Risky Biz News: Microsoft will enable better security defaults for all Azure AD tenants next month
In other news: CouchDB servers under attack; leader of major BEC gang arrested; and Verizon gets hacked, again.

This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Big news from Microsoft this week as the OS maker and cloud giant has announced plans to forcibly enable secure defaults for all Azure AD tenants next month.
These "secure defaults," also known as Azure AD Conditional Access, will enable multifactor authentication (MFA) for all of an organization's users and will block authentication on legacy protocols where MFA is not supported.
Microsoft began enforcing these requirements for all new Azure AD customers in October 2019, but it did not mess with the accounts of its existing customer organizations in order to prevent outages or downtime.
The company said that since late 2019, more than 30 million tenants now use its secure defaults and that these companies "experience 80 percent less compromise than the overall tenant population."
But this will soon change, according to Alex Weinert, Director of Identity Security at Microsoft. Starting with late June 2022, Weinert says that Microsoft will start forcibly enabling "secure defaults" for the older customers as well.
"When complete, this rollout will protect an additional 60 million accounts (roughly the population of the United Kingdom!)," Weinert said.
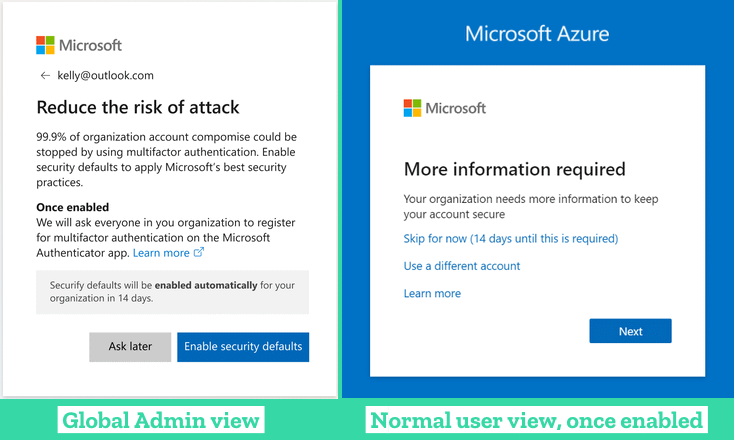
Starting next month, Microsoft said it plans to prompt every of its old customers' Global Admins with a pop-up about the new security defaults. Global admins will be able to enable the security defaults on the spot or delay the process for 14 days, at which point the feature will be forcibly enabled—if they like it or not. Once enabled, a tenant's employees will be prompted to add an MFA solution to their accounts, and Microsoft hopes this will put a huge dent in the number of accounts that get compromised via brute-force or phishing attacks on its Azure platform.
Breaches and hacks
Verizon employee breach: A hacker has obtained a database that includes the full name, email address, corporate ID numbers, and phone numbers of hundreds of Verizon employees. Motherboard reported that the threat actor got their hands on the data after tricking a Verizon employee into giving them remote access to their computer.
SpiceJet: Indian low-cost airline SpiceJet said it was hit by an "attempted" ransomware attack on Wednesday that disrupted some of its operations and delayed some flights.
#ImportantUpdate: Certain SpiceJet systems faced an attempted ransomware attack last night that impacted and slowed down morning flight departures today. Our IT team has contained and rectified the situation and flights are operating normally now.
— SpiceJet (@flyspicejet) 3:00 AM ∙ May 25, 2022
MGM Resorts data dumped: The data of more than 142 million guests who stayed at MGM hotels in the past was released for free on a Telegram channel earlier this week. The data comes from a 2019 security breach, which came to light in early 2020 after a data broker began advertising the data on cybercrime forums.
CIS leak: A security researcher said he found an Elasticsearch server leaking the personal details of more than 10 million Russians, Ukrainians, and Kazakhs who applied for "microloans." This included full names, dates of birth, home addresses, and even passport details.
General tech and privacy
FTC fines Twitter: The US FTC has fined Twitter $150 million for using phone numbers collected through its 2FA account security process for advertising purposes. The phone numbers of more than 140 million Twitter users were abused this way. The FTC said that Twitter's actions violated a 2011 FTC order that explicitly prohibited the company from misrepresenting its privacy and security practices.
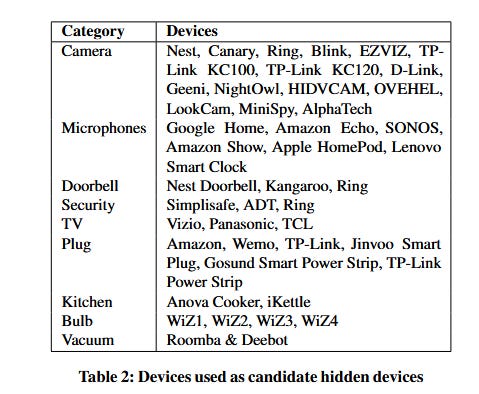
Lumos system: A team of academics from Carnegie Mellon University has developed a system they named Lumos that can run on laptops or smartphones and "enables users to identify and locate WiFi-connected hidden IoT devices and visualize their presence using an augmented reality interface." The CMU team said they tested 44 different IoT devices of various types, brands, and models, across six different environments and achieved a 95% detection rate. The researchers will present more details about their project at the upcoming USENIX conference this summer.
Government, politics, and policy
UN sanctions on Lazarus Group: Despite a push from the US for additional economic sanctions on North Korea—including a package that would freeze assets owned by the Lazarus hacking group—China and Russia have signaled their intention to use their veto option to negate the vote on the grounds that additional sanctions would worsen the existing humanitarian crisis. [Quite an ironic statement coming from two countries accused of mass genocide against the Uyghur minority and Ukraine, respectively.]
Kremlin decree on cybersecurity: The Russian government has ordered that all public and private organizations operating in critical sectors must have a cybersecurity team [PDF]. [via @lukOlejnik]
Very English Coop d'Etat: Reuters reported on Thursday that Russian state-sponsored hackers are behind a recently launched website named "Very English Coop d'Etat," where they leaked emails of several pro-Brexit hardliners earlier this month. This includes emails from ex-MI6 boss Richard Dearlove, leading Brexit campaigner Gisela Stuart, and pro-Brexit historian Robert Tombs. Several of the victims confirmed the hack. Shane Huntley, Director of the Google Threat Analysis Group, said there are "clear technical links" between the website and a Russian group the company calls "Cold River." Several security experts said the entire affair smells like Guccifer 2.0 and DCLeaks, two other politically-charged leaks orchestrated by Russian intelligence.
Literally DCLeaks 2.0
— Brian Liston (@brianjliston) 4:34 PM ∙ May 25, 2022
Dutch intelligence report: The Dutch intelligence & security services oversight board has published its annual report on Dutch intelligence activities. The oversight board found that the AIVD and the MIVD, the Netherlands' two cyber-security agencies, made 3,071 data access requests last year, including some unlawful ones that targeted journalists and broad ones meant to intercept internet cable traffic. In addition, both agencies also said that since 2018, they had failed to inform the oversight board about their usage of vulnerabilities to access third-party systems.
Cybercrime and threat intel
SilverTerrier arrest: Interpol, Palo Alto Networks, and Group-IB announced on Wednesday the arrest of a 37-year-old Nigerian man who was the leader of the SilverTerrier (Team TMT) BEC gang. The man was arrested this week at the Lagos airport in Nigeria. This marks the third wave of SilverTerrier arrests after Interpol also helped track and catch three gang members in November 2020 and another 11 in January 2022.
Bablosoft: Team Cymru has published a report on Bablosoft, a tool advertised on cybercrime forums and meant to help threat actors to automate web browser actions in order to create bots for spamming, brute-forcing passwords, or checking the validity of stolen credentials. The tool has been around for years, and Team Cymru says that malware operations like Bumblebee, BlackGuard, and RedLine have deep integrations with Bablosoft.
Cl0p returns: NCC Group is reporting a surge in activity from the Cl0p ransomware gang, with the group listing 21 new victims on its leak site over the past month. Prior to April 2021, the gang had greatly reduced its operations after several of its members responsible for money laundering were detained in Ukraine in June 2022.
ERMAC reaches v2: ESET said that it has discovered what appears to be the next iteration of the ERMAC Android trojan, which the company dubbed ERMAC 2.0. The first version of this trojan was spotted last year by ThreatFabric.
Attacks on Apache CouchDB: Threat actors are exploiting a vulnerability tracked as CVE-2022-24706 to take over Apache CouchDB servers. The vulnerability can be exploited by using a cookie with the value of "monster" sent over port 5984. This allows a threat actor access to a CouchDB server's admin user left over from its default installation without needing to provide a password—if the server owner has not removed that user or has not put the database behind a firewall. There are currently more than 81,000 CouchDB servers exposed online, although it's unclear how many still run default installs.
Confirmed exploitability of this last night.
— wvu (@wvuuuuuuuuuuuuu) 3:38 PM ∙ May 25, 2022
REvil-themed DDoS extortions: Akamai has reported this week that a cybercrime group is using the name of the REvil ransomware gang to extort companies with threats of DDoS attacks. Akamai said this DDoS extortion campaign is far smaller than previous REvil-themed campaigns from previous months.
Versus shutdown: The administrators of the Versus dark web marketplace have shut down operations after a hacker published details last week about a vulnerability in its servers that could be used to access its database and obtain details about users and the IP addresses they used to access the site. The market previously suffered another security breach in the summer of 2020, when hackers also stole funds from some user wallets.
Malware technical reports
New BPFDoor report: After reports from PwC, Sandfly Security, Elastic, security researcher Kevin Beaumont, and ExaTrack [PDF], we now have one more from security firm CrowdStrike. The malware, which CrowdStrike calls JustForFun, is a dangerous Linux malware used by a threat actor the company calls DecisiveArchitect (also known as Red Menshen). As with the previous reports, Crowdstrike said this threat actor uses the BPFDoor malware as an initial entry point into victim networks by targeting their Linux and Solaris servers, from where it moves laterally to other systems, including Windows stations.
ChromeLoader: Red Canary has published a report on ChromeLoader, a browser hijacker that modifies its victims' browser settings and redirects user traffic to advertisement websites.
Cheerscrypt ransomware: Trend Micro has published a report on Cheerscrypt, a new strain of Linux ransomware used to encrypt data on VMWare ESXi servers.
Black Basta ransomware: IBM's X-Force team has a technical report out on the Black Basta ransomware. Also, check out a similar report from Trend Micro.
Grandeiro: Trustwave has published a report on a spear-phishing campaign that spreads the Grandeiro banking trojan. The malware is known for mainly targeting banks in Latin American countries.
APTs and cyber-espionage
Earth Berberoka: Trend Micro has published a report on the activities of the Earth Berberoka (aka GamblingPuppet) APT. The company said the group uses tools previously seen used by Chinese state groups, and it primarily targeted the gambling industry catering to Asia, and more specifically, to Chinese-speaking users and the operators of gambling websites.
Gimmick macOS malware: CloudSek researchers have published a report on Gimmick, a new strain of macOS malware they discovered earlier this month. The company believes the malware is being used by a Chinese cyber-espionage group named Storm Cloud that has a history of targeting Asian regions. Also, see this report from Volexity.
Vulnerabilities and bug bounty
LinkedIn goes public: After eight years of having a private bug bounty program, LinkedIn has finally decided to open its platform to all vulnerability researchers, taking its HackerOne program public.
Pantsdown vulnerability: Hardware security firm Eclypsium said in a report on Thursday that base management controllers (BMCs) manufactured by Quanta Cloud Technology (QCT) are still vulnerable to Pantsdown, a set of vulnerabilities disclosed in 2019. The vulnerabilities can be exploited by attackers to rewrite server firmware and take over unpatched systems, Eclypsium said. Bricking servers is also a possibility.
Python&PHP library hacks: A Turkey-based security researcher has come forward and taken credit for the hijacking of two very popular Python and PHP libraries (CTX and PHPass) in an incident widely reported earlier this week. In a blog post on Medium, Yunus Aydın said he was only conducting security research and that he never meant any harm. Aydın said that despite collecting a trove of sensitive environment variables, such as AWS access keys, he has since deleted the collected information. Allegedly.
Kubernetes whitepaper: Palo Alto Networks has published a whitepaper detailing the recent types of privilege escalation attacks against Kubernetes clusters across a variety of cloud platforms. This typically includes targeting excessive permissions and Role-Based Access Control (RBAC) misconfigurations. A small excerpt: "In 62.5% of the Kubernetes platforms reviewed, powerful DaemonSets distributed powerful credentials across every node in the cluster. As a result, in 50% of platforms, a single container escape was enough to compromise the entire cluster."
Canon bugs at Pwn2Own: The Synactiv team have published their write-up on the vulnerabilities in Canon laser printers they exploited during the Pwn2Own hacking contest last year. The teams also exploited issues in HP and Lexmark printers too, but those write-ups have not yet been published.
Gin and Juice Shop: The team at PortSwigger has released an intentionally vulnerable web application—designed to look like an online shop & blog named "The Gin and Juice Shop"— on which security researchers can test their pen-testing skills.
Infosec industry
HieuPC: France24 has published a profile on Ngo Minh Hieu, the Vietnamese hacker who was arrested and sentenced in the US back in the mid-2010s for selling the personal details of more than 200 million Americans. Hieu, who went online as HieuPC, says he's now working with the Vietnamese government to educate people on cybersecurity, stopping cyberattacks, and catching other cybercriminals.
Lacework layoffs: According to a report from Protocol, cloud security firm Lacework has laid off more than 300 employees, which is around 20% of its workforce. The layoffs come following a $1.3 billion funding round at an $8.3 billion valuation in November 2021.
New CEOs: Cybersecurity firms McAfee and Binary Defense have both appointed new CEOs this week in Greg Johnson and Bob Meindl, respectively.




