Risky Biz News: LockBit-Mandiant drama, explained
In other news: New iOS security features announced at WWDC; Russia launches national phishing portal; and US warns of Chinese hackers targeting telcos.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
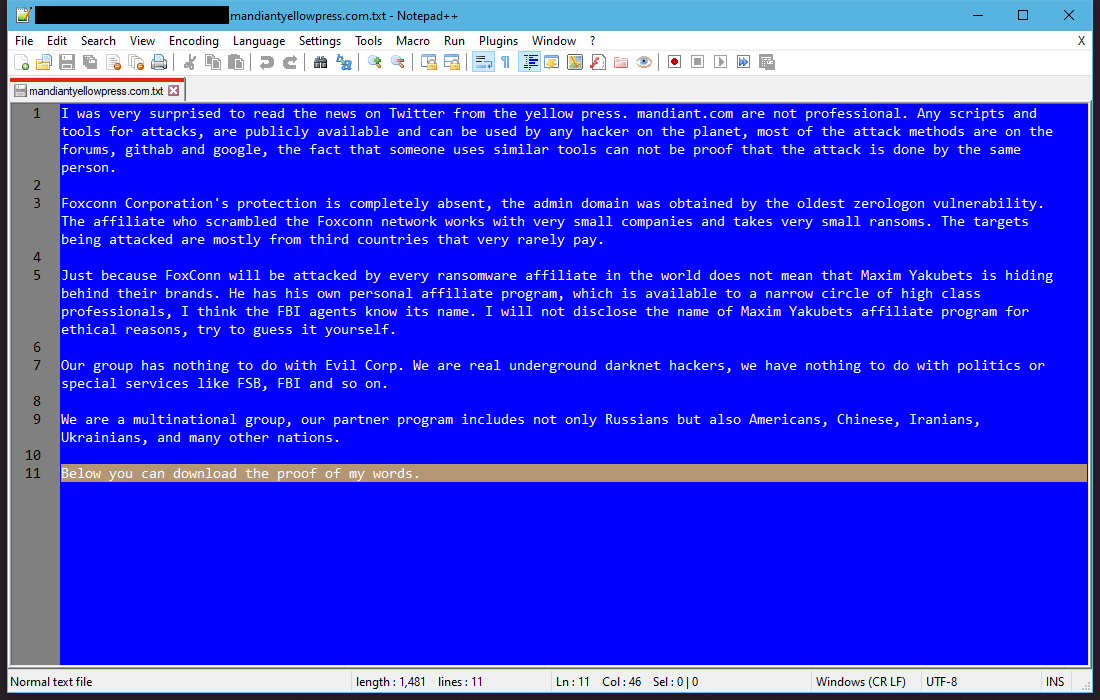
Standing as evidence that most ransomware gangs have the emotional intelligence of a petty 12-year-old online gamer, the group behind the LockBit ransomware pulled off one of the most cringe-worthy stunts in recent years after, on Monday, the group published an entry on its "leak site" claiming to have breached and encrypted the network of cybersecurity giant Mandiant (formerly FireEye).
The announcement made a huge initial wave through the cybersecurity community, but it didn't take long for industry experts to regain their wits and realize how unrealistic such an intrusion would be.
Obviously, Mandiant dismissed the claims as untrue; a task made immensely easier by the LockBit gang itself, which failed to share any evidence of their successful attack.
But the reality is that there was no such intrusion and one had to read between the lines to understand what really happened over the weekend.
All of the Monday drama is actually related to a report Mandiant published last week on EvilCorp, a major Russian cybercrime cartel that previously operated the Dridex banking trojan and ransomware strains such as Locky, Hades, WastedLocker, and BitPaymer.
One of the report's findings was that after getting sanctioned by the US Treasury in December 2019, the EvilCorp group has been having a harder and harder time receiving ransom payments following their intrusions, as victims and ransomware negotiators would not want to break sanctions, fearing fines and possible prosecution from US authorities.
Over the past two and a half years, EvilCorp tried to avoid the looming sanctions by developing new ransomware strains and constantly rebranding their Ransomware-as-a-Service (RaaS) portals, often posing as a new cybercrime group that just launched on the criminal underground.
However, security researchers kept findings clues linking these new services to the old EvilCorp gang. As this tactic appears to have become inefficient in recent months, Mandiant said last week that EvilCorp members began using the RaaS services of other gangs, hoping to disguise their real identity as a mere sub-group of another ransomware cartel.
But just by publishing its report last week, Mandiant indirectly nuked the profitability of the LockBit RaaS into the ground, six feet under, dead and buried.
Just by casually linking the EvilCorp brand with LockBit's operation, Mandiant has (accidentally?/intentionally?) ensured that victims and ransomware negotiators would now be just as skittish in making or approving payments following a LockBit attack, fearing the legal hammer of US authorities. This means that LockBit's profits are about to take a ginormous hit over the next few weeks—and LockBit knows it!
Hence, that's why we had all that kindergarten-level drama on Monday, which was nothing else but LockBit trying to ruin Mandiant's reputation in return, but with little success and only managing to make themselves look like fools in the process.
And LockBit also knows that nobody believed their wild claims since a few hours later, on Monday, the group also published a statement that is the definition of "damage control," a statement where they tried to distance themselves from EvilCorp and their leader, Maksim Yakubets, claiming no association. Alas, good luck getting paid, LockBit!
Breaches and hacks
Palermo: The IT infrastructure of the city of Palermo, Italy, has been down since last Friday following a cyber-attack.
Maiar hack: DeFi platform Maiar said on Monday that a threat actor exploited a vulnerability on its platform and stole more than $113 million worth of cryptocurrency from its wallets. In a YouTube video published on Tuesday, the platform's CEO said they had already recovered 95% of the stolen funds.
Schulte profile: The New Yorker has a fantastic profile of Joshua Schulte, the former CIA agent behind the WikiLeaks Vault7 leak.
General tech and privacy
iOS gets separate security update mechanism: At the WWDC 2022 developer conference this week, Apple announced plans to add a new feature to iOS called Rapid Security Response that will allow the company to deploy security updates to its devices as separate patches without needing to update the entire operating system. The new feature will be added in iOS 16, scheduled to be released later this fall.
iOS to protect victims of domestic abuse: In addition, at the same WWDC 2022 conference, Apple also announced plans to add another feature in iOS 16 to protect people in or leaving abusive relationships. Called Safety Check, the new feature will help users manage app access and passwords and let them know who else has their passwords and personal information. But the best feature is something called an "emergency reset" that allows users to sign out of iCloud, lock down privacy settings and limit incoming messages to only "the device in their hand."
Government, politics, and policy
Chinese telco spying: CISA, the NSA, and the FBI published a joint security advisory on Tuesday detailing a major hacking operation carried out by the Chinese government aimed at compromising major telecommunications companies and network service providers across the world. The advisory contains a list of vulnerabilities that Chinese threat actors have used to gain a foothold on targeted networks, along with other common tradecraft employed in these intrusions. Targeted equipment includes devices from Cisco, D-Link, Citrix, DrayTek, Fortinet, Netgear, QNAP, Pulse, Zyxel, and MikroTik, as well as some open-source software running on telco servers.
Russia threatens the US: In a statement published by the Russian Foreign Ministry on Monday, the Kremlin government accused the US of using Ukraine and its IT Army to launch cyberattacks against Russian targets. Russian officials also threatened the US with retaliatory attacks:
[...], we do not recommend that the United States provoke Russia into retaliatory measures - a rebuff will certainly follow, it will be firm and resolute. However, the outcome of this "mess" could be catastrophic, because there will be no winners in a direct cyber clash of states."
Russia launches phishing monitoring portal: The Russian government has launched an official portal for reporting and monitoring phishing websites. The website has been in the works since last year and can allegedly monitor up to one million Russian websites per hour. (h/t Oleg Shakirov)
IMEI codes database: Russia's FSB agency has instructed the Ministry of Digital Development to develop a database of mobile phone IMEI codes for all devices across Russia, Kommersant reported. The idea of creating such a database has been first suggested in the early 2010s as a way to improve and fast-track law enforcement investigations.
UN cybercrime treaty moves forward: A collection of autocratic countries are pushing forward with a Russian-proposed cybercrime treaty that would criminalize online free speech. Representatives from Egypt, Jordan, Russia, Belarus, Burundi, China, Nicaragua, Tajikistan, India, Kuwait, Pakistan, Algeria, Sudan, Burkina Faso, and Tanzania pushed the treaty forward towards new discussions last week. The treaty has alarmed many privacy and human rights organizations. The EFF and more than 130 civil society groups previously warned that Russia's proposed UN cybercrime treaty would be used to target journalists, whistleblowers, political dissidents, security researchers, LGBTQ communities, and human rights defenders, as these countries have been doing internally for years now, with the treaty giving them the ability to mobilize global law enforcement towards their oppressive goals.
Cybercrime and threat intel
Binance exposed: In an investigative piece published on Monday, Reuters has accused the Binance cryptocurrency platform of being ignorant of money laundering operations taking place on its platform. Reuters reporters said that Binance served as a conduit for the laundering of at least $2.35 billion in illicit funds, including from drug traffickers, online fraudsters, and North Korean hackers.
XLoader pauses Ukraine infections: The operators of the XLoader malware said in a post on a cybercrime forum that they will no longer infect Ukrainian systems due to the ongoing war.
Arrest in Vietnam: Vietnamese officials have detained a Taiwanese national on accusations of breaching the country's financial system. According to a statement published over the weekend, the suspect engaged in "scanning for security holes, privilege escalation attacks, [and] unauthorized access to the management system of servers at banks to withdraw money in customers' accounts."
Passwordstate digital certificate: The Passwordstate password management company, which suffered a major security breach last year, said they revoked their digital certificate after they were informed by an Australian security firm that it had been used to sign malware payloads last week. More specifically, the malicious payloads were Office files weaponized with the recently disclosed Follina zero-day.
Skimmer detained in Ukraine: In the midst of its war with Russia, Ukrainian Cyber Police have detained a Bulgarian national on accusations of installing skimmers on ATM devices across the country.
CyberSpecial Forces: A new pro-Russian hacktivist group called "Киберспецназ" (CyberSpecial Forces) has been spotted active online, with the group vowing to attack NATO countries. The group becomes the 115th cyberspace threat actor known to be involved in the Ruso-Ukrainian conflict.
Confluence exploitation: The Kinsing, Hezb, and Dark.IoT botnets have been spotted exploiting the recently-disclosed Confluence zero-day CVE-2022-26134 to install their payloads on unpatched servers.
Follina gets some love: After being disclosed last week, the Office zero-day vulnerability known as Follina (CVE-2022-30190) is seeing broader adoption by the cyber-criminal underground after being previously adopted by nation-state groups, Proofpoint's threat intelligence team reported, with the latest to get on the exploitation train being the Qbot malware botnet.
Emotet deploys credit card stealer: The same Proofpoint Threat Insights team also reported a major change in the Emotet botnet, which made a comeback last year. According to the security firm, in recent attacks, a section of the Emotet botnet also tried to load a payment card stealer module inside the Chrome browser. Proofpoint said that "once card details were collected they were exfiltrated to different C2 servers than the module loader," suggesting the data might have been collected by someone running tests or who rented access to the Emotet botnet for this particular operation.
On June 6th, Proofpoint observed a new #Emotet module being dropped by the E4 botnet. To our surprise it was a credit card stealer that was solely targeting the Chrome browser. Once card details were collected they were exfiltrated to different C2 servers than the module loader.
— Threat Insight (@threatinsight) 10:17 PM ∙ Jun 7, 2022
SSNDOB seized: US and Cyprus officials have seized this week four web domains that hosted SSNDOB, a cybercrime marketplace known for selling access to detailed PII data. The website, which has been operating for a few years now, was listing the personal details of approximately 24 million Americans and made at least $19 million from its operation, the DOJ said on Tuesday.

Malware technical reports
DeadBolt: Cybersecurity firm Trend Micro published a technical analysis of DeadBolt, a ransomware strain that appeared last year and has been targeting NAS devices. The ransomware uses two ransom notes, one for the infected users and a second for the NAS vendor. If users pay the ransom, they can decrypt their files, and if NAS vendors pay the ransom, they receive a master key to unlock all of their attacked customers. However, Trend Micro said that based on its analysis, only 8% of NAS users ever paid a ransom, while a code analysis found that there is no evidence to suggest that decryption via a master key is even possible.
Black Basta: NCC Group researchers have published a technical report on the operations of the Black Basta ransomware. Trend Micro and IBM also published reports on the same gang in previous weeks. NCC Group's findings confirm Trend Micro's assessment that many Black Basta infections originate from initial infections with the QakBot trojan. In addition, Uptycs also published its own report on this ransomware strain, analyzing the Linux version of the ransomware that can target VMWare ESXi servers.
TaRRaK: Avast has released a decrypter for the TaRRaK ransomware, which has been infecting victims for almost a year since June 2021.
SVCReady: HP's security team has published a report on SVCReady, a new malware loader strain delivered via malicious Office files. Researchers believe the malware may be linked to the TA551 threat actor.
APTs and cyber-espionage
Ruso-Ukrainian war: Trellix has a summary of the cyber-attacks and cyber-espionage operations that have taken place since the onset of the Ruso-Ukrainian war and all the threat actors involved.
AppleSeed: South Korean security firm AhnLab has found copies of AppleSeed, a malware strain linked to the Kimsuky APT, being spread as router firmware updates.
Vulnerabilities and bug bounty
Micropatch for another Microsoft zero-day: ACROS Security has released a micropatch for another zero-day vulnerability in the Windows operating system. This new zero-day is named DogWalk, was re-discovered last week after first being documented in 2020, resides in the Microsoft Diagnostic Tool's sdiageng.dll library, and can be used to bypass Mark-Of-The-Web (MOTW) markings. Microsoft classified this bug as a "won't fix" when it was initially reported to the company.
This is real. We've confirmed it to work on fully patched Windows. The attack scenario is similar to CVE-2020-1300: get the user to open a CAB file, and a malicious executable is silently copied to their StartUp folder, to be launched the next time they login.
— Mitja Kolsek (@mkolsek) 12:43 PM ∙ Jun 3, 2022
Telegram denies vulnerability report: Instant messaging service Telegram denied claims made by a user on Twitter that its platform contained a vulnerability that could be used to obtain private and group chats. In a message sent to Reuters reporter Raphael Satter, the company called the claims "fantastic at best" and that they had "all the hallmarks of a hoax."
Android security patches: Google has released the Android Security Bulletin for June 2022.
Infosec industry
IBM acquires Randori: IBM's cybersecurity arm has acquired Randori, a provider of offensive cybersecurity and attack surface management (ASM) services.




