Risky Biz News: LockBit gang made $91 million from US attacks
In other news: Microsoft identifies new GRU-operated APT; Atomic Wallet losses surpass $100 million; and Mandiant links Barracuda zero-day attacks to Chinese hackers.
This newsletter is brought to you by Thinkst Canary. You can subscribe to a podcast based on this newsletter by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The operators of the LockBit ransomware are believed to have made more than $91 million in ransom payments from more than 1,700 attacks targeting US organizations, according to CISA and the FBI.
The figure covers LockBit's entire lifespan since its official launch in January 2020, but it does not include ransom payments that have not been reported to the FBI or payments made by foreign companies.
Regardless, this puts LockBit right up there with the best-earning ransomware gangs of all time, trailing the likes of Ryuk, REvil, and Darkside. [obviously, based on limited visibility into the ecosystem]
- Ryuk – $150 million
- REvil – $123 million in 2020
- Darkside – $90 million between October 2020 and May 2021
- Maze/Egregor – $75 million
- Cuba - $43.9 million throughout 2021
- Conti - $25.5 million between July and November 2021
- Netwalker – $25 million between March and July 2020
- Dharma - $24 million between November 2016 and November 2019
In a very crowded ransomware landscape, officials attribute the group's success to several factors, including its constant presence on underground hacking forums and a dumbed-down point-and-click interface that lowers the technical know-how needed to use its encryption tools.
In addition, officials say LockBit has pioneered a new Ransomware-as-a-Service model where ransom payments go to its collaborators (called affiliates), who then pay a percentage back to the LockBit admin team.
Putting trust in its affiliates has helped the gang make a name for itself early on, back when most RaaS platforms would collect the payments themselves and then pay out affiliates—often leading to many affiliates getting scammed.
This explains why LockBit has been the most popular ransomware strain used in big-game hunting ransomware intrusions for almost a year and a half now. For example, one in five ransomware attacks that take place in Canada and one in four in New Zealand are carried out using LockBit.
Notable victims of LockBit extortions include Continental, Bridgestone, Accenture, UK Royal Mail, the city of Oakland (California), and the Italian Internal Revenue Service.
Another LockBit affiliate detained
The group has also been one of the most resilient ransomware operators in recent times, surviving a leak of its code—an incident that usually causes other gangs to shutter operations and rebrand.
LockBit's incessant operations have also put the gang on the radar of global law enforcement. So far, official charges have been filed against three of its affiliates, and two have been detained.
A first LockBit affiliate (Mikhail Vasiliev) was detained in Canada in November 2022 and he is currently awaiting extradition to the US.
A more "famous" LockBit affiliate named Mikhail "WazaWaka" Matveev was charged in May. Matveev remains at large in Russia.
A third LockBit affiliate (Ruslan Magomedovich Astamirov) was arrested in Arizona last month and charged this week.
If you're wondering what was a Russian national involved in the biggest ransomware operation today doing in the US, we have no good answer for you. Sorry!
Breaches and hacks
Bykea hack: Hackers have breached Pakistani bike-hailing and parcel delivery company Bykea and used its app to hurl insults at its users. Bykea blamed the incident on a compromised third-party communication tool that is typically used to show users notifications and popups. Due to the nationalistic theme of the messages, most users believe the hack was carried out by Indian hackers. The app has over 10 million users and operates in over 100 cities across Pakistan. [Additional coverage in The Print]
Atomic Wallet losses pass $100M: Losses from the hack of the Atomic Wallet service have now surpassed the $100 million mark, according to blockchain analytics service Elliptic. More than 5,000 Atomic crypto-wallets have been hacked so far. At least ten wallets lost more than $1 million worth of crypto-assets, while the average loss is $2,800/per wallet. The hack has been linked to North Korea's Lazarus Group. Funds are currently being laundered through Garantex, a Russian cryptocurrency exchange sanctioned by the US Treasury, and Sinbad, the reincarnation of the Blender mixing service, also sanctioned by US officials.
Hashflow crypto-heist: Cryptocurrency platform Hashflow has been hacked for $600,000. The platform says it will pay back all users who lost funds in the attack.
MOVEit hacks: The tally of organizations who have officially confirmed they've been hacked because of their MOVEit software has now reached 27, with the Johns Hopkins University and health system joining the list. In the meantime, CISA has also confirmed that the hacks have also impacted "several federal agencies."
General tech and privacy
EU statement on Google ad monopoly: The European Commission has published an official statement on its anti-monopoly case against Google. The Commission has concluded that Google's advertising business has broken EU monopoly laws and has threatened to fine the company and force it to break off its ad division. Google has an official response and claimed the success of its ad business has helped it keep many of its services free of charge.
Megaupload staffers sentenced: Two members of the Megaupload file-hosting service were sentenced to prison for their role in facilitating online piracy and being part of a criminal group. Mathias Ortmann was sentenced to 10 years and six months in prison, while Bram van der Kolk was sentenced to 10 years. [Additional coverage in Stuff]
Government, politics, and policy
FCC Privacy and Data Protection Task Force: The US Federal Communications Commission has launched a Privacy and Data Protection Task Force. The new task force will help the FCC draft laws and investigate data privacy incidents in the telco space. This will include breaches at telco providers and supply chain attacks and vulnerabilities at telcos and their suppliers.
CISA&NSA advisory on BMCs: CISA and the NSA have published joint guidance on the need for organizations to secure their baseboard management controllers (BMCs). More from said Neal Ziring, the Technical Director for NSA's Cybersecurity Directorate.
"Implementation of effective security defenses for these embedded controllers is frequently overlooked. The firmware in these controllers is highly privileged. Malicious actors can use the firmware's capabilities to remotely control a critical server while bypassing traditional security tools."
NNSA cyber report: GAO has published a report on the cybersecurity posture of tools used by the National Nuclear Security Administration (NNSA) to produce nuclear weapon components and in nuclear weapons themselves.
"NNSA officials told us that cyber risks vary from one nuclear weapon type to another. NNSA officials said that they have conducted preliminary reviews and determined that current nuclear weapons generally contain little IT that is at risk due to their age and reliance on older technology. Newer and more modern weapons are slated to begin entering the stockpile after 2030 and may contain more IT, however. For these weapons, NNSA officials said that each program is still considering approaches to managing cybersecurity risks as part of the weapon design and development process."
White House cyber official departs: Rob Knake, who has served as deputy national cyber director for budget and policy at the Office of the National Cyber Director (ONCD), is departing his role at the White House [Additional coverage in The Record]
SORM fines are now live: Russian President Vladimir Putin has signed a bill into law that imposes big fines on Russian ISPs that fail to implement the government's internet traffic surveillance system SORM. Fines range from 0.001-0.003% of annual revenue for the first violation and 0.01-0.03% for the second. [Additional coverage in Digital Russia]
Germany government national security strategy: The German government has published its national security strategy [PDF]. The document addresses risks from China and Russia and also covers the threat of cyberattacks and disinformation campaigns. [Additional coverage in the AP]
EU proposals to counter spyware abuse: The European Parliament has outlined a series of reforms needed to curb the abuse of spyware tools by some of its members. Recommendations below.
- EU should have rules on the use of spyware by law enforcement
- An in-depth review of spyware export licenses
- Stronger enforcement of the EU's export control rules
- A joint EU-US spyware strategy
- The creation of an EU Tech Lab to investigate surveillance and provide technological support, including device screening and forensic research
Sponsor section
This edition is brought to you by Thinkst Canary. Most companies find out way too late that they've been breached. Thinkst Canary changes this. Deployed and Loved on all seven continents. Deploys in minutes; almost zero admin overhead. It just works!
Cybercrime and threat intel
Phishing gang detained: Ukraine's Cyber Police has disrupted the activities of a phishing gang that hijacked more than 15,000 Telegram accounts. The gang consisted of five Ukrainians and one Russian national.
Proofpoint Human Factor report: Security firm Proofpoint has published its annual Human Factor report. The report analyzes recent techniques used by threat actors that combine technology and psychology to go after their targets. The report looks at TOAD attacks, new phishing techniques that bypass MFA, and recent social engineering techniques adopted by the likes of Emotet and SocGolish.
Another BreachForums clone: After law enforcement agencies took down the original BreachForums in March this year, another clone has now popped up online at BreachForums.vc. [Additional coverage in DataBreaches.net]
Illuminati scams: There's a legitimate—and I kid you not—scam campaign taking place where a threat actor named "Grand Masters" is tricking people into joining the Illuminati world-controlling organization and then scamming them out of their funds.
Bignum supply chain attack: Checkmarx has the details on how a threat actor has hijacked the AWS S3 bucket used by the Bignum npm library and attempted to carry out a supply chain attack.
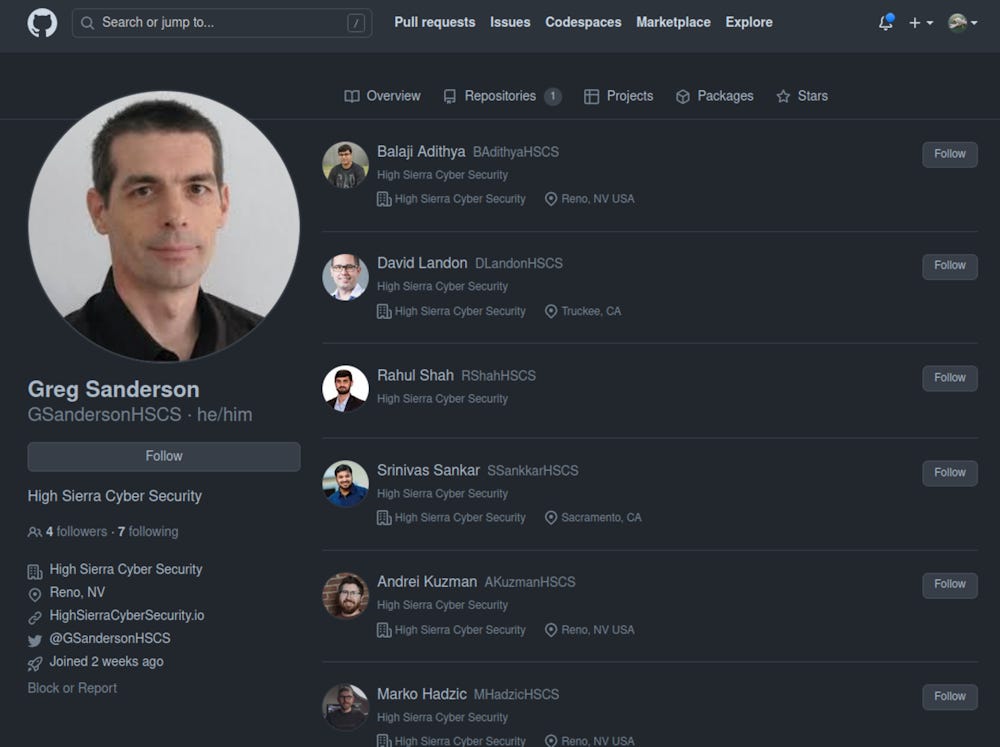
Malware in fake PoCs: A threat actor is posing as security researchers and publishing fake zero-day exploits laced with malware. The campaign, spotted by VulnCheck, has been active since May and has promoted supposed zero-days for popular software like Chrome, Discord, Exchange, Signal, and WhatsApp. The exploits are hosted on GitHub and promoted on Twitter using personas who claim to work for a company called High Sierra Cyber Security. Some of these accounts use photos of real security researchers, including Rapid7 employees. The malware baked into the fake PoCs works as a downloader for additional payloads. This is not new, btw.
Malware technical reports
IIS web shells: CISA has released additional IOCs for web shells that are being installed on government IIS servers by exploiting a 2017 Telerik vulnerability (CVE-2017-9248). CISA previously warned about this activity back in March; however, those initial attacks exploited a different 2019 security flaw (CVE-2019-18935).
Diicot malware: Cado Security says that a cybercrime group calling itself Diicot has recently expanded from cryptomining operations to running a DDoS botnet, defacing websites, and selling hacking tools via a Malware-as-a-Service platform. The group has been active since at least 2020 and was previously known as Mexals. Its recent name was taken from DIICOT, the name of Romania's anti-terrorism and organized crime agency. Cado Security, Akamai, and Bitdefender all believe the threat actor behind this malware is either based in Romania or a Romanian speaker.
Vidar: Team Cymru has published a second part of their analysis of the server infrastructure used by the Vidar infostealer. Part one is here.
Mystic Stealer: A new infostealer named Mystic Stealer is being advertised on underground cybercrime forums. The malware was launched in April and has already reached v1.2. Reports are available from CyFirma, InQuest, and Zscaler.
Skuld: Trellix researchers have discovered a new Go-based infostealer named Skuld. The stealer has already been used in the wild. Trellix has identified the malware's author as an individual named Deathined. The malware has been cobbled together from other open-source malware projects and also includes clipper capabilities.
SeroXen: Trend Micro has an analysis of the new SeroXen RAT (see previous AT&T report here).
GravityRAT: The latest version of the GravityRAT Android remote access trojan can now steal WhatsApp backups and delete files from compromised hosts.
"The actor behind GravityRAT remains unknown; we track the group internally as SpaceCobra."
Android malware: PAN's Unit42 has a rundown of Android malware strains impersonating ChatGPT apps.
Terminator: VoidSec has reverse-engineered Terminator, a tool that uses BYOVD techniques to bypass security solutions.
Shampoo: HP Wolf Security detected a new malware campaign built around a new malicious ChromeLoader extension called Shampoo. ChromeLoader is a family of malicious Google Chrome browser extensions that hijack search queries and redirect users to malicious sites. The Shampoo campaign is the latest iteration of this gang's campaign.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
APTs and cyber-espionage
Cadet Blizzard: Microsoft has identified a new APT group operating under Russia's GRU military intelligence service. Dubbed Cadet Blizzard, the group is distinct from other GRU APTs like Sandworm (Seashell Blizzard and Iridium) and Fancy Bear (Forest Blizzard and Strontium). Microsoft says Cadet Blizzard conducts cyber-espionage to support Russian military operations in Ukraine. The group also developed and deployed the WhisperGate data wiper against Ukrainian organizations, defaced Ukrainian websites, and operated the hack-and-leak forum known as "Free Civilian." Cadet Blizzard began operations in 2020 and besides Ukraine, has also carried out operations in Europe, Latin America, and Central Asia.
Shuckworm: The Shuckworm (Gamaredon) Russian cyber-espionage group has refreshed its toolset in a bid to stay undetected in its operations targeting Ukraine. According to Broadcom's Symantec division, the group has rolled out new versions of known tools, along with new additions, such as malware that spreads via USB devices. These new tools were used in cyber-espionage campaigns targeting Ukraine's security services, military, and government organizations. Symantec says the group has been focused on acquiring military and security intelligence in order to support Russia's invading forces.
"The attackers repeatedly attempted to access and steal sensitive information such as reports about the deaths of Ukrainian military service members, enemy engagements and air strikes, arsenal inventories, military training, and more."
Blind Eagle: Qihoo 360's security team has published a report on the Blind Eagle (APT-C-36), the suspected Latin American APT group.
North Korean espionage: South Korea's intelligence agency has published a security advisory warning that North Korean espionage groups are conducting phishing operations targeting users of Naver, a South Korean email service.
Another Lazarus zero-day campaign: The Lazarus North Korean cyber-espionage group is exploiting zero-days in South Korean financial software packages VestCert (from Yettiesoft) and TCO!Stream (from MLsoft). The group uses watering hole attacks to lure victims to malicious sites. If the victims have a vulnerable version of the software installed on their device, the group uses the VestCert zero-day to install malware on their systems. On the other hand, the TCO!Stream is used for propagation through internal networks if a victim has the software installed in their environments. The same group previously exploited similar zero-days in other South Korean software such as INISAFE CrossWeb EX and MagicLine4NX.
Earth Preta: Trend Micro has published a report on the new malware tools and delivery tactics employed by the Earth Preta (Mustang Panda) Chinese APT in campaigns conducted this year.
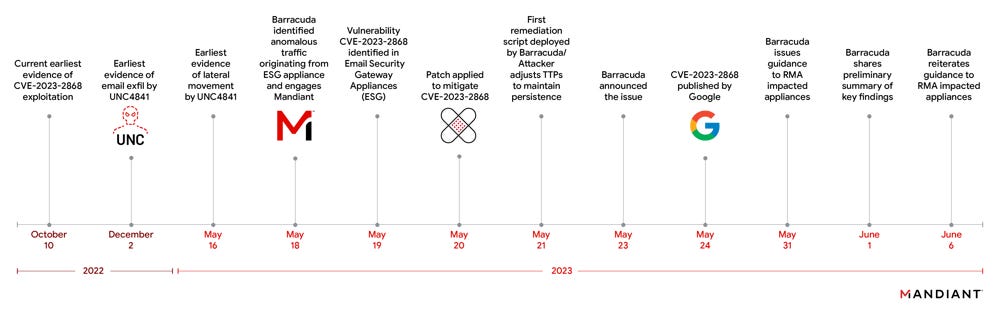
Barracuda attacks linked to China: Google's Mandiant division has linked the recently disclosed Barracuda zero-day (CVE-2023-2868) attacks to UNC4841, a suspected Chinese cyber-espionage group. Mandiant says UNC4841 attacks began in October 2022, and the group began exfiltrating email inboxes from hacked Barracuda servers on May 16, a week before Barracuda disclosed the incidents. Barracuda has recommended that all customers who had servers compromised replace their Barracuda appliances.
Vulnerabilities, security research, and bug bounty
MOVEit bug analysis: Assetnote researchers have published a two-part series on the MOVEit vulnerability (CVE-2023-34362) exploited by the Clop gang.
Third MOVEit vulnerability: In the meantime, Progress Software says it is in the midst of patching a third vulnerability in its MOVEit file-transfer appliance. This one hasn't been exploited in the wild yet.
Azure XSS vulnerabilities: Orca Security has identified XSS vulnerabilities in two Azure services—Azure Bastion and Azure Container Registry. The vulnerabilities allow unauthorized access to victim sessions and, if exploited, could allow data exfiltration, unauthorized modification, and the disruption of Azure service iframes. Microsoft has issued a patch.
Tor deanonymization: Security researcher Sh1ttyKids has published details about a new Tor server deanonymization trick that uses the entity tag (ETag) portion of an HTTP response header. The technique was initially developed back in November 2020 and privately shared with law enforcement agencies. The FBI seems to have used this technique to deanonymize the dark web leak site of the RagnarLocker ransomware group.
Bypass BIOS password on Lenovo laptops: CyberCX researchers have found a way to bypass the BIOS password on Lenovo laptops by shorting two motherboard pins using a small screwdriver while the PC boots up.
"As you can see in the demo, I power the laptop on, then I use the ‘elite’ technique of jamming a small screwdriver across the SCL and SDA pins to short them until entering the BIOS.
An interesting note is you could bypass the password, make changes to the BIOS, for example change the boot drive, and then not perform the short on next boot. You could then load into a new OS, do what you need to do, then re-short the pins again, changing the setting back. This still leaves the existing password in the EEPROM so a victim’s laptop would not have any evidence of tampering."
Drone security research: New research from IOActive shows that unmanned aerial vehicles are vulnerable to electromagnetic fault injection (EMFI) attacks that can allow a threat actor to run malicious code even if the drone is running up-to-date firmware. The attack was successfully tested against a DJI Mavic Pro drone, but in theory, it should work on other vendors and models as well.
"We demonstrated that is feasible to compromise the targeted device by injecting a specific EM glitch at the right time during a firmware update. This would allow an attacker to gain code execution on the main processor, gaining access to the Android OS that implements the core functionality of the drone."
EPP attack: A team of security researchers has identified vulnerabilities in the Extensible Provision Protocol that could be used to hijack top-level domains. The protocol allows domain registrars to communicate with each other and exchange information about their customers' domain name updates and new domain registrations. Researchers say that by exploiting an XML parsing vulnerability in EPP server software, they were able to hijack the root zones of 19 top-level domains, including the national domains for countries like the Ivory Coast, Kenya, Benin, Nigeria, Lebanon, Chad, and others.
"Our efforts in this space led to the ability to control the DNS zones of the following ccTLDs: .ai, .bj, .bw, .ci, .gl, .ke, .kn, .lb, .ly, .mr, .ms, .mz, .ng, .py, .rw, .so, .ss, .td, .zm."
New crypto recovery attack: A team of academics has devised a new attack that can recover encryption keys from smart cards and smartphones. The attack relies on recording the power LED of these devices when they're processing cryptographic operations. By analyzing flickers in the LED's intensity as the device allocates power to process cryptographic operations, the research team says they are able to infer encryption keys. The attack combines previous cryptographic side-channel techniques like Minerva and Hertzbleed. It was successfully tested on devices placed as far as 16 meters away from the recording device. [Additional coverage in ArsTechnica]
Infosec industry
New tools—Coalition ESS: Cyber insurer Coalition has launched its own vulnerability scoring system named the Coalition ESS.
Lemmy infosec instance: For members of the infosec community looking to step away from the Reddit drama, there's now a Lemmy instance just for you. The instance is managed by Jerry Bell, the admin of the Infosec.exchange Mastodon instance.
Hold Security sues Microsoft: Hold Security has filed a lawsuit against Microsoft, accusing the company of breaking an NDA contract. In a complaint filed last month, Hold says Microsoft requested access to a collection of more than 360 million credentials the company had found on the dark web. The security firm says that Microsoft broke an NDA and did not delete copies of credentials not associated with Microsoft logins. Instead, Hold says Microsoft used the collected credentials to show password compromise alerts for accounts on its Azure AD FS, LinkedIn, and GitHub services. [Additional coverage in GeekWire]
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the elements that make them think an operation is state-backed.




