Risky Biz News: MSS now dominates China's cyber activity
In other news: Russian hackers behind clever new Windows zero-day; Microsoft adds spoofing warning to Exchange; major breach at another data aggregator.

This newsletter is brought to you by Kroll. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Security firm Sekoia says most Chinese cyber operations are now conducted by China's Ministry of State Security. The ministry is one of the big three Chinese government bodies with offensive cyber capabilities, alongside the People's Liberation Army (PLA) and the Ministry of Public Safety (MPS).
MSS cyber activity has increased while the once-active Chinese military has slowed down considerably. Sekoia says MSS cyber operations have dominated since at least 2021.
Activity from PLA-linked APTs like BlackTech, Naikon, Tonto Team, and Tick has gone down, while more MSS-linked groups have emerged, such as APT10, APT31, APT40, APT41, Mustang Panda, and Lucky Mouse.
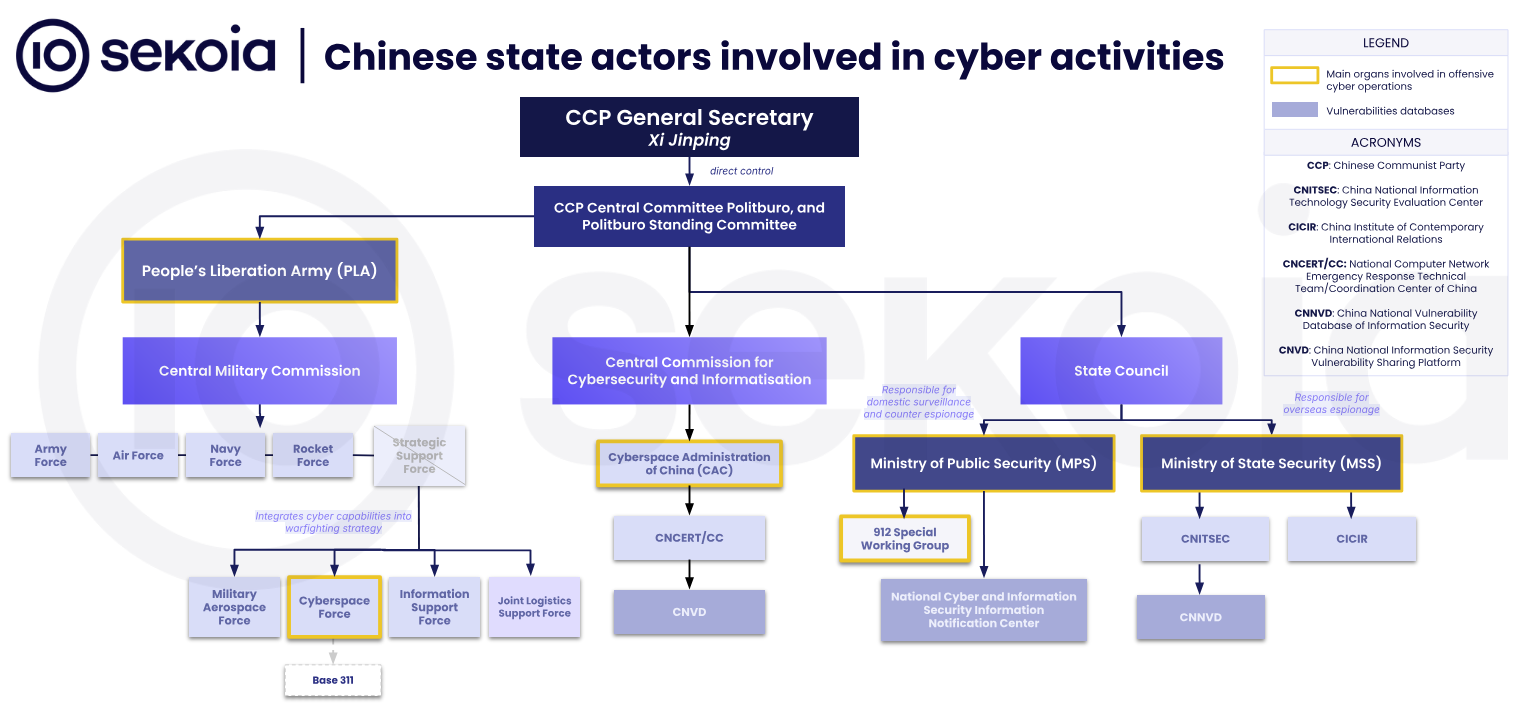
Sekoia says MPS activity is typically scarce because of the Ministry's priorities, which rarely intersect with the work of foreign cybersecurity firms.
The MPS, which is China's national police force, is usually involved in fighting crime and monitoring internet content. It is also known to track dissidents inside and outside the country, activity typically associated with the Poison Carp APT and the 912 Special Project Working Group, respectively.
New research suggests the MPS is also involved in influence operations in Southeast Asia and may have received help from QiAnXin, one of China's top cybersecurity companies.
The Sekoia report notes that recent reforms across the board in China appear to have granted more independence to both the PLA and the two ministries when it comes to cyber operations.
Operations are typically conducted via provincial-level agencies, which use their own local IT and hacker-for-hire contractors to achieve defined goals rather than rely on fully-employed staff.
The report also notes that some of these cyber contractors appear to have links to China's late 2000s and early 2010s hacktivist scene.
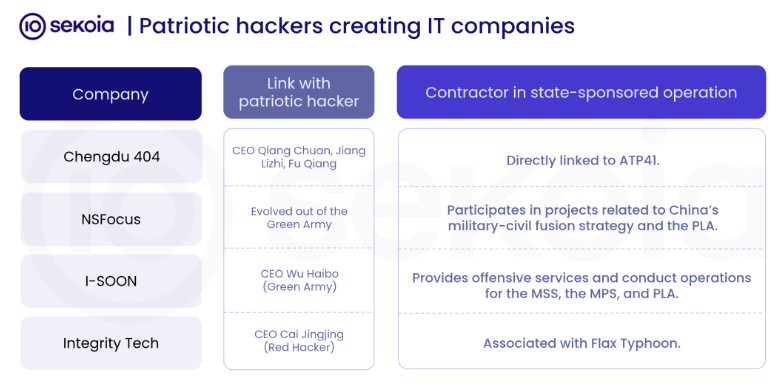
"When Xi Jinping came into power, he turned the principle of Military-Civil Fusion into a national strategy to make China a 'cyber powerhouse.' It led to major reforms of the PLA in 2015 and 2024 and the adoption of important laws regarding Chinese hackers and vulnerability disclosure, including the Notice on regulating the promotion of cybersecurity competitions or the RMSV. Chinese state-sponsored operations evolved towards more discretion and larger scales of targets. Attribution also became harder, with the appearance of new clusters of activity, while historical China-nexus APTs disappeared. APTs attributed to the PLA were less visible, while APTs related to the MSS, often relying on front companies or Chinese IT businesses, became most common in investigation reports."
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
PRC telco hacks update: The FBI and CISA have officially confirmed that the PRC hack of US telcos impacted the private communications of some US government officials and political figures. The hackers also copied "certain information that was subject to US law enforcement requests pursuant to court orders." The two (somewhat) statements confirm reports from US media that the hackers targeted both the Harris and Trump campaigns and sought information on which Chinese spies were under surveillance from US law enforcement. The FBI and CISA say they are notifying new victims as the investigation continues.
Hungary's defense procurement agency hacked: The INC ransomware group has hacked Hungary's defense procurement agency. Government officials confirmed the hack and said no classified data was compromised. Officials say the agency only manages plans and data about military procurement. [Additional coverage in Reuters]
Spanish lawyer sues NSO over hack: A Spanish lawyer has sued Israeli spyware vendor NSO Group for allegedly hacking his phone. The lawsuit was filed in a Barcelona court this week and also names NSO's founders and the executive of two NSO affiliate companies. Lawyer Andreu Van den Eynde claims he had his phone infected with NSO's Pegasus spyware due to his involvement in the Catalan independence movement. Van den Eynde was one of the lawyers advising Catalan political figures involved in the region's independence referendum. [Additional coverage in TechCrunch]
DemandScience leak: The personal data of almost 122 million users has been leaked online after it was sold on hacking forums earlier this year. According to security researcher Troy Hunt, the data originated from DemandScience, a data aggregation and enrichment service owned by Pure Incubation. The company confirmed the hack and claimed the data was taken from a now-decommissioned system. The data includes names, business addresses, emails, telephone numbers, and social media links.
General tech and privacy
Ads coming to Threads: Meta is expected to introduce paid advertising on its Threads micro-blogging platform at the start of next year, via The Information.
PyPI now supports digital attestations: The Python Package Index (PyPI) has rolled out support for digital attestations. The new system will replace the traditional PGP signatures, which PyPI has used to verify the authenticity of Python libraries for almost 20 years. Digital attestations are signed by a third party, while older PGP signatures rely on cryptographic key pairs. PyPI says several projects have already switched to the new system and more than 20,000 attestations have been published already. Support for digital attestations was co-developed together with security firm Trail of Bits.
New Android scam detection goes live: Google is rolling out a new Android security feature that listens to calls and warns of possible scams. The feature was announced earlier this year at the Google I/O conference.
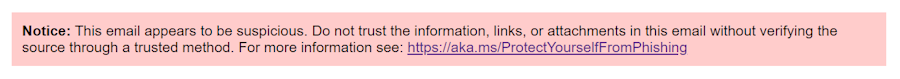
Microsoft adds spoofing warning to Exchange: Microsoft will prepend a red warning at the top of each email message that appears to be using a spoofed email address. The new warning is enabled by default for all Exchange servers running the November 2024 security patches. It is the result of a security patch that fixes an email spoofing attack (CVE-2024-49040) disclosed in May this year.
Government, politics, and policy
Russian CDN ban to expand: In a Telegram post, Russian officials said they plan to expand Russia's ban on foreign web hosting providers that host content that discredits the glorious RuSsIaN aRmY. Akamai and CDN77 may soon find themselves on the list.
Another Russian internet disconnection test: Russia's internet watchdog announced it plans to run another test this December and disconnect the country from the global internet. [Additional coverage in TASS]
EU tells Apple to stop geo-blocking users: An EU consumer protection agency has told Apple to stop geo-blocking EU users based on their country of origin (where the Apple account was initially registered). The Consumer Protection Cooperation Network says Apple's geo-blocking is illegal under multiple EU laws, such as the DSA and DMA. Both laws mandate that EU users be treated the same regardless of their home country.
Sponsor Section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with George Glass, Senior Vice-President for Kroll's Cyber Risk business. George covers the company's latest report, a Kimsuky attack on ConnectWise ScreenConnect devices with a new malware strain named ToddlerShark.

Arrests, cybercrime, and threat intel
WazirX hack suspect detained: Delhi police have arrested a man from West Bengal for his alleged role in the massive hack of Indian cryptocurrency exchange WazirX. Officials say SK Masud Alam created an account on WazirX under a false name. The account was then sold on Telegram and used to execute the attack. The company was hacked in July and lost over $230 million worth of crypto assets. The hack is this year's second-largest crypto-heist. [Additional coverage in the Times of India]
Crypto investment scammers detained in ROK: South Korean authorities have detained 215 suspects linked to a major cryptocurrency investment scheme. The group operated as an investment firm that created and sold 28 cryptocurrency tokens. It was led by a YouTuber who advertised the tokens on his channel and used a team of marketers to push prices in a classic pump-and-dump scheme. Officials say the group defrauded investors of almost $230 million. The group's leader fled to Australia but was also arrested and extradited back to South Korea. [Additional coverage in The Guardian]
Crypto investment scammer pleads guilty in the US: A foreign national has pleaded guilty in the US for laundering the proceeds of cryptocurrency investment scams. Officials say Daren Li laundered over $73 million through a web of shell companies and international bank accounts. He now faces up to 20 years in prison for his crimes.
Tax preparation firms hackers charged: The Justice Department has charged two Nigerien men with allegedly hacking tax preparation firms across the US. Officials claim Matthew Akande and Kehinde Oyetunji stole taxpayer information from the companies and filed fraudulent tax returns in their names. The duo filed $8.1 million worth of fraudulent tax refunds and successfully obtained over $1.3 million over a period of five years.
Serial swatter pleads guilty: A US teen has pleaded guilty to orchestrating hundreds of bomb threats and swatting attacks across the US last year. Alan Filion, from Lancaster, California, swatted and sent bomb threats to hundreds of schools, politicians, courthouses, and religious institutions. Officials described the 18-year-old as one of the most prolific swatters in American history. According to Wired, he also operated Torswats, a Swatting-as-a-Service operation hosted on Telegram.
Hacker Lifelock sentenced to 10y in prison: A US judge has sentenced an Idaho man to 10 years in prison and three years of supervised release for hacking the city of Newnan and a medical clinic in Griffin, Georgia. Robert Purbeck also attempted to extort a Florida orthodontist, threatening to publish the personal data of their patients. Purbeck went online under the hacker name of Lifelock. He was also ordered to pay over $1 million in restitution to his victims.
Infostealers updates: Red Canary looks at how some infostealer families have bypassed Chrome's new app-bound encryption. We covered this here, but the Red Canary report goes into the technical details.
Fake IP checkers on npm: Sonatype has found three npm packages posing as fake IP checkers that infected JS developers with cryptocurrency stealers.
Group Laski attacks: SanSec researchers say that more than 3,000 online stores were hacked and infected with an e-skimmer developed by a threat actor known as Group Laski.
SilkSpecter: EclecticIQ looks at a Black Friday-themed phishing campaign from the SilkSpecter group. The campaign aimed to lure visitors on fake stores and collect their card data. Yep, it's that season again! Get ready for the holiday sales spam!
Sitting Ducks domains: Infoblox says it found over 70,000 domains that were hijacked using the Sitting Ducks attack. Victim domains include well-known brands, non-profits, and government entities. At least four threat actors are involved in the attacks. The domains are now being used to host investment scams, phishing sites, and redirect malicious traffic. Up to 800,000 domains are known to be vulnerable to Sitting Ducks, a DNS attack that allows threat actors to hijack misconfigured domains.
DPRK worker scheme: Palo Alto Networks has its own report and TTPs on the DPRK IT worker scheme.
Snail mail leads to malware: Switzerland's cybersecurity agency warns that threat actors are using physical letters to send malicious QR codes to Swiss citizens. The letters claim to be from the country's meteorology agency and urge users to install its new weather app. The QR code leads victims to download and install an Android app infected with Octo2 (Coper), a known banking trojan.

Malware technical reports
ShrinkLocker decrypter: Bitdefender researchers have released a free decrypter for the ShrinkLocker ransomware. The ransomware has been active since May and is one of the rare strains that use the Windows BitLocker to prevent users from accessing their systems. The decrypter allows victims to recover the BitLocker key set up by the ransomware and regain control over their data and PCs.
Black Basta ransomware: CyFirma has published IOCs and TTPs from Black Basta ransomware attacks.
Cloud ransomware: SentinelOne looks at three ransomware strains that target cloud infrastructure, such as IndoSec, Pandora, and RansomES.
HawkEye: ANY.RUN has published a technical analysis of HawkEye, a keylogger also known as PredatorPain that has been around since 2010.
PHP Reinfector and Backdoor: Sucuri has published a report on a PHP script used as a backdoor and persistence mechanism. Seems to be related to the VexTrio operation/
Strela Stealer: IBM X-Force has published a report on Strela Stealer, an infostealer used by Hive0145, a financially motivated initial access broker (IAB). The group primarily targets Spain, Germany, and Ukraine.
"Strela Stealer is a malware designed to extract user email credentials stored in Microsoft Outlook and Mozilla Thunderbird, potentially leading to Business Email Compromise (BEC)."
Sponsor Section
Kroll has investigated many different tactics that threat actors use to steal consumer data on e-commerce sites. These types of attacks can be especially damaging for organizations that are responsible for storing customers' personal and financial information that is collected during transactions. Read more about Kroll's prevention tips and security best practices.

APTs, cyber-espionage, and info-ops
Windows zero-day linked to Ukraine attacks: One of the zero-days (CVE-2024-43451) patched this week by Microsoft was used in a Russian hack of Ukrainian organizations earlier this year. According to security firm ClearSky, the zero-day was part of an exploit chain that exposed Net-NTLM hashes when victims to interacted with .url files received via phishing emails. ClearSky said that right-clicking, deleting, or moving the file established a connection with the attacker's server, exposing authentication data. The report suggests that the campaign also used social engineering to convince victims to run an executables. Ukraine's CERT linked the attacks to a group named UAC-0194.
OPSEC fail links Doppelganger to Russian MOD IPs: A joint Qurium and Correctiv investigation has found an OPSEC mistake in Doppelganger infrastructure that links the group to the Russian Ministry of Defense. Researchers say they found login details for Doppelganger infrastructure from IPs operated by Voentelekom, a Russian ISP owned by the Russian government and a subordinate to the Ministry of Defense. In addition, Qurium says the Doppelganger group has also used a cybercrime service named VexTrio to take legitimate visitors from hacked sites and redirect them to their propaganda portals.
New PXA Stealer: Cisco Talos has discovered a new suspected APT malware strain named PXA Stealer that was used in cyber-espionage attacks against government and education entities in Europe and Asia. Talos researchers say the malware is operated by a Vietnamese-speaking group and appears to have connections to the CoralRaider APT.
Emennet Pasargad's WezRat: Check Point has published a technical analysis of WezRat, an infostealer used by Iranian group Emennet Pasargad.
"The latest version of WezRat was recently distributed to multiple Israeli organizations in a wave of emails impersonating the Israeli National Cyber Directorate (INCD). WezRat can execute commands, take screenshots, upload files, perform keylogging, and steal clipboard content and cookie files. Some functions are performed by separate modules retrieved from the command and control (C&C) server in the form of DLL files, making the backdoor's main component less suspicious."
Lazarus: Group-IB has published a report analyzing a new Lazarus APT technique of concealing malicious code in file metadata extended attributes in order to evade detection in macOS systems.
APT41: BlackBerry looks at APT41's LightSpy campaign, which saw a resurgence this year. New stuff includes:
- A new modular malware framework (DeepData v3.2.1228)
- 12 specialized plugins for comprehensive data theft
- Enhanced cross-platform surveillance capabilities
- Sophisticated command-and-control infrastructure
- Strategic targeting of communications platforms
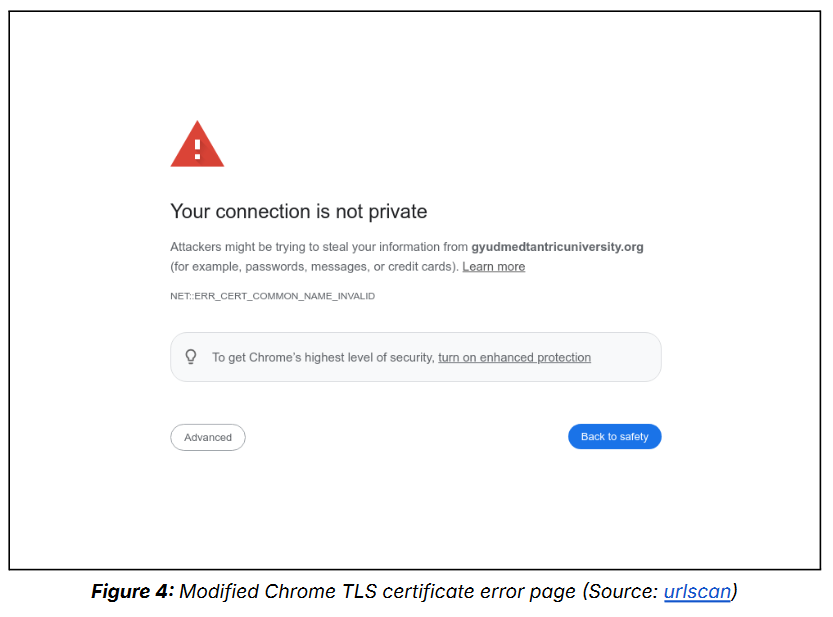
TAG-112 spies on Tibet: A Chinese cyber-espionage group named TAG-112 has compromised two local Tibetan websites to deliver Cobalt Strike to the site's visitors. The group used malicious JavaScript code to spoof a TLS certificate error and trick visitors into downloading a security certificate containing a Cobal Strike implant. Recorded Future believes the group is a smaller section of a larger group known as Evasive Panda (TAG-102).
Vulnerabilities, security research, and bug bounty
Jenkins security updates: The Jenkins project has published seven security updates for the project's core files.
PAN security updates: Palo Alto Networks has released nine security updates.
WhatToExpect app vulnerabilities: Security researcher Ovi Liber has discovered multiple vulnerabilities in the WhatToExpect fertility app that can be used to expose users' sensitive personal and reproductive health information.
RoboPAIR: A team of academics has developed RoboPAIR, a tool to hack LLM-controlled robots.
FortiJump Higher: watchTowr Labs has discovered a new EoP vulnerability that can be used with the Fortinet FortiManager FortiJump vulnerability. This one they appropriately named FortiJump Higher.
PostgreSQL Perl vulnerability: Varonis researchers have discovered a vulnerability in the Perl language extension of the PostgreSQL database. Tracked as CVE-2024-10979, the vulnerability allows unauthenticated threat actors to modify sensitive environment variables. Varonis says the vulnerability can be used to enable code execution attacks on the underlying OS or run queries against the database.
KEV update: CISA has updated its KEV database (twice) with seven vulnerabilities that are currently exploited in the wild. This includes the two Windows zero-days from this week's Patch Tuesday, two PAN bugs, and bugs in Metabase GeoJSON, Cisco ASA, and Atlassian Jira.
Exploitation waves: The Shadowserver Foundation reports seeing active attacks against two vulnerabilities disclosed this week. This includes attacks against D-Link NAS devices and Citrix Virtual Apps and Desktops.
NIST backlog update: US NIST says it updated the NVD dataset to include information on all actively exploited vulnerabilities that were reported this year. The agency says it's still dealing with a huge backlog of CVEs that don't include any metadata. The agency says it underestimated the size of the backlog and is unlikely to have everything up to date by the end of the year. NIST developed a backlog for new NVD entries in February. It promised in May to have it fixed by the end of September, which it clearly failed.
Infosec industry
Acquisition news #1: DevSecOps platform Snyk has acquired AppSec testing company Problely.
Acquisition news #2: Cyber risk management company Bitsight has acquired threat intel provider Cybersixgill. The acquisition is a nine-figure deal.
New tool—BlindBrute: Security researcher c3ll has released BlindBrute, a customizable Python tool designed for blind SQL injection attacks.
New tool—ShadowDumper: Security researcher Usman Sikander has released ShadowDumper, a tool used to dump LSASS memory.
Threat/trend reports: Akamai, AuditBoard, Google Mandiant, IANS, and ReliaQuest have recently published reports and summaries covering various infosec trends and industry threats.
POC 2024 slides: Slides from the POC 2024 security conference, which took place earlier this month, are now available on the conference's website.
Black Alps 2023 videos: Talks from the Black Alps 2023 security conference, which took place last November, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how ungoverned spaces on Telegram result in increasingly toxic and antisocial communities.
In this podcast, Tom Uren and Patrick Gray talk about what to expect from President Trump's second term. Trump is an activist president who believes in using state power, so intelligence agencies will be pushed to conduct more audacious or even outrageous covert operations.




