Risky Biz News: Microsoft revokes 100+ malicious drivers
In other news: EU and US sign new trans-Atlantic data transfer pact; US healthcare giant HCA confirms data breach; and Patch Tuesday comes with Apple and Windows zero-day fixes.
This newsletter is brought to you by Kroll. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
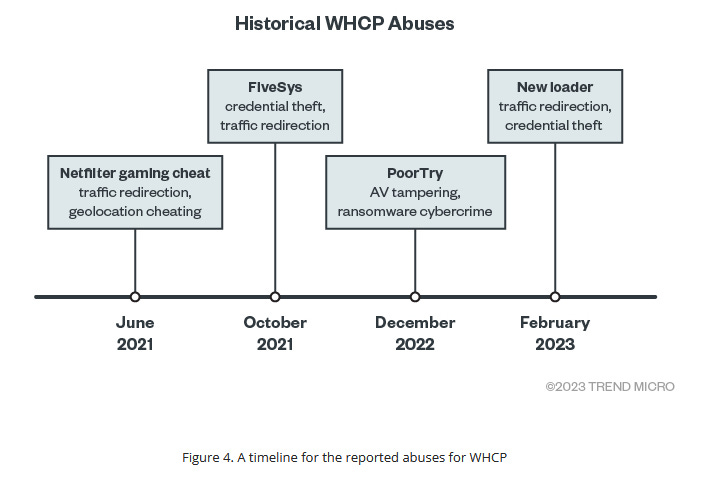
Microsoft has revoked more than 100 malicious drivers that received valid signatures via the company's Windows Hardware Compatibility Program (WHCP).
The malicious drivers were added to the company's driver revocation list and will be blocked from running on Windows systems going forward.
Microsoft credited security firms Sophos, Cisco Talos, and Trend Micro for discovering the malicious drivers and how they were being submitted to its developer portal.
The three companies say the drivers originated from the Chinese cybercrime underground and were used to power browser hijackers, rootkits, and gaming cheats.
Cisco Talos researchers say most of the malicious drivers were created with two tools named FuckCertVerify and HookSignTool. The tools have been around since 2018 and 2019, respectively, and they allow threat actors to sign malicious payloads.
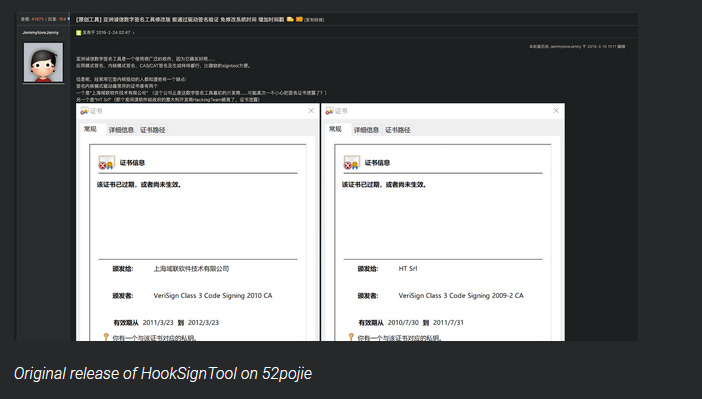
Researchers believe that sometime around April 2021, some Chinese threat actors realized they could use these simple tools to abuse an "exception" in Microsoft's HWCP program and sign drivers that run at the Windows kernel level.
The exception—present in the WHCP for legacy and compatibility purposes—is that if a Windows driver is signed with a non-revoked certificate issued prior to or expired before July 29, 2015, the driver will be allowed to run on Windows systems even if it doesn't meet all the WHCP requirements.
Drivers created with this technique include browser hijacker RedDriver, a new rootkit-level loader, FiveSys, "endpoint protection killers," and a boatload of gaming cheats and game-cracking tools.
In a security advisory published with this month's Patch Tuesday, Microsoft said it rolled out detections for some drivers back on March 2 this year. The company also suspended developer accounts whose certificates were often used to sign the malicious drivers.
Breaches, hacks, and security incidents
HCA data breach: Hospital Corporation of America (HCA), one of the largest healthcare providers in the US, has confirmed a security breach after the information of millions of patients was put up for sale on a hacking forum. The incident impacted 11 million patients who visited HCA hospitals across 20 US states. Stolen data includes patient names, addresses, emails, phone numbers, dates of birth, gender, and health care details.
Trinidad & Tobago incident: A cyber-attack has crippled the operations of the Trinidad and Tobago Justice Ministry. The attack took down email servers and access to the online court documents system. [Additional coverage in the Trinidad & Tobago Guardian]
General tech and privacy
Let's Encrypt certificates and Android: Let's Encrypt certificates will stop working on Android 7 and earlier versions starting February 8 next year. The Let's Encrypt project recommends that users still using older Android devices install Firefox Mobile, which will still allow them to access LE-protected websites.
Fedora telemetry: The Fedora Project is working on adding "privacy-preserving telemetry" support to its Fedora Workstation OS. A new metrics collection setting will be added to the OS privacy page to allow users to disable the behavior if they want to.
Thunderbird Supernova: Mozilla has launched a new version of the Thunderbird email client, v115, codenamed Supernova.
Threads passes 100M: Meta's Twitter clone—Threads—has passed the 100 million user mark less than a week after launch. [Additional coverage in Engadget]
Twitter Blue misinformation: A BBC investigation has found that a wave of Twitter Blue accounts are using the "benefits" of their blue tick to promote lies and misleading posts about the war in Ukraine. I am shocked!
Azure AD rebrand: Microsoft has rebranded its Azure Active Directory service as Microsoft Entra ID.
Government, politics, and policy
New EU-US data transfer pact: The European Union has adopted a new legal framework that will allow companies like Facebook, Google, and Apple to transfer and store data about European users in the US. The new EU-US Data Privacy Framework replaces the EU-US Privacy Shield, struck down by an EU judge in 2020 for not containing enough protections for EU users. The new agreement contains more protections for EU citizens, more obligations for US companies on how to handle user data, and contains provisions to limit the amount of data that US intelligence can gain access to.
Dutch government joins Mastodon: The Dutch government has set up an official Mastodon server following the recent instability of Twitter. It is the first major government to formally join Mastodon after the EU joined back in 2017.
Spain closes NSO probe: A Spanish court has shelved an investigation into the hacking of government officials with the Pegasus spyware. The court says the investigation stalled after four formal requests for international judicial assistance made to Israel were not answered. The judge cited a "complete lack of legal cooperation from Israel" in Spain's efforts to investigate spyware maker NSO Group. [Additional coverage in The Times of Israel]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Scott Hanson, Head of Global Security Operations at Kroll, on how the company has adopted Detection-as-Code for its approach to writing, managing, and rolling out detection rules for its customers:
Cybercrime and threat intel
Two Lapsus$ hackers charged: The UK government has formally charged two teenagers for hacking and blackmailing some of the world's largest companies while part of the Lapsus$ cybercrime gang. Eighteen-year-old Arion Kurtaj and an unnamed 17-year-old teen were accused of hacking US chipmaker Nvidia and UK ISP BT EE. Kurtaj was also charged with hacking and blackmailing ride-sharing service Uber, payments provider Revolut, and Rockstar Games, the company behind the Grand Theft Auto video game. The two suspects were detained by British police in March 2022, together with five other suspects. An eight suspected Lapsus$ member was also detained in Brazil. [Additional coverage in Bloomberg/non-paywall]
Security engineer arrested for crypto-heist: The US Department of Justice has arrested and charged a New York security engineer named Shakeeb Ahmed for hacking a cryptocurrency exchange in July 2022. Officials say Ahmed used skills he learned on his job to manipulate one of the platform's smart contracts and steal $9 million worth of crypto-assets. In a practice that has become quite common in the cryptocurrency world, Ahmed reached a secret agreement with the victim to keep $1.5 million of the stolen funds as a "bug bounty reward" and return the rest if the company didn't refer the hack to law enforcement. Officials didn't name the exchange, but the date of the hack and the value of the stolen and returned funds match the attack on the Cream Finance platform. The case marks the first time the FBI and DOJ have detained one of these hackers that reached "white hat bug bounty" agreements with their victims.
Mobile device spoofing market: A Resecurity report looks at the emerging collection of tools that can spoof various mobile operating systems and devices to allow threat actors to bypass anti-fraud detections when using compromised credentials to access bank and other financial accounts. Similar tools have been available for desktop operating systems but are now slowly being ported for Android and iOS devices as well. The price of some of these tools can be as low as $500, but they can be used to enable fraud in the realm of millions.
Malicious PyPI packages: PAN's Unit42 has a report on six malicious Python packages found on the PyPI portal intended to steal Windows app credentials, personal data, and crypto wallet data.
Cloudflare phishing abuse: Trustwave has detected a phishing campaign abusing Cloudflare's workers[.]dev and pages[.]dev domains to host phishing pages.
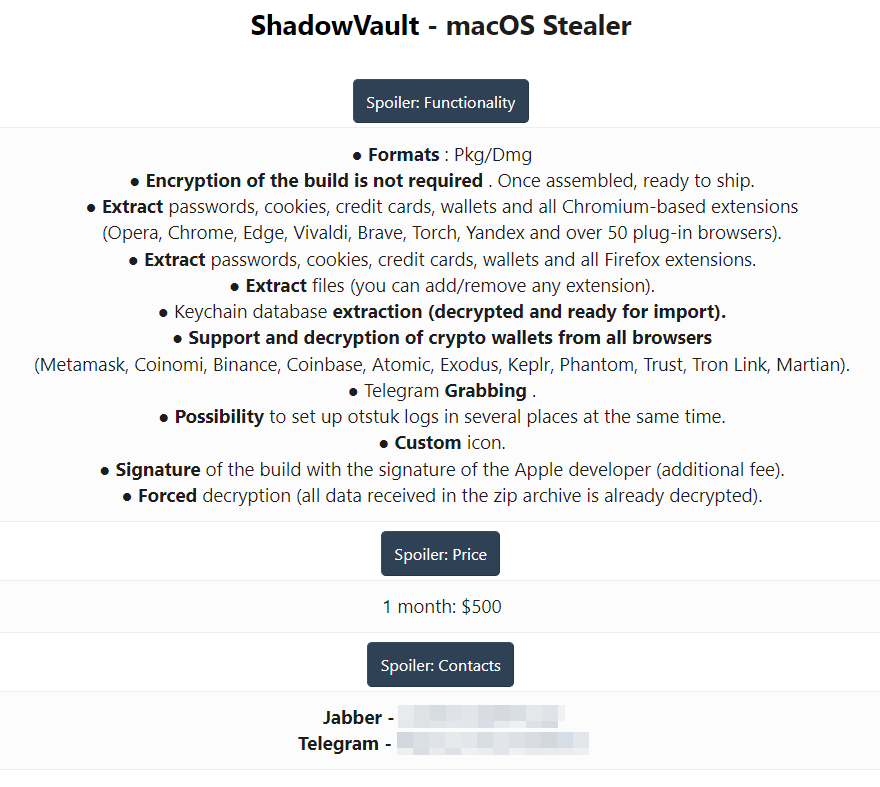
ShadowVault: Security firm Guardz has identified a new macOS infostealer named ShadowVault that is currently being advertised on underground cybercrime forums. Although it's coded for macOS, the malware has all the traits of modern Windows infostealers. It can extract and exfil browser passwords, grab Telegram data, crypto-wallet keys, and, of course, Apple keychains.
Malware technical reports
Clop: Sophos has published a report detailing some of Clop's usual intrusion techniques.
LockBit: Fortinet has a report on the history and evolution of the LockBit ransomware gang.
SCARLETEEL: Sysdig has a follow-up report on the SCARLETEEL cryptomining gang, which they first spotted back in February. The gang is known to use exploits in public-facing web apps to breach cloud environments and deploy their cryptominer. Sysdig says recent attacks are targeting AWS Fargate environments.
PyLoose: Wiz security researchers have discovered a cybercrime group targeting cloud services with a new malware strain named PyLoose. The malware is coded in Python and uses a rare Linux fileless execution technique to deploy cryptominers on cloud computing infrastructure. So far, Wiz says it has found the malware on more than 200 cloud resources.
"The attacker went to great lengths to be untraceable by using an open data-sharing service to host the Python payload, adapting the fileless execution technique to Python, and compiling an XMRig miner to embed its config to avoid touching the disk or using a revealing command line. All these steps suggest that the adversary has a level of sophistication not commonly observed in most publicly documented cloud workload attacks. Therefore, there are no strong indicators that can tie this attack to a specific threat actor."
Sponsor section
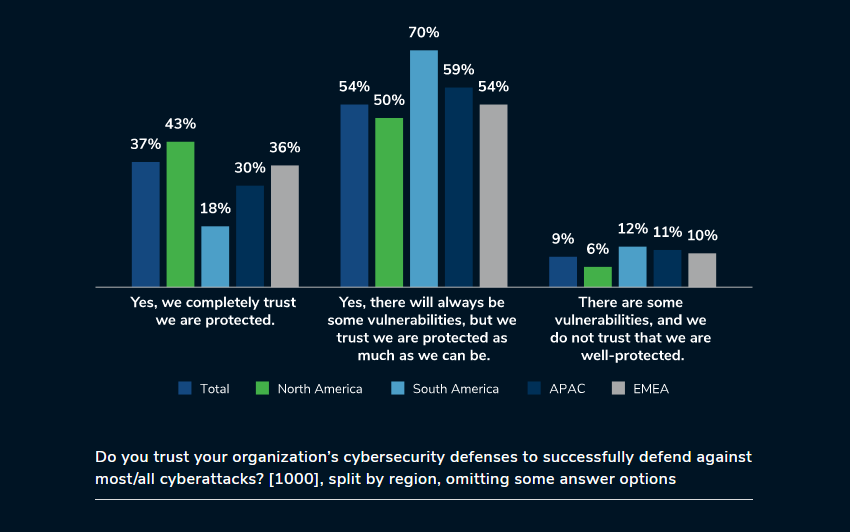
Kroll conducted a survey of 1,000 senior information security decision-makers based in North and South America, APAC, and EMEA. The goal was to understand the current state of cyber defense, the levels of organizational trust, and how true cyber maturity links to trust in facilitating organizations to stay ahead of the curve in a constantly evolving threat landscape.
APTs and cyber-espionage
Transparent Trive: ThreatMon has published a report on recent Transparent Tribe (APT36) phishing campaigns employing malicious PowerPoint files.
ScarCruft: QiAnXin researchers have published a report on the ScarCruft APT's recent abuse of cloud resources for operations, an after-effect following Microsoft's ban on macro-malware.
APT31's Rekoobe backdoor: AhnLab researchers have published a technical analysis of the Rekoobe backdoor used in attacks against Linux systems across South Korea. APT31 is a Chinese cyber-espionage group.
Beijing InfoOps in LATAM: Nisos has identified a network of Twitter accounts operated by the China News Service that were responsible for posting pro-Beijing propaganda across Latin America.
"Some of the accounts promote strategic Chinese state media-linked news content in both Spanish and Portuguese. The network is linked to China News Service and shows signs of coordinated inauthentic behavior, with accounts posting similar or identical content related to China at close time intervals. This indicates they are likely organized through a common operator echoing content mainly from Chinese state-linked media outlets, in an attempt to improve China's image and enhance its policy and diplomatic efforts."
Vulnerabilities, security research, and bug bounty
Citrix ShareFile RCE: Assetnote researchers have discovered a remote code execution vulnerability (CVE-2023-24489) in the Citrix ShareFile file-sharing application. The team's discovery comes after similar applications such as MOVEit, Fortra GoAnywhere, Accellion FTA, and Soliton FileZen have been repeatedly exploited by hackers for data extortion and cyber-espionage over the past three years. Citrix has released a security update last month. According to Assetnote, there are roughly 6,000 ShareFile servers available on the internet.
Foswiki vulnerabilities: usd HeroLab researchers have discovered a suite of vulnerabilities in Foswiki, an enterprise wiki and collaboration platform.
Patch Tuesday: Yesterday was the July 2023 Patch Tuesday. We had security updates being released by Adobe, Apple, Microsoft, Mozilla Firefox, Drupal, VMWare, Citrix, Fortinet, Juniper, Jenkins, and SAP. The Android project, Chrome, GitLab, Cisco, Progress, Mastodon, Ubiquiti, and Zyxel released security updates last week as well.
Microsoft zero-days: This month, Microsoft patched 130 vulnerabilities, including four actively exploited zero-days (CVE-2023-32046, CVE-2023-32049, CVE-2023-35311, and CVE-2023-36874). A fifth vulnerability (CVE-2023-36884) was included in the Patch Tuesday as actively exploited, but did not receive a patch. It is a variation of the Follina vulnerability from last year. Microsoft says the zero-day is being exploited in phishing campaigns by Storm-0978, the group behind the RomCom backdoor, recently linked to multiple espionage campaigns against NATO allies and Ukrainian targets. This most recent zero-day—already called Follina2—appears to have been used in a phishing campaign targeted at attendees of the recent NATO summit in Vilnius, as previously reported by BlackBerry last week.
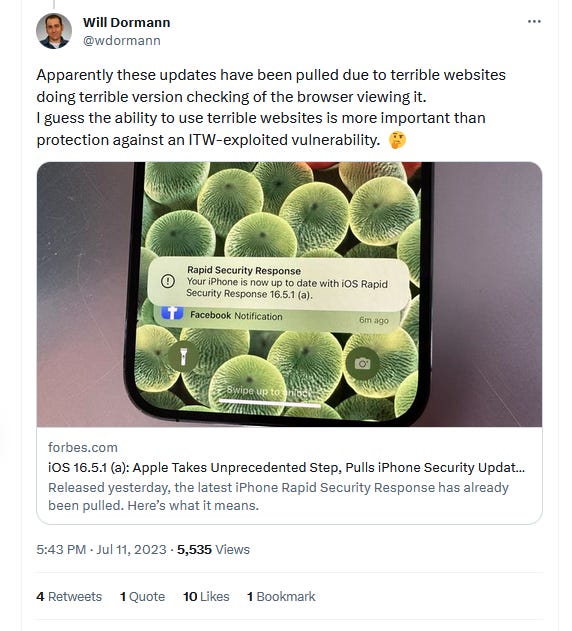
Apple zero-day: The Apple updates rolled out as a Rapid Security Response and fixed a Safari zero-day (CVE-2023-37450) that was also exploited in the wild to deliver payloads via web content. Apple pulled the update a day later after receiving reports of breaking web browsing for some users. The company promised to re-release the patch after fixing the reported issues.
Infosec industry
Acquisition news #1: TPG has acquired Forcepoint's governments and critical infrastructure business division from Francisco Partners for $2.45 billion, more than double what Francisco Partners paid for the entirety of Forcepoint back in 2021.
Acquisition news #2: Honeywell has acquired ICS security firm SCADAfence. The transaction is expected to close in the second half of 2023.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the EU's proposed media freedom act and how one of its goals is to protect journalists from spyware.




