Risky Biz News: Microsoft disrupts Bohrium APT infrastructure
In other news: Russia wants to jail execs whose companies get hacked; Edge and Firefox get new security features; and the apes are gone again.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Microsoft's Digital Crimes Unit (DCU) said on Friday that they disrupted infrastructure operated by Bohrium, a cyber-espionage group operating out of Iran.
Amy Hogan-Burney, DCU General Manager, said the DCU legal team successfully obtained a court order that granted Microsoft control over 41 domains used by the Bohrium group in spear-phishing operations.
Important work by the @Microsoft Digital Crimes Unit to share today. Our team has taken legal action to disrupt a spear-phishing operation linked to Bohrium, a threat actor from Iran. The court filings can be found here:
— Amy Hogan-Burney (@CyberAmyHB) 4:29 PM ∙ Jun 2, 2022
"Our DCU investigation found Bohrium targeted customers in the US, Middle East, and India. Targets come from sectors including tech, transportation, government, and education," Hogan-Burney said.
The Microsoft exec said the group's members used fake social media profiles, often posing as recruiters, and lured employees at targeted organizations on one of the 41 malicious sites. Here, they tried to collect their personal information, which they later used in subsequent email attacks that sought to infect the victims with malware.
To date, Microsoft's DCU team has used the US court system to seize domains and server infrastructure from more than two-dozen cybercrime and espionage groups alike.
Breaches and hacks
Ukrainian TV station hack: Russian hackers have breached the systems of Ukrainian TV station OLL and have broadcast Russian propaganda during the Wales-Ukraine soccer match that decided which of the two teams will attend the World Cup later this year. OLL TV confirmed the incident in a Facebook post, took down its feed, and live-streamed the game on its YouTube channel. (via @cyber_etc)
The apes are gone, again: A threat actor stole 32 NFTs from the Bored Ape Yacht Club collection after they managed to compromise the Discord account of one of its community managers. The threat actor used this compromised account to share a phishing link through which they gained access to BAYC owners' cryptocurrency wallets. From there, they misappropriated the NFTs and also allegedly stole an additional $145,000 worth of Ether. This is the second hack of BAYC NFTs over the past two months after hackers also stole 54 Bored Ape NFTs valued at more than $13.7 million in April.
🚨BAYC & OtherSide discords got compromised‼️
— OKHotshot (@NFTherder) 10:46 AM ∙ Jun 4, 2022
Seems because Community Manager @BorisVagner got his account breached, which let the scammers execute their phishing attack. Over 145E in was stolen
Proper permissions could prevent this
General tech and privacy
Google privacy settlement: Illinois residents are eligible to receive part of a $100 million settlement after an Illinois judge found that Google broke the state's Biometric Information Privacy Act after the tech giant used a face regrouping tool in the Google Photos app without users' express permission. Claims can be submitted here.
Telegram privacy accusations: De Spiegel reported last week that instant messaging service Telegram shared the data of some of its users with the German Federal Criminal Police Office (BKA). The report is the first known instance where Telegram has collaborated with the BKA. The German newspaper said the cooperation was related to cases of child abuse and terrorism.
WhatsApp threatens to leave the Netherlands: Facebook has threatened to pull its WhatsApp service from the Netherlands if the local government continues with its plan to force the company to add a backdoor to its service, local media reported.
Microsoft Edge network service sandbox: Microsoft's Edge web browser now ships with a separate sandbox system for the browser's network component. The feature shipped with Edge v102 but is disabled by default while its performance is still being tested. The feature previously shipped with Chrome in April, in v100, where it caused some issues in its initial rollout.
New Firefox privacy feature: Mozilla plans to add a new privacy feature to Firefox v102, set to be released later this month. The new feature is named "Query Parameter Stripping," and works by automatically removing tracking parameters from URLs to improve user privacy. The feature has been available since Firefox v96 but will be enabled by default for all users in the next v102 release. The Brave browser also has a similar feature.
1Password joins FIDO: The 1Password software company, maker of the eponymous password management utility, has formally joined the FIDO Alliance, the industry group behind the new WebAuthn standard.
Government, politics, and policy
Russia gets tough on privacy: The Russian Ministry of Digital Development is working on a new legislation draft that will make tech company execs personally liable for the improper collection and storage of the biometric data of Russian citizens. According to Kommersant, Execs risk fines of up to 300,000 rubles, a ban from holding certain positions, forced labor, and even up to 10 years in prison. The draft legislation comes after last month, in May, Russia also made execs personally liable for their companies' lacking IT security, with similar prison sentences on the table for severe security breaches.
Australia’s new cyber minister: Australia now has a dedicated minister for cyber security after Australia’s new Prime Minister Anthony Albanese appointed Clare O'Neil as the Minister for Home Affairs and Minister for Cyber Security last week.
Cybercrime and threat intel
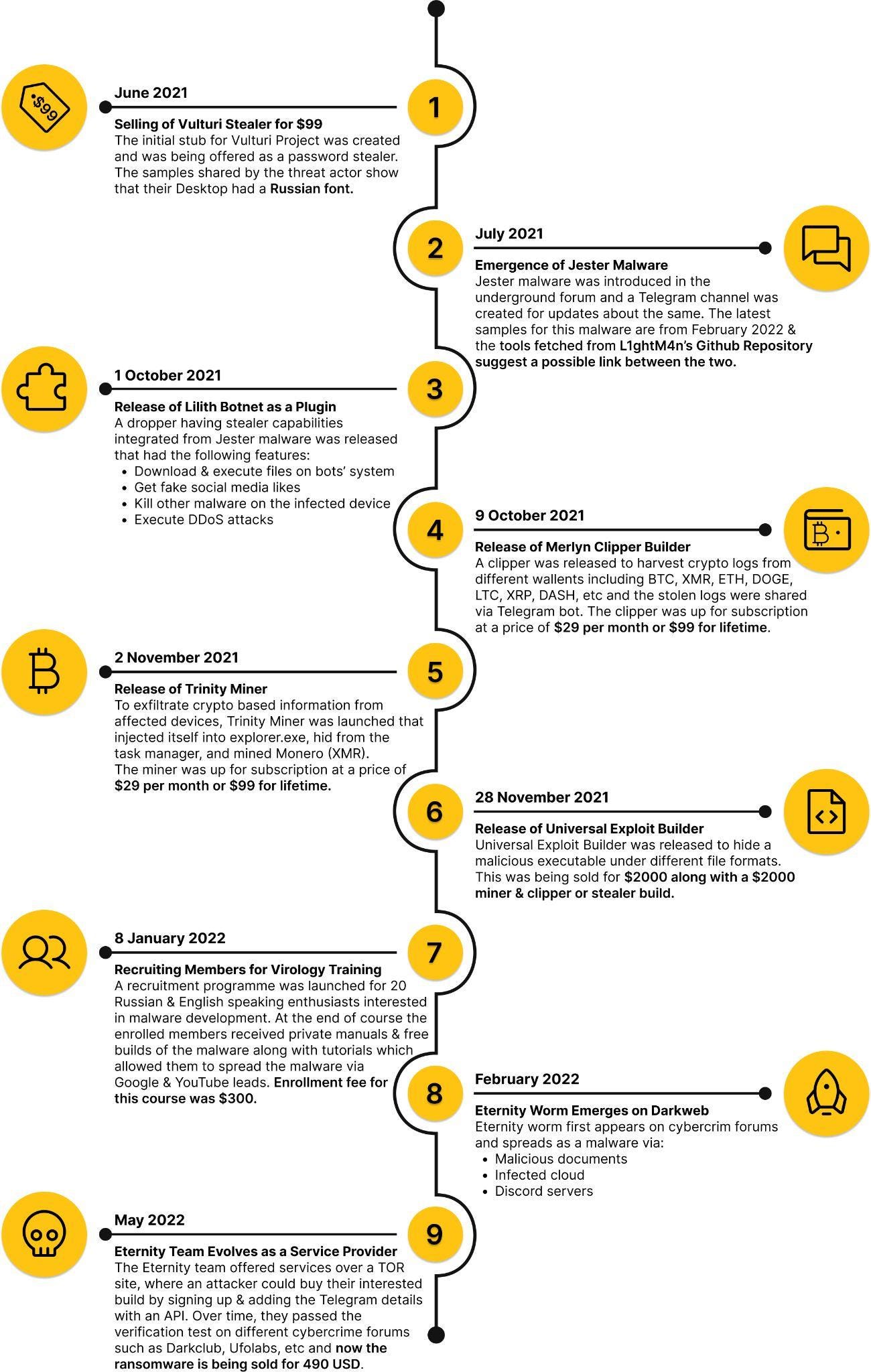
EternityGroup: CloudSEK has published a report on the timeline and evolution of Eternity, a financially motivated threat actor group selling worms, stealers, DDoS tools, and ransomware builders.
Pysa research: According to DataBreaches.net, the Pysa ransomware gang dumped the data of more than half-of-dozen schools last year before the group shut down their leak site.
Windows RDP brute-forcing: A recent report from TRUNC found that 75% of the RDP brute-force attacks the company registered over the past week tried to gain access to their system via the "Administrator" account.
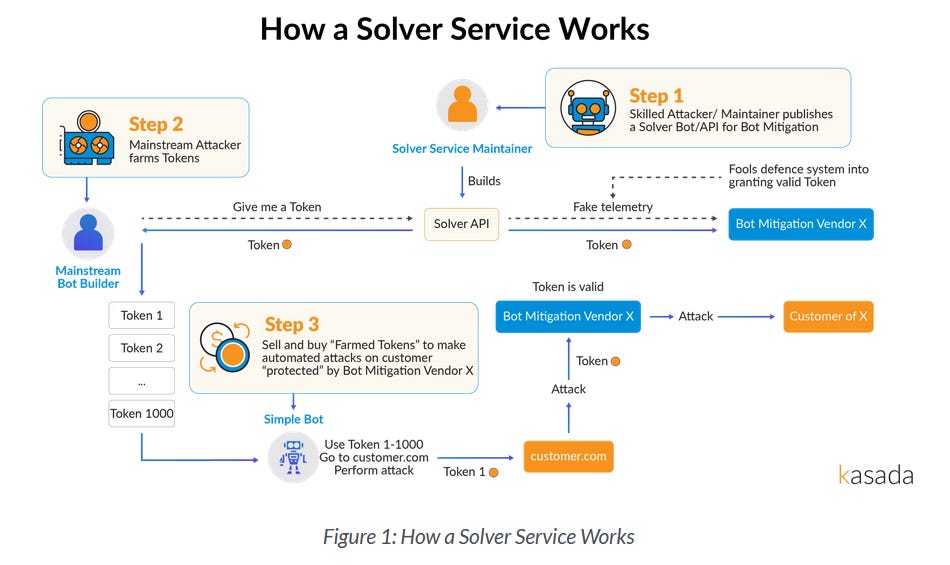
Solver services: Bot detection and mitigation service Kasada said that it detected a 750% rise in the use of "solver services" to bypass existing bot detection systems. These solver services are typically maintained by cybercrime groups and provided as a paid service to other groups that want to engage in fraud against an online service, such as online retail stores, social networks, and others.
Malware technical reports
APTs and cyber-espionage
GADOLINIUM (APT40): Avast published a report last week on an email spear-phishing campaign that hit an Australian ISP and which weaponized the Follina Office zero-day (CVE-2022-30190). Microsoft linked this campaign to the GADOLINIUM (APT40) group.
GADOLINIUM/APT40 activity shown in a good writeup by Avast. GADOLINIUMs focus on the South Pacific continues…
— bk (Ben Koehl) (@bkMSFT) 5:39 PM ∙ Jun 3, 2022
APT-Q-36: QiAnXin researchers have published a report on a recent campaign launched by the APT-Q-36 threat actor, also known as PatchWork or White Elephant.
Vulnerabilities and bug bounty
Google GCP VRP: Google has announced the winners of its Google Cloud Platform Vulnerability Research Program for 2021. The first-place prize ($133,337) went to Sebastian Lutz, who found a bug in Identity-Aware Proxy (IAP) that an attacker could have exploited to gain access to a user's IAP-protected resources by making them visit an attacker-controlled URL and stealing their IAP authentication token.
U-boot vulnerabilities: NCC Group researchers have published a technical analysis of CVE-2022-30790 and CVE-2022-30552, two vulnerabilities in U-Boot, a boot loader popular in some Linux-based embedded systems such as ChromeOS and Android devices.
Infosec industry
CodeSec is now free: Contrast Security has made its CodeSec code-scanning service free to use.
New tool: France's ANSSI cybersecurity agency has open-sourced another tool for the security community. The tool is called AnoMark and can be used to detect anomalies in command-line arguments run on a system.




