Risky Biz News: LofyGang runs amok in the npm ecosystem with minimal gains
In other news: Intel confirms BIOS/UEFI source code leak; Greek journalist sues spyware vendor; and Iranian state TV hacked.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
For almost a year, a threat actor believed to be located in Brazil has flooded the npm portal with malicious JavaScript packages that tried to pass as legitimate libraries but contained hidden functionality to steal payment card details and credentials for Discord Nitro, gaming, and online streaming accounts from infected hosts.
In a report on Friday, security firm Checkmarx said the threat actor, which goes online as the LofyGang, was behind almost 200 packages uploaded on the npm portal across 53 different developer accounts. [See full list here]
LofyGang has been prodigious this year, but despite this, they've also been very hard to spot, at least to their full extent. Checkmarx said that pieces of LofyGang's cluster of malicious packages were spotted earlier this year by other security firms, such as Sonatype, Securelist, and jFrog, but none saw the larger infrastructure.
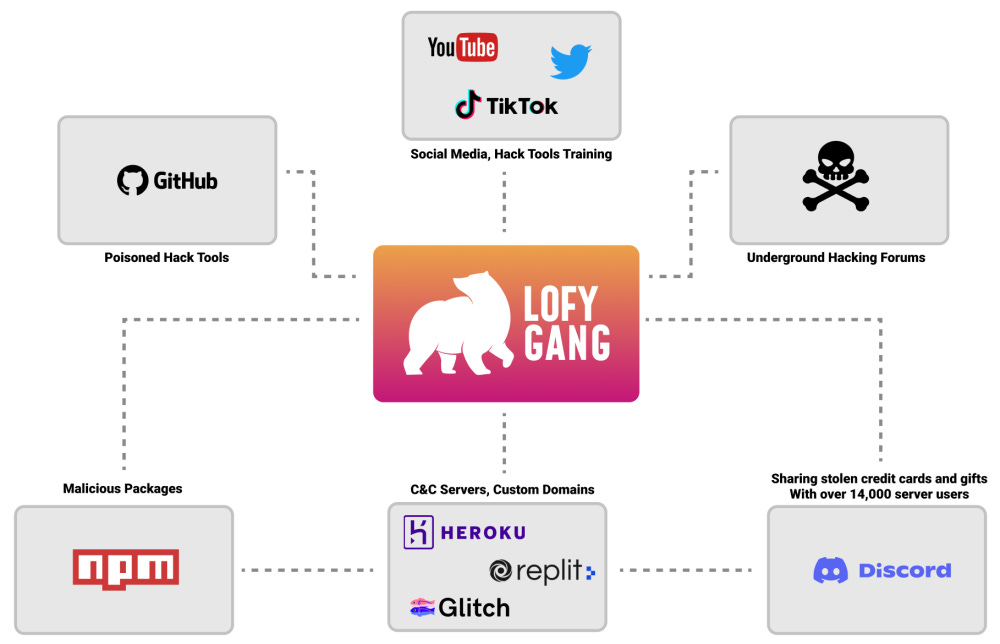
But despite their oversized presence on npm, their end goals were not up to par with their determination to infect targets. Checkmarks said that the group used the stolen credentials to merely boost their Discord server. Stolen gaming and streaming account creds were leaked on the Cracked.io hacking forum as a way to draw attention and promote their hacking tools (many of which were widely available via a public GitHub page) and an underground service for selling fake Instagram followers.
Imagine spending all this time flooding the npm portal with fake libraries, compromising developer boxes, and all of it just for some hacker rep.
We often hear about reports of malicious libraries being found on PyPI, npm, or Rubygems, but in recent years, all of these have been linked to teenage hackerism like this or to some lame cryptomining op. For all the hype surrounding supply chain attacks, it appears that threat actors like LofyGang are exhibiting a serious lack of imagination when they manage to land a malicious package on any of these repos for more than a week or two. One reason why these attacks are often spotted early on is because the DevSecOps has quickly matured, and tools to continuously scan public package repos have caught up with attackers' speed.
Breaches and hacks
BRB ransomware attack: BRB, one of the largest banks in Brazil, paid 50 BTC ($950,000) to cyber criminals last week following a ransomware attack that took place last weekend. According to Brazilian tech news outlet Tecmundo, the attack was linked to Crydat, an affiliate for the LockBit ransomware gang.
ADATA update: Chipmaker ADATA denied that it suffered a security breach last week, after the RansomHouse extortion group leaked a trove of files it claimed to have stolen from the company. ADATA said the leaked data was the same that was stolen in a ransomware attack last year.
Celsius leak: Cryptocurrency platform Celsius Network leaked the names and transaction history of hundreds of thousands of its customers. The company filed a 14,532-page document part of its bankruptcy proceedings last week that contained the names and recent transactions of every user on the platform. The judge allowed the company to redact the document, but only the home and email addresses, as the rest of the information had to be disclosed as part of regular bankruptcy procedures; hence the leak was somewhat unavoidable. The document is still available via PACER and other legal document portals. [Additional coverage in Gizmodo]
This Celsius leak may go down as one of the greatest breaches of customer information ever.
— NickH 🛡️ (@hash_bender) 12:39 AM ∙ Oct 7, 2022
Names, balances and transaction ids. Any wallet that’s ever touched Celsius is now exposed and linked to an ID
A perfect demonstration of why KYC only hurts honest consumers
Iranian TV hacked: The Edalaate Ali (Ali's Justice) hacktivist group hijacked the signal of the Iranian state television during a news bulleting on Saturday. A news piece showing Iranian Supreme Leader Ayatollah Ali Khamenei meeting with government officials was replaced with an image of Khamenei with a crosshair on his forehead and photos of protesters slain in the recent anti-government protests. The incident, which only lasted a few seconds before TV engineers cut off the broadcast, also included the phrase "join us and rise up" as the Iranian state is set to enter its second month of anti-government protests this week.
گروه «عدالت علی» اخبار ساعت ۹ شب صدا و سیما را هک کرده و تصویر سه دختر کشته شده را همراه با شعار زن زندگی آزادی نمایش داده است
— ايران اينترنشنال (@IranIntl) 6:21 PM ∙ Oct 8, 2022
General tech and privacy
Tracking Linux users online: In an academic paper published last month, a team of academics from the Hebrew University of Jerusalem said they found a security flaw in the Linux kernel that allowed them to individually track Linux users across browsers, browser privacy modes, containers, and IPv4/IPv6/VPN networks. The research team said they reported the issue to the Linux kernel team, who fixed it in a security patch this May.
"We describe a tracking technique for Linux devices, exploiting a new TCP source port generation mechanism recently introduced to the Linux kernel. This mechanism is based on an algorithm, standardized in RFC 6056, for boosting security by better randomizing port selection. Our technique detects collisions in a hash function used in the said algorithm, based on sampling TCP source ports generated in an attacker-prescribed manner. These hash collisions depend solely on a per-device key, and thus the set of collisions forms a device ID that allows tracking devices across browsers, browser privacy modes, containers, and IPv4/IPv6 networks (including some VPNs). It can distinguish among devices with identical hardware and software, and lasts until the device restarts."
Intel code leaks online: An unknown individual leaked the source code for Intel's Alder Lake BIOS/UEFI firmware earlier this week in a 4chan post. Intel confirmed the leak on Sunday and said that they "do not rely on obfuscation of information as a security measure." More details are available here, and a script also exists to check if your system is using the leaked BIOS/UEFI firmware.
Greek journalist sues spyware maker: Greek finance journalist Thanasis Koukakis has filed a lawsuit this week against Intellexa, the company behind the Predator spyware. Koukakis is one of the four major political figures who had their smartphones infected with the Predator spyware in a scandal that is rocking the Greek government.
Avast marks Firefox as ransomware: Mozilla released an emergency security update for Firefox on Friday to fix an issue where the Avast and AVG antivirus products were detecting Firefox installations as ransomware and crashing users' browsers.
Avast thinks that the Mercurial executable we ship with Mozilla's tooling for Windows is actually ransomware. Just in case you needed to know how bad Avast is.
— Gabriele Svelto (@gabrielesvelto) 12:22 PM ∙ Oct 7, 2022
Government, politics, and policy
EU-US data flow agreement: US President Joe Biden signed an executive order on Friday, setting up a new legal framework for personal data transfers between the EU and the US. The new EO is meant to replace the past Safe Harbor and Privacy Shield agreements, both of which were struck down by the European Court of Justice in 2015 and 2020, respectively, for not protecting user data against sprawling signals intelligence collection practices. According to a fact sheet for the new agreement, the White House claims it has added more safeguards, but some EU privacy advocates do not seem impressed. [Additional coverage in CNBC]
Election company CEO arrested: The Los Angeles County district attorney announced on Tuesday the arrest of Eugene Yu, the CEO of Konnech, the company behind PollChief, an election worker management software platform. US officials said Yu stored the personal details of the app's users on servers located in China, which is in violation of the data privacy and security clauses of its contract with the state of California.
Guacamaya leaks expose Chile's spyware secrets: OCCRP reporter Jurre van Bergen has a nice Twitter thread on how a recent leak from the Guacamaya hacktivist group has exposed the Chilean government's dealings and courtship of spyware vendors, including Xmartlab, an NSO Group reseller.
The hacktivist group Guacamaya compromised the chiefs of staff of Chile and published several gigabytes of their e-mail spools online. In this data, there's some references to known spyware and resellers of these tools. 🧵👇
— 🏴 Jurre van Bergen (@DrWhax) 10:06 AM ∙ Oct 6, 2022
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. Last week, the company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
Phisher detained in the Netherlands: Dutch authorities are requesting a three-year prison sentence for a 24-year-old man from Amsterdam accused of carrying out phishing campaigns. According to Dutch authorities, the suspect was detained after he created a phishing template using the text from an authentic banking email he received himself but forgot to remove a link that contained a unique identifier that allowed authorities to track him down.
Meta discovers malicious apps: Meta's security team said on Friday that it discovered more than 400 Android and iOS apps that contained hidden functionality meant to steal Facebook account credentials. The company said the apps were disguised as legitimate applications, some were hosted on the official Google Play Store and Apple App Store, and that more than one million Facebook users installed the apps and are currently being notified to change their account passwords.
1/ We just shared new security research by our malware discovery team into 400+ malicious iOS and Android apps. They were designed to steal people's Facebook login info 🧵 about.fb.com/news/2022/10/p…
— David Agranovich (@DavidAgranovich) 2:07 PM ∙ Oct 7, 2022
Malware technical reports
Clever cryptominer: Bitdefender researchers have a report on a new cryptominer operation that lures users with pirated and cracked software but then exploits a DLL side-loading vulnerability in the Microsoft OneDrive app to install a cryptocurrency miner on their systems. Bitdefender said the malware has infected at least 700 users between May 1 to July 1 this year.
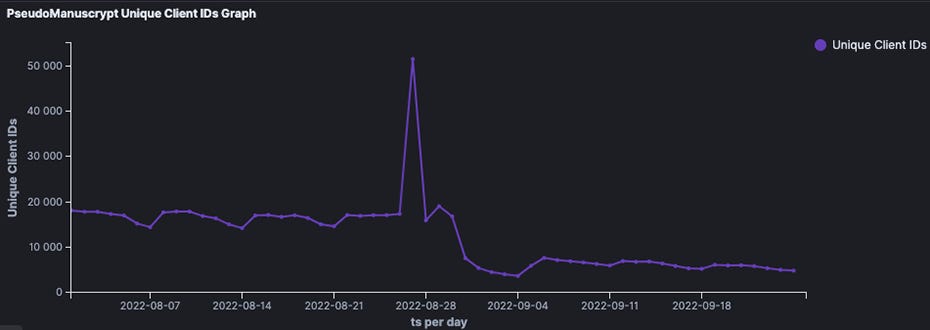
PseudoManuscrypt: Security firm BitSight said in a report last week that they tracked up to 51,500 systems infected with the PseudoManuscrypt malware until its operators changed their command-and-control infrastructure at the end of August. Since then, the botnet has gone down to around 7,000 daily infected systems.
APTs and cyber-espionage
Mustang Panda: BlackBerry's security team published a report last week on a recent campaign carried out by Mustang Panda, a Chinese government-linked espionage group, against Myanmar government agencies.
https://securelist.com/top-10-unattributed-apt-mysteries/107676/
Vulnerabilities and bug bounty
Fortinet auth bypass: Networking equipment vendor Fortinet privately notified customers last week about an authentication bypass (tracked as CVE-2022-40684) in the web admin interface of its FortiGate firewalls and FortiProxy web proxies. It's unclear why the company notified customers in private instead of a public security advisory, so all clues now suggest the issue may be easily exploitable.
Update: By now the full text of the e-mail and a screenshot of the internal advisory have been shared.
— Gitworm (@Gi7w0rm) 2:54 PM ∙ Oct 7, 2022
So here goes a screenshot of the unredacted full e-mail as shared on Facebook. Also containing possible #workarounds.
#Fortinet #CVE202240684 #RCE #authbypass #advisory
Dompdf vulnerability: Tanto Security disclosed a vulnerability in Dompdf, a popular PHP library used for rendering PDF files from HTML. The vulnerability allows RCE in PHP apps that use it.
Infosec industry
New tool—Aftermath: Cybersecurity firm Jamf open-sourced last week a new project called Aftermath, a Swift-based, open-source incident response framework for macOS.
New tool—IcedID Decryptor: Matthew B., a security researcher at Huntress Labs, has open-sourced a new tool called IcedID Decryptor that can extract configuration data from systems infected with the IcedID malware, information typically stored in a file called license.dat.
I recently wrote a static decoder for encrypted #IcedID files using Ghidra and Python😀
— Matthew (@embee_research) 11:21 AM ∙ Oct 1, 2022
You can find it on Github, along with some sample files to play around with.
github.com/matthewB-huntr…
1/ More notes below👇
#Malware #RE #reversing #ghidra




