Risky Biz News: Last of the Twitter hackers to be extradited to the US
In other news: GoDaddy discloses multi-year breach; FBI reports small breach; Franco-Israeli BEC gang detained.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Spain's National Court has agreed to extradite a 23-year-old UK national to the US for his role in the 2020 Twitter hack.
Joseph James O'Connor was arrested by Spanish authorities at the request of the US government in July 2021 and has fought his extradition since.
He is accused of working together with three other individuals to hack into Twitter's internal network in July 2020.
The group gained access to one of Twitter's internal Slack channels, where they found credentials for Twitter's moderation panel.
The group used this panel to access and post tweets promoting a cryptocurrency scam on 130 Twitter accounts belonging to high-profile politicians, celebrities, and companies, such as Apple, Uber, Bill Gates, Elon Musk, and US presidents Joe Biden and Barack Obama.
Two weeks after the hack, the FBI and Justice Department arrested and charged three individuals connected to the hack, two from the US and one from the UK.
- Nima Fazeli, aka "Rolex," 23, of Orlando, Florida.
- Graham Ivan Clark, aka "Kirk," 18 of Tampa, Florida.
- Mason Sheppard, aka "Chaewon," 20, of Bognor Regis, in the United Kingdom.
Infosec reporter Brian Krebs identified O'Connor (who went online as "PlugwalkJoe" or "j0e") as one of the hackers immediately after the original hack.
Besides hacking Twitter, the DOJ also charged O'Connor with hacking TikTok and Snapchat user accounts and cyberstalking an unnamed victim.
Breaches and hacks
GoDaddy data breach: Web hosting provider GoDaddy has discovered a multi-year breach, the company said in SEC filings last week. GoDaddy says a sophisticated threat actor installed malware on its systems and even managed to steal some of its source code. The company says it discovered the breach in December 2022, when it found the group's malware on its cPanel hosting servers. GoDaddy says the malware was being used to redirect traffic from some customer websites to malicious sites.
FBI breach: The FBI is investigating a potential breach of its internal network. The breach allegedly involves an FBI computer system used in investigations of images of child sexual exploitation. The FBI described the incident as "malicious cyber activity" and told CNN the breach had been contained.
Crypto-heist #1: DeFi trading service Platypus says an attacker stole $8.5 million worth of cryptocurrency assets after exploiting a flash loan attack in its service. Platypus says the exploit targeted a logic error in its implementation of USP, a token issued by Polaris Finance. Just like all respectable cryptocurrency platforms, Platypus says it contacted the hacker to beg and grovel for its money back. Apologies, we mean "negotiate a bounty in exchange for return of the funds."
Crypto-heist #2: On the same note, DeFi platform Dexible was hacked as well. The platform allegedly lost $2 million after an attacker exploited a vulnerability in a recent trading contract Dexible added to its service. So glad the cryptocurrency community incessantly brags about how they're superior to the old-fashioned banking system, yet they get hacked every time they update their platforms.
Applied Materials indirect losses: Semiconductor technology company Applied Materials expects to lose around $250 million in the next quarter after a ransomware attack on one of its suppliers has disrupted its supply chain. Applied Materials didn't name the supplier, but The Record believes the company may be engineering firm MKS Instruments after the firm postponed an earnings call a week before due to a ransomware attack.
General tech and privacy
DMCA and GDPR abuse: Spanish company Eliminalia is behind a wave of fake GDPR and DMCA complaints that have flooded tech companies over the past year and have been used to remove articles and stories exposing financial fraud and corruption. The company advertises its services to the rich and wealthy, such as politicians, business moguls, and shady companies. According to a report from investigative journalism outfit Forbidden Stories, tech giants have often sided with Eliminalia and enforced their takedown requests, even if they were blatantly fake.
"In January 2020, Gallardo filed a claim with Digital Ocean, Pagina 66's US-based hosting provider, alleging that Sánchez had copied his content illegally. As proof, Gallardo linked to a third-party site that had published a replica of Sánchez's piece, but with a falsified earlier publish date and fake author: Humberto Herrera Rincón Gallardo.
This time, the strategy worked. Digital Ocean ordered Sánchez to remove his article from Página 66's site, or it would go black. He appealed to Digital Ocean but was unsuccessful."
Meta Verified rolls out: Meta CEO Mark Zuckerberg has announced a paid verification feature that will let Facebook and Instagram users verify their accounts using a government ID. Zuckerberg says this feature, named Meta Verified, will allow users to add a verified blue badge to their accounts, get extra protections against impersonation attacks, and direct access to customer support representatives. The feature is expected to launch later this year in Australia and New Zealand and will cost $11.99/month on the web or $14.99/month on iOS.
Twitter 2FA drama: Twitter will disable SMS-based two-factor authentication for anyone who has not paid for Twitter Blue on March 20, 2023. After that date, normal accounts will have their SMS 2FA option disabled. Normal accounts still have the option to use a security key or an authenticator app as their 2FA method. The risk to many accounts, especially those who may not be active in the coming month, comes from having their 2FA disabled without their knowledge. Twitter says it took this step because SMS 2FA was being abused by fraudsters who would establish accounts using application to person – or A2P – premium telephone numbers. When Twitter would text these numbers, Musk claims, the fraudsters would get paid. Estimated losses are in the tune of $60 million a year. Whether that's true or not, it seems certain that this is a cost-cutting measure and not about improving user security.
Government, politics, and policy
Ukraine cyber incident stats: The Ukrainian government says it recorded 2.8 times more cyber incidents throughout 2022 than in 2021. Officials say they registered 415 distinct cyber incidents throughout the year, most connected to Russia's military invasion.
Fines for SORM disobedience: The Russian Duma is working on a law that will introduce turnover-based fines for local telco providers that fail to install its SORM traffic monitoring system. SORM, initially introduced in the 90s, is special equipment installed in the telco's backend network that logs internet and telephony traffic and allows Russian law enforcement and intelligence services to search through the data. SORM is already mandatory for all Russian telcos, but no penalty was specified for companies that failed to implement it or refused to have the equipment working, which has been the case with the smaller operators. The fines will range from 0.001 to 0.003% of a telco's annual revenue, according to Russian news outlet Vedomosti.
Centralized database of fraudsters: Elvira Nabiullina, the head of the Central Bank of Russia, wants to create a centralized database of fraudsters to improve the security of Russian banks and their customers. We wonder if Mrs. Nabiullina's "centralized database" will also include all the Russian cybercrime groups and money launderers operating within Russia's borders.
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company has recently launched a new type of canary token that looks like an Azure login token and warns companies whenever a threat actor tries to use them.
Our (free) AWS Canarytokens have always been popular.
— Thinkst Canary (@ThinkstCanary) 5:04 PM ∙ Feb 13, 2023
Today, we released the Azure alternative on our canarytokens.org server¹
Attackers who find ‘em have to use ‘em (and reveal their presence).
Check out Pieter’s blog post at: blog.thinkst.com/2023/02/canary…
__
¹ also free
Cybercrime and threat intel
Crypto-seizure in Norway: Norwegian authorities seized $5.8 million worth of cryptocurrency funds stolen by North Korean hackers from the Axie Infinity game. Officials called it "the largest seizures of money ever made in Norway." The Axie Infinity hack took place in March 2022, when hackers stole more than $620 million worth of Ethereum from the Ronin Network, the cryptocurrency platform used inside the game. The FBI linked the hack to North Korea's Lazarus hacking group a month after it took place.
CEO fraud gang dismantled: Europol has dismantled a French-Israeli BEC group that tricked companies into making large payments into bank accounts under their control. Officials say the group made more than €38 million, money they subsequently laundered through bank accounts in the EU, China, and Israel. Eight gang members have been detained, with six arrested in France and two in Israel, including the group's leader. Only €5.5 million of the stolen money was recovered.
IMSI catcher gang detained: Five men were detained and charged in France for using an IMSI catcher device to collect the phone numbers of nearby individuals and use them to send out SMS spam. Officials say the suspects sent more than 424,000 messages. The SMS texts asked recipients to visit a fake health insurance website and enter their personal details. The suspects were detained following a routine traffic stop and after police spotted the IMSI catcher, according to reports in local media.
Two new pro-Russian "hacktivist" groups: Three so-called "hacktivist" groups named Furious Russian Hackers, Russian Clay, and Lira were spotted last week. Right off the bat, groups started leaking "classified NATO documents" and attacking networks in Ukraine.
AgainstTheWest: Chinese security firm PanguLabs has a report out on AgainstTheWest, a hacktivist group that has been engaging in hack-and-leak operations against the Chinese government and private companies.
Magecart attacks: Akamai researchers have spotted another Magecart (web skimmer) campaign, this one trying to pass its code as a Google Tag Manager script.
"The attackers were able to inject a malicious inline JavaScript code into the targeted websites by exploiting a vulnerability. The skimmer used techniques such as impersonating a legitimate third-party vendor, like Google Tag Manager, and hiding the malicious code through Base64 encoding."
Malware technical reports
GlobeImposter ransomware: SentinelOne says the recent TZW ransomware, spotted active in South Korea, is a variation of the GlobeImpsoter ransomware.
CatB ransomware: Fortinet has an analysis of CatB, a new ransomware strain first spotted in the wild last November.
RambleOn: Interlab researchers have a report out on RambleOn, an Android malware strain that was recently discovered on the smartphone of a South Korean journalist.
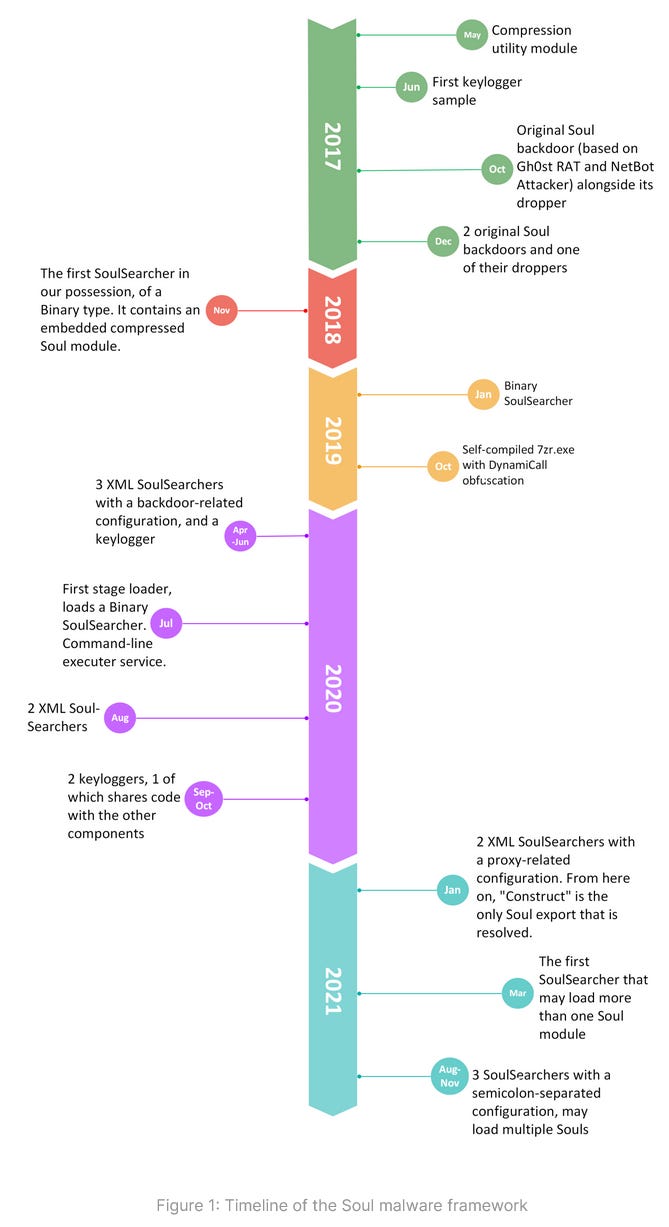
SoulSearcher: OALABS has a report out with IOCs on SoulSearcher, a backdoor-keylogger combo that has been out in the wild since 2017 and has recently been seen sporting worm capabilities.
APTs and cyber-espionage
Earth Kitsune: Trend Micro has discovered a new backdoor used by Earth Kitsune, an APT group with a history of targeting individuals who are interested in North Korea. Trend Micro says it discovered the new backdoor on the website of a pro-North Korean organization. They say the website was hacked in December 2022 and modified to prompt visitors who wanted to view videos to install a video codec. This video codec contained the new backdoor, which Trend Micro tracks as WhiskerSpy.
Gamaredon: Accenture's Gianluca Tiepolo has a report on a recent Gamaredon APT spear-phishing campaign. Tiepolo says the campaign appears to be part of a recent set of operations recently covered by BlackBerry's security team here.
Vulnerabilities and bug bounty
npm supply chain attack averted: DevSecOps company Illustria discovered that a popular npm package with nearly 4 million weekly downloads was vulnerable to an account takeover attack. Illustria researchers did not name the package. They say the package's GitHub account could have been easily hijacked because one of its maintainers used an expired domain name to receive password reset emails. Illustria says they disclosed their findings to the package's maintainer, who re-registered their domain.
Fortinet boo-boo: Patch yo' Fortinets! There's a pretty bad un-auth path traversal to command execution bug (CVE-2022-39952) in FortiNAC firewalls. This was part of the company's Patch Tuesday update.
Azure AD B2C bug: Microsoft's Azure Active Directory B2C service contained a cryptographic flaw that would have allowed an attacker to craft an OAuth refresh token for any user account. Took a while to patch, though.
"Praetorian reported this security vulnerability to Microsoft in two parts in March 2021 & July 2022 and Microsoft applied two changes in December 2022 and February 2023."
Linux bug: Trail of Bits has a write-up on a bug in the Linux readline utility that can be used for lateral movement. Tracked as CVE-2022-0563, this was patched a year ago, in February 2022. From the researcher:
"I totally fumbled reporting the CVE for this, so my name isn't listed against the CVE with MITRE... RIP my career."
Infosec industry
New tool—MAAD Attack Framework: Cybersecurity firm Vectra has open-sourced a new tool named MAAD Attack Framework, a cloud attack tool developed for testing security of Microsoft 365 & Azure AD environments through adversary emulation.
Infosec.exchange update: Infosec.exchange, the primary Mastodon for the cybersecurity community, has passed 50k members.
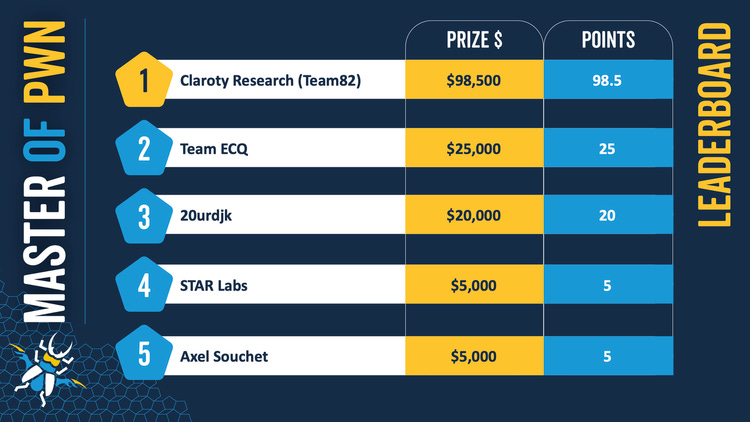
Pwn2Own Miami: The Pwn2Own ICS-themed hacking contest, which took place in Miami last week, has concluded. Team Claroty has won this year's Master of Pwn award after dominating the competition with ten successful exploits. Claroty won $123,500 of the $180,000 awarded during the contest, two-thirds of the entire prize pool. Dominated indeed!
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




