Risky Biz News: Move aside RowHammer, the RowPress attack is here
In other news: Volt Typhoon observed exploiting Zoho ManageEngine systems; Polish stalkerware company gets hacked; and encrypted messaging apps are often very confusing.
This newsletter is brought to you by application allowlisting software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Back in 2014, a new attack named RowHammer upended the memory market and forced chip makers to rethink how they were manufacturing and what type of security features they were baking into DRAM chips.
The RowHammer attack—and all its variations—used super-fast read-write operations directed at a row of memory cells inside a DRAM chip to generate electrical disturbances that altered or corrupted data in nearby rows.
Throughout the years, chip vendors started placing memory rows at larger distances between each other and added software-level protections to detect when apps were accessing memory rows at super-high rates.
This would have been all fine and dandy, but in new research published earlier this month, a team of academics from Swiss university ETH Zurich has described an alternative to RowHammer—a new attack they named RowPress.
Unlike RowHammer, this attack works by accessing a row of memory cells and then just keeping it open for a long period of time.
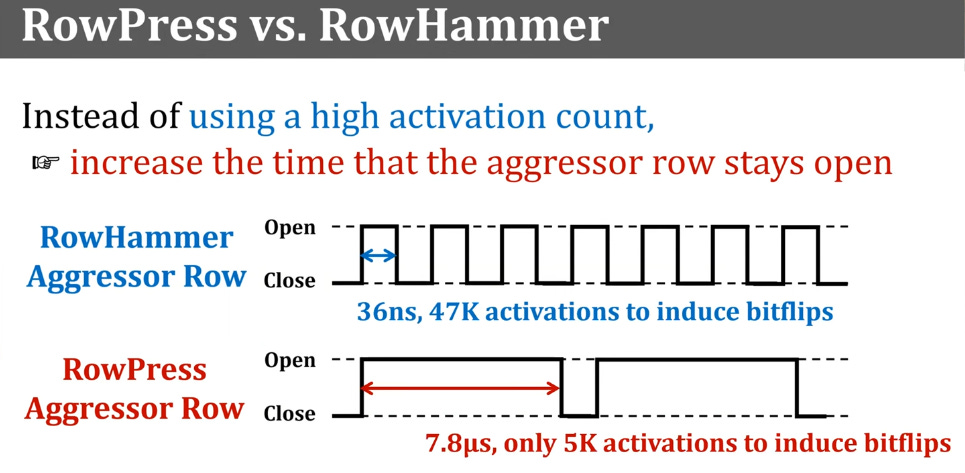
The research team says this is unnatural behavior for the memory cells, which end up causing bit-flips in nearby cells, just like in a classic RowHammer attack. There are also some extreme cases where bit-flips occur in a DRAM row just after one activation.
Because RowPress doesn't need to execute super-fast read-write operations, RowHammer software protections don't apply.
The attack also becomes more efficient as the chip's temperature increases.
Researchers say they tested the new RowPress attack with 164 DDR4 DRAM chips from all three major vendors—Samsung, SK Hynix, and Micron—and all were vulnerable.
Although the research sounds grim, the team says the attack can be easily mitigated at the software level by limiting the amount of time a memory row can stay open.
The full RowPress paper is available here [PDF], and the code to reproduce the attack is available on GitHub.
Breaches, hacks, and security incidents
Petro-Canada incident: Canadian energy company Suncor says a cyber-attack has hit the systems of its gas station chain Petro-Canada. The incident took place on Friday, June 25, and has impacted the company's website and mobile apps. It also impacted its payment systems, and customers have had to pay cash since the attack. The incident is suspected to be a ransomware attack. Suncor was ranked as the 48th-largest public company in the world in 2020. [Additional coverage in CBC]
University of Hawaii ransomware attack: The University of Hawaii has confirmed that its Community College was the target of a ransomware attack.
Medibank hack: Australia's financial regulator APRA has told private insurance provider Medibank to add an extra AUD$250 million (US$167 million) to its capital in the aftermath of the company's October 2022 security breach. The new capital will have to be established by July 1, 2023. It will serve as an operational risk charge and will have to remain in place until APRA deems Medibank has taken steps to strengthen its security environment and data management. The personal and healthcare data of more than 9.7 million Australians was stolen by the REvil ransomware group in an attack last year, marking one of the largest security breaches in Australia's history.
Chibi Finance crypto-heist: The operators of the Chibi Finance crypto platform appear to have deployed a malicious smart contract that stole more than $1 million worth of tokens from their users. Commonly referred to as a "rug pull," the incident led to the CHIBI token losing 98% of its value. According to CoinDesk, the stolen funds were quickly laundered over the weekend through several exchanges.
LetMeSpy hack: Polish stalkerware company LetMeSpy has been hacked, and its data published online. The company makes an Android app that can be side-loaded on modern smartphones and track calls, SMS messages, and the phone's location and movement. The incident exposed information on all LetMeSpy customers, such as names and email addresses. It also exposed data each customer had collected from infected devices. The contents of the dumped SMS messages reveals the typical spying in abusive relationships, but also drug trades and credentials for various online accounts. Based on the leaked data, the company had more than 26,000 paying customers. [Additional coverage in Niebezpiecznik/English coverage in TechCrunch]
RFID scanners in Formula E: The DS Penske Formula E team has been caught using an RFID scanner that grabbed live car and tire data from rival teams. The scanner was installed at the pitlane entry during a free practice session ahead of the Portland E-Prix that took place over the weekend. The team was fined €25,000—a record for the Formula E championship. Its two pilots were also forced to start from the pitlane in for the race. RFID scanners are commonly used in stores and other industries but are considered illegal in modern motor racing, where usage of such devices is considered cheating and hacking. [Additional coverage in The Race]
MOVEit hacks: The victim count has now gone over 100 with the addition of Siemens Energy, Schneider Electric, Calpers, Genworth, and UCLA.
General tech and privacy
Passkeys support in Windows 11: Microsoft is working on adding a new section in the Windows 11 control panel that will let users manage their passkeys. The feature is currently being tested in Windows 11 Insider Preview builds and should be available at Settings > Accounts > Passkeys.
RIP Windows: Microsoft's plans for its Windows OS have leaked in an ongoing court case, and the company is apparently preparing to move the home userbase of its Windows OS to a cloud-based deployment model it currently uses for its business-focused Windows 365 OS. No deadline has been set for this, but be ready to kiss your locally-installed OS goodbye in the coming years. That or be prepared to painfully migrate to Linux. [Additional coverage in The Verge]
GKE security dashboard: The Google Kubernetes Engine (GKE) Security Posture dashboard is now generally available for all Google Cloud customers. The dashboard is a new UI to help organizations track their cloud environment's security posture. It includes tools to detect common misconfigurations, scan for vulnerabilities, and automatic security bulletin surfacing. Many of the dashboards new security features have also been enabled by default when deploying new clusters.
"Now that the Security Posture dashboard is generally available, we're turning on baseline Security Posture capabilities such as configuration audits and security bulletin surfacing for newly-created clusters.
For new GKE Autopilot clusters, we're also enabling container OS vulnerability scanning by default. Since GKE Autopilot leverages Google Cloud-managed system components, you won't be billed for any of the compute resources this feature uses."
CISA cloud guidance: The US Cybersecurity and Infrastructure Agency has released guidance documents as part of the Secure Cloud Business Applications (SCuBA) project. The first is a security guide that agencies can use to adopt technology for cloud deployment, adaptable solutions, secure architecture, and zero-trust frameworks. The other is a visibility framework guidebook for identifying and mitigating threats in common cloud environments and cloud services.
Flipper Zero sales: The company behind the Flipper Zero hacking devices is on track to sell $80 million worth of products by the end of the year. The figure is more than three times the $25 million worth of devices the company sold in 2022. The devices are typically used by security researchers but they have also been adopted by criminal groups. They were banned from import into Brazil earlier this year and are regularly removed from Amazon stores.
QNAP retires PhotoStation: Taiwanese NAS vendor QNAP will retire its PhotoStation app on October 1, 2023. Users are advised to uninstall the app, which was often targeted by ransomware gangs. These attacks will most likely increase once the app stops receiving security updates this fall. This might also be a good time to read the company's security guide too.
Encrypted messengers are confusing: An 86-page study of modern secure and encrypted messaging apps has concluded that the apps often use confusing and complicated user interfaces that negate many of their features. The study analyzed apps such as Signal, WhatsApp, Telegram, Google Messages, Apple Messages, and Facebook Messenger. Researchers found that unless the app enforces end-to-end encryption by default, most users may not be able to tell if they're having a secure conversation. The study found that very few users understood the difference between using terms like "secret" or "private chat" or the different color schemes used by iMessage and Google Messages to show if the conversation is encrypted or not. The research found that Signal was the only app they analyzed that took steps to protect its users, such as hiding contacts, metadata, and sender information.
Government, politics, and policy
The Netherlands unifies cybersecurity agencies: The Dutch government has unified its three cybersecurity agencies into one larger body. The process will merge the staff and resources of the National Cyber Security Center (NCSC) with the Digital Trust Center (DTC) and the Computer Security Incident Response Team for digital service providers (CSIRT-DSP). The new unified agency will operate under the Dutch Ministry of Justice and Security. The unification process is set to complete by January 1, 2026. The name of this new agency has not been announced yet.
Changes to EU cybersecurity regulations: EU political camps have reached an agreement and will support the passing of a set of new cybersecurity regulations proposed in March 2022. According to the proposed regulation, all EU bodies will have to adopt a cybersecurity risk and government framework, conduct regular cybersecurity assessments, and share data on cybersecurity incidents with CERT-EU without any delay. The same legislation will also have CERT-EU renamed as the EU Cybersecurity Centre.
Israel's Shin Bet uses AI: Shin Bet director Ronen Bar says the agency has incorporated AI technology in its daily workflow and has successfully spotted a "not-inconsequential number of threats" already. Bar says the new AI toolkits have flagged anomalies in surveillance data and are helping agents sort through "endless" intelligence streams. [Additional coverage in Reuters/non-paywall]
Canada passes Online News Act: The Canadian government has passed the Online News Act, a new law that will force online services to pay Canadian news agencies for links to their articles. As a result of the new law, Meta has pulled news content from its Facebook and Instagram services in Canada. No statement from Google, but the company is expected to pull its news section as well.
The GOP is mad at CISA: The GOP-controlled House Judiciary Committee and the—I kid you not, something like this actually exists—Select Subcommittee on the Weaponization of the Federal Government have published a report on how CISA "colluded" with big tech to "to surveil and censor Americans' speech on social media." Let me translate this for you. The GOP is mad because CISA debunked their "election was stolen" claims back in 2020. You know this report is pure partisanship garbage and a PR stunt when it cites the "Twitter Files" as its source. The entire report also mysteriously keeps using the term "viewpoints" instead of "proven election lies"—but sure, you do you, GOP!
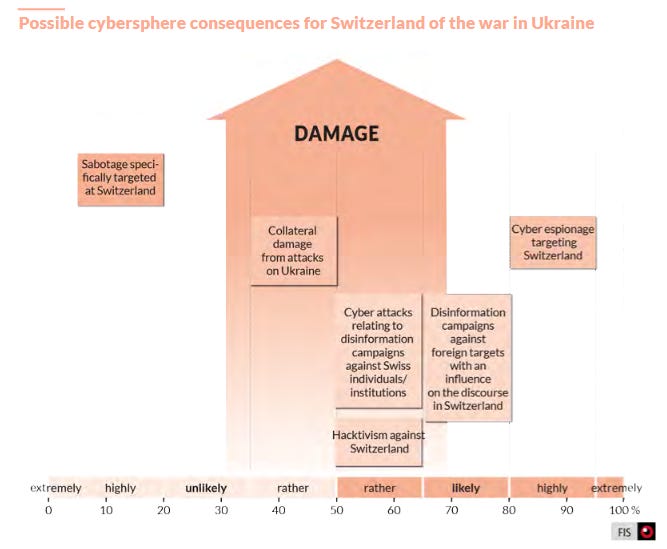
Swiss intelligence report: The Swiss federal government has published its annual intelligence and espionage threat report [PDF]. Cyber count: a lowly 20.
Sponsor section
In this sponsored Soap Box podcast, Patrick Gray talks to Airlock Digital co-founders Daniel Schell and David Cottingham about living off the land. The recent Volt Typhoon report out of Microsoft chronicled the adventures of a Chinese APT crew in US critical infrastructure. But one of the most fascinating aspects of the Volt Typhoon campaign was that the attackers almost exclusively used so-called living off the land techniques.
Cybercrime and threat intel
Silver Fox: Chinese security firm Weibu says the Silver Fox cybercrime group they have been monitoring since September 2022 has switched from SEO poisoning attacks to classic email phishing operations. The group specifically targets Chinese businesses. Their typical payloads are open-source remote access trojans such as Gh0st RAT and AsyncRAT.
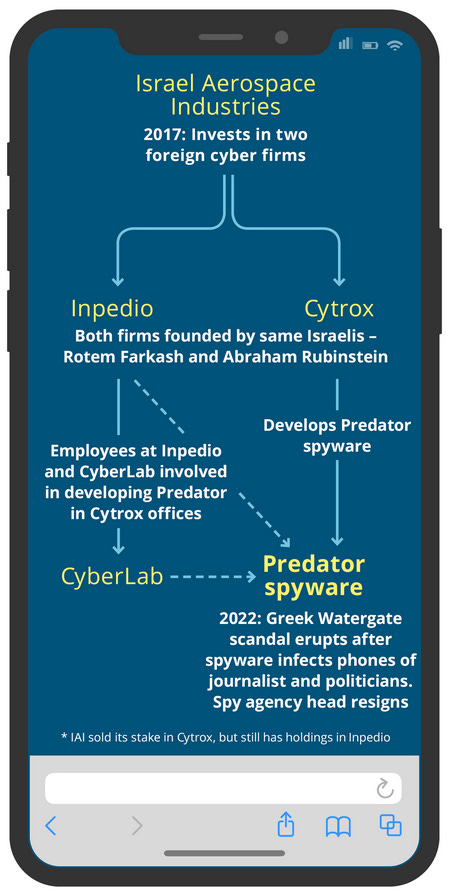
Spyware industry: A Haaretz investigation has discovered that two Israeli nationals named Rotem Farkash and Abraham Rubinstein are behind both Cytrox and Inpedio, two companies linked to the development of the Predator surveillance platform. Former Cytrox workers told Haaretz the two firms initially operated from the same Skopje offices, and Inpedio also helped with the development of Predator, although today, only Cytrox's name is associated with the spyware. The Predator spyware is widely known for its use inside Greece in a political spying scandal known as Predatorgate, and is at the center of a EU investigation.
DarkForums hack: The DarkForums cybercrime forum has allegedly been hacked, and its user database was published on BreachForumsVC. In your typical hacker forum drama, both sites are now offline.
Styx Market: Threat intel firm DarkOwl has a profile on the Styx dark web marketplace. The site has a focus on financial crime, being often used to sell hacked accounts, card data, RDP access, malware, and more.
ITG23 crypters: The IBM X-Force security team says that even if the ITG23 (Conti/Trickbot) group disbanded last year, its malware crypting tools are still used across the underground ecosystem. Five of the former group's 13 crypters are still alive and widely used by some of today's largest cybercrime cartels. The list includes the likes of Emotet, IcedID, Qakbot, Bumblebee, Gozi, SVCReady, CargoBay, Matanbuchus, Pikabot, Aresloader, Vidar, Minodo, and LummaC2 Stealer. Former ITG23 members have also developed two new crypters named Snow and Forest, which are slowly gaining ground and name recognition.
BOD 23-02 exposure: Internet scanning service Censys has discovered more than 1,300 federal systems that have management interfaces exposed on the internet. Exposed devices include Cisco networking devices, Cradlepoint router management systems, and Fortinet and SonicWall firewalls. These systems fall under BOD 23-02, a CISA directive issued earlier this month that mandates federal civilian agencies remove the management panels of these devices from the internet.
Another warning for law firms: After the UK NCSC warned law firms to boost their cybersecurity defenses last week, France's ANSSI intelligence agency issued a similar alert this week. Potential threats include your typical ransomware attacks but also espionage campaigns, typically conducted by mercenary hackers hired by litigation rivals looking to keep an eye on their opposition.
Open redirect phishing campaign: SilentPush has uncovered a massive phishing campaign that uses open-redirect vulnerabilities in the subdomains of legitimate services. The threat actor uses subdomains from legitimate email marketing services to manipulate URLs and redirect traffic to their own malicious infrastructure.
Hacked Bitrix servers used in phishing ops: Russian cybersecurity firm CyberOK [PDF] says that Bitrix CRM servers belonging to Russian companies were defaced and used to host phishing sites. The attacks took place at the end of May and appear to be a continuation of the same campaign spotted by PIXM researchers in March 2023 and before that at the end of 2022. The attacks exploited the same vulnerability, tracked as CVE-2022-27228.
npm malware: Phylum has a report on 31 malicious libraries uploaded on the npm repository. The purpose of the packages appears to be to download and run some mysterious and yet-to-be-identified payload.
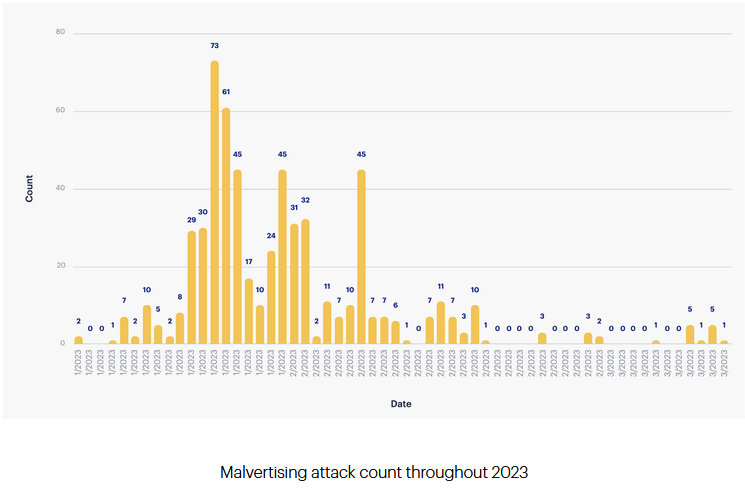
Malvertising campaigns in 2023: More than 800 malvertising campaigns have taken place in 2023 so far. According to a new Malwarebytes report, many of these campaigns are often hosted by Google Search ads. In most cases, the campaigns deliver infostealer and malware strains such as Aurora, BatLoader, and IcedID.
Malware technical reports
SALTWATER: Security researcher Vlad Pasca has published a technical analysis of the SALTWATER backdoor used in the Barracuda zero-day vulnerability (CVE-2023-2868) exploitation.
GootLoader: ReliaQuest has published a report from a May 2023 infection with the GootLoader malware that led to a later infection with the SystemBC RAT.
ThirdEye infostealer: Fortinet researchers analyze a previously unseen infostealer named ThirdEye.
"While this malware is not considered sophisticated, it's designed to steal various information from compromised machines that can be used as stepping-stones for future attacks."
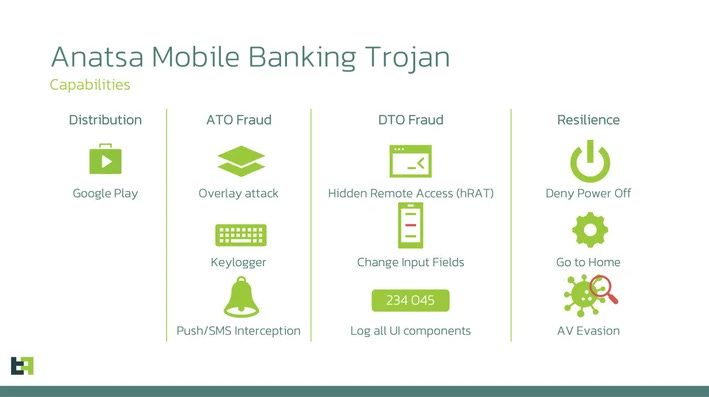
Anatsa: Mobile security company ThreatFabric says it has found five Android apps available on the official Play Store deploying the Anatsa mobile banking trojan. The apps have been downloaded and installed more than 30,000 times. They have been live since March 2023. ThreatFabric says this new Anatsa campaign comes after a period of more than six months of inactivity from the group. The Anatsa trojan has been active since 2020 and is a dangerous and well-developed mobile banking trojan.
Risky Business Demo
Airlock Digital is one of this newsletter's supporters and this week's featured sponsor. Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
APTs and cyber-espionage
Lazarus: Qihoo 360 researchers have observed the Lazarus APT use a file posing as the ComcastVNC app to deploy its BlindingCan malware.
Vanguard Panda (Volt Typhoon): CrowdStrike has published additional information on Volt Typhoon, a Chinese cyber-espionage group that was recently observed hacking US critical infrastructure entities and preparing for possible destructive attacks. While initial reports from CISA and Microsoft say the group leveraged Fortinet devices for initial access, CrowdStrike says it also saw the group repeatedly use Zoho ManageEngine Self-Service Plus exploits to breach networks. CrowdStrike tracks this group as Vanguard Panda.
GhyamSarnegouni (Rise to Overthrow): CyberScoop's AJ Vicens has a good profile on GhyamSarnegouni (Rise to Overthrow), the anti-Iranian and pro-MEK hacktivist group.
Vulnerabilities, security research, and bug bounty
Grafana auth bypass: The Grafana project has released a security update to fix an account takeover and authentication bypass vulnerability (CVE-2023-3128). The vulnerability allows an attacker who runs their own Azure AD multi-tenant app to create an account with the victim's email address and then use OAuth to hijack the victim's legitimate Grafana account.
LearnDash LMS vulnerability: A vulnerability (CVE-2023-3105) in the LearnDash LMS WordPress plugin can allow threat actors to reset the password for the WordPress admin account. The plugin is installed on more than 100,000 sites.
ASUS security updates: Taiwanese hardware vendor ASUS has released a security update to fix a vulnerability in its 4G-N16 modems that allowed attackers to brute-force the PIN for the WiFi Protected Setup (WPS).
Mockingjay technique: Security Joes have published details on a new process injection technique they're calling Mockingjay.
Infosec industry
Cyber Threat Alliance expands: The Cyber Threat Alliance, a nonprofit organization working to improve the cybersecurity of the global digital ecosystem, has expanded its ranks with CyberCX.
New tool—DNS Analyzer: SEC-Consult has open-sourced a new tool named DNS Analyzer, a Burp Suite extension for discovering DNS vulnerabilities in web applications.
New tool—actions-permissions: GitHub's security team has open-sourced a tool named actions-permissions that can monitor GitHub Actions workflows and then recommend the minimum permissions required to run them so Actions don't have too much broad access to your code.
New tool—SNAPPY: Security firm Trustwave has open-sourced a tool named SNAPPY that can detect rogue or fake WiFi wireless access points.
New tool—ParaForge: Security researcher Sourav Kalal has open-sourced ParaForge, a Burp Suite extension to extract the paramters and endpoints from the request to create custom wordlist for fuzzing and enumeration.
SANS New2CyberSummit 2023 videos: Talks from the SANS New2CyberSummit 2023 security conference, which took place in March, are now available on YouTube.
CyCon 2023 papers: The NATO CCDCOE has published the full 24 papers selected from 200 submissions and presented at the CyCon 2023 security conference, held at the end of May and the start of June this year. (h/t Stefan Soesanto)
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at three different state operations that have recently been outed and what these operations tell us about how these states are behaving.




