Risky Biz News: Microsoft budges on Windows 11 Recall
In other news: Apple to add a password manager; DJI to disable flight data syncing for US drones; another stalkerware app gets hacked.

This newsletter is brought to you by Detection-as-Code company Panther. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Breaches, hacks, and security incidents
GetResponse data breach: The email marketing platform GetResponse disclosed a security breach after a threat actor gained access to one of its employees' accounts. The company says the attacker used the account to pivot to less than 10 of its customers. So far, the GetResponse breach has been linked to at least one other breach—at cryptocurrency platform CoinGecko. The company says the hacker stole the email addresses of almost two million CoinGecko subscribers.
LendingTree breach: Loan comparison site LendingTree has confirmed that its QuoteWizard subsidiary had data stolen from its Snowflake account. [Additional coverage in TechCrunch]
Bangladesh data leak: The Bangladesh intelligence agency has caught two police officers from its anti-terror unit selling citizen data to criminals on Telegram. According to TechCrunch, the officers sold both PII and classified data via a Telegram channel. The Bangladesh government says the two officers had access to government systems suspended as they are being investigated. The NTMC intelligence agency caught the two after reviewing logs of its own systems.
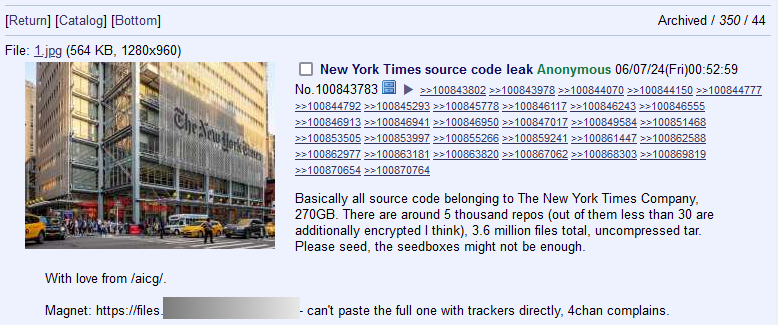
NYT & Wordle leak: A threat actor has leaked the source code for the New York Times after one of the company's workers allegedly left a private GitHub access token in a public code paste. The leaked data allegedly includes the source code of the company's public website, mobile apps, and even its Wordle game. The dump contains 270GB of data, with most being unencrypted.
Pre-election DDoS attacks: A pro-Kremlin "hacktivist" group launched DDoS attacks last week against the websites of several Dutch political parties just ahead of the EU Parliament elections this weekend. [Additional coverage in Politico Europe]
CEPOL data breach: The EU Agency for Law Enforcement Training (CEPOL) says it was the victim of a cyberattack last week. The agency did not reveal any details about the nature of the incident but said that its services have remained functional. Officials say they have notified CERT-EU and are working with the EU agency to investigate the incident.
BSU hack: Belarusian hacktivist group the Cyber Partisans say they hacked the Belarusian State University, the country's oldest and largest university. The group claims it obtained documents and audio records from the university's internal network showing how its leadership dismissed staff and students who participated in anti-government protests. The documents also show that the university declined to admit new students who participated in protests and left comments online against the dictatorship. The Cyber Partisans say the political repression is still ongoing at the university to this day.
mSpy hack: Hacker and privacy advocate Maia Arson Crimew claims that a threat actor has hacked and dumped the helpdesk of stalkerware service mSpy. The researcher says the helpdesk database contains evidence that several law enforcement agencies reached out to the company to rent out its spyware under a white label. Maia Arson Crimew claims the company received inquiries from the Israeli National Police, the Thai Royal Police, and the Vietnamese Defense Ministry. It also received inquiries from Italian law enforcement, the UAE government, the Nebraska National Guard, and the Tasmanian Police. The researcher says there is no evidence in the helpdesk dump that any agreements were signed. mSpy joins a list of over a dozen hacked spyware vendors.
Vietnam Post ransomware attack: Vietnam's national postal service says it restored IT systems after suffering a ransomware attack on June 4. Vietnam Post websites and mobile apps have been offline since the attack. According to reports in local media, the attack has impacted postal delivery services but not package delivery or financial services. [Additional coverage in VietnamNet]
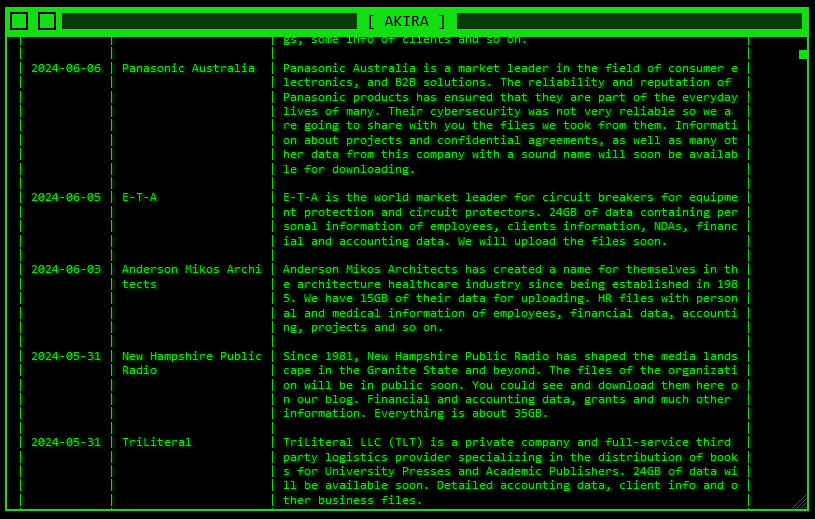
Panasonic Australia incident: The Akira ransomware group has breached Panasonic's Australian division. The group listed the company on its dark web leak site at the end of last week. Panasonic confirmed the breach to Australian cybersecurity news site CyberDaily but said the group did not manage to get its hands on any customer data.
General tech and privacy
Apple to add a password manager: Bloomberg's Mark Gurman reports that Apple will announce a password manager app at its upcoming WWDC developer conference this week. The app will be named Passwords and will be shipped to both iOS and macOS users alike. Besides storing passwords, the app will also function as a MFA authenticator, similar to the Google and Microsoft Authenticator apps.
ChromeOS Recall-like feature: A Google executive confirmed last week that the company is working on a Windows 11 Recall-like feature for its Chromebooks. The feature is currently named ChromeOS "memory" and is still under development. John Solomon, the Google VP in charge of ChromeOS, says the feature is different from Recall because users will have control of how and where the "memory" feature works. [Additional coverage in PCWorld]
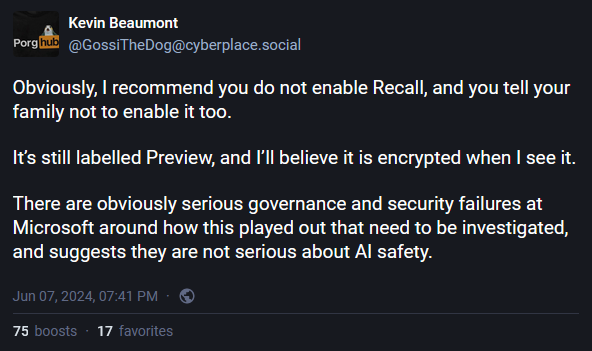
Microsoft budges on Windows Recall: Microsoft has cracked under the public's pressure and is rolling out changes to its upcoming Windows 11 Recall feature. The company says Recall will ship disabled by default for all upcoming Windows 11 compatible systems. Users will be able to activate Recall only if they previously enrolled in the Windows Hello biometrics authentication system. Recall data will also be encrypted and accessible only after users have authenticated via Windows Hello. The Recall feature has been a PR disaster for Microsoft over the past month. Users have reacted negatively to the news that Recall would be taking snapshots of their screen every five seconds and storing sensitive information in an unencrypted local database. Microsoft says it made changes to Recall after feedback from its customers.
DJI to disable flight data syncing for US drones: DJI is disabling the ability for US users to sync drone flight data to its servers. The change will take place on June 12, and the option to sync US drone data will be removed completely by the end of the month. The company's decision comes as the US Senate is scheduled to discuss a bill (Countering CCP Drones Act) to limit the use of Chinese-made drones in the US on national security grounds.
LastPass outage: LastPass was down last week for half a day because of a borked update to its Chrome extension.
EDHOC: The IETF takes a look at EDHOC (Ephemeral Diffie-Hellman Over COSE), a recently approved key exchange protocol for IoT devices.
OpenSSH anti-brute-force protection: The OpenSSH project is adding a new security feature to protect servers from exploits and brute-force attacks. The new feature will penalize and time out SSH clients that repeatedly fail authentication or crash the server. Default timeouts are 30 seconds, and trusted clients can be exempted.
Government, politics, and policy
CYBERCOM acquisition power: US Cyber Command is standing up a new program executive office to get more acquisition authority for its Joint Cyber Warfighting Architecture program. [Additional coverage in FNN]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Panther Senior Engineering Manager Nicholas Hakmiller on how the IT market is adapting to the cybersecurity skill shortage by training regular software talent in detection engineering, how AI is not there yet, and how Panther excels at spotting initial account compromise.

Cybercrime and threat intel
Smishing suspects arrested: London Police detained two individuals suspected of using a homemade mobile antenna to send thousands of smishing messages. The duo sent SMS messages posing as UK banks and other official organizations. Officials say the antenna allowed the duo to bypass telco security systems that defend against SMS spam.
Genesis user pleads guilty: A 27-year-old man from Buffalo has pleaded guilty to using the Genesis Market to buy stolen credentials. Officials say Wul Isaac Chol bought 778 credentials from the market between June 2019 and January 2021. Chol used one of the credentials to access and steal over $25,000 from the New York State Department of Labor.
Kuiper failed sale: The threat actor behind the Kuiper ransomware tried to sell its source code on the XSS hacking forums only to get immediately banned back in April.
Vidar campaign: eSentire looks at a malvertising campaign spreading the Vidar stealer to users searching for the KMSPico app.
Agent Tesla campaign: Fortinet researchers analyze a malspam campaign targeting Spanish-speaking users with the Agent Tesla infostealer.
JScript RAT campaign: On the same note, G Data researchers look at a malspam campaign delivering Cobalt Strike beacons and the JScript RAT.
DDoS groups analysis: South Korean security firm S2W has published a comprehensive look at the DDoS-as-a-Service operations that are promoting themselves via Telegram these days. Researchers look at the likes of Project DDoSia, SERVER KILLERS, CYBERBOOTER, DDOS-V4, and more. The research is in Korean.
EU election DDoS threats: Several pro-Kremlin faketivist groups have promised a wave of DDoS attacks on the websites of EU governments on June 9, the date of the EU's Parliament election day. How lovely! [Additional coverage in DailyDarkWeb]
HU election spear-phishing: Hungarian security researcher Szabolcs Schmidt reports a massive spear-phishing wave coming from the same threat actor and targeting Hungarian NGOs right ahead of the EU Parliamentary election this past weekend. The payload is the Snake keylogger.
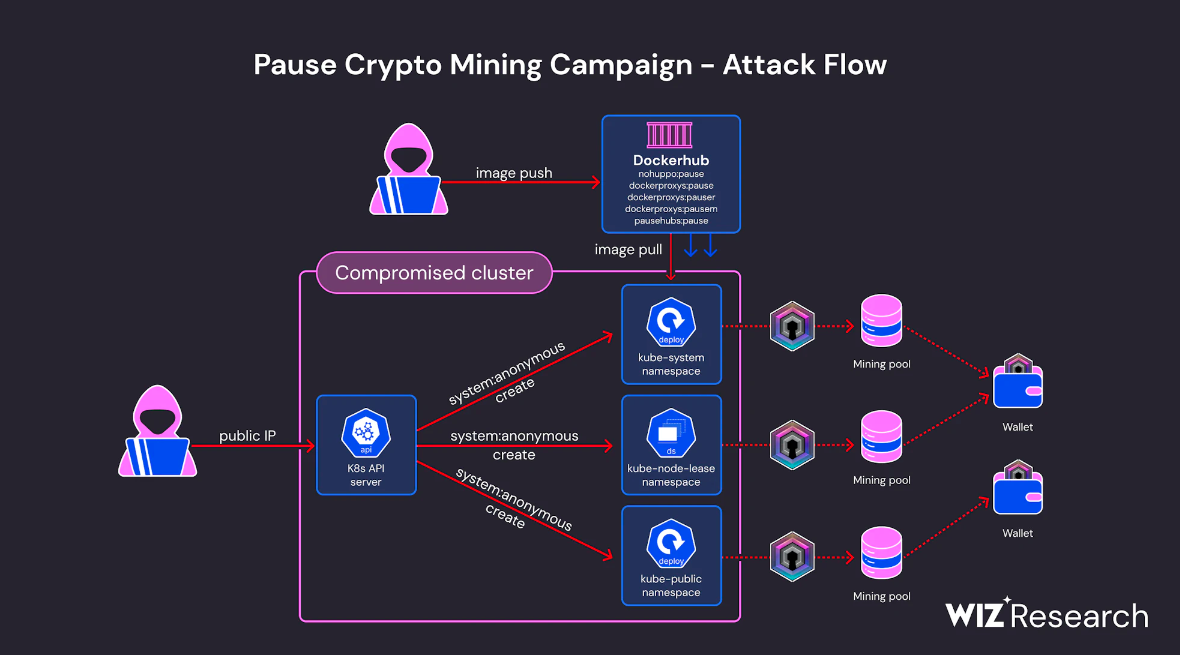
DERO crypto-miner campaign, part II: Last year, CrowdStrike published a report on a new crypto-mining operation that was targeting exposed Kubernetes systems with a miner for the Dero cryptocurrency token. This threat actor—no official name yet—is still active today, according to a new report from cloud security firm Wiz.
New npm malware: One-hundred-thirty-five malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Threat/trend reports: Arete, Cloudflare, ConnectWise, Hornetsecurity, Moody's, and SlashData have recently published reports covering infosec industry threats and trends.
Malware technical reports
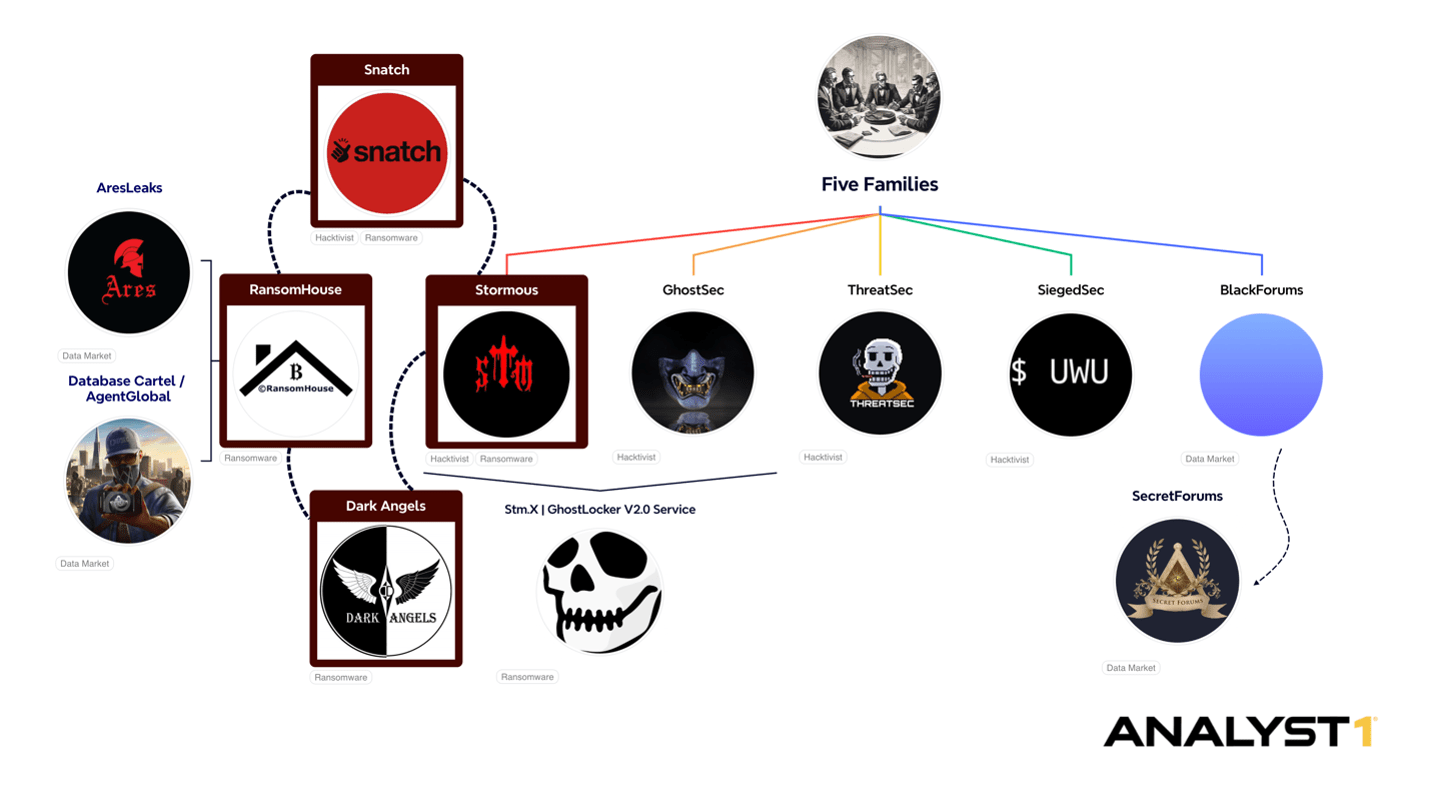
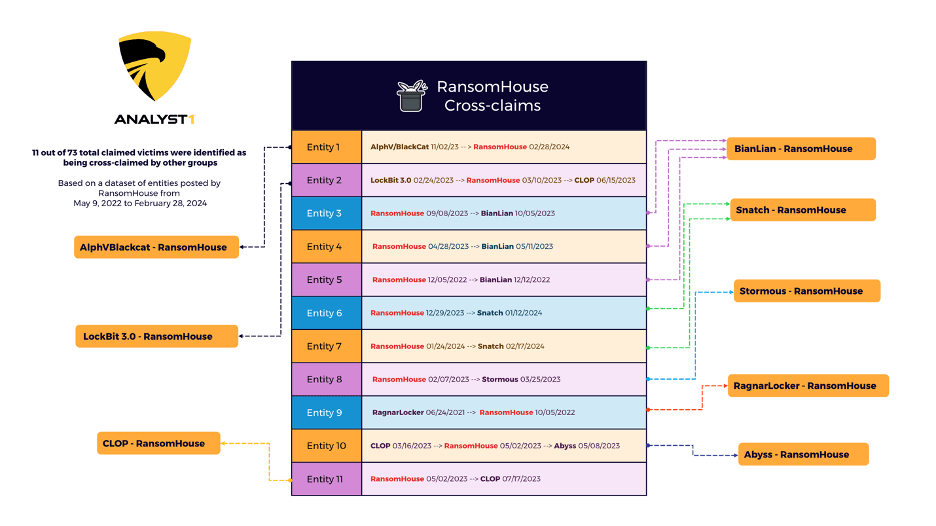
RansomHouse: Analyst1 has published a report that looks at the history of a ransomware operation named RansomHouse. Researchers say the platform has been used by threat actors with links to ransomware gangs such as White Rabbit, Mario ESXi, RagnarLocker, and Dark Angels (Dunghill Leak). Not to be confused with RansomHub, which is a different group.
"The analysis of the geopolitical alignment indicates that RansomHouse, Snatch, and Stormous are likely aligned with Russia. This is based on the observed infrastructure analysis revealing connections originating from servers based in Russia and other artifacts. Additionally, an analysis of major pro-Russian media channels reveals strong support for these groups, reinforcing their narratives in a way that aligns with and supports the broader agenda of the Russian state."
Sponsor Section
Today's podcast is brought to you by Detection-as-Code company Panther... and, in what we think is a first, they've released a detection-as-code graphic novel... called Guardians of Valora. It teaches the five key principles of Detection-as-Code... grab it now from panther.com."

APTs, cyber-espionage, and info-ops
Disinfo ops: Russian disinfo operators are back on Meta with paid ads just hours after the company shut down their accounts and published its adversarial threat report. Apparently, they're extremely easy to spot for everyone except Meta. Gotta get that bread!
Sticky Werewolf: Morphisec has published a report on a campaign targeting Russia's aviation sector. The company linked the attacks to a group tracked as Sticky Werewolf, an APT known to target Russia and Belarus exclusively. This is the first report on the group from a non-Russian security firm.
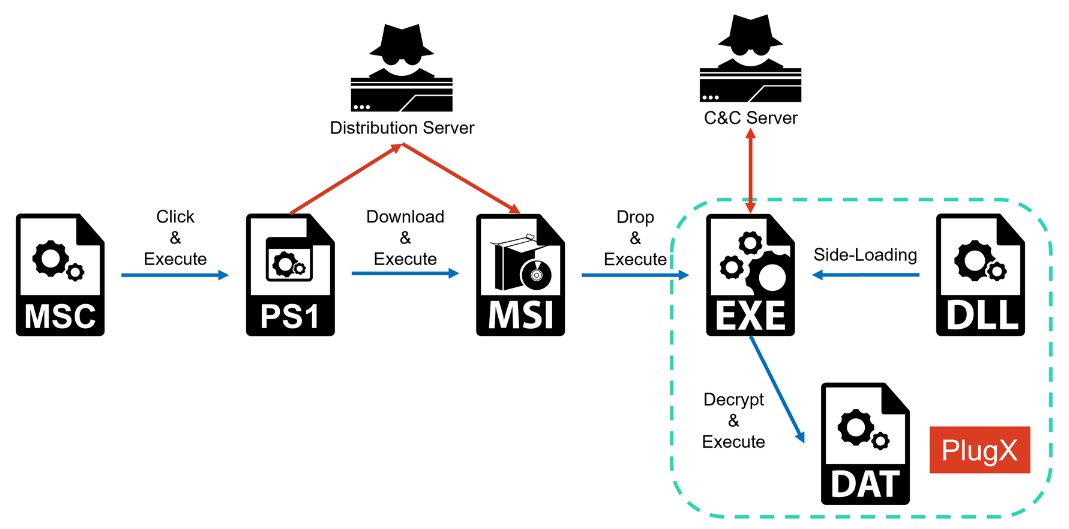
DarkPeony: NTT's security team has published a report on a recent DarkPeony campaign that they tracked as Operation ControlPlug. The campaign abused Microsoft Management Console (MSC) files to deliver the PlugX malware.
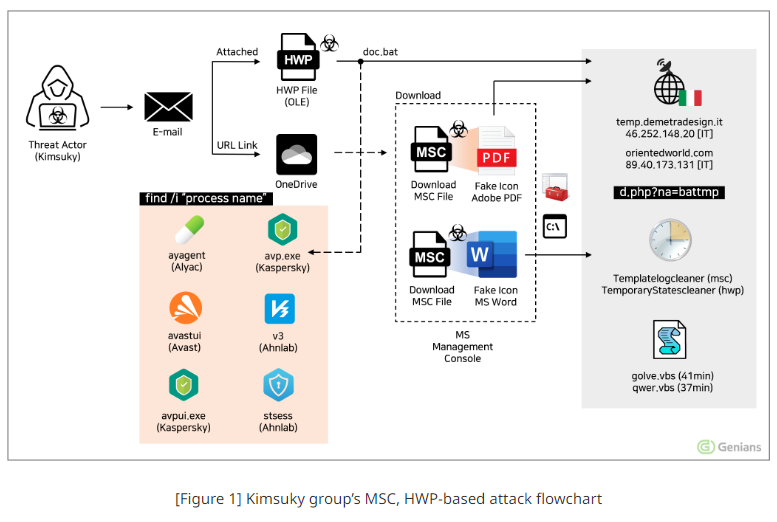
Kimsuky: Another group abusing MSCs is Kimsuky, about which you can read in a separate report from South Korean security firm Genians here, but this is a separate and unrelated campaign.
Vulnerabilities, security research, and bug bounty
PHP-CGI vulnerability: Security firm watchTowr has published its own analysis of CVE-2024-4577, a PHP-CGI vulnerability impacting Windows systems. The bug was initially discovered by DEVCORE. watchTowr has also released proof-of-concept code, and so have others. This led to almost immediate exploitation in the wild.
0Din: Mozilla has launched a new bug bounty program focused on large language models (LLMs) and other deep learning technologies. The new platform is named 0-Day Investigative Network (0Din) and works as an intermediary between researchers and LLM vendors—similar to the likes of ZDI. Mozilla says 0Din will accept bug reports for common LLM vulnerabilities and attacks such as Prompt Injection, Training Data Poisoning, Denial-of-Service, and more.
Dangerous WP plugin bug: A security researcher has found a critical vulnerability in a WordPress authentication plugin. The vulnerability impacts Login/Signup Popup, a WordPress plugin installed on more than 40,000 sites. The bug is considered extremely dangerous because the plugin is often used on WooCommerce-based online stores where new user registration is enabled by default. Researchers say the bug can allow a threat actor to register a new account with full admin rights over a WordPress site.
Disabling Windows Defender: Altered Security's Munaf Shariff has published details and a PoC on how to disable Windows Defender by abusing SYSTEM/TrustedInstaller privileges. The technique works on all currently supported versions of Windows. Administrative privileges are required to run the POC and technique, so the technique will require an EoP before use.
Infosec industry
RIP David Ross: David Ross, one of the early pioneers of browser security research, has passed away, his family announced on Twitter. In 1999, together with Georgi Guninski, he authored the first paper on XSS attacks named "Script Injection". He also worked on implementing X-Frame-Options in Internet Explorer.
New tool—WolfHSM: WolfSSL has open-sourced WolfHSM, a quantum-resistant cryptography framework for Automotive HSMs (Hardware Security Modules).
New tool—aiDAPal: Security firm Atredis Partners has open-sourced aiDAPal, an IDA Pro plugin that uses a locally running LLM—that has been fine-tuned for Hex-Rays pseudocode—to assist with code analysis.
New tool—jollyexec: SensePost's Dominic White has released a tool named The Jolly Executioner (jollyexec) that works as a command execution proxy.
RWC 2024: Talks from the Real World Crypto 2024 security conference, which took place in March, are available on YouTube.
PrivacyCamp24: Talks from the Privacy Camp 2024 security conference, which took place this January, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about law enforcement agencies trolling cyber criminals when they carry out disruption operations, and why it might be counterproductive.




