Risky Biz News: Microsoft mitigates PPL exploit after four years
In other news: Dutch government fears China might turn off its solar panels; new UEFI rootkit targets ASUS and Gigabyte motherboards; and WebAssembly used for crypto-mining in the wild.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Almost four years after James Forshaw, a security researcher with Google's Project Zero team, published a blog post detailing a new exploit in the Windows Protected Process Light (PPL) security mechanism, Microsoft added mitigations for this technique in insider builds of the Windows 10 and Windows 11 operating systems.
These secret patches were spotted last month by a GitHub user and confirmed over the week by Clément Labro, a French penetration tester and the author of PPLdump, a tool that weaponized and automated PPL attacks using Forshaw's 2018 technique.
What are PPLs?
Added in Windows 8.1 in mid-2013, PPLs are a special class of processes that are protected and can't be tampered with by normal Windows processes, even if these processes run with SYSTEM/administrator privileges. Only other PPLs or PPs (protected processes) can interact with PPLs.
In theory, PPLs were added to Windows alongside PPs as a way to protect Windows services and even third-party apps handling sensitive operations. For an app to receive a PPL status for its process, they have to register with Microsoft, pass authentication and authorization procedures, and only then use a special ELAM driver that grants its process PPL status.
Antivirus and security software makers were among the most common deployers of PPLs, as this allowed them to protect their software from being tampered with or deactivated by malicious threat actors, even if the threat actor had gained admin rights on a compromised machine.
Both PPs and PPLs protected their processes by only loading DLL files that were signed appropriately and from a small list of locations stored on disk, with PPLs also being allowed to load DLLs from a memory cache location known as "\KnownDlls."
In 2018, Forshaw found that there was a way to abuse the \KnownDlls loading mechanism to effectively allow non-PPLs to dump the memory of PPL processes, opening the door for hijacking the PPL by a malicious threat actor.
While Microsoft delivered a patch for Forshaw's findings at the time, the PPLdump tool found and used other creative ways to weaponize the initial technique—until this month.
"The conclusion is that PPLs now appear to be behaving just like PPs and therefore no longer rely on Known DLLs," Labro said over the weekend, describing what happened in Microsoft's secretive recent patch.
Great post and kudos to MS for mitigating this technique! I love dead techniques.😃
— Matt Graeber (@mattifestation) 10:54 AM ∙ Jul 25, 2022
While this is definitely good news, defenders shouldn't take it as an easy win, as even Labro doesn't rule out the possibility of finding new ways to attack Microsoft's PPL security mechanism.
"[T]his tool leveraged only one weakness of PPLs, but there is a couple of other userland issues we can probably still exploit. So, from my standpoint, it is also an opportunity to start working on another bypass," the researcher said.
Breaches and hacks
Entrust incident: In an email sent to customers last week, security access software maker Entrust said it fell victim to a cyber-attack after a threat actor gained access to its IT network. [Additional coverage in SecurityWeek]
Entrust security incident dated June 18th.
— Dominic Alvieri (@AlvieriD) 2:03 PM ∙ Jul 21, 2022
Entrust blog still down on your left and official statement on your right.
No one seen taking credit to date.
@Entrust_Corp
#cybersecurity #infosec
@Cyberknow20 @GossiTheDog
@campuscodi @vxunderground @FBI
Attack on Italy's tax agency: The operators of the LockBit ransomware gang claimed to have breached, encrypted, and stolen data from Italy's tax and revenue agency. However, Sogei, the Italian IT company that services the Italian government, denied LockBit's claims and said in a statement that "no cyberattacks have occurred or data stolen from the financial administration's technological platforms and infrastructure." [Additional coverage in The Record]
WordFly ransomware attack: Sixteen days after being hit by a ransomware attack, email provider WordFly is still offline, according to the company's status page.
Another crypto heist: A threat actor has stolen more than $6 million worth of cryptocurrency from decentralized music platform Audius, blockchain security firm SlowMist reported over the weekend. In a post-mortem of the incident, Audius said the attacker exploited a vulnerability in its platform, siphoning funds from its platform, despite the presence of a community governance-based system.
Unverified Campaygn leak: Security researcher Bob Diachenko reported on Tuesday that social media analytics platform Campaygn exposed more than 231 million records, including details on "popular social media influencers." Nine servers were exposed, which have now been secured. The company has yet to confirm the incident.
Titanium ICO: The CEO of the Titanium blockchain company pleaded guilty this week to defrauding investors of more than $21 million during the initial coin offering (ICO) for the BAR coin.
General tech and privacy
TikTok confirms Chinese staff accessed US user data: In what appears to be a slip of the tongue moment, ByteDance appears to have confirmed reports from earlier this month that its Chinese employees had access to its US users' personal data, despite promises and claims that they would not.
NEW: In an email to congressional staff, TikTok provided an update on “minimizing” its ongoing transfer of U.S. user data to China.
— Brendan Carr (@BrendanCarrFCC) 3:57 PM ∙ Jul 25, 2022
This raises lots of questions—including ones about the non-“minimized” data flows that TikTok has sent to China.
The federal government must act.
Some AWS users get a free security key: AWS announced earlier this month that US-based AWS account root users who spent more than $100 each month over the past three months are eligible to receive a free security key to help them secure their accounts.
First-ever warrant of its kind: Forbes reported last week that the FBI obtained a first-ever warrant of its kind that forced a suspect to use his face to unlock a device—in this case, forcing a man accused of possessing child sexual abuse material to unlock access to their Wickr encrypted messaging app using their Apple's FaceID system.
Nail polish thwarts NSA: Purism, a vendor of privacy-focused products, said in a blog post last week that its engineers apply glitter-based nail polish on screws as a way to prevent threat actors from opening and tampering with their devices while in transit to their customers. The company said it uses glitter-based nail polish because the glitter also works to create a unique pattern on the screws, preventing the threat actor from re-applying a new layer on top, as the pattern would differ.

Government, politics, and policy
Dutch govt looks into the danger of using Chinese-made solar panels: Members of the Dutch Parliament have asked the Dutch government to look into the possible national security risk of using Chinese-made solar panels inside the country's power grid. Officials cited a news article published this Sunday by Dutch magazine Follow the Money as the main cause of their concern. FTM reported how a Dutch security researcher found a super-admin password that allowed him to enter the IT network of the panel's manufacturer—Chinese company SolarMan—from where he could take full control of all the company's products across the globe. FTM also reported how the company ignored the researcher's findings for months until the Dutch embassy in China stepped in and finally got Solarman to fix its issue. But the discovery of this super-admin panel alongside the ongoing Ruso-Ukrainian war has made FTM reporters and Dutch officials alike also ask themselves if the Netherlands isn't in danger of exposing its power grid to a situation where the Chinese government might force SolarMan to disable solar panels inside the country in the aftermath of a possible political confrontation, similarly to how Russia has now cut-off gas supply across Europe in the aftermath of EU sanctions. The same question could also apply to Australia, where these panels are also widely used.
US bill to crack down on spyware firms: The US House of Representatives is set to vote on a bill to crack down on and even ban firms that sell spyware from working with the US government, Cyberscoop reported.
No more victim-blaming: Following the release of a report that found that most victims tend to blame themselves after falling victim to a financial scam, the AARP (formerly the American Association of Retired Persons) and FINRA (the Financial Industry Regulatory Authority) said they plan to team up and work to shift the language and support services provided to victims of financial fraud.
No More Ransom reaches six years: On the six-year anniversary of the No More Ransom project, Europol said the project has now released 136 free decryption tools for 165 ransomware variants, helping more than 1.5 million people successfully decrypt their devices without needing to pay attackers.
Cybercrime and threat intel
Attack technique breakdown: German cyber-security company DCSO published a report on Monday detailing a relatively unknown attack technique recently employed by several threat actors such as SVCReady, Gozi, and IcedID to deploy their payloads. The technique uses Word document properties to store shellcode that is later used in the attack chain.
June malware reports: Russian cyber-security firm Dr.Web has published reports on malware trends for the month of June 2022. The company said that while ransomware activity grew by 17.6% from the previous month, adware remained the most pervasive threat on the desktop. On the other side of the spectrum, adware activity decreased on mobile devices, but the company also found 30 adware trojans uploaded on the official Google Play Store that, it says, had been downloaded by almost 10 million users.
Malicious IIS extensions: The IIS maker itself, Microsoft, published a blog post on Tuesday with tips on how to spot and remove malicious IIS extensions that are commonly used as a backdoor and persistence mechanism on compromised IIS servers.
WebAssembly used for crypto-mining in the wild: A Sucuri report last week has found a web-based cryptojacking script that uses WebAssembly to run a cryptocurrency miner in the user's browser when they access a compromised website. Sucuri said the script was live on 207 websites at the time of their blog post last week.
Underground bots for stealing OTPs: Recorded Future has a report out on the avalanche of automated bots offered in underground cybercrime communities that can be used to bypass one-time-passcodes (OTPs) for various online services.
Malware using Discord's CDN: Intel471 has put together a list of malware families that are abusing the Discord file-hosting CDN to host malicious payloads for their campaigns. The list currently includes the likes of PrivateLoader, Discoloader, Colibri, Warzone RAT, Modi Stealer, Raccoon Stealer, Smokeloader, Amadey, Agent Tesla, GuLoader, Autohotkey, and njRAT, according to the company.
Doxing cybercrime operators via newsletter: Over the weekend, a threat intel analyst who likes to go online by the pseudonym of Pancak3 launched a newsletter where they dox the identities of various cybercrime operators. Currently listed on the Substack website are reports on carding fraudsters, Conti and REvil operators, the creator of the Predator the Thief infostealer, the EvilCorp cybercrime cartel, and others.
Malware technical reports
Hive ransomware: Italian security firm Yoroi has published a technical write-up on the Hive ransomware.
CosmicStrand: Kaspersky's GReAT team published Monday a report on CosmicStrand, a UEFI rootkit that has been deployed in the wild since at least 2016 by what appears to be a Chinese cybercrime group. Kaspersky said the rootkit can infect ASUS and Gigabyte motherboards using the H81 chipset. Mark Lechtik, a former Kaspersky malware researcher who worked on the malware before he left the company, also published a Twitter thread with additional insight into this new threat.
[1/n] Before I left Kaspersky, I had one more UEFI related research along with @vaber_b in the pipeline that wasn't released thus far. This research on a little known UEFI firmware implant has now become public with the amazing help of @JusticeRage. A 🧵
— Mark Lechtik (@_marklech_) 10:42 AM ∙ Jul 25, 2022
Symbiote: Security researcher @GeeksCyber has published another one of their great technical deep-dives, this time in the Symbiote Linux malware.
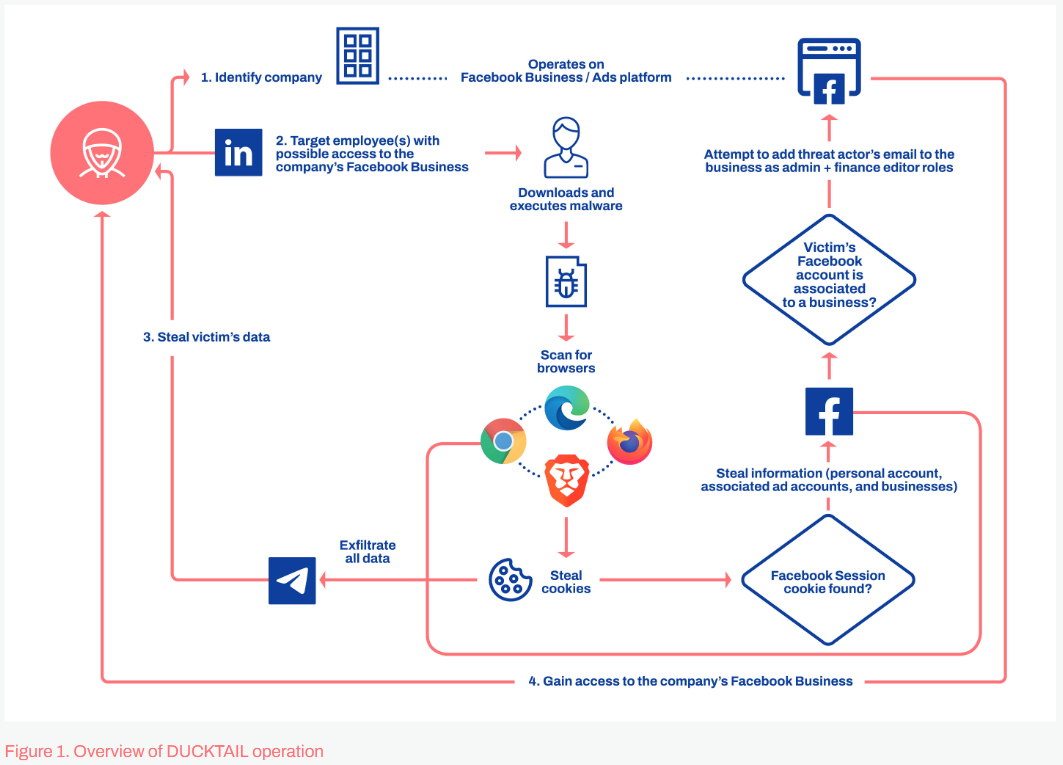
DUCKTAIL: WithSecure (F-Secure) researchers published a report on Tuesday on DUCKTAIL, a new infostealer they've observed in the wild that targets and infects victims likely to have access to Facebook Ads or Business accounts. WithSecure says the threat actor appears to be operating out of Vietnam and targets victims via their LinkedIn accounts. The threat actor has been active since late 2018 and has been using the DUCKTAIL malware in attacks since the second half of 2021.
APTs and cyber-espionage
Kimsuky in South Korea: Chinese security firm QiAnXin has published a report on the Kimsuky APT's recent spear-phishing operations targeting South Korean organizations.
Operation Tejas: The same company also published a report on the operations of two APT groups known as Manling Flower (APT-Q-41) and Diamondback (APT-Q-39) against targets across South Asia.
Vulnerabilities and bug bounty
PrestaShop zero-day fix is out: The team behind the PrestaShop e-commerce CMS released a security update on Monday to address an actively exploited zero-day vulnerability that was discovered last week. Tracked as CVE-2022-36408, the zero-day was being used to add malicious code to PrestaShop websites via an SQL injection vulnerability and then steal payment information from checkout forms.
Nuki smart lock bugs: NCC Group researchers said they found and help fix 11 issues in Nuki smart lock products.
FileWave MDM bugs: Security firm Claroty has also disclosed two vulnerabilities in the FileWave mobile device management (MDM) system, used across more than 1,100 enterprises. Both vulnerabilities are remotely exploitable and allow an attacker to bypass authentication mechanisms and gain full control over the MDM platform and its managed devices.
2022 vulnerabilities report: Palo Alto Networks has published the 2022 Unit 42 Incident Response Report, a study of more than 600 incidents the company's analysts responded to over the past year. Here are some of its main conclusions:
- Phishing (37%) and software vulnerabilities (31%) were the top initial access entry points for most incidents.
- ProxyShell accounted for 55% of all the exploited vulnerabilities last year.
- Attackers, both script kiddies and sophisticated groups, moved quickly to weaponize a vulnerability once public PoCs were available.
- Time-to-patch got shorter this year, with attackers starting scans for some vulnerabilities as fast as 15mins after CVEs are announced.
Infosec industry
Tool release: Cyber-security firm Exein has open-sourced a new tool named Pulsar, which the company described as a powerful and fast runtime security observability framework designed for IoT devices, running on top of the eBPF feature. The code is also available on GitHub.
ODAT ported to C#: A security researcher named InitRoot has ported the Python-based ODAT tool to C#, so it can run smoother on Windows. ODAT stands for Oracle Database Attack Tool and is a penetration testing tool used for testing and breaking into Oracle-based database servers.
Free toy to break: Mandiant released a vulnerable-by-design Azure lab environment where security researchers can test their red team attacking and blue team detecting capabilities.
Did someone clone you?: Dutch security researcher Wesley Neelen has launched a new tool called "Did someone clone me" that uses custom links embedded inside original websites to detect when threat actors are using clones of the legitimate site for phishing attacks.
Do you want to get notified ones your website is cloned and used in a phishing attack? Check out my project (free to use):
— Wesley (@wesleyneelen) 10:35 AM ∙ Jul 25, 2022
👉 go to didsomeoneclone.me
👉 fill in the form (website + email address)
👉 add the generated link to your website
youtu.be/Vn6cuEaXwYw




