Risky Biz News: Microsoft announces Quick Machine Recovery, a feature to fix future CrowdStrike disasters
In other news: Phobos ransomware admin arrested; US Library of Congress discloses breach; Microsoft to host in-person hacking contest.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
At its Ignite developer conference this week, Microsoft announced a new feature for its Windows 11 operating system that will allow admins to remotely fix PCs with booting issues.
The company developed the feature as a way to tackle future cases like the CrowdStrike incident that crashed over 8.5 million PCs in July this year.
The new feature is named Quick Machine Recovery and will allow a company's IT administrators to tap into the Windows Update system to deliver fixes for boot-related bugs that normally require physical access to a machine.
Quick Machine Recovery will be available for testing via Windows Insider builds in early 2025 before a broader rollout at a later date.
The feature is one of several new security-centric features coming to Windows 11 next year. Another feature is Admin Protection, which we covered in a previous newsletter edition, here. The feature basically creates a hidden admin account on the OS to which users are moved every time they need to perform a sensitive action and then moved back to their low-level account. Unlike the current User Access Control system, to elevate access to this account, users will need to authenticate with valid credentials, rather than just press a "Yes" button in a popup.
Windows 11 will also roll out passkey support for Windows Hello, a security-hardened print system named Windows Protected Print, and a hotpatching system for deploying patches without restarting PCs.
On top of that, Windows 11 will also support the ability to refresh PC configs to defaults after a certain period of time, support for Zero Trust DNS (run all DNS queries via a trusted DNS only), and the ability to encrypt and restrict access to sensitive documents via Windows Hello.
Other stuff was also announced at Ignite, but they're not security-related, so we don't care. But in case you wanna take a look through them, The Verge has a nice summary here.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Library of Congress data breach: The Library of Congress has notified US lawmakers that a threat actor breached its IT network and gained access to internal communications. The attacker is believed to have stolen emails sent between congressional offices and library staff. According to the Associated Press, the breach allegedly lasted from January to September this year and took advantage of a vulnerability in its IT environment.
Gaetz hacking claims: A yet-to-be-confirmed NYT article claims that a hacker gained access to files containing damaging testimony related to Matt Gaetz' sex trafficking probe.
Polter Finance crypto-heist: DeFi lending platform Polter Finance was hacked for $12 million after a flash loan attack over the weekend. [Additional coverage in Decrypt]
General tech and privacy
DOJ wants Google to divest Chrome: As part of its anti-monopoly suit, the US DOJ will push Google to sell off its Chrome browser division—which, honestly, is a spectacular decision since Google has been abusing its browser market control for a few years now. [Additional coverage in Bloomberg]
GitHub Secure Open Source Fund: GitHub has launched a new fund to help secure open-source projects. The company is committing $1.25 million to the Secure Open Source Fund to help fund security features across 125 popular open-source projects. Besides GitHub, other companies have also contributed to the fund, such as Microsoft, 1Password, Shopify, and American Express.
Ondsel shuts down: Open-source CAD engineering suite is shutting down at the end of this week.
"From the beginning, we knew competing with commercial CAD would be tough. Closed-source CAD is taught in schools and is deeply entrenched in established industry use. We knew that to be successful, we would have to find a way to provide real value and coexist in environments where other tools are already used."
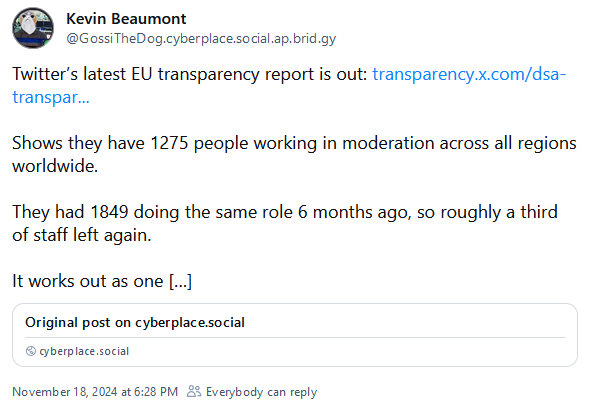
Twitter moderation: Twitter/X seems to have "lost" a third of its moderation staff over the past quarter.
Government, politics, and policy
Pakistan preparing VPN ban: Pakistan's religious advisory board has ruled that the use of VPN apps is against Shariah Law. The announcement from the Council of Islamic Ideology comes weeks after the government announced plans to ban VPNs. VPN use exploded in Pakistan after the government deployed a national firewall in July to block access to unwanted information. [Additional coverage in VOA News]
US water systems fraught with vulnerabilities: A report from the Environmental Protection Agency's Office of Inspector General has found that around 9% of public drinking water systems are fraught with critical vulnerabilities that can be used to compromise systems. [Additional coverage in StateScoop]
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about what to expect from President Trump's second term. Trump is an activist president who believes in using state power, so intelligence agencies will be pushed to conduct more audacious or even outrageous covert operations.
Arrests, cybercrime, and threat intel
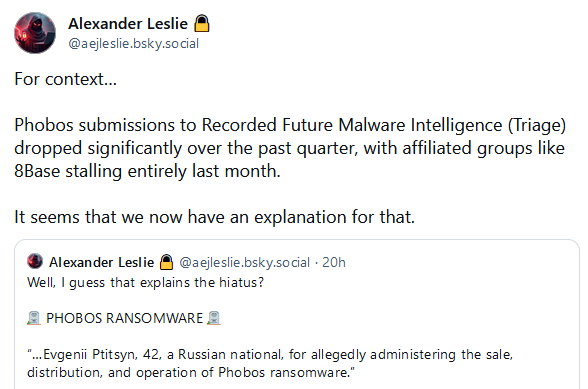
Phobos ransomware admin arrested: US authorities have charged a Russian national for allegedly running the Phobos ransomware operation. Evgenii Ptitsyn was arrested in South Korea and extradited to the US earlier this month. Ptitsyn operated on hacking forums under monikers like "derxan" and "zimmermanx," where he advertised access to the Phobos Ransomware-as-a-Service. His operation catered to individuals who wanted to ransom home users and smaller companies, with most ransom demands being under $2,000. Recorded Future analyst Alexander Leslie says news of the arrest comes after detections of new Phobos infections stopped last month.
Cyber scam leader arrested: Thai officials have arrested a Chinese national for running a cyber scam compound in the country's south. A 33-year-old individual named Mr. Jiang was arrested on November 10. Officials have described him as the leader of a scam compound they raided in May. [Additional coverage in Khaosod]
Razzlekhan sentenced to 18 months: A US judge has sentenced Heather "Razzlekhan" Morgan to 18 months in prison for helping launder cryptocurrency from the 2016 Bitfinex hack. The hack was carried out by Morgan's husband, Ilya "Dutch" Lichtenstein. He was sentenced to five years last week. [Additional coverage in CoinDesk]
AitM phishing campaign abuses Dropbox: Abnormal Security looks at an AitM phishing campaign targeting corporate employees that abuses Dropbox as a lure and to host phishing pages.
Facebook malvertising targets Bitwarden users: Romanian security firm Bitdefender looks at a malvertising campaign abusing Facebook Ads to target Bitwarden password manager users. The campaign lured users to a malicious Chrome extension.
Microsoft servers abused to send sextortion emails: Threat actors are abusing the Microsoft 365 Admin Portal to send out sextortion emails. According to Bleeping Computer, the attackers are abusing Personal Message, a feature of the Admin Portal that lets corporate admins send personal messages to any email address. The attackers are exploiting a coding mistake to bypass the feature's character limit and send the extortion emails with what appears to be an automated script.
Women in Russia's cybercrime ecosystem: SANS, Intel471, and others have published a joint report on the role women play in Russia's underground cybercrime scene.
Akira returns: After more than a month of inactivity, the Akira ransomware gang returned and listed 35 victims on its dark web leak site on Monday.
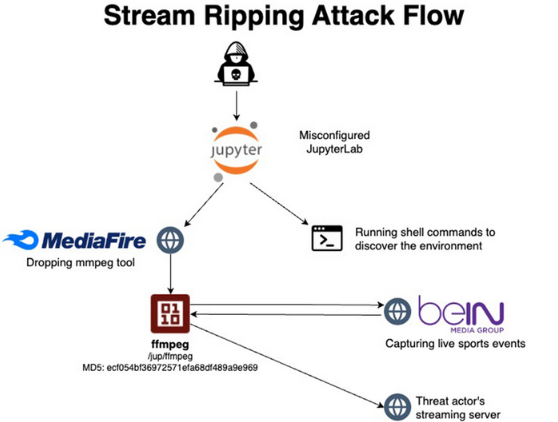
Hacked Jupyter Notebooks host pirate streams: A threat actor is hijacking misconfigured Jupyter Notebook applications to host illegal sports streams. The attackers take over unsecured Notebooks, install the FFmpeg library to capture video from legitimate streams, and then broadcast the captured stream through their own streaming website. Cloud security firm AquaSec says the hacks appear to support an illegal streaming service known as Ustream.tv.
Malware technical reports
Strela Stealer: Logpoint researchers have published a technical report on the Strela infostealer.
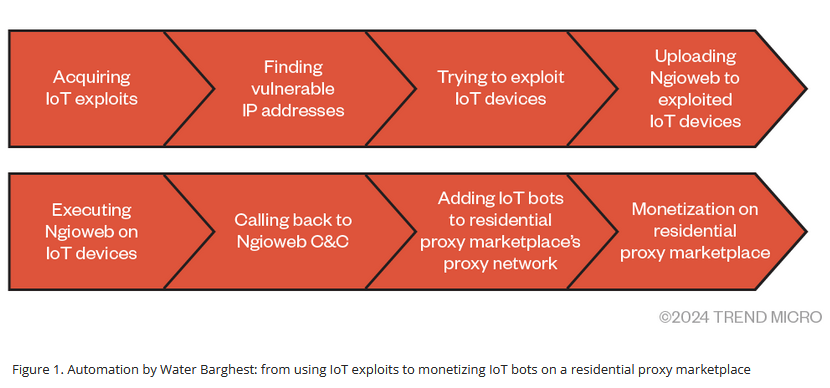
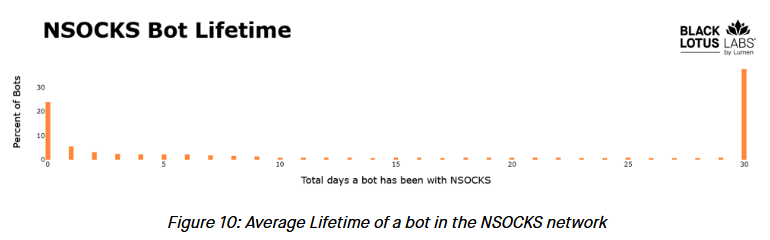
Lumen sinkholes Ngioweb traffic: Internet infrastructure company Lumen (formerly CenturyLink) has started blocking all traffic coming from the Ngioweb IoT botnet. The company's decision comes after the botnet grew ten times its initial size over the past months and is now estimated to have reached over 35,000 infected daily systems. AT&T, Lumen, and Trend Micro say the botnet is the backbone of Nsocks, a public website that rents access to proxy servers installed on Ngioweb-infected devices. These proxies have been linked to various cybercrime operations, such as DDoS attacks, ransomware, and malware command-and-control infrastructure.
Helldown ransomware exploits Zyxel zero-day: A new ransomware group named Helldown is exploiting a zero-day in Zyxel firewalls to gain access to corporate systems. According to Truesec and Sekoia, the zero-day seems to match a bug reported through Zyxel's public forum earlier this month. The group has been active since August and has listed over 30 victims on its dark web leak site so far.

Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how ungoverned spaces on Telegram result in increasingly toxic and antisocial communities.
APTs, cyber-espionage, and info-ops
FrostyGoop: Palo Alto Networks has looked at FrostyGoop (BUSTLEBERM), the malware used by Russia to cut heating to 600 Ukrainian apartment buildings earlier this year.
APT targets Pakistan's Navy: BlackBerry researchers have published a report on a suspected APT campaign that targeted Pakistan's Navy over the past year. No formal attribution.
Liminal Panda: A suspected Chinese cyber-espionage group known as Liminal Panda has been hacking telco companies across Africa and Southeast Asia since 2020. According to CrowdStrike, the group uses custom hacking tools and primarily focuses on stealth and intelligence collection. Most of the targets are associated with China's Belt and Road Initiative.
Sharp Panda: Securite360 has published a technical report on a new malware loader utilized by the Sharp Panda Chinese APT.
Volt Typhoon: Tenable has collected a series of TTPs and IOCs used by the Volt Typhoon APT.
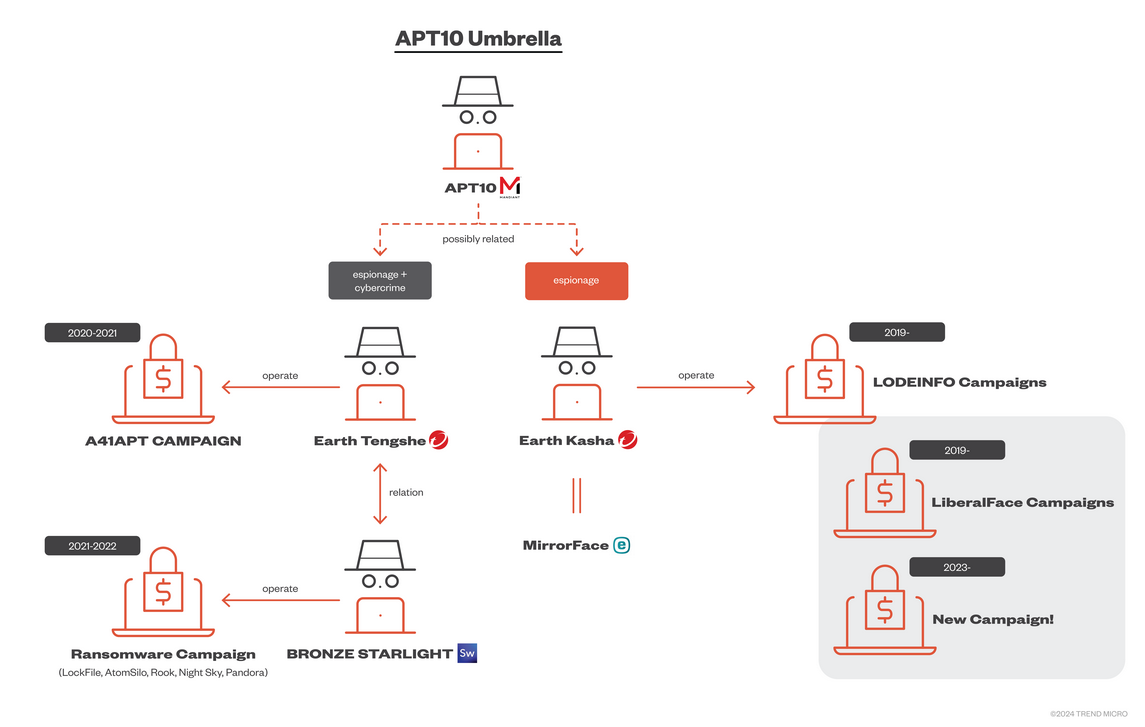
Earth Kasha: Trend Micro has published a report on an APT group it tracks as Earth Kasha, which has been using the LODEINFO malware against targets in Japan since 2019. The security firm says it found clues to identify Earth Kasha as one of the smaller groups part of the larger APT10 Chinese cluster.
Vulnerabilities, security research, and bug bounty
VINTEO zero-days: A threat actor has exploited two zero-days in the Vinteo video conferencing server in an attack against a Russian company. The attacks were discovered by Russian security firm Positive Technologies. The zero-days included an SQL injection and an arbitrary code execution vulnerability. Both issues were fixed by the vendor.
Second PAN firewall zero-day: Palo Alto Networks says the recent attacks against the management panels of its firewalls include not one but two zero-days. The exploit chain consists of an authentication bypass (CVE-2024-0012) and a privilege escalation (CVE-2024-9474) that allows the attacker to pivot from the management panel to the underlying firewall firmware. The company says attackers are using the two zero-days to gain access to internet-exposed firewalls and deploy a webshell for future access. Palo Alto learned of rumors about a zero-day in its products two weeks ago and confirmed active exploitation last week. It released patches on Monday. watchTowr Labs has also published a technical breakdown of the exploit chain.
New VMware exploitation: Broadcom says that threat actors are now exploiting two VMware vCenter vulnerabilities (CVE-2024-38812, CVE-2024-38813) the company patched back in September. The vulnerability was reported to Broadcom after it was initially used at a Chinese hacking contest in May. Broadcom has not published any details about the nature of the recent attacks.
Citrix exploitation: The SANS ISC has detected active exploitation of vulnerabilities in Citrix Virtual Apps and Desktops. The vulnerabilities were disclosed last week by watchTowr Labs after the vendor failed to release fixes.
Oracle PLM out-of-band zero-day update: Oracle has released an out-of-band security update for the Oracle Agile PLM Framework to fix a pre-auth information disclosure bug tracked as CVE-2024-21287. Per Oracle security team, this was actively exploited in the wild as a zero-day.
Invisible Salamander on S/MIME: Lutra Security has adapted the Invisible Salamander attack on Facebook Messenger to the S/MIME protocol.
D-Link tells customers to retire old gear: For the third time this month, D-Link has told device owners to retire and replace old gear after a new security flaw was discovered in its older products. This time, it's a bunch of VPN tools and routers.
Microsoft announces hacking contest: Microsoft will host a new hacking contest next year that will focus on cloud and AI vulnerabilities. The new event is named the Microsoft Zero Day Quest and will have a prize pool of up to $4 million. Microsoft plans to invite top researchers from its bug bounty leaderboards and researchers who apply via an open submissions process. The new hacking event was announced at Microsoft's Ignite developer conference and will hold its first edition at the company's headquarters in Redmond next year.
Infosec industry
Threat/trend reports: BforeAI, Cato Networks, Gen Digital, and Nuspire have recently published reports and summaries covering various infosec trends and industry threats.
New tool—PSDNSExfil: SensePost's Felipe Molina has released PSDNSExfil, a PowerShell-based tool that exfiltrates data via DNS.
New tool—TokenCert: Security firm Nettitude has released TokenCert, "a C# tool that will create a network token (LogonType 9) using a provided certificate via PKINIT. This way, we can have a make-token functionality using certificates instead of passwords."
r2con videos: Talks from the r2con 2024 security conference, which took place earlier this month, are available on the conference's website and YouTube.




