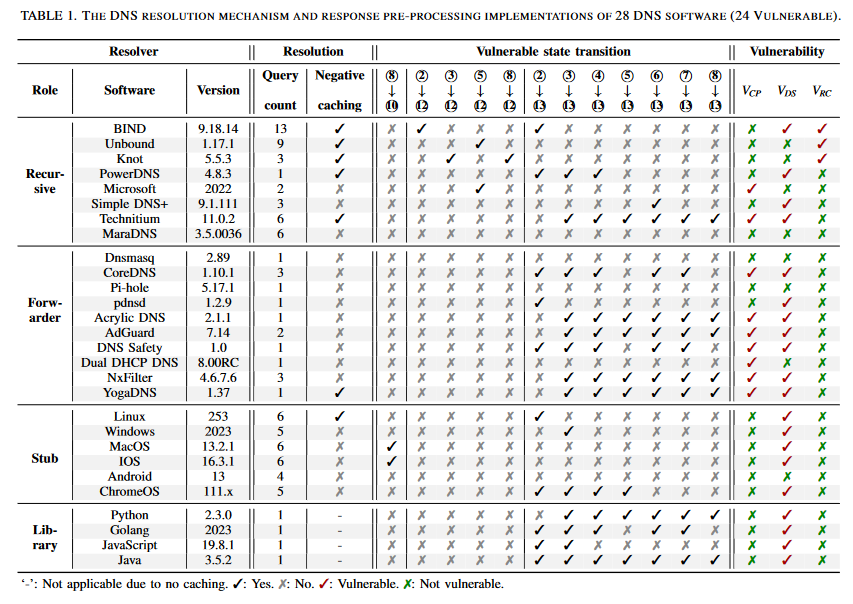
At the time of their work last year, researchers said they scanned the internet and found that 423,652 open DNS resolvers were vulnerable to TuDoor attacks. The number represented 23.1% of all open DNS resolvers online. It's unclear how many are still vulnerable today.
The team named the attack after the TuMen (突门) secret openings left in China's Great Firewall to allow scouts to go through.
Some of the academics who worked on the TuDoor research also worked on the DNSBomb attack published earlier this year.
Breaches, hacks, and security incidents
Leidos hack: A threat actor has leaked data they claim to have stolen from Leidos Holdings, one of the largest IT contractors for the US government. Leidos claims the data was stolen from one of its suppliers, Diligent Corp. Leidos primary customers include the US Department of Defense, NASA, and Homeland Security. The Trigona ransomware gang took credit for the attack and leaked the company's data earlier this week. [Additional coverage in Bloomberg]
Z-Library copycat leak: A clone of the Z-Library academia piracy portal has leaked the details of more than 10 million users. [Additional coverage in CyberNews]
BSNL breach: Bharat Sanchar Nigam Limited (BSNL), one of India's largest telecom companies, admitted to a security breach. The hack came to light in May after a hacker started selling customer data on an underground hacking forum. [Additional coverage in Hindustan Times]
Spytech breach: Hackers have breached and leaked data from US spyware vendor Spytech. The leaked data contains information on more than 10,000 devices where the company's spyware was installed. The data dates back to 2013 and covers Android, Windows, Mac, and Chromebook devices. Spytech's CEO told TechCrunch, the company was not aware of the breach, and they have now started an investigation.
MonoSwap crypto-heist: Cryptocurrency platform MonoSwap has confirmed that hackers gained access to its service and drained funds from its liquidity pools. The platform says the hack took place after one of its developers fell victim to a phishing email pretending to come from a VC firm. The size of the lost funds is still unknown. MonoSwap told users not to deposit new funds on the platform until it concludes its investigation.
General tech and privacy
CrowdStrike incident analysis: Security firm CrowdStrike has published a technical analysis of the bug that caused 8.5 million Windows systems to crash last week with a BSOD error. The company has blamed the incident on a bug in its content validator testing system that allowed the faulty configuration update to go through. CrowdStrike says it's planning for better testing and staggered updates to smaller pools of customers. It will also provide release notes for EDR content updates, something it has not done before.
CrowdStrike losses to reach $15 billion: Insurer Parametrix estimates that financial losses from the CrowdStrike IT outage could reach around $15 billion globally. Companies in banking and healthcare are expected to be hit the hardest. [Additional coverage in Reuters]
Windows Update issues: Microsoft warns that one of its July 2024 security updates is causing some devices to boot into the BitLocker recovery screen.
Let's Encrypt to end OCSP service: Free certificate authority Let's Encrypt has announced plans to retire support for the Online Certificate Status Protocol (OCSP) in favor of Certificate Revocation Lists (CRLs). Both are technologies to allow CAs to revoke bad certificates. Let's Encrypt says it's deprecating OCSP support because of the protocol's privacy issues.
Proton launches crypto-wallet: Proton, the company behind ProtonMail, has launched a cryptocurrency wallet—obviously, named Proton Wallet.
Chrome 127: Google has released version 127 of its Chrome browser. See here for security patches and webdev-related changes. The biggest change is a feature named "App-bound encryption for cookies" that encrypts local cookies with a key only the Chrome application has. This helps secure browser cookies against theft by malware running as the same user. Although, as Google explains, this is not a perfect feature.
"This does not protect against an attacker who is able to elevate privilege or inject into Chrome's processes."
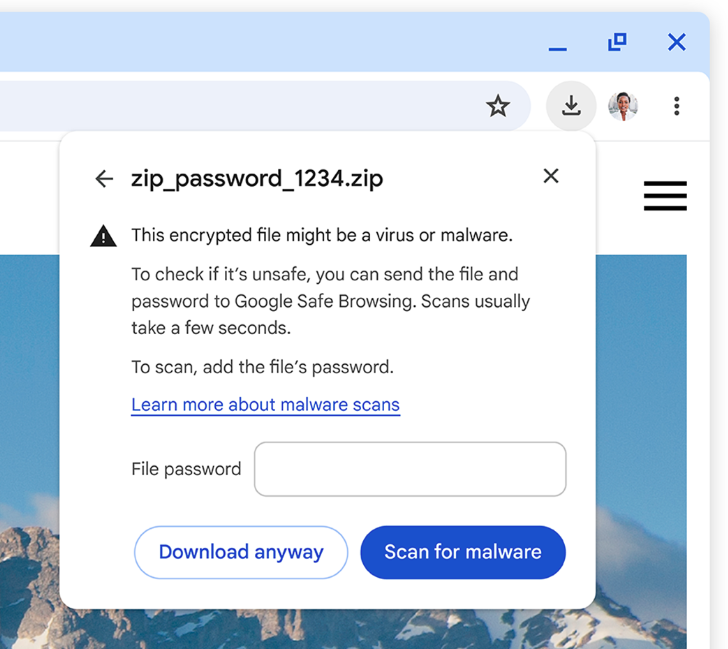
Chrome adds warning for password-protected archives: Google has added a new warning system to the Chrome browser that alerts users when they download password-protected archive files. The company says these types of files are often used to deliver malware because security software can't unzip the archive and scan for threats. Chrome shows a similar warning when users download executable files, another format abused for malware distribution.
Government, politics, and policy
Switzerland goes FOSS: The Swiss government has passed new legislation mandating the use of open-source software in the public sector. [Additional coverage in ZDNet]
Candiru infection in the EU Parliament: German Green MEP Daniel Freund says he was targeted in May this year with the Candiru spyware. Freund says the attack did not succeed because he did not click the malicious link he received via email. The MP says the email was made to look like coming from a female student at Kyiv International University organizing an EU-related seminar. The official did not attribute the attack to any entity. Politico Europe points out Freund has been Viktor Orban's greatest critic in the EU Parliament.
NSO lawsuit goes political: Amnesty International and Forbidden Stories claim the Israeli government is meddling on the side of NSO Group in a lawsuit filed in the US by WhatsApp. Reporters claim the Israeli government has raided NSO offices and seized documents related to the Pegasus spyware. The government has also allegedly issued gag orders to prevent news of the raids and the documents from being widely shared. According to documents leaked to reporters, the gag was put in place to allegedly "protect Israel's national security and foreign relations." The purpose of the raids and seizures is to prevent Pegasus files from being included in the WhatsApp lawsuit discovery process.
Separate NSO lawsuit update: News of the gag order comes a day after an update in a separate NSO lawsuit. Google, Microsoft, and other tech companies have also filed a legal document arguing that foreign nationals should be able to sue Israeli spyware maker NSO Group in the US if they have been targeted with the company's spyware. The amicus brief is part of a separate lawsuit filed by an El Salvadoran journalist against the Israeli company. A judge initially dismissed the lawsuit in March, arguing that all parties involved are "entirely foreign" to the US legal system. US tech companies argued that as long as NSO uses US infrastructure for the attacks, the company should be liable. [Additional coverage in The Record]
CrowdStrike outage used for state propaganda: Both China and Russia are using the recent CrowdStrike outage to tout their tech "independence" and how much more reliable their local tech solutions are. I guess Russia forgot about all the Kaspersky-caused outages.
Russia admits slowing down YouTube: In typical Kremlin fashion, Russian officials couldn't keep a straight face about one of their lies and have unofficially admitted to slowing down YouTube traffic on purpose as punishment for Google banning their propaganda channels. The Russian government previously blamed the slower traffic on "defective Google equipment." In reality, they launched their own YouTube clone called Platforma and are preparing for a full-on YouTube ban later this fall. Now, State Duma deputy Alexander Khinshtein claims YouTube traffic is slower by 40% and is scheduled to reach 70% by next week.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Feross Aboukhadijeh, CEO and Founder of Socket, about how open-source repositories are riddled with horrible software. Feross explains why it makes a difference if a package is vulnerable, malicious, or just unwanted and how current transparency mechanisms such as CVEs and the NVD just aren't suitable for the challenge of open-source repositories.

Cybercrime and threat intel
Meta disrupts Nigerian scammers: Social media company Meta has suspended 63,000 Instagram accounts that were used by Nigerian threat actors to target victims with sextortion attempts. Meta says 2,500 of the accounts were run by a group of 20 individuals believed to be working as part of a coordinated campaign. The company says it also removed 7,200 Facebook accounts, pages, and groups that were being used to recruit and train new scammers.
French authorities take down PlugX botnet: French authorities have taken control of the PlugX botnet and are pushing a special payload that removes the malware from infected systems. The disinfection operation is taking place with the help of French security firm Sekoia, which sinkholed one of the botnet's command and control servers earlier this year. In April, Sekoia offered to help national CERT teams perform "sovereign disinfections." The PlugX botnet is a Windows malware trojan that spreads via USB devices. It was initially used in Chinese cyber-espionage campaigns but was later also adopted by the Chinese cybercrime ecosystem. Sekoia says the botnet infected 2.5 million distinct devices, with 100,000 systems pinging command servers on a daily basis.
Threat/trend reports: Action1, BI.ZONE, Check Point, Cisco Talos, Docker, Europol, NetRise, Positive Technologies, Red Canary, SonicWall, StormWall [1, 2], and Symantec have recently published reports covering infosec industry threats and trends. The most interesting of these is the Europol report which found that cybercrime groups are staying away from larger RaaS platforms after some had been the target of law enforcement disruptions over the past years. Instead, groups are using smaller services or developing their own custom tools using previously leaked code.
Hamster Kombat threats: ESET looks at the ever-growing plethora of threats around the silly Hamster Kombat Telegram game.
New Cronus ransomware: CyFirma's Kaushík Pał has spotted a new ransomware strain named Cronus. The ransomware popped up this month and appears to be specifically targeting PayPal users.
Silly W2 Form campaign: Rapid7 has spotted a silly phishing campaign using IRS W2 form lures to trick users into infecting themselves with malware.
Indian smishing: Fortinet has published details on a smishing campaign targeting Indian mobile users using India Post lures. Fortinet links this to a group known as the Smishing Triad.
DDoS attacks in Spain: Netscout looks at all the threat actors launching DDoS attacks against Spain. It's quite a lot, and probably why Spain moved to arrest three NoNam057 members last week.
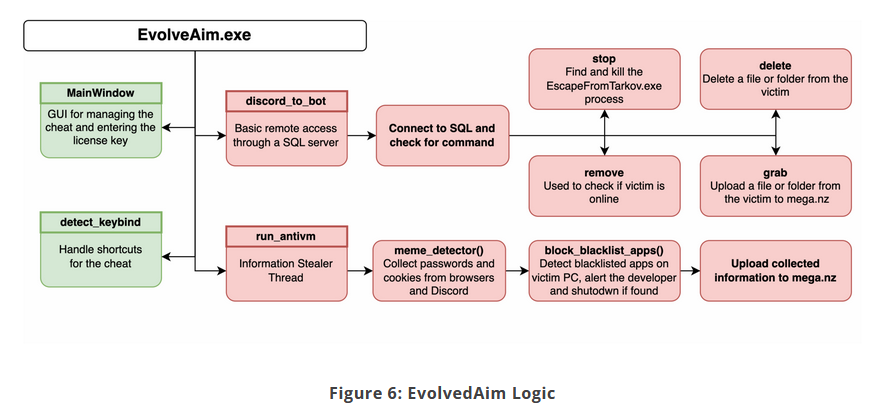
EvolvedAim Tarkov cheat delivers malware: Security firm CyberArk says that a cheat tool for the "Escape from Tarkov" game has infected its buyers with an infostealer. The malware was designed to collect passwords and cookies from a user's local browsers and upload the data to a remote Discord server. CyberArk estimates the number of infected victims at around 1,000. The company's discovery comes after some Tarkov players called out the cheat maker for bundling malware with its tool back in January.
Stargazer Goblin: A threat actor named Stargazer Goblin is operating a network of more than 3,000 GitHub accounts dedicated to posting and promoting malicious links. The accounts are part of an underground service that helps cybercrime groups spread links to malware or phishing sites. Security firm Check Point says it tracked down ads for the service as far back as August 2022. The company estimates the group has made at least $100,000 from operating the service.
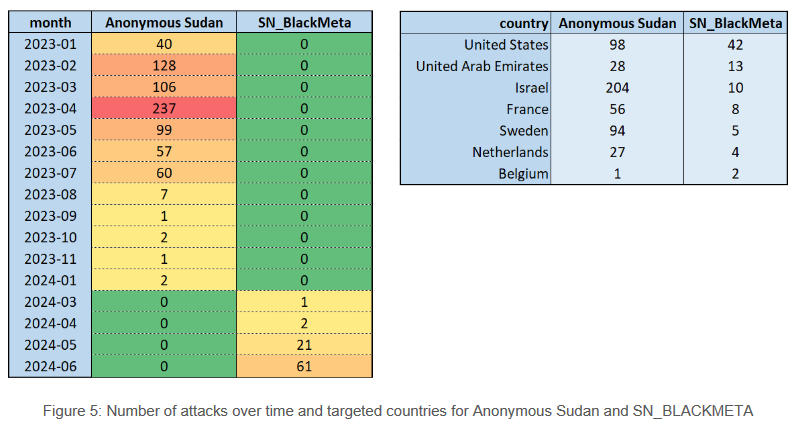
SN_BLACKMETA: A new hacktivist group carrying out DDoS attacks for the Palestinian cause appears to be an alternate persona for the Anonymous Sudan pro-Kremlin group. Security firm Radware says the new SN_BLACKMETA group began launching attacks as activity from Anonymous Sudan stopped earlier this March. Radware says SN_BLACKMETA's attacks came from infrastructure previously associated with Anonymous Sudan. In addition, the group often posts in Russian, and one of its Twitter accounts appears to have been created by an individual from Staraya Russa, a town in Novgorod Oblast, Russia. SN_BLACKMETA joins a long list of fake hacktivist groups that try to mimic grassroots movements but are actually Russian info-ops designed to stoke anti-Western sentiments.
Malware technical reports
Brute Ratel C4: ANY.RUN has published a write-up on how the Brute Ratel C4 framework is being used to drop the Latrodectus loader in campaigns in the wild.
SocGolsih: German security firm G Data looks at recent activity from the SocGolish (FakeUpdates) group.
Flame Stealer: CyFirma looks at Flame Stealer, a new C/C++ infostealer that is being advertised by a Portuguese-speaking threat actor.
LATAM banking malware: IBM X-Force has published a report on CyberCartel, Caiman, and OTPBypass/Figrabber, three banking malware strains currently being used to target LATAM users.
Sponsor Section
Come meet the Socket team at BlackHat and DEF CON! We're sponsoring some fun networking events, and we would love to see you there.

APTs, cyber-espionage, and info-ops
US charges Andariel member: The US Department of Justice has charged a North Korean man for his role in launching ransomware attacks against US hospitals. Officials say Rim Jong Hyok is a member of North Korean APT group Andariel and participated in attacks that deployed the Maui ransomware across the US throughout 2021 and 2022. Rim becomes the second North Korean hacker to be charged in connection to ransomware attacks in the US after Park Jin Hyok, the alleged creator of the WannaCry ransomware. Rim was added to the FBI's Cyber Most Wanted list, and the US State Department is offering a $10 million reward for any information that may lead to his capture. The Andariel group is one of the cyber units linked to North Korea's RGB military intelligence agency.

Andariel/APT45 reports: On the same day of the DOJ charges and State Dept reward, CISA, Google, and Microsoft published reports on the group's known tactics. Besides Andariel, the group is also known as APT45, Onyx Sleet, Stonefly, and Silent Chollima.
Cuckoo Spear: Cybereason has published a report on the revamped arsenal of Chinese APT group Cuckoo Spear (APT10).
UAC-0057: Ukraine CERT has seen new activity from the UAC-0057 group, this time spreading macro-based Office documents that drop Cobalt Strike and PICASSOLOADER.
APTs in SEAsia: Positive Technologies has published a report looking at how APT groups operate across Southeast Asia. The report looks at both attackers and defenders (the state of cybersecurity in the region).
Vulnerabilities, security research, and bug bounty
AWS session tokens: Security researcher Tal Be'ery takes an in-depth look at how AWS session tokens work.
"Today, we are making it more of glass box, by sharing code and tools to programmatically analyze and modify AWS Session Tokens. Using this code we were able to take a seminal deep look into the contents of AWS Session Tokens, expose unknown facts about AWS cryptography and authentication protocols and finally test their resilience against forging attacks (Spoiler alert: surprisingly good!)"
Progress Telerik updates: Progress Software has released two security updates for its Telerik reporting server. One of them is an insecure deserialization vulnerability with a score of 9.9/10.
NVIDIA security updates: NVIDIA has released two security updates this week to patch issues in its Jetson robotics system and data center switch OS.
Check Point zero-day analysis: WatchTowr Labs has published an analysis of CVE-2024-24919, the Check Point VPN zero-day exploited back in May.
Easy!Appointments vulnerabilities: Palo Alto Networks says it used an AI tool to identify 15 Broken Object-Level Authorization (BOLA) vulnerabilities in the Easy!Appointments open-source project.
Docker AuthZ auth bypass: The Docker security team says that certain versions of the Docker Engine contain a vulnerability in the AuthZ authorization plugin. The bug can be exploited to bypass authentication using a specially crafted API request to the AuthZ plugin. Docker says the issue has been known since 2018 but was never patched until this week.
ServiceNow exploitation: Threat actors are exploiting a recently disclosed vulnerability (CVE-2024-4879) to hack ServiceNow business platforms. The attacks started after details and a PoC for three ServiceNow vulnerabilities were published online. Resecurity says attackers are taking over unpatched systems and dumping user details, including passwords. According to IoT search engine FOFA, there are almost 300,000 ServiceNow instances connected the internet.

CFOR vulnerability class: Truffle Security has published details about a new type of vulnerability class known as Cross Fork Object Reference (CFOR). The new vulnerability occurs when one repository fork can access sensitive data from another fork, including data from private or deleted repos. The company says the major implication is that any code committed to a public repository may be accessible forever as long as there is at least one fork of that repository still available somewhere. Truffle Security says the issue impacts GitHub but can't be fixed because of how the service was designed to work.
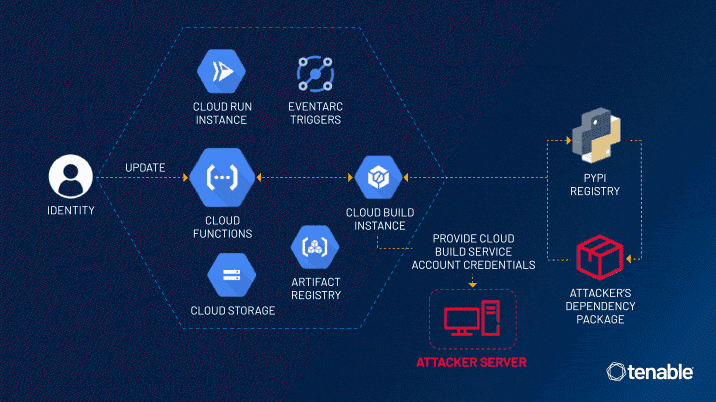
ConfusedFunction vulnerability: Security firm Tenable has found a vulnerability in Google's Cloud Build CI/CD pipeline service. Named ConfusedFunction, the vulnerability can allow threat actors to elevate access from Cloud Function permissions to the default Cloud Build service account. The access can allow attackers to poison an organization's GCP build process. Google has mitigated the vulnerability, but only for new Cloud Build accounts going forward. Existing GCP users are required to take manual actions to fix the issue.
Infosec industry
New tool—DuffMan: Security researcher Kanstantsin Markelau has open-sourced DuffMan, a diagnostic utility for fuzzing and fault management of API nodes.
Cisco Talos history: Cisco Talos is celebrating its 10th anniversary, and the team has published a short history of its evolution across the years.
China's Matrix Cup: The Natto Team and Eugenio Benincasa have published an in-depth look at China's newest hacking contest, the Matrix Cup. The competition looks like a revamped and improved version of the older Tianfu Cup, and also looks to be another vulnerability and exploit-harvesting operation for state authorities.
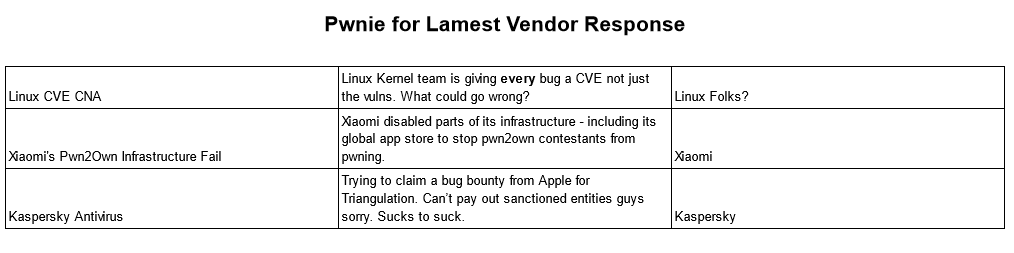
Pwnie Awards 2024: This year's Pwnie Awards nominations are out! This year, we have 11 categories, from Best Crypto Bug to Lamest Vendor Response. Some of the major bugs and incidents nominated this year include BlastRADIUS, Operation Triangulation, the GoFetch attack on Apple chips, the Ahoi attack on AMD chips, Linux giving everyone a CVE, and the XZ backdoor incident.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss whether the rise of cloud computing has been a boon or a curse for cyber espionage agencies.
In this podcast, Tom Uren and Patrick Gray discuss the wild story of a Chinese illegal gambling operation that involves human trafficking, shell companies, money laundering, hundreds of thousands of websites, and sponsorship of European football teams.
This Soap Box edition of the show is with Mike Wiacek, the CEO and Founder of Stairwell. Stairwell is a platform that creates something similar to an NDR, but for file analysis instead of network traffic. The idea is you get a copy of every unique file in your environment to the Stairwell platform, via a file forwarding agent. You get an inventory that lists where these files exist in your environment, at what times, and from there, you can start doing analysis.




