Risky Biz News: Microsoft accused of negligence in dealing with security flaw, again
In other news: Salesforce zero-day abused in Facebook phishing campaigns; Fortinet bug tops list of most exploited vulnerabilities of 2022; and a Tesla jailbreak to be revealed at BlackHat.
This newsletter is brought to you by GreyNoise. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Hours before this newsletter was scheduled to go live, Microsoft released a full patch for this vulnerability and backported it to all Azure apps and customers. The patch came after the company had been intensely and publicly criticized for how it handled the issue. We left the original intro intact to reflect the public sentiment that led Microsoft to accelerate its patch development. In the meantime, Tenable has also released a detailed write-up of the vulnerability, along with a PoC.
Amit Yoran, the CEO of vulnerability management platform Tenable, has accused Microsoft of being grossly irresponsible and blatantly negligent when it comes to addressing security flaws in its Azure cloud platform.
Yoran's scathing criticism is in relation to a security flaw a Tenable researcher found in the Azure platform that could have allowed unauthenticated attackers to access cross-tenant applications and grab any Azure customer's data.
The Tenable CEO says they notified Microsoft of the issue, but the company dealt with what appears to be a catastrophic vulnerability in the most unprofessional manner possible.
It took them three months to deliver a partial fix, and once their spotty fix was out, they only applied to new apps deployed on its Azure platform, leaving all past tenants still exposed to attacks.
Microsoft "claims" it will fix the issue in September, but that's six months after the initial report, way beyond the industry-acceptable 90-day patching and disclosure deadline. For something as serious as this, Microsoft should have prioritized patching.
In addition, Yoran says Microsoft also failed to at least notify customers of the issue. And he's right. If you're going to half-ass a patch and only apply it to new apps, at least tell your customers they might be exposed and share mitigations until you roll out your magic patches in September.
Yoran's LinkedIn post is the second time the Tenable CEO has accused Microsoft of questionable vulnerability patching practices in its Azure platform after a similar post last year in June.
His criticism carries a lot of weight. He isn't just another angry infosec nobody, but the CEO of Tenable, one of today's largest vulnerability management platforms, and the former US National Cybersecurity Director during the Bush Jr. administration.
Yoran going on his second LinkedIn rage-posting spree also comes at a very bad time for Microsoft. It comes a week after Senator Ron Wyden asked three US government agencies—the Justice Department, the Federal Trade Commission, and the Cybersecurity and Cyber Safety Review Board—to investigate Microsoft for its serious and repeated security lapses that have enabled the SolarWinds and Storm-0558 hacks.
The two incidents allowed Russian and Chinese hackers access to sensitive government systems, and my colleague Tom Uren has a fantastic breakdown of Microsoft's failures that enabled the Storm-0558 hacks in this week's edition of his newsletter.
Tom predicted that this time, Wyden's letter may have some bite.
He was 100% right, again, as he usually is, because as he submitted his newsletter for final editing, the US House Oversight and Accountability Committee launched a formal inquiry into Microsoft's Storm-0558 Chinese hacks.
Yoran's recent LinkedIn post may not be related to those incidents, but it will almost certainly turn out to be one of the logs in the fire that will roast Microsoft's buttocks for its opaque and unprofessional behavior when it comes to security issues.
And by no means is Yoran alone in thinking like this about Microsoft. Probably one of the best breakdowns for how Microsoft's security practices have degraded in recent years, mired in incompetency and a pool of sub-par lawyers, comes from Juan Andres Guerrero‑Saade, a threat researcher at SentinelOne and a lecturer at Johns Hopkins University.
Breaches, hacks, and security incidents
Russian "hacktivism," part I: Italy's cybersecurity agency says that a wave of DDoS attacks has impacted the public websites of several Italian government agencies, banks, and other private businesses on Monday. The DDoS attacks took place as Italian Prime Minister Giorgia Meloni visited Kyiv this week, where she announced a sixth military aid package to Ukraine. A Russian "hacktivist" group named NoName057(16) took credit for the attacks, accusing Italy of rUsSoPhObIa. The DDoS attacks targeting Italy come after the group previously targeted Spain the previous weeks. [Additional coverage in ANSA]
Russian "hacktivism," part II: Totally-not Russian "hacktivist" group Anonymous Sudan has issued threats of "reprisals" if France decides to send military troops to Niger to restore the country's democratically-elected government and overthrow a small Russian-backed military junta that has taken control of the African country. [Additional coverage in Le Parisien]
Voyager crypto-heist: Cryptocurrency platform Voyager has reported to authorities a potential hack of its systems. The company claims it was hacked during a 30-day window the platform opened to allow customers to retrieve funds as part of its court-supervised liquidation process. Voyager didn't reveal how much hackers stole but said that customers recovered $490 million of their assets, representing 80% of what the company still had in its accounts. [Additional coverage in Yahoo News]
General tech and privacy
Veilid: The Cult of the Dead Cow plans to unveil a new project at the Def Con hacking conference in Las Vegas next week. The famed white-hat hacking group will release Veilid, a protocol and framework for building encrypted social media applications. Veilid will mark the group's major software release in more than a decade. [Additional coverage in the Washington Post/non-paywall]
WEI criticism: The Brave browser team has added its voice in opposition to Google's proposed Web Environment Integrity (WEI) standard, likened to a Web DRM. It adds to criticism from Vilvaldi and Mozilla.
Card PIN failures across the Netherlands: A network connectivity error has been blamed for a technical glitch that caused payment card PIN verification to fail for more than an hour across the Netherlands on Thursday, August 3.
OpenUSD: Pixar, Adobe, Apple, Autodesk, and NVIDIA have united to create the OpenUSD standard to be used for cinematic and large-scale 3D content. The new standard will be based on Pixar's Universal Scene Description technology. The new organization will also receive contributions from the Joint Development Foundation (JDF), an affiliate of the Linux Foundation.
Codecov goes open-source: The Codecov code coverage and code testing platform has released an open-source version of its tools, now available on GitHub across several repos.
SCARF: A team of academics from universities across the world have developed SCARF, a new and highly efficient cipher that randomizes the cache memory of a modern CPU. Researchers say their system can be used to protect processors from side-channel attacks that use novel and unpredictable ways of retrieving data from the CPU while it's being processed. SCARF stands for Secure CAche Randomization Function and is touted as the first dedicated low-latency cache randomization cipher.
AMD fTPM: There's a high chance AMD's fTPM CPU security module might be disabled in the Linux kernel after it's been linked as the root cause of severe stuttering on both Windows and Linux. The proposition to disable fTPM came from Linux creator Linus Torvalds himself. [Additional coverage in Tom's Hardware]
Government, politics, and policy
Nigeria's DDoS attack warning: Nigeria's cybersecurity agency has issued a security advisory this week warning of threats made by a hacktivist group against government systems. The warning is related to threats of DDoS attacks and other repercussions made by Anonymous Sudan in relation to Nigeria's potential military involvement in the Russian-backed coup in Niger.
China calls on citizens to catch spies: China's Ministry of State Security has launched an official WeChat account, and its first-ever post has asked "all members of society" to help catch spies operating inside China. Serving as the country's main intelligence body, the normally secretive spy agency has urged other government agencies to open reporting channels so citizens can freely report local or foreign individuals conducting espionage on behalf of other states, with rewards and anonymity for all whistleblowers. It also urged news agencies and advertising companies to carry out a "national security literacy" program with messages in the media and screen terminals meant to educate the general public on how to spot and report spies. Also referred to as the MSS, the agency is also known in the West for its central role in hiring private contractors to conduct some of its foreign cyber-espionage operations. [Additional coverage in CNN]
AIVD/MIVD hackathon: The Netherlands' civilian and military intelligence agencies, the AIVD and MIVD, have announced they are organizing a joint hackathon. The event will be held later this fall, on November 18-19, in a "secret location in the Netherlands."
NSF cyber funding: The US National Science Foundation has renewed its CyberCorps Scholarship for Service program and will be providing $24 million in funding for the next four years to seven academic institutions to teach cybersecurity classes. The funding will go to the University of Alabama at Birmingham, the University of Tennessee at Chattanooga, the California State University, Sacramento, SUNY at Buffalo, Mississippi State University, Tuskegee University, and Idaho State University. The program is now funding 98 institutions participating in the CyberCorps program across 39 US states.
FCC record fine: The US Federal Communications Commission has imposed a record fine of $300 million on an international network of companies. The agency says the companies made five billion robocalls to 500 million US phone numbers during a period of three months in 2021. The FCC called the campaign, which consisted of auto warranty scam calls, one of the largest robocall operations the agency ever encountered.
Flipper Zero warnings: Police departments across the US have been warned that white nationalists and other violent extremist groups may attempt to use Flipper Zero hacking devices in attempts to hack and crash sections of the US power grid. The warning is based on discussion of Flipper Zero devices on certain Telegram channels, not attacks observed in the wild. The tool, which sells only for $169, allows IT enthusiasts to tinker with radio, NFC, infrared, Bluetooth, and other communication protocols. Because of its ability to perform RFID emulation and digital access key cloning, the tool is believed to be a boon for criminal organizations involved in car thefts, house burglaries, and ATM fraud. The warning is based on discussion of Flipper Zero devices on certain Telegram channels, not attacks observed in the wild [Additional coverage in The Daily Dot]
"The NYPD Intelligence and Counterterrorism Bureau (ICB) assesses that racially and ethnically motivated violent extremists (REMVEs) may seek to exploit the hacking capabilities of a new cyber penetration tester, known as the Flipper Zero, in order to bypass access control systems."
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with GreyNoise founder and CEO Andrew Morris about the company's vast network of honeypots and how they're preparing to take it to the next phase.
Cybercrime and threat intel
Team Bangladesh: Group-IB has a report on Team Bangladesh, a hacktivist group that conducted more than 750 DDoS attacks over the past year. The group is primarily driven by religious and political motives, and its main targets have been the government, financial, and logistics sectors in India and Israel. Researchers have identified the group's founder and leader as an individual going on Telegram as D4RK_TSN.
CryptoRom scam apps return: Sophos researchers have uncovered a new set of fake cryptocurrency investment apps that lead customers to "pig-butchering" investment scams. The seven apps were available on the official Apple and Google app stores. Sophos has tied the apps to a crypto-scam campaign it calls CryptoRom, which they've been tracking since 2020. The security firm says that while early CryptoRom apps avoided the official app stores, recent campaigns have been leveraging the stores to increase the legitimacy of their apps and the number of potential targets. Crypto investment schemes like CryptoRom were last year's most damaging form of cybercrime, accounting for $3.3 billion in losses, according to the FBI.
White Snake campaign: Russian security firm BI.ZONE says it is tracking a phishing campaign spreading the White Snake stealer to Russian organizations.
DarkGate: Kaspersky says that a "well-known malware developer" has launched a new Malware-as-a-Service named DarkGate. Launched in June 2023, this new service provides a malware toolkit that can be used to infect users and then download additional payloads—also known in infosec jargon as a "downloader." Kaspersky says it has already detected samples of this new malware being used in the wild.
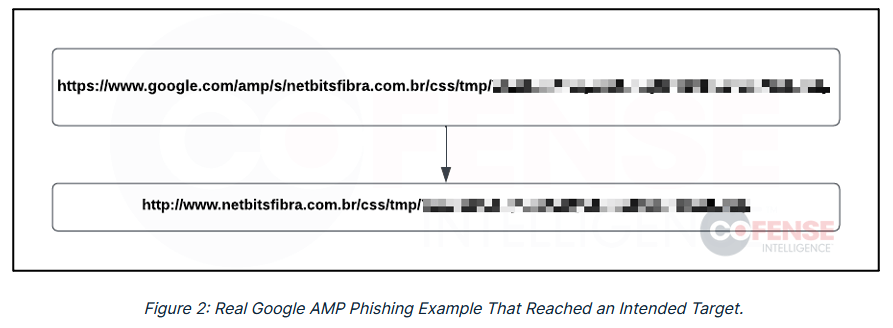
Google AMP phishing abuse: Cofense has spotted threat actors using Google AMP links inside phishing emails meant to evade detection and disguise the location of phishing sites. Follows similar abuse seen with Google Translate and Google Docs links.
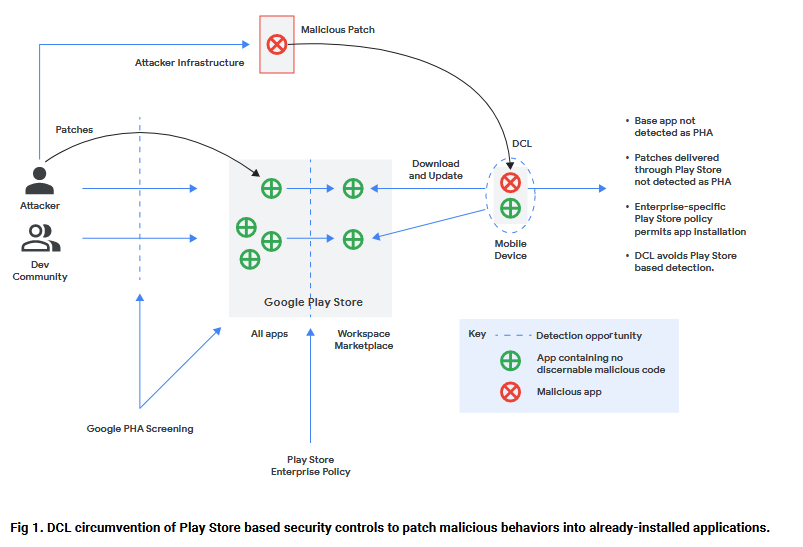
Google Cloud Threat Horizons Report #7: In the seventh edition of its threat and trends report [PDF], the Google Cloud security team highlighted the use of DCL (direct code loading) as a way for threat actors to introduce malware on the official Play Store. One well-known malware strain that heavily relies on DCL is the SharkBot Android banking trojan.
"One way malicious actors attempt to circumvent Google Play's security controls is through versioning. Versioning occurs when a developer releases an initial version of an app on the Google Play Store that appears legitimate and passes our checks, but later receives an update from a third-party server changing the code on the end user device that enables malicious activity. One common form of versioning is using dynamic code loading (DCL). DCL is defined as an app which downloads and loads code files from untrusted sources."
ICS vulnerabilities in 2023: A study from ICS security firm SynSaber has discovered that a third of vulnerabilities disclosed in the first half of 2023 and impacting industrial equipment have not received official patches. The number represents 34% of 670 CVEs disclosed in H1 2023.
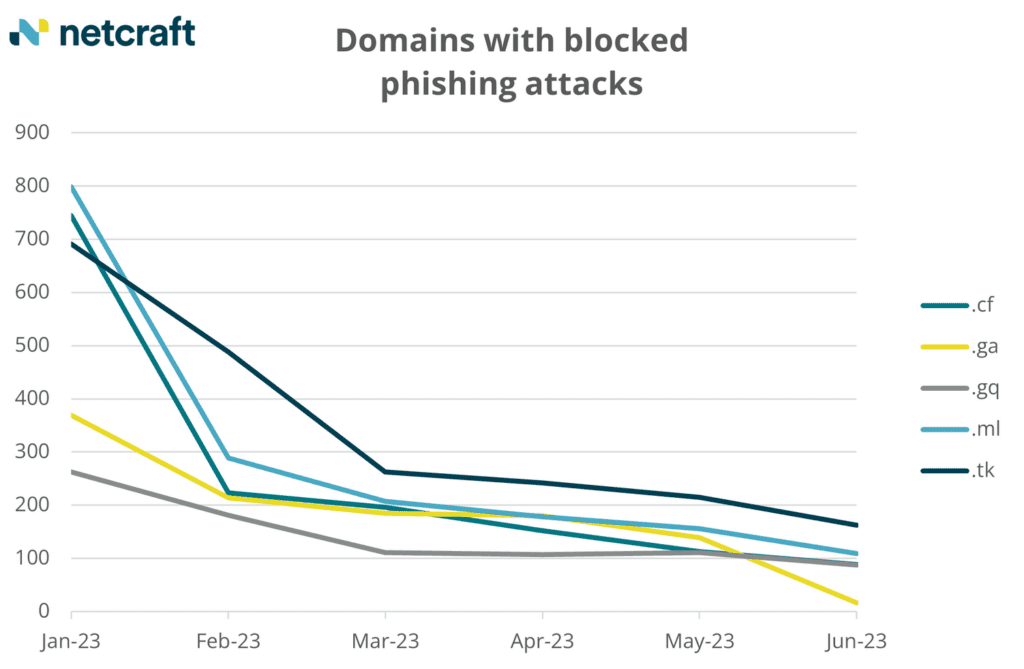
Freenom phishing domains go down: Netskope has observed a significant reduction in phishing domains being hosted on top-level domains previously managed by domain registrar Freenom. The significant drop in malicious activity comes after Meta sued Freenom earlier this year for ignoring abuse reports and allowing criminal activity on its platform that impacted Facebook users. The lawsuit specifically mentioned Freenom providing free registration of domains for the Central African Republic (.cf), Equatorial Guinea (.gq), Gabon (.ga), Mali (.ml), and Tokelau (.tk), which were being abused by cybercrime groups. In response to the lawsuit, Freenom halted registrations and allowed the domains to go back to their national registrars in countries. Netskope's findings echo the findings of other security researchers, which also saw a significant decline in malicious activity on the former Freenom-managed domains.
Malware technical reports
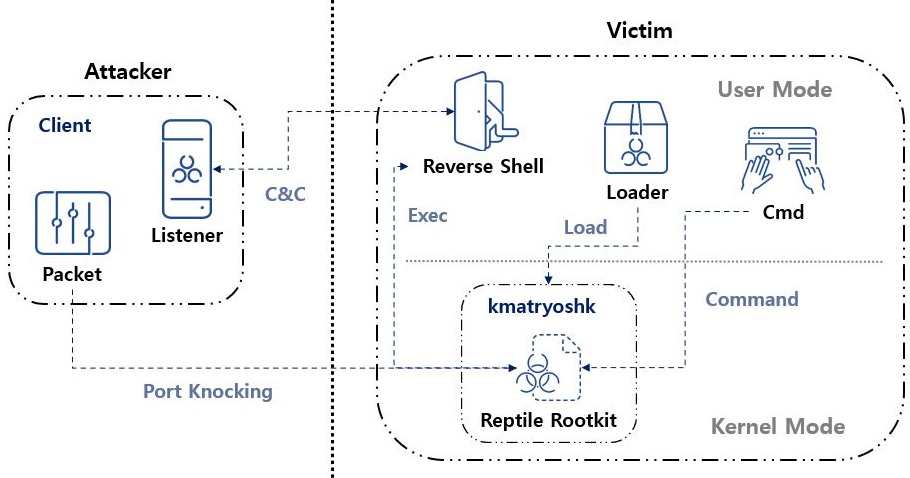
Reptile rootkit: AhnLab researchers have published a breakdown of Reptile, an open-source rootkit that has been "used consistently in attacks" over the past years in attacks targeting Linux systems.
Syssphinx's Sardonic backdoor: Darktrace researchers have a breakdown on Sardonic, a backdoor used by the Syssphinx (FIN8) group to deploy the Noberus (BlackCat) ransomware. Previously also covered by Broadcom's Symantec.
PyPI malware: Hacktive Security has published an analysis of pythoncryptolibraryV2, a malicious Python library that was available on the official PyPI portal and contained various backdoors and malicious features.
Rilide: Trustwave researchers say they've seen a new version of the Rilide Chrome extension malware that was rewritten to be compatible with Google's new Manifest V3 rules for Chrome extensions. The original Rilide malware was spotted earlier this year in campaigns targeting cryptocurrency users. The malware can steal login credentials, authentication cookies, and browsing data, install other extensions, take screenshots of the user's browser, and inject malicious scripts to withdraw funds from various cryptocurrency exchanges. Rilide is part of a new wave of malicious Chrome extensions that can bypass security features introduced with Chrome's new extensions API.
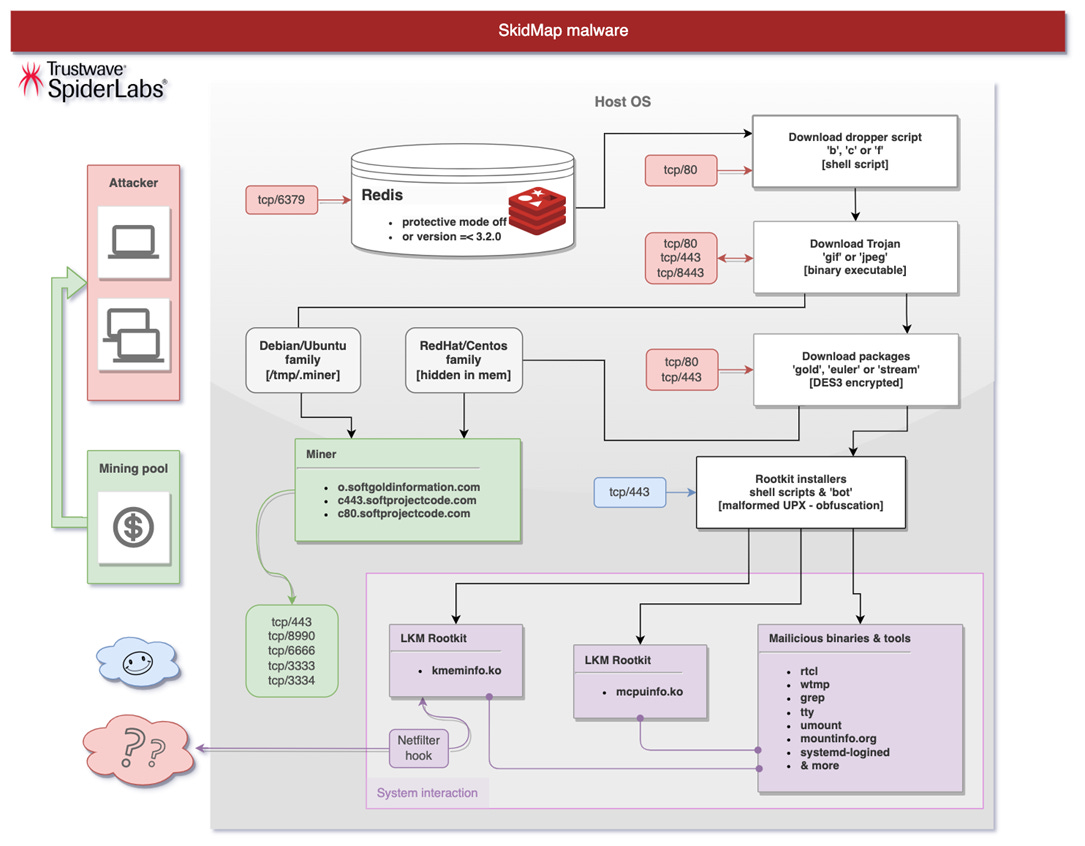
SkidMap botnet: Owners of Redis databases are advised to review the security posture of their servers as security researchers have spotted two new malware strains specifically designed to infect their systems. The first is named P2PInfect, a worm spotted last month by Palo Alto Networks and Cado Security spreading from one Redis system to another, backdooring servers for future access. The second is named SkidMap, a crypto-mining botnet that infects Redis systems, installs a powerful rootkit, and then abuses local resources to mine cryptocurrency.
Sponsor Webinar
In this webinar, GreyNoise's Abigail Whidden explores the powerful combination of Splunk and the GreyNoise platform and how customers can leverage GreyNoise's vast intelligence on internet-wide scans and attack activity to enhance security operations.
APTs and cyber-espionage
Midnight Blizzard: Microsoft says that a Russian cyber-espionage group named Midnight Blizzard (NOBELIUM) has been using hacked Microsoft 365 tenant accounts to send out spear-phishing emails that appear to come from legitimate companies. Microsoft says the group has designed the emails to appear to come from domains associated with security or technical support departments. The emails carry notifications for unread Microsoft Teams chats but lure victims to phishing sites capable of intercepting MFA challenges and hijacking accounts. Microsoft says the phishing campaign has "affected" fewer than 40 organizations and that the companies are Midnight Blizzard's typical "espionage objectives."
BlueCharlie (ColdRiver, Callisto, SEABORGIUM, TA453): A Russian cyber-espionage group known as BlueCharlie and ColdRiver has been spotted building new infrastructure to use in upcoming attacks. The new infrastructure consists of at least 94 domains that are most likely going to be used in phishing and other credential-harvesting operations. Security firm RecordedFuture believes BlueCharlie is retooling after the UK's cybersecurity agency exposed its old infrastructure earlier this year in January. The new infrastructure consists of at least 94 domains that are most likely going to be used in phishing and other credential-harvesting operations.
Vulnerabilities, security research, and bug bounty
Microsoft Bug Bounty Program: Microsoft has awarded $13.8 million in rewards to security researchers who reported vulnerabilities through its official bug bounty program. The funds went to 345 security researchers from 45 countries across the globe. The largest award was $200,000, the company said. The biggest The figure is nearly identical to the $13.7 million the company paid to researchers the year before that.
2022 Top Routinely Exploited Vulnerabilities: A Fortinet bug from 2018 was the most routinely exploited vulnerability of 2022, according to CISA and cybersecurity agencies from the Five Eyes Alliance. The Fortinet bug (CVE-2018-13379) replaces the Log4Shell exploit, which topped 2021's list. The rest of the Top Five is identical to last year, with three variations of the ProxyShell exploit impacting Microsoft Exchange servers and a Zoho ManageEngine RCE.

Router vulnerabilities: Cisco Talos says that since 2018 when they discovered the VPNFilter malware attacking Cisco routers, its researchers have conducted research on the router security ecosystem and identified 289 vulnerabilities impacting models from 13 router vendors. The full list of CVEs is in the company's blog post.
Tesla jailbreak: A team of researchers has revealed a new Tesla jailbreak that can provide car owners with free access to paid Tesla car features. The jailbreak targets the car's infotainment system and can provide the car with better bandwidth, faster acceleration, and heated seats. In addition, the jailbreak can also be used to pivot to other internal Tesla car systems and allow owners to modify other core features, such as self-driving capabilities, geolocation restrictions, and even migrate driver profiles between cars. The jailbreak works only on Tesla vehicles with the MCU-Z infotainment system. Academics will present this research at the BlackHat security conference in Las Vegas next week. [Additional coverage in DarkReading]
QueueJumper analysis: IBM's X-Force team has published a root cause analysis of CVE-2023-21554, an RCE in the Microsoft Message Queueing (MSMQ) service. The vulnerability is also known as QueueJumper. It was patched back in April.
Azure AD attack: Sygnia researchers have revealed a new attack that targets the Password Hash Sync mechanism in Azure AD and can intercept connector credentials and dump users' NT hashes.
AWS SSM abuse: Mitiga has published new research this week showing how AWS' Systems Manager (SSM) agent can be used as a RAT on compromised systems, controlling a (Linux or Windows) system via a remote AWS account. The attacker requires "high privilege access on an endpoint" to abuse SSM this way, but we're featuring it because it's somewhat of a novel technique that may need to be accounted in post-exploitation and IR scenarios. PoC code is on GitHub to reproduce Mitiga's techniques.
New Ivanti/MobileCore vulnerability: Ivanti has released a security alert about a new vulnerability in its MobileIron MDM product, also known as the Ivanti EPMM. Tracked as CVE-2023-35082, this new vulnerability was discovered and privately reported by security researchers at Rapid7. It is a CVSS 10 issue that can allow threat actors to bypass authentication and access a server's resources. Ivanti says it will not patch this bug because it affects older versions of its software and urged customers to update to newer versions. The issue comes on the heels of two similar bugs that were exploited in the wild in attacks that breached the Norwegian government's network. One of those zero-days (CVE-2023-35078) has now reached the point of large-scale exploitation, according to GreyNoise.
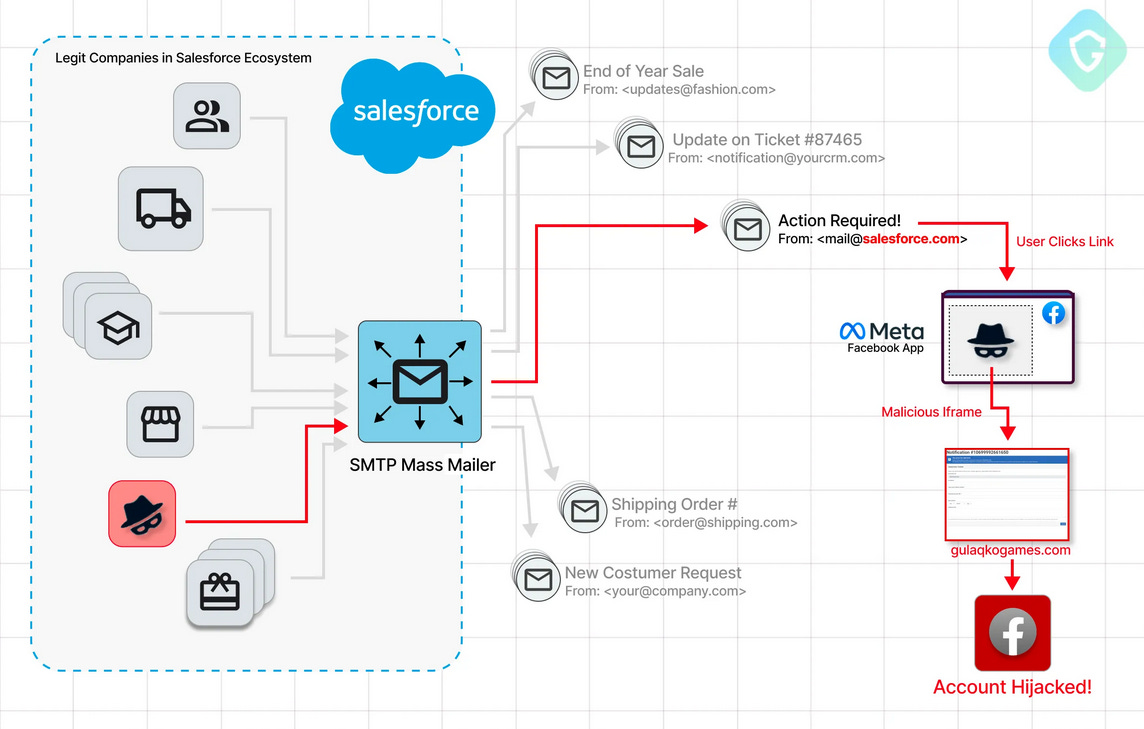
PhishForce: Threat actors have exploited zero-days in the Salesforce and Facebook Games platforms to send out a phishing campaign designed to hijack Facebook accounts. Named PhishForce, the campaign leveraged a zero-day in Salesforce to abuse its email servers and send out the phishing emails. The attackers also exploited a bug in Facebook's platform to host their phishing kits on the company's legacy games platforms. The campaign was discovered by researchers at Guardio Labs, who say they reported the issue to both platforms but that only Salesforce released a fix.
Infosec industry
HackerOne layoffs: Bug bounty platform HackerOne has laid off 12% of its staff. The company's CEO called the firings a "one-time event" as the company was forced to restructure due to current economic conditions. Most of the fired employees are based in the UK and the Netherlands.
TROOPERS23 videos: Talks from the TROOPERS23 security conference, which took place at the end of June, are now available on YouTube. Only the keynote is live. The other talks are hidden and will likely be published in the coming days.
New tool—Steampipe plugin for OpenStack: German cybersecurity firm ERNW has open-sourced a Steampipe plugin for OpenStack to allow companies to check OpenStack resource configuration for common security flaws.
New tool—RansomLord: Security researcher John "hyp3rlinx" Page has published a new tool named RansomLord that uses exploits in various ransomware strains to prevent them from running on protected systems. The tool uses exploits in 32 ransomware families, including some of the big names like AlphV, Lockbit, Clop, Play, and Royal. It does not provide full ransomware coverage, so don't rely exclusively on this for protection—obviously. It's just a very "unique" experiment.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the arguments against intellectual property theft and why there isn't a universal agreement that it should be prohibited.




