Risky Biz News: Microsoft rolls out number matching to counter MFA push notification spam attacks
In other news: US Treasury sanctions MOIS cyber contractors; Apple paid $20 million to bug hunters since 2019; Raspberry Robin USB worm linked to Clop ransomware attacks.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Earlier this week, Microsoft announced the general availability of several new security features for Azure AD tenants, including "number matching," a feature to protect against an increasingly popular attack known as MFA push notification spam.
Also known as MFA fatigue or MFA prompt-bombing, this MFA bypass technique has been a little-known secret of infosec red teams for years, but it has also become extremely popular with several threat actors over the past 12 months.
The technique is typically used when a threat actor has managed to obtain a victim's valid user credentials. If the account is protected by a multi-factor authentication (MFA) solution, the attacker uses the credentials and then intentionally triggers a smartphone push notification on the account owner's phone to grant them access to the account.
The idea behind an MFA fatigue attack is to trigger repeated push notifications in the hopes that the account owner gets tired of the "spam" and approves the attacker's access to the account, or they accidentally click "yes/approve" and allow the attacker access.
Cyber-espionage groups like APT29 were among the first major threat actors seen using this technique, which has also since been adopted by the APT (advanced persistent teen) group Lapsus$ in their recent intrusions at Cisco, Microsoft, Okta, Nvidia, and Uber.
Lapsus$ did not invent 'MFA prompt bombing' please stop crediting them with them as creating it.
— Greg Linares (@Laughing_Mantis) 4:47 PM ∙ Mar 25, 2022
This attack vector has been a thing used in real world attacks 2 years before lapsus was a thing
The new "number matching" feature works to protect accounts by showing a number inside the push notification message received by account owners. Even if the user clicks "yes/approve" by accident, the attacker won't be able to log in without entering this number as well, which most attackers would not be able to do.
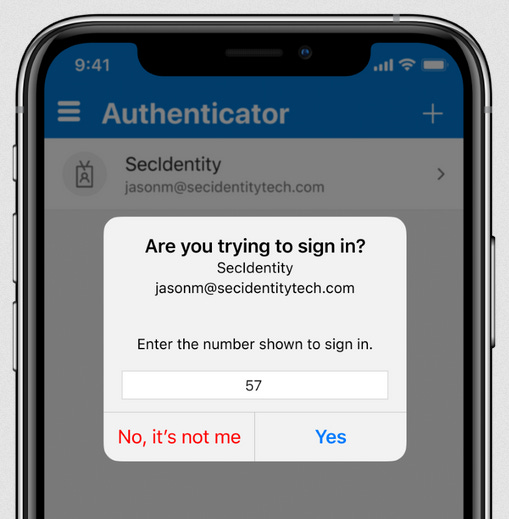
Microsoft announced this feature earlier this year—after Lapsus$ compromised its network—but a similar number matching feature has also been available in other secure authentication providers like Cisco Duo, Okta, and others.
However, it must be mentioned that this technique is not foolproof, and attackers who contact employees posing as IT staff have been known to extract these numbers from employees in some attacks. But if you're forcing employees into MFA that rely on push notifications, it's better to have numbers matching enabled than not. Either way, if FIDO-based MFA is an option, better use that, as that form of cryptographic device-based authentication is not vulnerable to MFA fatigue attacks.
Breaches and hacks
Twilio breach: Twilio said it concluded its investigation into its July security breach and has posted a final version of its IR report on its blog. Conclusions below:
- The last observed unauthorized activity in our environment was on August 9, 2022;
- 209 customers – out of a total customer base of over 270,000 – and 93 Authy end users – out of approximately 75 million total users – had accounts that were impacted by the incident; and
- There is no evidence that the malicious actors accessed Twilio customers' console account credentials, authentication tokens, or API keys.
Phishing "compensation": Cryptocurrency exchange platform FTX said it is providing $6 million in compensation for some of its users who fell victim to a phishing scam last week. The company said the users didn't fall victim to sites posing as FTX but to sites posing as another cryptocurrency platform named 3Commas. FTX said its users provided this fake site copies of their FTX API keys, usually provided to integrate two different services, which the hackers then used to drain accounts. FTX CEO Sam Bankman-Fried called this action a "one-time" compensation and said that the platform does not intend to compensate users again for losses due to phishing at other platforms. [Additional coverage in CoinTelegraph]
Team Finance hack: DeFi platform Team Finance confirmed on Twitter on Thursday that a hacker exploited a platform migration feature and stole roughly $14.5 million worth of cryptocurrency from its wallets.
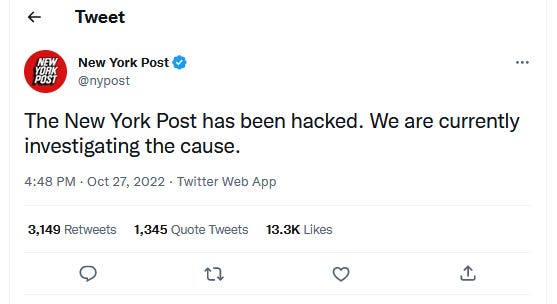
New York Post hack: Controversial right-wing tabloid the New York Post said it suffered a security breach on Thursday. No official details were provided, but users on social media reported that the NY Post website and Twitter accounts were seen posting calls for the assassination of several prominent Democrat figures.
General tech and privacy
Apple security updates: Apple has updated its software update policy page this week and is finally confirming that it does not always backport security patches to the older versions of its operating systems.
Apple has finally officially state their stance on the latest operating system is the only fully patched one. If you are running anything other than $latest you are likely vulnerable
— Graham Gilbert (@grahamgilbert) 5:34 AM ∙ Oct 26, 2022
Improved account recovery on npm: GitHub has rolled out an improved and easier account recovery procedures for developers that lost access to their MFA device and their account recovery codes.
Microsoft fixes drivers blocklist: After a report that the company failed to update a list meant to block the installation of malicious and vulnerable drivers, Microsoft updated its drivers blocklist earlier this week to fix the issue and even rolled it out to more Windows 11 users as well.
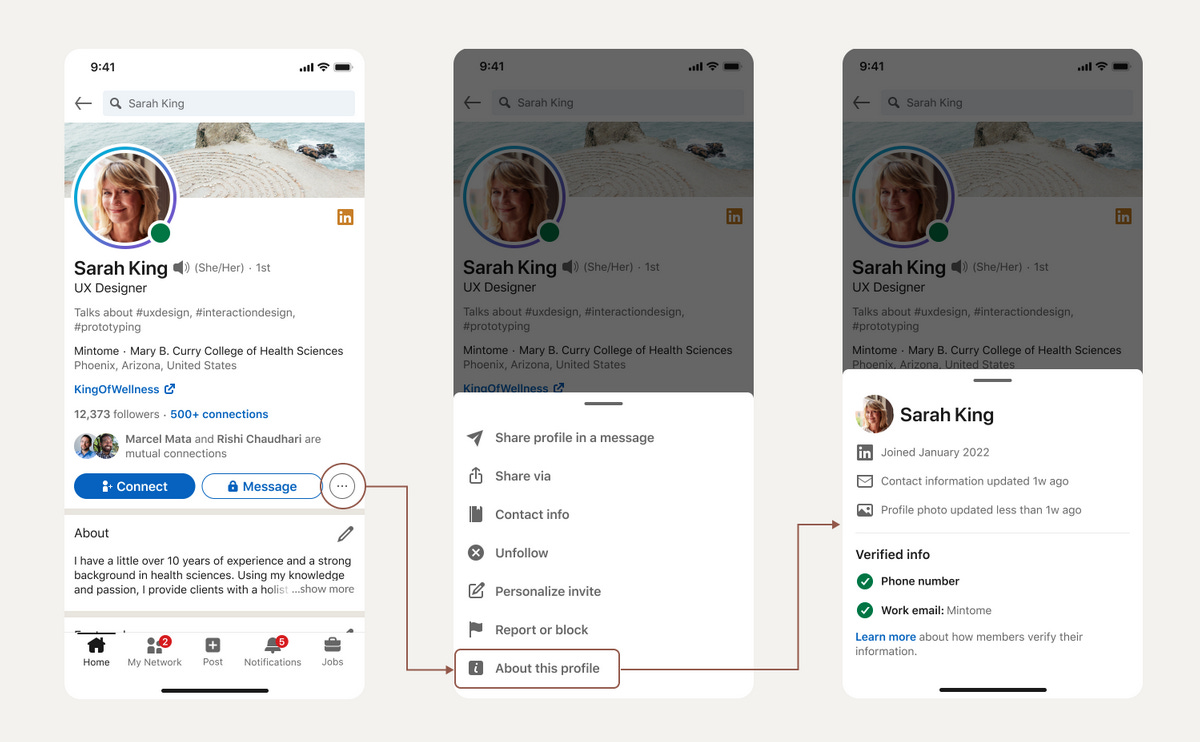
New LinkedIn security features: LinkedIn announced new security features this week to help users verify and determine if a profile is authentic. In addition, the company is also deploying a system to detect AI-generated profile images and more systems to detect suspicious DMs. The move comes after the social network has become wildly popular among cybercrime and cyber-espionage groups alike for both scamming and luring users to malware and phishing sites.
Government, politics, and policy
US Treasury sanctions MOIS contractors: As part of a larger sanctions package aimed at the Iranian government for its crackdown against its citizens for taking part in the Mahsa Amini protests, the US Treasury on Wednesday also sanctioned two individuals working as cybersecurity contractors for the Iranian Ministry of Intelligence and Security (MOIS). Treasury officials said that Farzin Karimi and Seyed Mojtaba Mostafavi, two MOIS members, also founded Ravin Academy, a company that has provided cyber security and hacking training to MOIS recruits. In addition, the US Treasury also imposed sanctions on Sahab Pardaz, an Iranian company that has been contracted by the Iranian regime to perform deep packet inspection (DPI) on internet traffic and help the government censor its citizens' internet, and especially social media content.
Cybersecurity sprint: The Biden administration announced this week a 100-day cybersecurity sprint meant to help protect the US chemical sector from cyberattacks. This will be the fourth cybersecurity sprint launched by the White House since April 2021, after similar programs targeted the pipeline, water, and railway transportation sectors. [Additional coverage in Cyberscoop]
Sponsor section
RunZero (formerly Rumble Network Discovery) is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Popopret/BestBuy arraigned in US court: The US Department of Justice arraigned in court Daniel Kaye, a British national, for his role in operating The Real Deal, a former dark web marketplace where criminals traded stolen data and credentials. Kaye, who went online under names like Popopret and Bestbuy, was extradited from Cyprus to face charges. In 2017, Kaye also received a suspended prison sentence of one year and eight months in Germany after he hijacked and crashed more than 900,000 Deutsche Telekom routers. In 2019, Kaye was also sentenced to two years and eight months in the UK for using a copy of the Mirai malware to build a DDoS botnet to attack UK ISPs. He also used the same botnet as part of a DDoS-for-hire service to take down the connectivity of a major Liberian ISP at the request of one of their competitors.
Didn't think I'd hear this name again. Was tracking him back in 2016 when he took offline the UK's largest bank, Crashed nearly 1 million Germans' internet routers, and tried to take out Liberia's largest ISP. Dude was a straight menace.
— Marcus Hutchins (@MalwareTechBlog) 5:06 PM ∙ Oct 26, 2022
XSS adds section for security firms: Probably tired after having his site scraped over and over again by security firms and malware researchers, the operator of the XSS cybercrime forum decided this week to add the ability for security firms to purchase a "scraper" option to allow them to collect data from the forum without getting blocked or banned.
Today, the XSS forum introduced the forum group "Scraper" for white hats.
— 3xp0rt (@3xp0rtblog) 7:48 PM ∙ Oct 26, 2022
Facebook subscription spam: A threat actor has hammered Polish Facebook users with a giant subscription spam campaign that used more than 600 different malicious landing sites, according to Avast.
New wave of a subscription scam currently active in Poland 🇵🇱 using more than 600 infected sites. Almost 6000 users protected. Victims click on #Facebook link leading to subscription scam landing page.
— Avast Threat Labs (@AvastThreatLabs) 4:21 PM ∙ Oct 27, 2022
Warzone RAT: Fortinet documented a phishing campaign using a fake Hungarian government to target local users with a version of the Warzone RAT.
Kiss-a-Dog campaign: Crowdstrike published a report on Kiss-a-Dog, a new cryptomining operation that has been targeting vulnerable Docker and Kubernetes infrastructure. The Kiss-a-Dog threat actor targets cloud servers with exposed administration APIs, uses a container escape vulnerability to attack the underlying servers, deploys the Diamorphine and libprocesshide rootkits to take over the system, then deploys a backdoor for future access, and finally, a cryptominer to exploit the servers for their own profits.
LockBit main threat for ICS sector: A report from ICS security firm Dragos analyzes the ransomware attacks that have targeted the industrial sector across the world in Q3 2022. Per the company, the LockBit and Black Basta gangs were responsible for the vast majority of incidents targeting ICS firms.

Malware technical reports
Fodcha DDoS botnet: Qihoo 360's Netlab division said it spotted new DDoS attacks carried out using Fodcha, a DDoS botnet that first emerged earlier this year in April. According to Netlab, the botnet has grown significantly over the past months, is now capable of executing DDoS attacks of over 1 Tbps, and its operators are also using it to extort companies. Netlab said they are doing this by adding an extortion demand in the UDP packets of their attack, requesting payment to a Monero address.
send 10 xmr to 49UnJhpvRRxDXJHYczoUEiK3EKCQZorZWaV6HD7axKGQd5xpUQeNp7Xg9RATFpL4u8dzPfAnuMYqs2Kch1soaf5B5mdfJ1b or we will shutdown your business
ERMAC v2: QuoIntelligence published an in-depth analysis of ERMAC v2, an Android banking trojan that was first spotted last year and which got updated to v2 earlier this year in May.
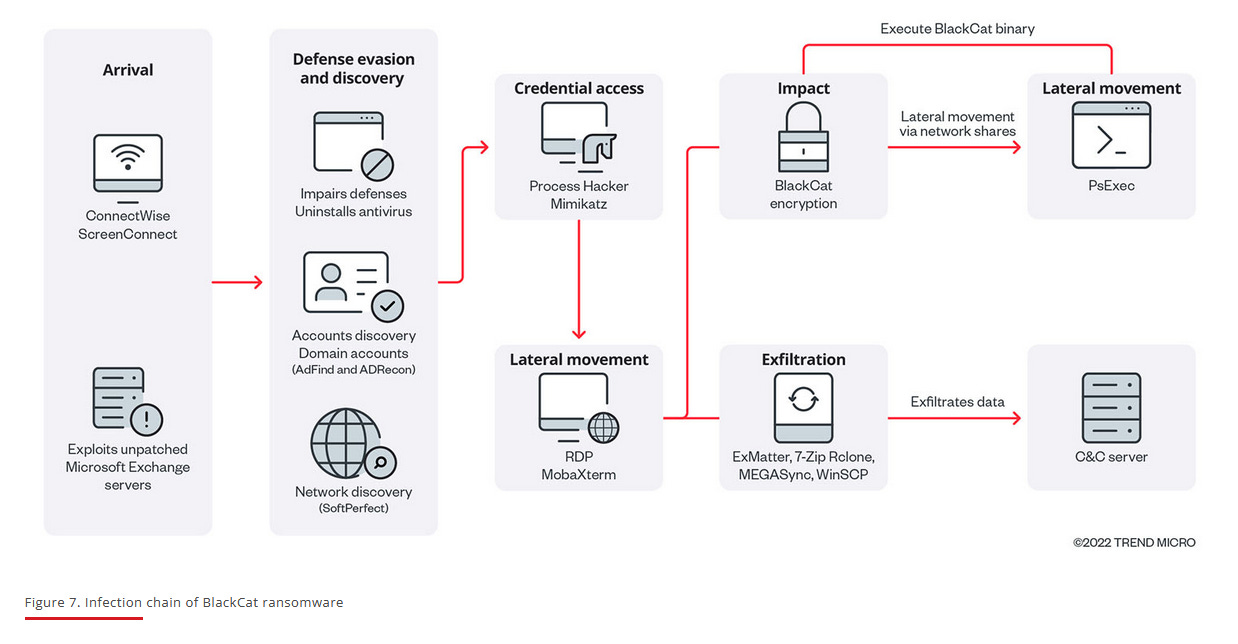
AlphV/BlackCat: Trend Micro has a pretty good profile on the AlphV/BlackCat ransomware operation.
Raspberry Robin malware linked to ransomware attacks: In a report on Thursday, Microsoft was able to finally confirm that in some cases, systems infected with the Raspberry Robin USB worm were used as entry points for hands-on-keyboard ransomware attacks—and more specifically, with the Clop ransomware strain. In addition, Microsoft also confirmed IBM X-Force's findings that the Raspberry Robin malware was developed by the EvilCorp gang, the same group that created the Dridex banking trojan and the Locky and BitPaymer ransomware strains.
APTs and cyber-espionage
DragonBridge: Two weeks ago, this newsletter covered a weird social media influence operation where a group of Chinese bots tried to mislabel the Chinese APT41 cyber-espionage group as the US NSA. This week, Mandiant confirmed that this was indeed a well-coordinated social media influence operation, one the company tracks as DragonBridge. In addition, the same operation also tried to discredit the US democratic process, including attempts to discourage Americans from voting in the 2022 US midterm elections, and promoted the conspiracy theory that the US was responsible for the Nord Stream gas pipeline explosions. Alethea Group confirmed seeing the same thing in a separate report.
Patchwork's Operation Herbminister: Chinese security firm Knowing Chuangyu published a report this week on Operation Herbminister, a series of attacks carried out by the Patchwork APT against scientific research targets across several countries last year.
Kimsuky: AhnLab documented a phishing campaign carried out by the Kimsuky North Korean APT targeting various companies working in the nuclear power plant sector. The final payload in these attacks was the AppleSeed malware.
Vulnerabilities and bug bounty
Apple bug bounty program: Apple says it has awarded more than $20 million to security researchers via its bug bounty program since its launch in late 2019. Apple said the program has an average payout of $40,000 and also dished out 20 separate rewards of over $100,000 for high-impact issues.
VMware vulnerability: Sina Kheirkhah of Source Incite published details about CVE-2022-31678, a pre-authenticated remote code execution vulnerability in VMWare NSX Manager, a component of the VMware Cloud Foundation service. The vulnerability was patched earlier this week.
TCP/IP RCE: Researchers from Numen have published a write-up on CVE-2022–34718, a remote code execution vulnerability in the Windows TCP/IP component patched in September. A PoC is also included.
SiriSpy: According to reverse engineer Guilherme Rambo, any app with access to the Bluetooth service can record conversations with Siri, using audio from the iOS keyboard dictation feature while AirPods or Beats headsets are connected. The bug, named SiriSpy, was patched earlier this week.
Leeloo Multipath: Qualys researchers published details on Leeloo Multipath, two EoP vulnerabilities in the Linux multipathd service.
GitHub vulnerability: Checkmarx researchers said they helped GitHub fix a vulnerability in a feature they launched this April that prevented threat actors from claiming old usernames and hijacking existing packages—a technique known as repojacking. If exploited, this vulnerability would have allowed attackers to carry out new repojacking attacks and execute supply chain attacks via legitimate projects.
Infosec industry
New tool—Text4Shell tools: DevOps security firm JFrog has open-sourced a collection of tools to scan projects for the Text4Shell vulnerability.
Hexacon 2022 videos: Talks from the Hexacon 2022 security conference, which took place earlier this month, are available on YouTube.
Some infosec humor: kek
An apology
— Malwarebytes (@Malwarebytes) 9:43 PM ∙ Oct 27, 2022




