Risky Biz News: Microsoft says Chinese APTs used the most zero-days last year
In other news: New spyware victims revealed in Greece; Qatar hacked FIFA officials; FBI makes fun of pro-Russian hacktivists.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Although APT groups use zero-day vulnerabilities as part of their attack kill-chains, in its yearly Digital Defense Report last week, Microsoft said it spotted Chinese threat actors using an increased number of zero-days over the past year.
Microsoft believes this sudden spike in zero-day exploits from Chinese threat actors comes as a direct result of a new law passed by the Chinese government last year.
Passed in July 2021 and entered into effect in September 2021, this new law requires that all Chinese security researchers report new vulnerabilities they find to a state security agency.
Faced with criticism at the time it passed the law, the Chinese government said it only wanted to maintain an accurate index of vulnerabilities and make sure local companies don't dodge responsibility for failing to patch vulnerabilities in time and leaving Chinese users and government networks exposed to attacks.
But the new law also contains several generically-worded clauses that could be interpreted to suggest that the Chinese government was setting up a secret process through which its offensive cyber units could pilfer and suppress the work of the infosec community for the country's espionage operations.
While no solid evidence has been found so far to support these theories, Microsoft appears to be sold on this narrative in its latest report.
" This new regulation might enable elements in the Chinese government to stockpile reported vulnerabilities toward weaponizing them. The increased use of zero days over the last year from China-based actors likely reflects the first full year of China's vulnerability disclosure requirements for the Chinese security community and a major step in the use of zero-day exploits as a state priority.
The company listed five zero-days in its report as possible examples of abuse: two in Zoho ManageEngine (CVE-2021-40539 and CVE-2021-44077), and one in SolarWinds Serv-U (CVE-2021-35211), Atlassian Confluence (CVE-2022-26134), and Microsoft Exchange (CVE-2021-42321).
Were exploits for these zero-days developed by Chinese APTs after they were reported through China's in-house vulnerability disclosure rules? Possibly. Maybe. Who knows.
Has the same software been repeatedly plagued by major vulnerabilities and zero-day exploits over the past years? Yes! Oh, God, yes!
Maybe that's a more accurate assessment. You can’t blame Chinese APTs for looking at what everyone else is looking at. Are they getting a little help from the state's mandatory disclosure law? We’re not convinced so far. China has a huge cybersecurity scene, so there’s no need to "steal" someone's bug report when you can just as easily buy it from a private contractor who is also going to keep their mouth shut.
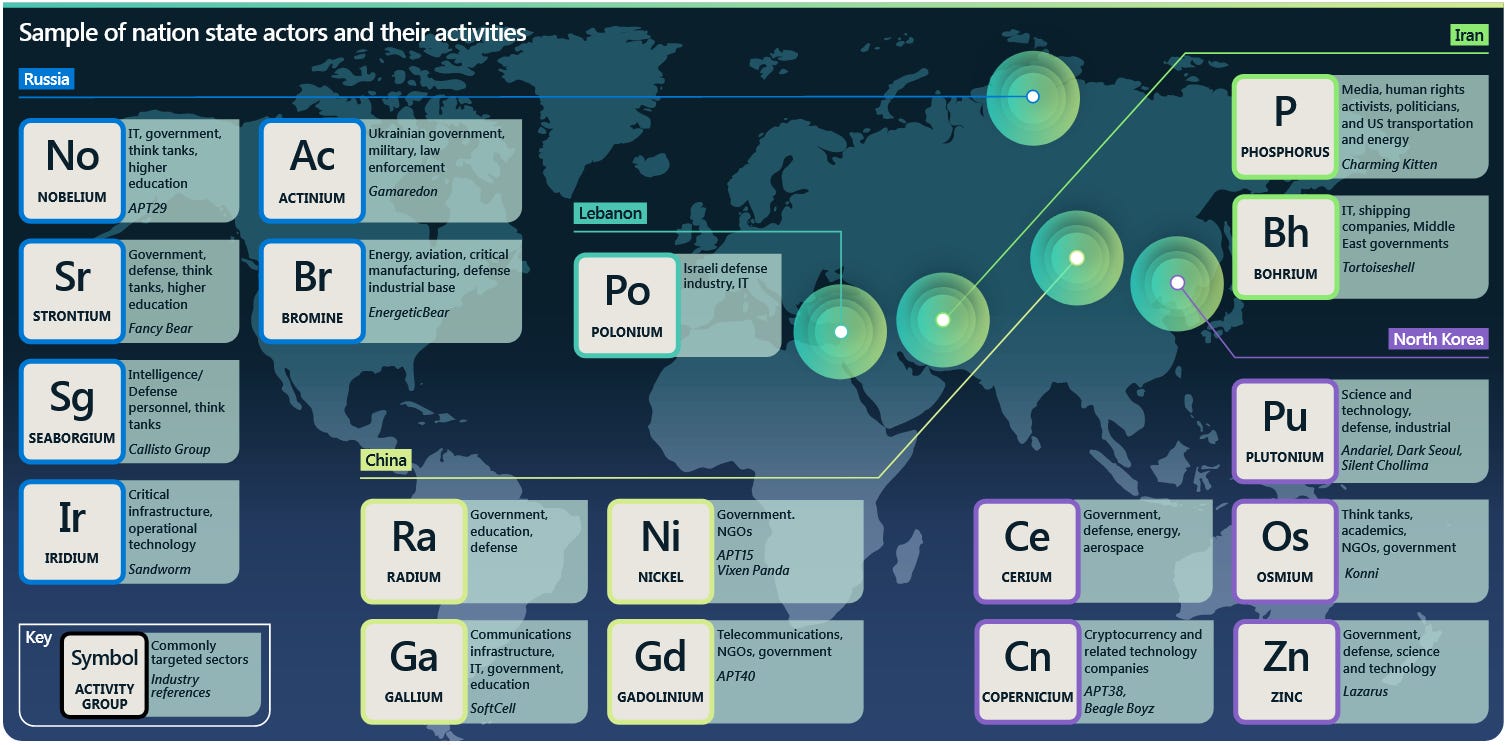
In the meantime, please enjoy Microsoft's latest APT names chart. You're gonna need it if you wanna decipher any of the company's APT reports and attributions.
Breaches and hacks
Solend crypto-heist: DeFi platform Solend said it lost $1.26 million worth of cryptocurrency following an Oracle attack on its platform, targeting the Hubble (USDH) currency.
Successful defense: In a post-mortem, pNetwork said it successfully defended an attack on its pGALA token.
DSB cyber-attack: Danish train operator DSB said that the disruptions to some of its trains over the previous weekend were the result of a cyber-attack on the infrastructure of one of its IT subcontractors.
Personal Paraguay hack: Paraguay's Personal ISP service disclosed last week that it was the victim of a cyber-attack.
General tech and privacy
SolarWinds settlement: SolarWinds said it reached a settlement with its shareholders in a class-action lawsuit filed in 2021 in which the company was accused of misleading its investors about the 2020 hack and subsequent supply chain attack. According to documents filed with the SEC, the settlement is worth $26 million but still needs to be approved by the case judge.
Government, politics, and policy
Qatar spied on FIFA officials: A report in Swiss media claims that Qatar officials "orchestrated a large-scale and long-standing intelligence operation against FIFA officials with the help of former CIA operatives" in the run-up to Qatar being awarded the FIFA 2022 World Cup. The report claims that "the highest echelons of the Qatari government were involved" and that the cyber-espionage campaign targeted critics inside and outside FIFA alike.
"The scale of the espionage activities is considerable. One sub-operation alone involved the planned deployment of at least 66 operatives over nine years. The budget amounted to $387 million. And the activities spanned five continents."
The AP reported last week that the FBI started an investigation against Kevin Chalker, a former CIA agent and the founder and CEO of Global Risk Advisors, the company that helped the Qatari government orchestrate this operation.
Armenian cyber-attacks: Azerbaijan officials said they successfully mitigated "large-scale cyberattacks by Armenia" following the second Karabakh War in September 2022. No details were provided on what those cyber-attacks were.
Greece's spyware scandal: On Sunday, Greek newspaper Documento published a list of 33 names they claim were targeted and infected with the Predator spyware as part of an illegal surveillance operation ordered by the Greek government led by Prime Minister Kyriakos Mitsotakis. The list includes names of state officials, journalists, and local businesspeople—and adds to four already-known individuals. The highest-profile figure on the list is Nikos Dendias, Greece's current Foreign Minister and a member of the ruling party New Democracy. [English coverage in Politico Europe]
Japan joins NATO CCDCOE: Japan's Ministry of Defense announced it formally joined the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) last week. Japan is the fifth country to join this year after South Korea, Canada, Ukraine, and Luxembourg were also admitted earlier this year.
NCCoE guidance: The National Cybersecurity Center of Excellence (NCCoE), a part of the National Institute of Standards and Technology (NIST), published guidance on how the manufacturing and industrial sectors can respond to cyber-attacks on their OT/ICS networks.
FBI makes fun of pro-Russian hacktivists: In a PIN alert [PDF] on Friday, the FBI warned about a rising wave of DDoS attacks carried out by pro-Russian hacktivist groups but urged companies to stay calm and not panic as these attacks are mostly ineffective.
"These attacks are generally opportunistic in nature and, with DDoS mitigation steps, have minimal operational impact on victims; however, hacktivists will often publicize and exaggerate the severity of the attacks on social media. As a result, the psychological impact of DDoS attacks is often greater than the disruption of service."
UK DfE lapse: An investigation by the UK Information Commissioner's Office (ICO) found that the Department for Education (DfE) had a major privacy lapse in its LRS database. The LRS system was designed to let educational institutions inspect a record of a pupil's qualifications before admittance to courses or special programs, but British press and the ICO confirmed that the DfE granted access to the system to a company named Trustopia, which then used it to allow online gambling companies to verify if a new account was over 18.
"This data sharing meant the information was not being used for its original purpose. This is against data protection law. The ICO issued a reprimand to the DfE setting out clear measures they need to action to improve their data protection practices so children's data is properly looked after."
NCSC scans internal IP space: The UK National Cyber Security Centre (NCSC) revealed details about an internal initiative through which the agency plans to scan internet-connected devices across the UK IP space to create an inventory of vulnerable systems and then attempt to warn the device owners. NCSC officials said they plan to use this information to be better prepared to respond to sudden waves of exploitation attacks targeting a particular vendor or device and warn affected organizations. Similar programs to what the NCSC is attempting have also been underway, typically managed by CERT teams, in multiple countries, to a larger/smaller degree.
"All activity is performed on a schedule using standard and freely available network tools running within a dedicated cloud-hosted environment. [...] Note that these IP addresses are also both assigned to scanner.scanning.service.ncsc.gov.uk with both forward and reverse DNS records. Scan probes will also attempt to identify themselves as having originated from NCSC where possible."
ACSC threat assessment: Australia's Cyber Security Centre (ACSC) published on Friday its annual cyber threat report for the period of July 2021 to June 2022. Some of the report's main findings include:
- An increase in financial losses due to BEC to over $98 million.
- A rise in the average cost per cybercrime report to over $39,000 for small businesses, $88,000 for medium businesses, and over $62,000 for large businesses.
- A 25% increase in the number of publicly reported software vulnerabilities.
- Over 76,000 cybercrime reports (13% up from the previous year).
- A cybercrime report every 7 minutes on average.
- 150,000 to 200,000 SOHO routers in Australian homes and small businesses are vulnerable to compromise.
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. Last week, the company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
Atlantis Cyber Army: Israeli cybersecurity firm CyberInt said it found a new mercenary hacking group Atlas Intelligence Group, also known as the Atlantis Cyber Army. The company said the group is led by an individual going by the name of Mr. Eagle, and they provide services such as exclusive data leaks, DDoS, RDP, and other methods of access to organizations. A Times of Israel report makes this look like some top apex hacker-for-hire actor, but a CyberInt report from July actually paints the picture of a run-of-the-mill initial access broker advertising stuff on Telegram.
Malware technical reports
Vultur: Mobile security firm Cleafy said it found a version of the Vultur malware hidden inside an Android app uploaded on the official Google Play Store. The app, which claimed to allow users to recover deleted files, was downloaded more than 100,000 times, the company said.
APTs and cyber-espionage
Iranian threat actors: The security team at the US Department of Health and Human Services has a summary [PDF] of Iran-based threat actors and their most common TTPs.
Hamas expanding in cyber domain: A report from the Atlantic Council highlights Hamas' efforts to expand into the cyber domain, where it is slowly becoming a capable threat actor.
" [The] analysis will show how Hamas's cyber activities do not indicate a sudden shift in strategy but, rather, a realignment that augments operations. In other words, offensive cyber operations are a new way for Hamas to do old things better. As the title of this report suggests, Hamas is like a green hat hacker—a term that is not specific to the group but recognized in the information security community as someone who is relatively new to the hacking world, lacking sophistication but fully committed to making an impact and keen to learn along the way. Hamas has demonstrated steady improvement in its cyber capabilities and operations over time, especially in its espionage operations against internal and external targets. At the same time, the organization's improvisation, deployment of relatively unsophisticated tools, and efforts to influence audiences are all hallmarks of terrorist strategies. This behavior is in some ways similar to the Russian concept of 'information confrontation,' featuring a blend of technical, information, and psychological operations aimed at wielding influence over the information environment."
Vulnerabilities and bug bounty
New Sudo vulnerability: The Sudo project patched last week a major vulnerability tracked as CVE-2022-43995 that can allow a threat actor to run code on a vulnerable system.
"This can be triggered by arbitrary local users with access to Sudo by entering a password of seven characters or fewer. The impact could vary depending on the system libraries, compiler, and processor architecture."
Android zero-day write-up: Project Zero's Maddie Stone has published an analysis of three Android zero-day vulnerabilities (CVE-2021-25337, CVE-2021-25369, CVE-2021-25370) that were used as part of an exploit chain in attacks against Samsung device users. All three zero-days were patched in March this year.
"TAG believes belonged to a commercial surveillance vendor. These exploits were likely discovered in the testing phase. The sample is from late 2020. The chain merited further analysis because it is a 3 vulnerability chain where all 3 vulnerabilities are within Samsung custom components, including a vulnerability in a Java component."
Infosec industry
PrivacyCon 2022 videos: Talks from the FTC's PrivacyCon 2022 conference, which took place last week, are now available on the agency's website.
Twitter implosion: As Twitter slowly implodes under Musk's dilettante leadership, Mastodon reported that it reached an all-time high of 655,000 active users after an influx of 230,000 new users to the platform last week alone. And since we're on it, you will be able to find the author of this newsletter on Mastodon here.
NSA job openings: The NSA has a fast-track program for former employees, including for cybersecurity roles.
Former NSA or Intel community? Come on back! We now have a vacancy listing to fast track former employees back in. Check it out.
— Rob Joyce (@NSA_CSDirector) 1:20 AM ∙ Nov 6, 2022
apply.intelligencecareers.gov/job-descriptio…
IDA Pro community: See below.
We’re happy to announce our new blog series called “Plugin Focus” where authors of some of the most useful plugins will introduce them and provide some valuable insights. We start with HRDevHelper 🌐 hex-rays.com/blog/plugin-fo…
— Hex-Rays SA (@HexRaysSA) 4:51 PM ∙ Nov 4, 2022
#PluginFocus #IDAPro #IDAPython #IDAPlugin




