Risky Biz News: Microsoft puts the limelight on another spyware maker—DSIRF from Austria
In other news: Rostelecom hijacks Apple traffic; new Cytrox and NSO incidents discovered in the EU; and fewer ransomware victims are paying.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
On the day representatives from CitizenLab, Google, and Microsoft were in Congress to testify on the dangers posed by commercial surveillance vendors, Microsoft's security teams published a report exposing the hacking tools of another company—namely, Austrian software maker DSIRF.
The revelation that DSIRF was a commercial spyware vendor was news for most international audiences, but German media had been on their case for at least a year and especially focused on the possible ties the company may have with Russia.
Founded in 2016, the company appears to have gone through multiple stages in its six-year history, such as election security, biometrics authentication, and cyber-warfare, before deciding to have a go at the commercial surveillance market.
Microsoft appears to have been tracking attacks carried out with the company's tools since last year, initially grouping this activity under the pseudonym of KNOTWEED before OpSec mistakes allowed it to link some attacks to DSIRF official websites.
Now, after a year of digging around, Microsoft says that DSIRF is the author of powerful malware toolkits like Subzero, Mex, and PassLib.
Of the three, Subzero is the company's main product, comprising of the actual malware deployed on Windows systems once a target is compromised.
According to Microsoft, Subzero and its components are usually deployed on targeted systems using the good ol' technique of spear-phishing, with malicious documents such as PDF and Excel files.
But DSIRF is not your regular script kiddie. Microsoft said the company uses exploit chains that use actual zero-day vulnerabilities, with Subzero being deployed with at least four Windows zero-days. Microsoft also suspects that DSIRF may also be in possession of at least one Adobe zero-day as well, and clues in the malware's code also suggest a browser-based delivery of Subzero payloads for Chrome browser users.
Once a system is compromised, tools like Mex and PassLib are deployed, with Mex being a mash-up of various open-source red team tools typically available on GitHub and PassLib being a custom-developed password stealer "capable of dumping credentials from a variety of sources including web browsers, email clients, LSASS, LSA secrets, and the Windows credential manager."
These tools are provided to DSIRF customers for their operations, but Microsoft said that it also observed the tools being used in attacks from official DSIRF websites and GitHub accounts, which suggests the Austrian company may also be running or at least hosting some of the attack infrastructure on behalf of its customers as well.
Victims of past attacks included law firms, banks, and consultancy firms in countries such as Austria, the United Kingdom, and Panama, the OS maker said.
It's important to note that the identification of targets in a country doesn't necessarily mean that a DSIRF customer resides in the same country, as international targeting is common.
The proliferation of these kinds of tools and services is what has the US scared, especially at the thought of some of these tools being used against its government officials and foreign diplomats. It's certainly happening in Europe [1, 2].
The US has recently taken some steps toward addressing the runaway problem of commercial surveillance vendors, but in the opinion of several experts, it may now be too late for a crowded market that has learned to incorporate in foreign countries, and outside the reach of the US government.
Breaches and hacks
JustTalk leak: Security researchers have found a database belonging to secure instant messaging application JusTalk that contained plaintext messages sent by its users, despite the company's claims that communications are end-to-end encrypted. The database, and the hundreds of gigabytes of data inside, were left exposed online on a Chinese server for months, since January this year, TechCrunch reported.
MSP attack: US-based managed service provider NetStandard shut down services on Tuesday after suffering a cyber-attack. While the nature of the incident has not been confirmed, news of the attack comes after a threat actor published a request on a cybercrime forum last week, looking for help in orchestrating an attack against a large US-based MSP.
Anyone want to guess what this exploit[.]in forum post is about? 💀 Hint: it involves a Managed Service Provider 🤬
— Kyle Hanslovan (@KyleHanslovan) 2:20 PM ∙ Jul 26, 2022
Newport, RI incident: The city of Newport, Rhode Island, disclosed a security breach that took place in early June 2022, when a threat actor gained access to one of its servers and accessed files with information on city employees.
Microleaves leak: Microleaves, a ten-year-old proxy service that lets customers route their web traffic through millions of Microsoft Windows computers, recently fixed a vulnerability in their website that exposed their entire user database, Brian Krebs reported. Microleaves claims its proxy software is installed with user consent, but data exposed in the breach showed otherwise.
General tech and privacy
Google delays cookie phase-out once more: Google said this week that it will get rid of support for third-party cookies—a way online advertisers use to track users online—in the Chrome web browser in 2024. This is the second time that Google has delayed the cookies phase-out plan after it initially planned to replace third-party cookies with its Privacy Sandbox API in 2022, only to push it back to 2023 and now to 2024.
France closes Facebook investigation: France's data protection watchdog, CNIL, said today that it is closing its Facebook investigation after the company added a button to its cookie popup that will allow users to refuse non-essential cookies. CNIL previously fined Facebook €60 million earlier this year after the company, at the time, was requiring users to go through multiple steps to use only essential cookies and block the use of optional/tracking ones.
Rostelecom hijacks Apple traffic: MANRS, an industry security group specializing in BGP routing security, said that Rostelecom appears to have hijacked Apple traffic. The incident took place earlier this week and lasted 12 hours before Apple engineers stepped in to mitigate the issue from their side.
Government, politics, and policy
New Cytrox incident: Nikos Androulakis, a member of the EU Parliament and the president of Greece's second-largest opposition party (PASOK), filed a complaint with the country's Prosecutor's Office of the Supreme Court on Tuesday, claiming that his device had been infected with Predator, a commercial spyware product sold by North Macedonian company Cytrox. Androulakis said he discovered the infection in June after he contacted a cybersecurity unit in the European Parliament that was founded earlier this year and which is tasked with checking the devices of EU MPs for commercial spyware products. According to the NYT, this marks the unit's first-ever positive detection in more than 200 devices it scanned so far.
New NSO incident: On the same note, EU Justice Commissioner Didier Reynders said he received a notification last year from Apple that his device was compromised with Pegasus, a commercial spyware product sold by Israeli company NSO Group.
CISA+SSSCIP: The Cybersecurity and Infrastructure Security Agency (CISA) and the Ukrainian State Service of Special Communications and Information Protection of Ukraine (SSSCIP) signed an agreement on Wednesday to strengthen collaboration on shared cybersecurity priorities.
Cybercrime and threat intel
Spain arrests RAR hackers: Spanish authorities detained two suspects on charges of hacking the country's radioactivity alert network (RAR). The two suspects—previously employed by Spanish authorities to manage the RAR network—disrupted the activity of more than 300 out of 800 radioactivity detection sensors spread across Spain in a series of attacks that took place between March and June 2021. [Additional coverage in The Record]
BEC scammers detained in Hungary: Authorities in Hungary said this week that they detained almost 100 suspects in a crackdown against a group of BEC scammers specializing in invoice fraud. Europol said the crackdown is a result of two joint operations—Operation Wine Cellar and Operation Theatre—carried out in November of last year, but whose details were released this week due to operational reasons.
ShinyHunters arrest: A suspected member of the ShinyHunters hacking group was detained earlier this year at the airport in Rabat, Morocco, while trying to take a flight to Brussels, Belgium. Authorities have identified the suspect as Sébastien Raoult, a 21-year-old French student from the city of Epinal in eastern France.
Romance scammers: Three Nigerians pleaded guilty in Ireland this week to defrauding a 66-year-old woman of more than €282,000. The three suspects approached the victim via the PlentyOfFish dating website and exchanged more than 800 pages of private messages over a period of six months. Of the money the victim transferred to the scammers, €278,760 was returned because of a transfer error. The victim filed a report with authorities after the scammers sent her to Dubai for a meeting, where she was asked for another $650,000, RTE reports.
Fewer ransomware victims pay: Data compiled by ransomware negotiation company Coveware suggests that fewer victims of a ransomware attack have made payments to their attackers in the second quarter of 2022, which has also contributed to the decrease of the average ransom payment over that period by 51% to $36,360. In addition, Coveware also reports that while a year ago, only a small number of ransomware variants were capable of encrypting non-Windows-based operating systems, today, almost all RaaS variants have stable Windows, Linux, and eSXI versions.
LockBit dominated 2022: According to a report from Sekoia, the LockBit ransomware operation has accounted for the most publicly-disclosed ransomware attacks this year.
LockBit adopts new tactic: The operators of the LockBit ransomware appear to have adopted a new tactic of intentionally leaking the private conversations between their operators and the victims of their attacks as another way of putting pressure on the victim to pay.
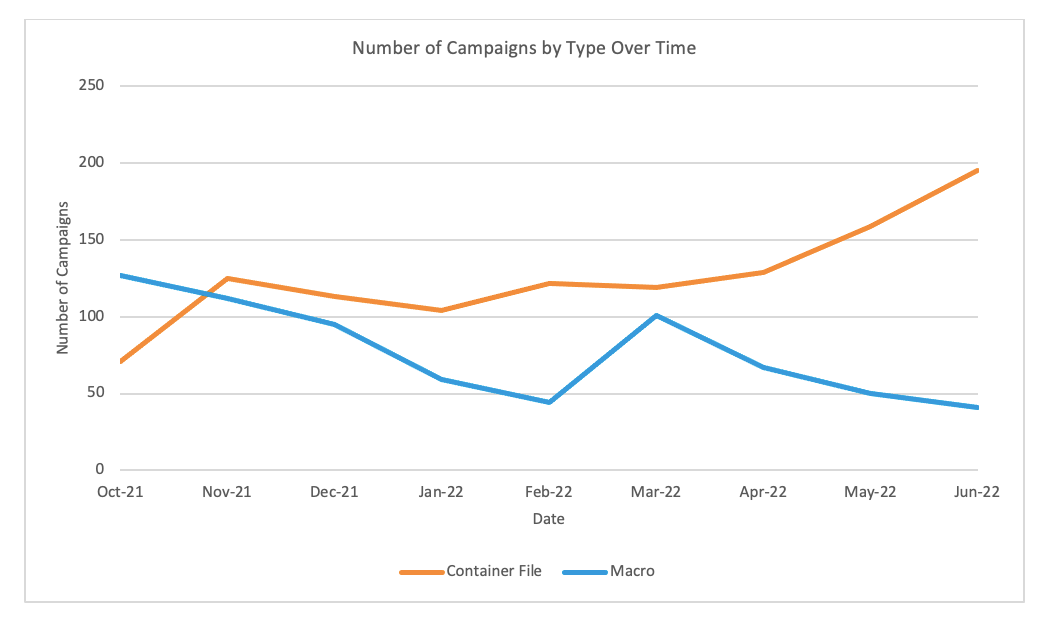
Email threat landscape changes: In a report on Thursday, email security provider Proofpoint said that the use of VBA and Excel 4 macros for email malspam decreased around 66% from October 2021 through June 2022, after Microsoft took steps to disable these features by default for most of its users. Instead, the company is now seeing threat actors switch to using other malware delivery methods that rely on container files such as ISO and RAR, and Windows Shortcut (LNK) files.
IPFS adoption among phishing actors: Trustwave reports that after several cloud service providers started offering support for the IPFS peer-to-peer protocol, threat actors have started abusing these services to create new types of "cleaner" phishing URLs. In addition, Trustwave also anticipates that email spam groups will also adopt this new technique, as it allows them to "easily camouflage their activities by hosting their content in a legitimate web hosting services or use multiple URL redirection techniques to help thwart scanners using URL reputation or automated URL analysis."
New PhaaS: IronNet researchers have discovered a new phishing-as-a-service platform named Robin Banks that comes with built-in templates for attacking customers of major US banks (Bank of America, Capital One, Citibank, Wells Fargo) and various online services (Google, Microsoft, Netflix).
New malicious npm packages: Kaspersky researchers said they discovered four malicious JavaScript libraries uploaded on the npm portal. According to the researchers, the npm packages would download and install Python and JavaScript-based malware on infected systems.
The Python malware is a modified version of an open-source token logger called Volt Stealer. It is intended to steal Discord tokens from infected machines, along with the victim's IP address, and upload them via HTTP. The JavaScript malware we dubbed "Lofy Stealer" was created to infect Discord client files in order to monitor the victim's actions. It detects when a user logs in, changes email or password, enables/disables multi-factor authentication (MFA) and adds new payment methods, including complete bank card details. Collected information is also uploaded to the remote endpoint whose address is hard-coded.
Malware technical reports
Matanbuchus: CyberArk researchers have published a technical breakdown of the Matanbuchus loader, which they described as possessing "many advanced techniques" not found in other similar malware loaders.
Proxyware deployments: South Korean security firm AhnLab has published details on a malware distribution campaign that installs proxyware applications on victims' devices to use their systems as proxies in pay-for-traffic proxy networks like Peer2Profit and IPRoyal. Among victims observed by AhnLab, MSSQL database servers were also infected.
CISA Log4Shell MAR: CISA published on Wednesday a malware analysis report (MAR) on a malicious campaign utilizing the Log4Shell vulnerability to breach VMWare Horizon and Unified Access Gateway (UAG) servers.
Green Stone: InQuest researchers have published a report on Green Stone, a set of malicious documents that have been uploaded on VirusTotal from an Iranian IP address.
APTs and cyber-espionage
SharpTongue: Cyber-security firm Volexity said in a report on Thursday that a North Korean threat actor it is tracking as SharpTongue has been using a malicious Chrome, Edge, and Whale (South Korean web browser) extension called SHARPEXT as a way to steal emails from a victim's browser as they read their webmail. Volexity said the threat actor has been using this technique since September 2021, and it may be connected to the activity of other North Korean APTs like Kimsuky and BabyShark.
Volexity frequently observes SharpTongue targeting and victimizing individuals working for organizations in the United States, Europe and South Korea who work on topics involving North Korea, nuclear issues, weapons systems, and other matters of strategic interest to North Korea.
Arrest issued for FSB hacker: German officials secretly issued an arrest warrant for a Russian FSB officer for his role in orchestrating cyber-attacks against German critical sector operators, including power grid operator EnBW in the summer of 2017. Reports in German media identified the suspect as Pawel A., and he appears to be Pavel Aleksandrovich Akulov (Павел Александрович Акулов), also indicted in the US earlier this year as a member of the Berserk Bear (Dragonfly, Energetic Bear, Crouching Yeti) APT, for their attacks against US critical infrastructure.
Vulnerabilities and bug bounty
Code reuse aftermath: Cisco Talos said it found four vulnerabilities in open-source router firmware packages and drone programming tools. The company said the root cause of all four issues was a piece of code that all projects had taken from an open-source library owned by Broadcom.
Samba vulnerabilities: The Samba open-source project has released security updates, including a fix for a vulnerability (CVE-2022-32744) that can be used to forge password change requests for any user on an AD server and use this to change the password of administrator accounts to gain total control over the domain.
Infosec industry
Human Security merges with PerimeterX: Bot mitigation company Human Security announced a merger with PerimeterX, a company specialized in detecting account takeover and automated fraud attacks.
Aaaaand... it's gone: Substack has suspended a newsletter (that we featured in our previous edition) dedicated to doxing cybercrime operators and named Behind the Keyboard.
For those who were following the Substack newsletter, it’s gone. They removed, not just a single post, but the whole account.
— pancak3 (@pancak3stack) 8:13 PM ∙ Jul 28, 2022




