Risky Biz News: New Chinese APT attacks US critical infrastructure
In other news: Barracuda patches actively exploited zero-day; new Russian-made ICS malware discovered; and new Pegasus spyware infections found in Armenia and Mexico.
This newsletter is brought to you by Thinkst. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Microsoft and the NSA have discovered a new Chinese APT group targeting critical infrastructure organizations in the United St.
Named Volt Typhoon, the group has been active since mid-2021 and has gone under the radar due to a focus on stealth in its intrusions.
Operators rely almost exclusively on living-off-the-land and hands-on-keyboard techniques to avoid detection.
They also use a network of compromised SOHO routers to proxy and hide connections from infected networks inside residential internet traffic.
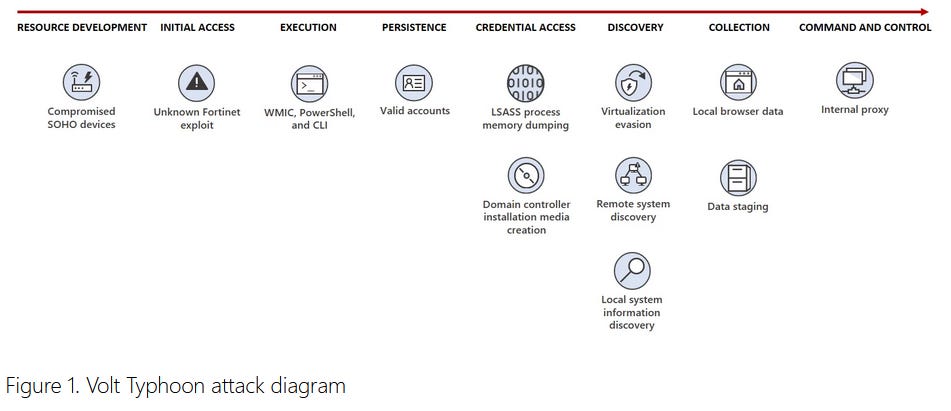
Microsoft says it initially found the group while investigating an intrusion at a US port and later saw the group target the telecommunications sector in Guam. An investigation found a sprawling trail of hacks among several US critical sectors.
Microsoft says the group's motives are espionage and information gathering, and they believe the group may be "pursuing development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises."
The company, the NSA, and its Five Eyes allies have released an in-depth technical advisory [PDF] of the group's TTPs, which they hope will help organizations find traces of the group's operations on their networks.
Secureworks has also released a technical report on the group, which the company is tracking as BRONZE SILHOUETTE.
The company also provides probably the best explanation on why the once-noisy Chinese APT groups are now putting so much effort into stealth and remaining undetected.
"This focus suggests a high level of operational maturity and adherence to a blueprint designed to reduce the likelihood of the detection and attribution of its intrusion activity. This attention to operational security, particularly when targeting Western organizations, is consistent with network compromises that [Secureworks] CTU researchers have attributed to Chinese threat groups in recent years. These tradecraft developments have likely been driven by a series of high-profile U.S. Department of Justice indictments of Chinese nationals allegedly involved in cyberespionage activity, public exposures of this type of activity by security vendors, and the consequential likely increased pressure from PRC leadership to avoid public scrutiny of its cyberespionage activity."
The recent focus of Chinese APTs on stealth makes a lot of sense, especially when we've seen Chinese government officials mount a very public campaign bent on portraying the US as an "iresponsible cyber power." You can't really make those kinds of accusations if you haven't told your own hackers to keep it on the down low, or at least try.
Breaches and hacks
China hacks Kenyan government: Chinese cyber-spies have breached the networks of several Kenyan government entities in a years-long campaign. The hacks hit the country's finance ministry, foreign affairs ministry, president's office, and even its spy agency. Sources told Reuters the espion was most likely trying to gather information on Kenya's plan to pay down $9 billion in Chinese loans.
CS Token crypto-heist: A threat actor has exploited a vulnerability in the smart contract of the newly launched CS Token project to steal $714,000 worth of crypto assets.
Fintoch exit scam: The operators of the Fintoch DeFi platform appear to have absconded with $31.6 million in cryptocurrencies belonging to their investors in an apparent exit scam. News of the platform's sudden disappearance isn't a surprise for many in the cryptocurrency space, as the platform has been tied to several scandals in the past months. Fintoch was accused of using the image of a paid actor for its CEO's headshot on its official website. It also claimed to be owned by Morgan Stanley, a statement the financial powerhouse denied in a rare press release [PDF]. Fintoch also claimed to be licensed by the Monetary Authority of Singapore, a claim the MAS immediately shot down earlier this month and issued an investor alert about Fintoch and its management. [Additional coverage in CoinTelegraph]
Bit Lucky Ponzi scheme: More than 1,000 investors lost around €70 million after Croatian cryptocurrency investment platform BitLucky made a bunch of bad investments and lost all their funds. In hindsight, local media is reflecting that the company was a giant Ponzi scheme from the get-go after promising monthly returns of 5-25%, something that should have stood out as suspicious to most serious investors. [Additional coverage in Juatarnji]
General tech and privacy
PyPI subpoenaed: The Python Software Foundation says it received three subpoenas for data on three users on PyPI, the package repository for the Python programming language. All three subpoenas were issued by the US Department of Justice and were sent in March and April of this year. The Foundation says that after consulting with its legal team, it honored the requests and shared details about five PyPI accounts with US authorities. Shared information included names, mail and email addresses, connection details, IP addresses, and telephone numbers, but also the IP addresses of those who downloaded packages from the five users.
Aave bug freezes user funds: More than $110 million worth of crypto assets are stuck on the Aave DeFi platform due to a bug in the company's code. The protocol developers said all funds on the platform remain safe, although a bit frozen. A fix is expected to be rolled out this week, more than a week after the funds have become inaccessible to their owners. [Additional coverage in BeInCrypto]
Windows 11 gets better archive support: Microsoft has announced that Windows 11 will soon support most open-source archive file formats supported by the libarchive project, which means that after decades, Windows will have native support for extensions such as 7zip, rar, gz, and others. Good news for some APT groups, which won't have to bring their pirated WinRAR versions on future intrusions anymore!
Brave gets an OTR mode: The Brave browser has announced a new feature called Off-The-Record mode, where websites can mark their content as "sensitive." When Brave comes across one of these sites, it will prompt users to load the content in its OTR mode, a temporary storage area that gets wiped as soon as the user leaves the site. Other websites are treated normally, meaning users will appear to have a normal browsing history—which only lacks data on the website visited in the OTR mode. Brave says it developed this feature for victims of domestic abuse and others who need a safe way to access "sensitive" sites. Brave says this feature will release in the near future with version 1.53 on the desktop and version 1.54 on Android.
Government, politics, and policy
Massive robocall lawsuit: Attorneys General from 49 US states have filed a joint complaint against VoIP provider Avid Telecom for facilitating billions of robocalls across the US. Officials claim Avid Telecom intermediated more than 24.5 billion calls between December 2018 and January 2023 and that more than 90% of these were under 15 seconds—and most likely robocalls. The company did not only sell data and phone numbers of US citizens to its customers, but it also provided dialing software and expertise to help its customers make mass robocalls. In addition, officials also accused Avid Telecom of helping customers make hundreds of millions of calls using spoofed or invalid caller ID numbers. More than 8.4 million of these calls spoofed the identity of government and law enforcement agencies.
Space Force cyber update: The US Space Force expects to have more of its in-house cybersecurity professionals work on defending its core systems, such as satellite communications, in the near future. The service expects to free up more of its specialized personnel after the 16th Air Force cyber unit picks up some of the Space Force's more mundane tasks, such as monitoring emails and telephone communications. [Additional coverage in DefenseScoop]
Pegasus in Mexico: The Pegasus spyware has been found on the phone of Mexico's under-secretary for human rights, Alejandro Encinas. The spyware was discovered as Encinas began investigating abuses committed by the nation's military, a known contractor of the Pegasus spyware. The news comes after Mexico's Attorney General charged four former government officials as part of an investigation into the country's purchase of the Pegasus spyware in 2014. [Additional coverage in the New York Times/non-paywall]
Pegasus in Armenia: AccessNow, Amnesty International, and CitizenLab say they discovered traces of the Pegasus spyware deployed in Armenia on the phones of reporters, government officials, a UN official, and members of the country's civil society. The malware was deployed in 2021 and 2022, and investigators say evidence suggests that the targeting is related to the Nagorno-Karabakh military conflict between Armenia and Azerbaijan. Investigators say this marks the first time any commercial spyware was deployed during an international armed conflict. Researchers didn't attribute the attacks to either government. Although Azerbaijan is a known customer of NSO Group, the targets of this campaign also include critics of the Armenian government.
Sponsor section
This edition is brought to you by Thinkst Canary. Most companies find out way too late that they've been breached. Thinkst Canary changes this. Deployed and Loved on all seven continents.Thinkst Canary. Deploys in minutes; almost zero admin overhead. It just works!
Cybercrime and threat intel
Story of Mirai: IEEE Spectrum has a profile on the early years of the Mirai DDoS malware/botnet.
HiddenEyeZ: Stormshield published a report on HiddenEyeZ, a cybercrime group behind many RedLine Stealer campaigns, and their evolution to using their own custom-made malware (HiddenEyeZ HVNC) and the launch of their own crypting service named HiddenCrypt.
DarkCloud spam: AhnLab has details on a malspam campaign distributing the DarkCloud infostealer.
RPMSG phishing abuse: Trustwave has detected a threat actor using compromised Microsoft 365 accounts and encrypted emails (RPMSG) to deliver phishing emails. A clever campaign, as Trustwave also notes.
"The use of encrypted .rpmsg messages means that the phishing content of the message, including the URL links, are hidden from email scanning gateways. The only URL link in the body of the message points to a Microsoft Encryption service."
VPN brute-forcing activity: SOS Intelligence says it has seen indications of a rise in brute-force login activity against VPN services. The company linked the activity to an Initial Access Broker (IAB) who has recently released a brute-force scanning tool on a high-profile cybercrime forum.
Apache NiFi scanning: SANS ISC researchers have spotted a sudden spike in scans for Apache NiFi installations. The project was initially developed and later open-sourced by the NSA and is typically used to re-route large streams of raw data from sources to data processing endpoints.
ABUS scanning: The same SANS ISC team also saw scans for ABUS security cameras. The scans appear to use a recent ABUS vulnerability (CVE-2023-26609) disclosed in February of this year. There's a 99% chance the scanner is some DDoS botnet/booter service, like most of these usually are.
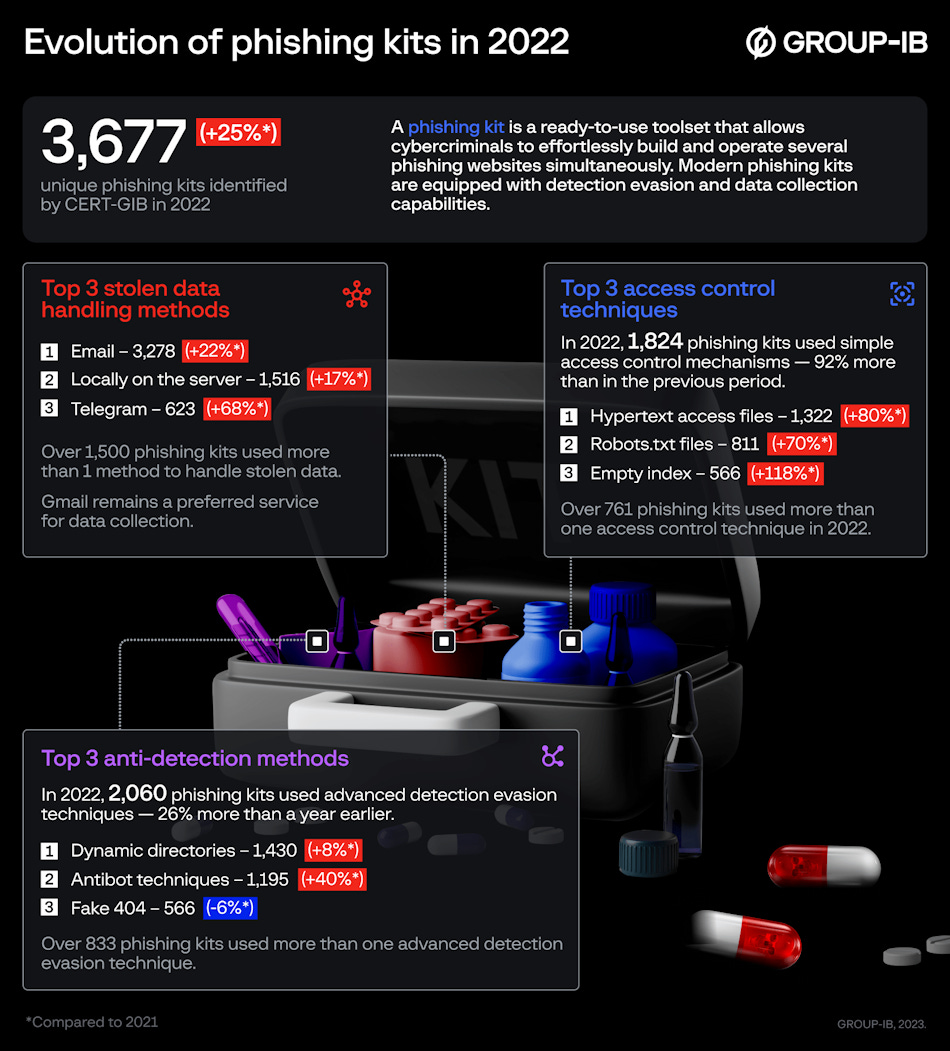
Phishing kit usage soars: Group-IB says it identified 3,677 unique phishing kits deployed in the wild last year, a 25% increase from the previous year. The company notes that many kits had support for evasive tactics, such as antibot techniques and randomization, showing a trend among threat actors wishing to avoid detection by security analysts and expand the lifespan of their phishing campaigns as much as possible. Another trend spotted last year was that most phishing kits used an email account—usually a Gmail inbox—to receive phished credentials. While email was the preferred collection method for 45% of phishing kits last year, Telegram channels were also found as an alternative collection method in almost 1,500 phishing kits spotted last year, indicating a new rising trend in the phishing ecosystem.
Malware technical reports
Legion: Cado Security says Legion, a tool used to hack into web servers, has been updated with support logins over SSH and SMTP and to be able to target additional AWS cloud services.
Dark Frost: Akamai has discovered a new IoT malware strain named Dark Frost that is being used to build a new DDoS botnet. Researchers say the malware was cobbled together using stolen code from several popular malware families, such as Mirai, Gafgyt, and Qbot. Although the botnet's author has bragged on social media about the botnet's expansive exploits, Akamai says Dark Frost has only infected a few hundred devices so far.
IZ1H9: PAN's Unit42 has discovered a new Mirai malware variant named IZ1H9 that is currently targeting Tenda, LB-Link, DCN, and Zyxel devices—obviously, for DDoS attacks. This new Mirai variant appears to have been active since early April this year.
PikaBot: Zscaler has a technical analysis of PikaBot, a new malware strain that Kaspersky reports has been targeting Russian users this month. Keep an eye on this one, as it's also being used as an initial launchpad for ransomware like BlackBasta.
"Pikabot may have potential ties to Qakbot with some commonalities in the distribution, design, and campaign identifiers. However, ThreatLabz has not established a definitive link yet between the two malware families."
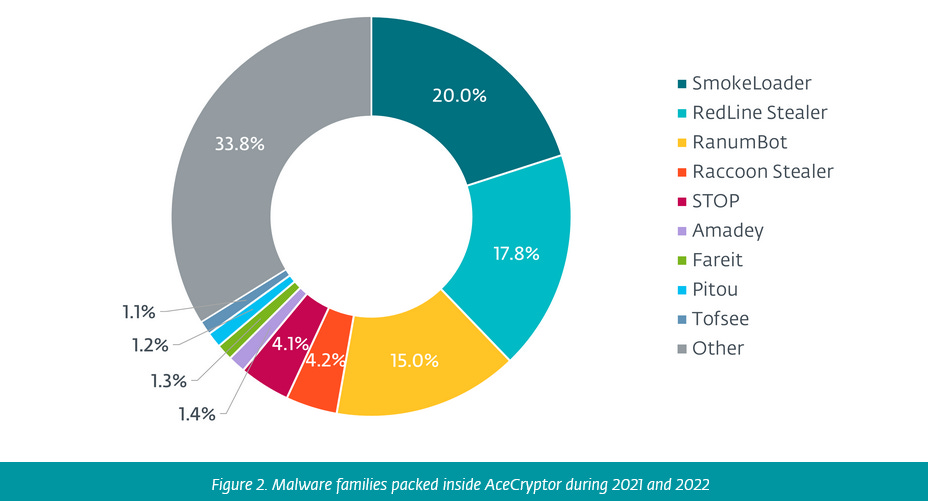
AceCryptor: ESET has an analysis of AceCryptor, a prevalent cryptor operating as a cryptor-as-a-service used by tens of malware families. The service has been live since 2016 and is currently used by the likes of the STOP ransomware, SmokeLoader, the RedLine Stealer, and a bunch more. (see image below)
Buhti: Broadcom's Symantec published a report on Buhti, a new ransomware strain based on the leaked LockBit source code that is operated by a new cybercrime group known as Blacktail. Symantec says recent Buhti attacks targeted PaperCut NG and MF systems (CVE-2023-27350). Back in February, the same Blacktail group targeted IBM Aspera Faspex file exchange servers (CVE-2022-47986).
Operation Magalenha: A Brazilian cybercrime group has launched a new series of attacks aimed at users of Brazilian financial institutions seeking to infect their systems with two new backdoors known as PeepingTitle. Tracked as Operation Magalenha, the attacks are seeking to steal credentials and PII data from infected hosts. SentinelOne says the two PeepingTitle backdoors have code overlaps with an older malware strain known as Maxtrilha that was first observed back in 2021. They believe the same group behind Maxtrilha is behind the recent attacks. SentinelOne noted that, unlike the previous attacks, the group has now chosen to use a Russian web hosting provider named Timeweb, known for ignoring abuse reports.
COSMICENERGY: Google's Mandiant division has identified a new strain of OT/ICS malware capable of disrupting electrical power grids. Named COSMICENERGY, the malware was uploaded to VirusTotal in December 2021 from a location in Russia. It contains functionality to interact with IEC-104 devices, which are remote terminal units used for remote control of power grid equipment across Europe, the Middle East, and Asia. Mandiant says that based on its analysis, they believe the malware might be a red-teaming tool used to simulate cyber-attacks on power grids during defensive cyber training exercises. Mandiant believes the tool was either developed by a contractor or by Russian security firm Rostelecom-Solar, which received a government subsidy in 2019 to train cybersecurity experts for emergency responses to attacks on electric power grids.
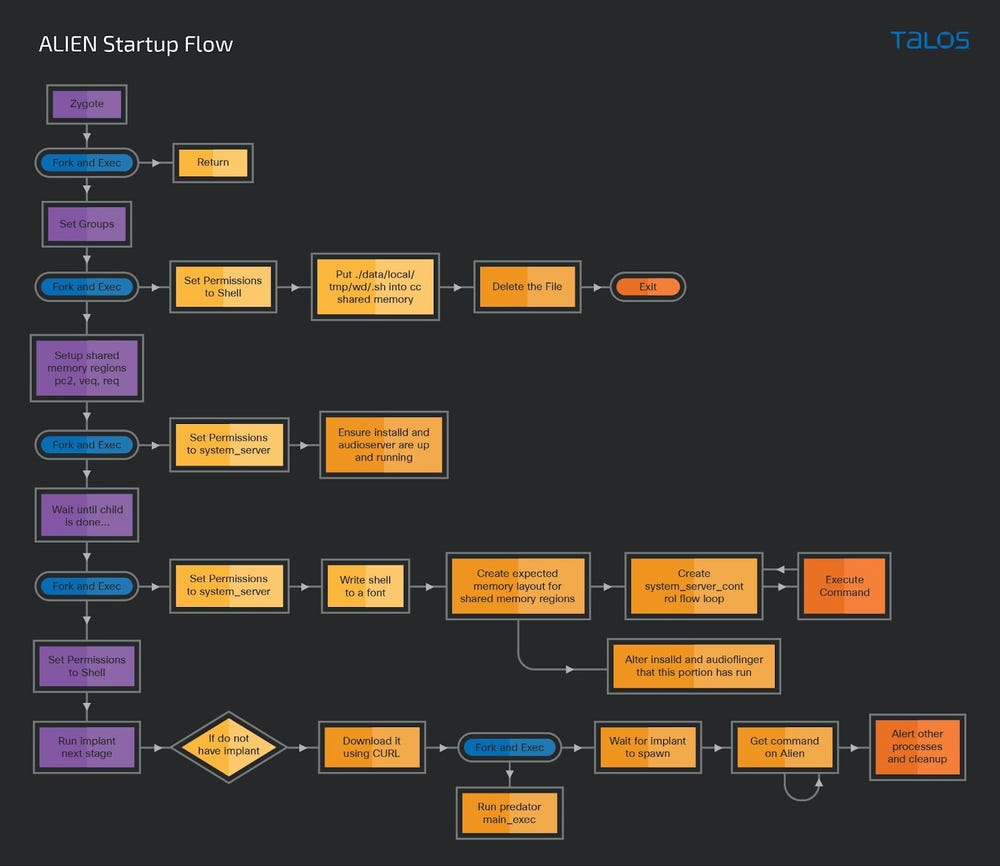
Alien-vs-Predator: Cisco Talos researchers have published a technical breakdown of Intellexa's Predator spyware and its loader, the ALIEN malware.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
APTs and cyber-espionage
APTs and SMBs: In a recent report on APT attacks that have targeted small-to-medium businesses (SMBs), Proofpoint says it observed several state-sponsored groups targeting smaller companies, such as threat actors aligned with the Russian, Iranian, and North Korean governments.
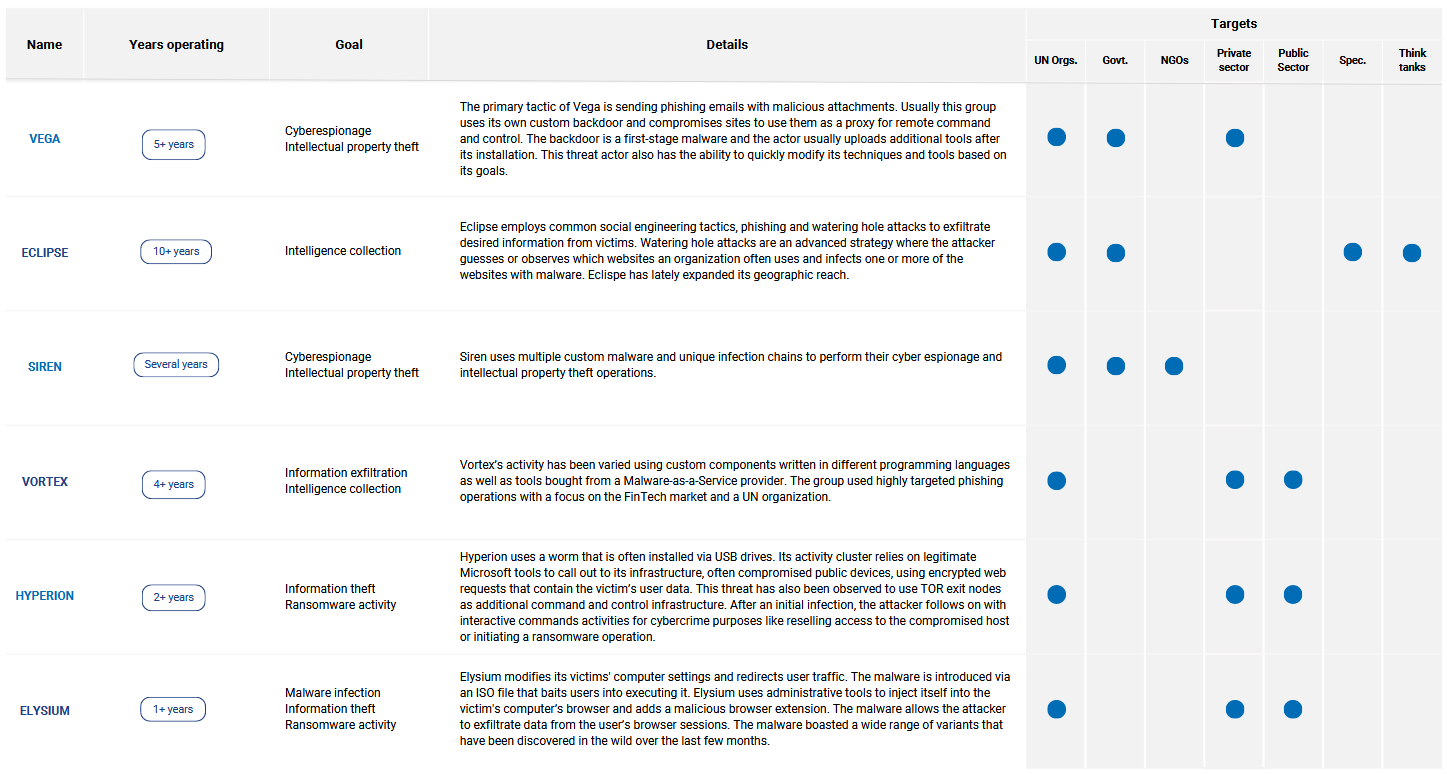
Cyberattacks on the UN: The United Nations International Computing Centre (UNICC) has published its yearly threats report [PDF] that details cyber-attacks on UN-associated organizations. The organization says that during 2022, its cybersecurity teams have discovered six new threat actors targeting one or more of its member organizations. This includes threat actors such as Vega, Eclipse, Siren, Vortex, Hyperion, and Elysium. While some are clear APTs, Hyperion seems to be the UN's name for EvilCorp and its Raspberry Robin USB malware.
APT29: Lab52 has a report on a recent version of QuarterRig, a malware strain linked to the Russian group APT29.
Vulkan leaks: Trustwave has an analysis of the VulkanFiles leaks, a collection of documents from Vulkan, a private firm contracted by the Russian Ministry of Defense to develop offensive cyber weapons. Mandiant and Sekoia also have write-ups on the leaks.
Lazarus: Security researcher Monty has a summary of all the TTPs typically associated with the Lazarus Group APT.
Kimsuky: AhnLab says it identified a Naver phishing site operated by the Kimsuky North Korean APT group.
APT37 (Reaper): South Korean security firm Genians has published a report on North Korean state-sponsored group APT37.
APT34's PowerExchange backdoor: Fortinet has identified a new backdoor named PowerExchange that is being installed on Microsoft Exchange servers. The malware was found on the Exchange server of a government entity in the United Arab Emirates. Fortinet linked the malware to Iranian state-backed APT34 based on "striking commonalities" between PowerExchange and the TriFive backdoor the group previously deployed on servers of Kuweiti government organizations years before.
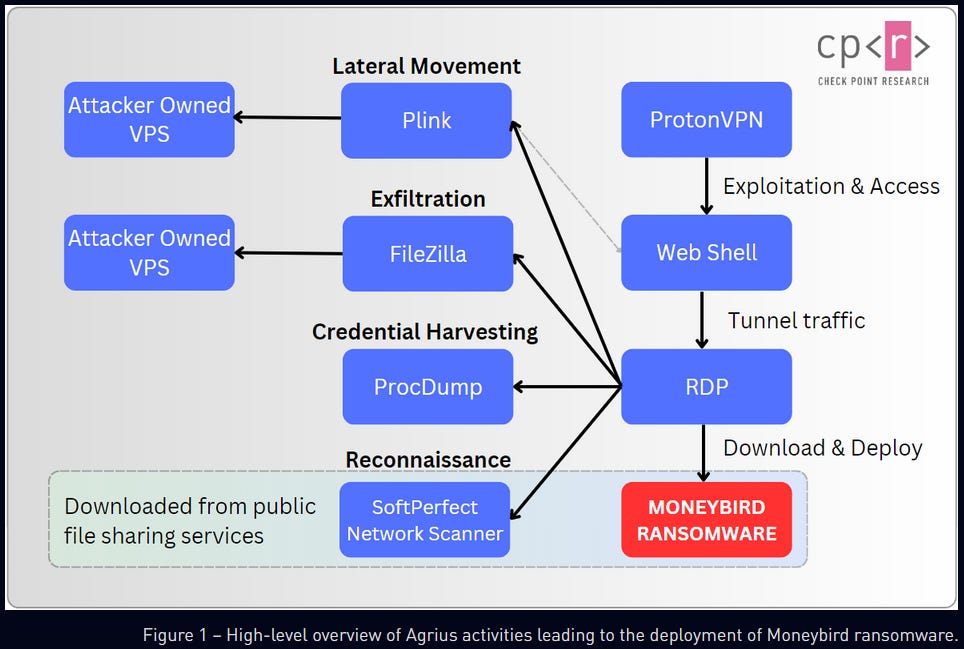
Agrius' Moneybird: A new ransomware strain named Moneybird has been deployed on the networks of Israeli organizations throughout the last months. Security firm Check Point says that while the attackers tried to present themselves as a mundane ransomware gang, they tied the intrusions to Iranian state-backed group Agrius. The group has a long history of breaching networks to collect intelligence and then deploying either ransomware or a wiper to hide its intrusions and disrupt the organization's activity. Also known as BlackShadow, the group has been linked [PDF] by Microsoft to Iran's Ministry of Intelligence and Security, or the MOIS.
Vulnerabilities and bug bounty
Expo vulnerability: Salt Security has discovered a vulnerability (CVE-2023-28131) in Expo, a popular framework used by many online services to implement OAuth support. The vulnerability allows threat actors to take over online accounts where OAuth logins are supported. In certain scenarios, threat actors can also perform actions on the user's linked account, such as Google, Facebook, and so on. Expo developers released a hotfix for the vulnerability on the same day of the report and have now announced plans to retire the module where the vulnerability was found.
GitLab vulnerability: GitLab has released a security patch for its software hosting and development platform to address a vulnerability tracked as CVE-2023-2825. GitLab says that "an unauthenticated malicious user can use a path traversal vulnerability to read arbitrary files on the server when an attachment exists in a public project nested within at least five groups." While the vulnerability sounds complicated to exploit, GitLab says it is critical and has "strongly recommend[ed]" that companies update their servers "as soon as possible." The vulnerability has also received a rare 10/10 CVSSv3 severity score, which should be enough to convince most companies to patch it ASAP.
Trezor hardware vulnerability: Cryptocurrency recovery company Unciphered says it found a "hardware vulnerability" that can allow it to recover seed phrases from Trezor T hardware crypto wallets. This is the same company that also used a similar hardware exploit to hack into OneKey hardware wallets earlier this year. Physical access to the hardware wallet is needed to exploit both bugs.
Windows vulnerability analysis: QiAnXin has published an analysis of CVE-2023-28252, a Windows zero-day patched in April 2023 by Microsoft that was exploited in the wild by the Nokoyawa ransomware.
GCP CloudSQL vulnerability: Dig Security has discovered a vulnerability in the Google Cloud Platform CloudSQL database service that can be used to escalate access from the CloudSQL user to full-fledged sysadmin on the entire GCP container. Google fixed the issue last month.
Zyxel security updates: American networking company Zyxel has released security updates this week to fix two vulnerabilities in its firewalls.
Zyxel exploitation: In the meantime, a Zyxel vulnerability (CVE-2023-28771) that was patched last month is being exploited in the wild by a Mirai DDoS botnet. The attacks come a week after security researchers released a proof-of-concept exploit for the bug.
Barracuda patches exploited zero-day: Barracuda Networks says that hackers used a zero-day vulnerability (CVE-2023-2868) to gain access to a subset of Email Security Gateway appliances. The company says it detected the attacks last Friday, May 19, and issued two separate patches over the weekend to address the issue, including one that was applied automatically to all appliances worldwide. In an incident status report, Barracuda says the vulnerability existed in a module that screens incoming email attachments. The company says its investigation was limited to its own products and urged customers to investigate their networks further for any possible post-intrusion activity.
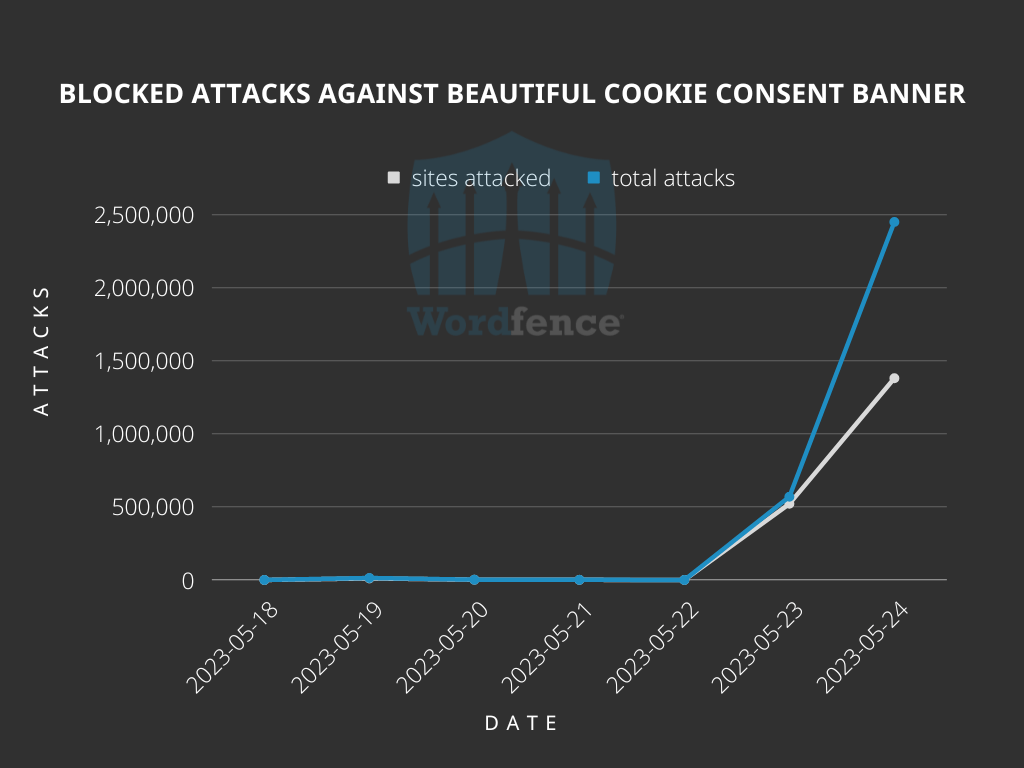
WP plugin exploitation: WAF service provider Wordfence is seeing an increase in attacks targeting WordPress sites using an old XSS vulnerability in the Beautiful Cookie Consent Banner plugin. Attacks targeting this plugin have exploded this week, and Wordfence says they appear to be the work of just one single threat actor.
"The vulnerability, which was fully patched in January in version 2.10.2, offers unauthenticated attackers the ability to add malicious JavaScript to a website, potentially allowing redirects to malvertizing sites as well as the creation of malicious admin users, both of which are appealing use cases for attackers."
Infosec industry
New tool—Code Credential Scanner: NCC Group has open-sourced a new tool named Code Credential Scanner that can detect hardcoded credentials or credentials present in configuration files within a repository.
New tool—CowCloud: NCC Group has open-sourced a new tool named CowCloud that can be used to run security tools like recons and vulnerability scanners in a distributed cloud infrastructure setup.
New tool—go-exploit: Security firm VulnCheck has open-sourced a new tool named go-exploit, the company's in-house exploit framework (obviously written in Go).
New tool—ACME API: Google has made the Google Cloud ACME API available for free to all customers. The API can be used to verify, manage, and automate their TLS certificate management operations.
Tool update—GUAC: Google has rolled out v0.1 of GUAC, a metadata synthesis and aggregation tool for security professionals.
Ransomware chats: LeMagIT reporter Valéry Rieß-Marchive has published a GitHub repo with ransomware-victim chats that have leaked online over the past years. It includes leaked chats from ransomware gangs such as LockBit, Hive, Darkside, BlackMatter, and others. The chats are also hosted online at ransomch.at.
JS for pen-testers guide: TrustedSec's Luke Bremer published a basics guide for using JavaScript for pen-testing.
Cyber insurance: Backup provider Veeam has published its ransomware trends report. Some of the main findings below:
- 77% of ransom payments were paid through cyber insurance
- 21% of surveyed organizations have recently found out that ransomware has been "specifically excluded" from their cyber insurance
- 74% of the survey's 1,200 respondents saw their insurance rates increase
- 10% saw their coverage benefits reduced
- 41% of organizations had a do-not-pay ransom policy
- 80% of respondents who suffered a ransomware attack also ended up paying
- one-in-four companies that pay the ransom don't actually manage to recover their encrypted data
Check Point mafia: Ross Haleliuk of Venture in Security has an interesting analysis on how initial investors and former Check Point alumni have gone to found more than 40 companies in the infosec space, creating the infosec equivalent of the "PayPal Mafia." Some of the security firms linked to early Check Point alumni include SentinelOne, Orca Security, Palo Alto Networks, Imperva, Cato Networks, and Illusive. Besides Check Point, there are also similar groups around network equipment vendors like Cisco and Juniper Networks, but in terms of cybersecurity startups alone, Check Point stands at the top. Ross' newsletter is also a must-subscribe for the infosec VC news space. [h/t Zach Allen]