Risky Biz News: Microsoft accused of concealing Azure vulnerabilities
In other news: NSO Group might have a new owner; Microsoft patches Follina zero-day; and an actually dangerous side-channel attack.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Amit Yoran, the CEO of vulnerability management platform Tenable, published a LinkedIn post on Monday accusing Microsoft of downplaying the severity of two Azure vulnerabilities his team reported to the company earlier this year, and only patching one of them.
Quoting from a blog post by James Sebree, Principal Research Engineer at Tenable:
"It took entirely too much effort to get any sort of meaningful response from our case agent. Despite numerous attempts at requesting status updates via emails and the researcher portal, it wasn't until we reached out via Twitter that we would receive responses. During the disclosure process, Microsoft representatives initially seemed to agree that these were critical issues. A patch for the privilege escalation issue was developed and implemented without further information or clarification being required from Tenable Research. This patch was also made silently and no notification was provided to Tenable. We had to discover this information for ourselves.
During the final weeks of the disclosure process, MSRC began attempting to downplay this issue and classified it as a "best practice recommendation" rather than a security issue. [...] It wasn't until we notified MSRC of the intent to publish our findings that they acknowledged these issues as security-related. At the eleventh hour of the disclosure timeline, someone from MSRC was able to reach out and began rectifying the communication mishaps that had been occurring.
But while this looks like a bungled bug report, both Yoran and Sebree say this is part of a larger trend and "repeated pattern of behavior" where Microsoft intentionally tries to downplay or hide a security issue from its customers.
The two point to similar recent reports from companies like Wiz and Orca Security, both of which have had to deal with Microsoft botching patches and trying to hide the issue from its customers.
"For an IT infrastructure provider or a cloud service provider that is not being transparent, the stakes are raised exponentially," Yoran said on Monday.
"Without timely and detailed disclosures, customers have no idea if they were, or are, vulnerable to attack…or if they fell victim to attack prior to a vulnerability being patched. And not notifying customers denies them the opportunity to look for evidence that they were or were not compromised, a grossly irresponsible policy," he added.
"The fox is guarding the henhouse," Yoran said.
But the reason we chose to highlight this issue in today's newsletter goes far beyond how Microsoft deals with the disclosure of vulnerabilities in its Azure cloud service.
While the OS maker has gone through a period in recent years where it was far more open with security researchers and its patching process, they appear to be going back into their shell again and actively trying to hide the severity of certain security issues from its users.
One of the early indicators of this was the redesign of its Security Update Guide in September 2020. At the time, the company removed a lot of verbose information about security bugs, replacing bug descriptions with a soup of numbers and generic terms that even some of today's most experienced security researchers can barely understand and put into context.
At the time, Bob Huber, Chief Security Officer at Tenable, called it "a bad move, plain and simple."
"With this new format, end users are completely blind to how a particular CVE impacts them. What's more, this makes it nearly impossible to determine the urgency of a given patch. It's difficult to understand the benefits to end-users," Huber told this reporter in an email back in 2020.
"However, it's not too difficult to see how this new format benefits bad actors. They'll reverse engineer the patches and, by Microsoft not being explicit about vulnerability details, the advantage goes to attackers, not defenders. Without the proper context for these CVEs, it becomes increasingly difficult for defenders to prioritize their remediation efforts. Context is king and it's extremely disappointing to see Microsoft remove that from this equation."
But since then, more voices also started speaking up about their bad experiences when reporting vulnerabilities to Microsoft's bug bounty program, with many issues either being ignored, downplayed, misunderstood, intentionally left without a patch, or not even classified as security issues—adding to a general trend where Microsoft appears to be trying its best to downplay any security issue reported to its security engineers.
This has to be a joke. That path traversal 0day is a "wonfix" again. 🤦♂️
— j00sean (@j00sean) 10:45 AM ∙ Jun 7, 2022
I think someone at @msftsecresponse didn't get this is not a chromium-based bug. It's a MSDT one, buddies! Someone at Redmond should review my Twitter timeline :-) Isn't a MSRC guy there reading this? 🫤
For those looking for the Follina / CVE-2022-30190 update in the June 2022 Patch Tuesday updates, take note:
— Will Dormann (@wdormann) 5:41 PM ∙ Jun 14, 2022
Despite the patches being released today, they're listed as being released in May. 🤷
With the update, msdt.exe is still automatically spawned. But without injection.
So Microsoft only patched the "ms-msdt" #zero-day bug in Windows this PT but keep leaving the attack surface wide open, which means the next "copycat" zero-day attack coming in ..
— Haifei Li (@HaifeiLi) 6:11 PM ∙ Jun 14, 2022
Whatever is going on at the Microsoft Security Response Center, it appears that's rubbing a lot of today's top researchers the wrong way, but also creating a lot of frustration for those who have to deal with the company’s technology on a daily basis, especially from a security posture.
Breaches and hacks
Belarus leak: Belarusian hacktivist group Cyber Partisans released on Tuesday 1.5 TB of data they claim is phone calls secretly collected by the Belarusian Ministry of Internal Affairs from foreign embassies and consulates inside Belarus. The group claims they have more than 50,000 hours of recorded calls, according to Cyberscoop. Among the leaked audio are phone calls allegedly recorded inside the Russian embassy in Minsk.
🔥Wiretapped conversations of #Russian embassy in #Belarus. The "brotherly" Lukashenka turns out to be not so brotherly after all. Do you think it violates the The Vienna Convention on Diplomatic Relations of 1961?
— Belarusian Cyber-Partisans (@cpartisans) 3:11 PM ∙ Jun 14, 2022
(eng subs incl) youtu.be/wKYE3VmiC08
Shoprite incident: Shoprite, one of the largest supermarket chains in South Africa, has been hit by the RansomHouse ransomware group, according to The Record.
New Aadhaar leak: An Indian security researcher told TechCrunch that the website of PM-Kisan, an Indian government project aimed at providing Indian farmers with basic financial income, has leaked their Aadhaar numbers. The researcher said he found the issue in January, and it took the agency more than four months to fix it, with the website being patched in late May.
General tech and privacy
Firefox Total Cookie Protection: Mozilla has rolled out a new feature to Firefox users this week named Total Cookie Protection. The feature works by limiting access to cookies to the website where they were created, which has the side effect of preventing tracking companies from using the same cookies to track users browsing from across the web, from site to site. Mozilla described Total Cookie Protection as its "strongest privacy protection to date."
Thunderbird comes to Android: The Thunderbird Foundation announced that the K-9 open-source Android email client has officially joined the Thunderbird project and will soon be rebranded and relaunched as Thunderbird for Android.
IE retirement: Starting June 15, 2022, Microsoft has retired its Internet Explorer web browser from some versions of Windows 10. On affected versions, when users try to open IE or an URL, they will be redirected to Microsoft's newer Edge browser instead. IE did not ship with Microsoft's newest Windows 11 OS at all. More in Microsoft's IE retirement FAQ page.
is Internet Explorer ever truly dead?
— Tom Warren (@tomwarren) 12:30 PM ∙ Jun 14, 2022
Chrome's Rust migration: In its quarterly security newsletter for Q1 2022, Google said that work has continued on moving some of the Chrome codebase from C++ to Rust, but the Chrome team does not know if they can ergonomically mix Rust with C++ in the Chromium code yet. In addition, the Chrome team said it is also continuing its efforts to put the browser's networking service into its own sandbox process.
Government, politics, and policy
L3Harris plans to acquire NSO Group: Citing sources, IntelligenceOnline reported on Tuesday that US electronic warfare giant L3Harris is in talks to acquire NSO Group, the controversial Israeli company that's behind Pegasus, the spyware strain often found being abused by oppressive regimes against political rivals, journalists, and dissidents. The news is unexpected because the US Department of Commerce sanctioned NSO Group last fall, and seeing an American company trying to acquire it has raised many eyebrows in the intelligence community. Citizen Lab's John Scott-Railton has a Twitter thread on why this acquisition is a wrong move and a very bad idea for the US defense contractor:
4/ Could a US defense contractor exercise meaningful control over NSO?
— John Scott-Railton (@jsrailton) 11:26 AM ∙ Jun 14, 2022
Doubtful.
-The company is a sanctioned scofflaw.
-They claim sovereign immunity from the US law.
-And they stonewall their own management
Story @kayewiggins & @JavierespFT
ft.com/content/3323ae…
Secure Russian IM apps: Earlier this month, the Russian government ordered government agencies to move away from Western instant messaging services to native solutions for security reasons. At the time, the only solution was an app developed by Russian tech firm VK, but this week, Russian IT company Rostec also announced its own proprietary solution named Kolibri (or Hummingbird).
Fraud protection in Russia: Russia's Central Bank announced on Tuesday that Russian citizens will be able to activate a credit lock (ban) in their names as a way to prevent threat actors from using stolen identities to obtain loans in their names. The decision comes as pro-Ukrainian hacktivist groups have leaked troves and troves of personal data from hundreds of Russian companies over the past few months, since the Kremlin's illegal invasion of Ukraine, leaks that have exposed Russian citizens to an increased risk of fraud.
More Chinese wailing: In one of the first editions of this newsletter, we covered a recent trend from Chinese officials and state-owned media where they constantly complained about "US global spying" by referencing really old incidents from the Snowden and Shadow Broker leaks. The same trend has also been covered in a Wired article here. Well, it's another month, so more wailing from Chinese officials, this time referencing the findings of a security firm named Anzer.
Cybercrime and threat intel
GhostDNS attacks: Avast said it detected new attacks in Brazil carried out by the GhostDNS threat actor. This group breaks into SOHO routers to modify DNS settings that resolve certain DNS queries to malicious sites.
A new #GhostDNS #DNShijack #RouterEK campaign was found in Brazil on hxxp://www.asamas.com[.]br/loja01
— Avast Threat Labs (@AvastThreatLabs) 12:19 PM ∙ Jun 13, 2022
Malvertising node: hxxps://c.srvpcn[.]com/iclick?id=c
Rogue DNS servers: 66.70.155[.]224 (dead now), 167.114.43[.]24 (forwarding mode)
All avast users are already protected
NakedPages: Threat intel firm CloudSEK says it observed a threat actor selling a "battle-tested" reverse proxy, PHP-based phishing app called NakedPages on a cybercrime forum. The threat actor claims the toolkit can be used to phish users of Google and Microsoft Office.
DownThem & AmpNode: The operator of the DownThem and the AmpNode DDoS-for-hire services was sentenced to two years in prison, according to the US DOJ. Investigators said that DownThem had more than 2,000 customers at the time of its owner's arrest and had been used to launch more than 200,000 attacks. The owner, Matthew Gatrel, 33, of Illinois, ran the service with co-administrator Juan Martinez, 29, of Pasadena, who also pleaded guilty and was sentenced to five years of probation last year.
OpsPatuk: Hacktivist group DragonForce Malaysia announced last week a campaign of DDoS attacks against the Indian government and private sector entities as part of a new operation they're calling OpsPatuk. DDoS mitigation provider Radware, which has been tracking the recent attacks, said the attacks are a direct result of a BJP politician attacking the Prophet Muhammad, comments that have outraged many Muslim communities last week.
Another record-breaking DDoS attack: Cloudflare said that it mitigated last week a 26 million request per second DDoS attack. According to the company, the attack is now the largest HTTPS DDoS attack on record, beating a previous 17.2M rps HTTPS DDoS attack recorded last year.
Malware technical reports
Syslogk: Avast has published a report on Syslogk, a new kernel rootkit found in the wild and targeting Linux systems. Researchers who analyzed the malware said Syslogk was based on Adore-Ng, a relatively old, open-source, well-known kernel rootkit for Linux, which initially targeted kernel 2.x but is currently updated to target kernel 3.x releases.
BlackCat ransomware: Microsoft has published a report on the recent operations of the BlackCat/ALPHV ransomware-as-a-service (RaaS) operation. Microsoft said BlackCat's for-rent ransomware had been adopted by several of the major underground cybercrime gangs such as DEV-0237 (aka FIN12) and DEV-0504 (a prolific ransomware affiliate on many other RaaS programs).
Also, BlackCat: In addition, there is a new report that the BlackCat group is now using clear web websites using domains personalized to fit their victims as a way to threaten and leak data from some of their targets.
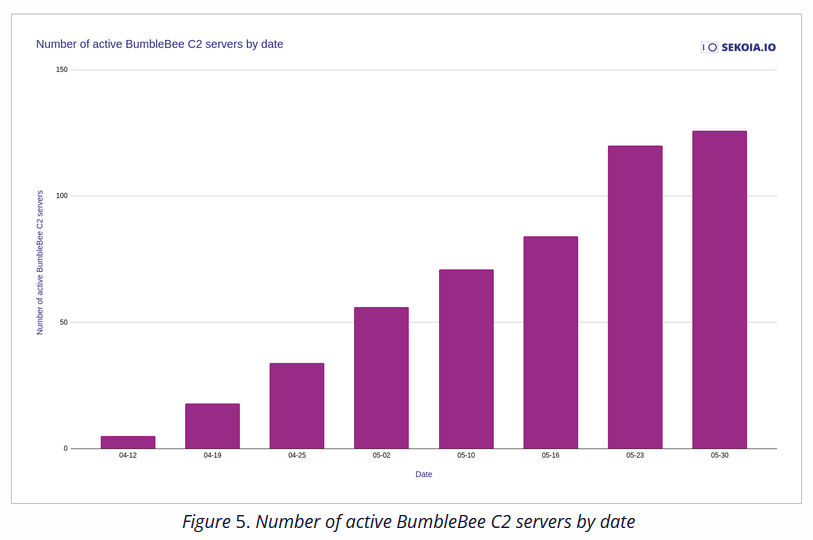
Bumblebee: Cyber-security firm Sekoia has published its own report on the new Bumblebee malware. The company said it noted a rise from only five C&C servers at the start of April to over 130 at the start of June, making Bumblebee one of the major threats today and being often used for initial access by multiple cybercrime groups.
PureCrypter: Cybersecurity firm Zscaler has published a report on PureCrypter, a malware loader strain that has been for sale on underground forums since March 2021. According to the company, the malware is written in .NET and has been observed distributing a variety of remote access trojans and information stealers.
NFT scamming: Confiant also released a report about a new tool advertised in cybercrime circles that can allow threat actors to create fake NFT minting pages that actually steal a victim's NFT ownership and even Ethereum funds. The company estimates the tool has been responsible for the theft of NFTs worth tens of millions of US dollars worth of cryptocurrency.
APTs and cyber-espionage
Gallium APT: Palo Alto Networks said on Monday that it observed the GALLIUM APT group conduct new attacks expanding from its usual targeting of telecommunication operators to also go after financial institutions and government entities. Targeted entities were located in Afghanistan, Australia, Belgium, Cambodia, Malaysia, Mozambique, the Philippines, Russia, and Vietnam, and researchers said the group also debuted a new remote access trojan for these attacks, named PingPull.
Iranian operation: Check Point has detailed a recent Iranian spear-phishing operation aimed against former Israeli officials, high-ranking military personnel, research fellows in research institutions, and think tanks. According to the company, some of the high-profile targets of this operation included:
- Tzipi Livni – former Foreign Minister and Deputy Prime Minister of Israel.
- A former Major General who served in a highly sensitive position in the Israeli Defense Forces (IDF).
- Chair of one of Israel's leading security think tanks.
- A former US Ambassador to Israel.
- A former Chair of a well-known Middle East research center.
- A senior executive in the Israeli defense industry.
Vulnerabilities and bug bounty
Follina patches: The Microsoft Patch Tuesday security updates for June 2022 are out. The OS maker fixed 61 security vulnerabilities this month, including an official patch for the Follina Office zero-day vulnerability that is currently under mass exploitation by both nation-state and cybercrime groups. An analysis of this month's patches is available on the ZDI blog.
Other Patch Tuesday fixes: Besides Microsoft, Adobe, Citrix, and Siemens have also released their own set of security updates on Tuesday.
Hertzbleed attack: A team of academics from US universities has published a research paper on Tuesday detailing a new side-channel attack they have named Hertzbleed. This new attack targets Dynamic Frequency Scaling, a feature in modern x86 processors that allows CPUs to lower their frequency to consume less power if they aren't used to their full extent. According to the research team, "Hertzbleed is a real, and practical, threat to the security of cryptographic software," compared to many other previous side-channel attacks disclosed in the past. In their tests, the team said it was able to extract cryptographic keys from remote servers. All Intel CPUs are impacted, and a vast majority of AMD's top processors, as well.
Zimbra attack: SonarSource researchers have published a report on a new vulnerability in Zimbra email systems where an unauthenticated attacker can steal cleartext credentials from Zimbra servers without any user interaction. The vulnerability (CVE-2022-27924) resides in the local Zimbra Memcache instance included in the Zimbra server's reverse proxy component and impacts the 8.8.x and 9.x versions, both of which received patches.
SynLapse details: Orca Security has published in-depth technical details about a vulnerability known as SynLapse, a remote code execution impacting the Azure Synapse Analytics and Azure Data Factory services. The vulnerability allowed attackers to hijack Azure Synapse workspaces, obtain Synapse customer account credentials, and bypass tenant Azure tenant separation.
Zombie zero-days: Google's Project Zero team has published a root-cause analysis of a zero-day first abused in the wild in 2013. P0's Maddie Stone discovered that the zero-day, initially patched in 2013, had its fix regressed in 2016 and was re-exploited again in 2022.
"25% of all 0-days detected and disclosed as exploited in-the-wild in 2020 were variants of previously disclosed vulnerabilities... Attackers don’t need novel bugs to effectively exploit users... but instead can use vulnerabilities closely related to previously disclosed ones."👇
— Tim Willis (@itswillis) 5:21 PM ∙ Jun 14, 2022
Infosec industry
GhostWriter news: GhostWriter, the project management tool for penetration testers developed by SpecterOps, has reached v3.
Microsoft buys Miburo: Microsoft announced this week plans to acquire cyber threat analysis and research company Miburo. The company is specialized in the detection of and response to foreign information operations.




