Risky Biz News: KiwiFarms discloses security breach, says user data may have been stolen
In other news: Vietnamese couple takes credit for InterContinental hotels hack; GTA6 source code stolen; and Revolut hacked "through the use of social engineering methods."
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Internet racism cesspit KiwiFarms said on Sunday that one of its service providers was hacked and that data on its users might have been stolen.
In a series of messages posted on its Telegram channel, the site's administrator said the breach occurred on Saturday at Vsys, a Ukrainian company that provides them with forward-proxy services.
"Today, the site was hacked to change everyone's avatars to logos of another site (which I am not naming because I'm not sure what the motivation is behind it)," Josh, the site's administrator, wrote on Telegram and KiwiFarm's official website. "Then, each node on the forum index was deleted one at a time."
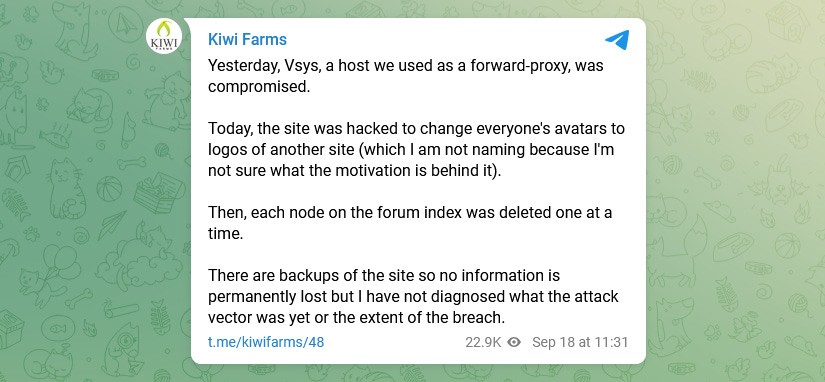
"The attacker had access to my admin account, probably through session hijacking (bypassing password and 2fa)," the admin also added.
KiwiFarms said that while information from the site's log suggests that a user database export operation performed by the intruder might have failed, registered users should still assume that their data might have been compromised through another means.
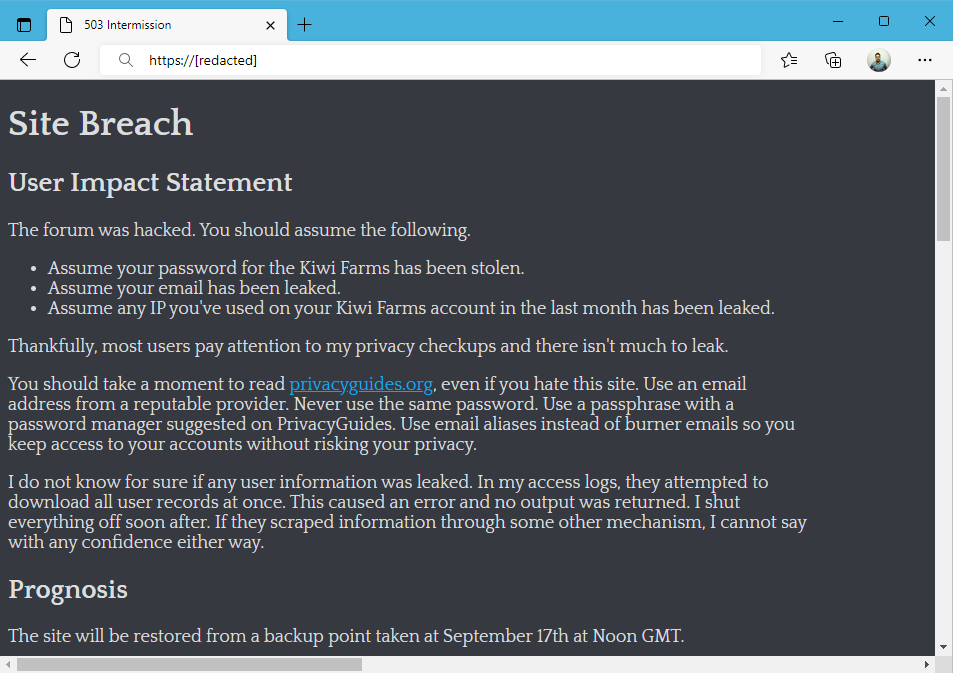
The incident sparked quite a wave of panic among the site's users, most of whom now fear that their real identities could be revealed through the stolen data, which is a very plausible scenario for those who did not practice good OpSec when registering on the site.
It’s the first Kiwi Farms telegram post comments section I’ve seen without racism.
— Kevin Beaumont (@GossiTheDog) 2:29 PM ∙ Sep 18, 2022
While it's been around for half a decade, KiwiFarms rose to infamy this summer after its members started harassing and threatening a trans streamer named Keffals. The streamer responded by arranging a social media campaign to bring down the website, which eventually succeeded with help from mainstream media and the infosec community.
Cloudflare booted KiwiFarms (after some serious convincing work), the service was then dropped by Russian provider DDoS-Guard a day later, and Portuguese web host DiamWall last week, before encountering its most recent issues with Vsys.
Breaches and hacks
IHG hackers come forward: Hackers describing themselves as a couple from Vietnam took credit for the hack of the InterContinental Hotel Group earlier this month. The duo told the BBC they gained access to the hotel's network after tricking an employee into downloading and installing malware on their system through a booby-trapped email attachment. The hackers said they then found a password vault for several of the hotel group's internal systems, including its main database, which was allegedly protected by a password of "Qwerty1234." The hackers said they tried to install ransomware on the hotel's network, but after failing, they just wiped the database instead, in frustration.
Starbucks Singapore: The data of more than 330,000 users who registered on the Starbucks Singapore web portal was put up for sale in underground cybercrime forums last week. The company confirmed the breach on Friday in an email sent to affected customers.
Revolut hack: Mobile banking operator Revolut confirmed it was hacked after a third-party gained access to its systems and stole the data of 50,150 of its customers. The incident came to light last week after the company disclosed the breach to Lithuania's data privacy regulator, where the company holds a banking license. Revolut said the hacker gained access to one of its databases " through the use of social engineering methods." In a statement to Polish tech blog Trusted Third Party, Revolut said the breach impacted only 0.16% of its customers.
Rockstar Games hack: More than 90 videos showing gameplay from the upcoming GTA6 video game was leaked online on Sunday by an individual who claimed to be the same person who hacked Uber last week. Going by Teapot, the hacker said he plans to leak more gameplay and even some of the game's source code. Rockstar Games confirmed the videos were authentic to Bloomberg's main games reporter Jason Schreier, but has not commented on the news of the hack or if the hacker did indeed steal the game's source code.
Not that there was much doubt, but I’ve confirmed with Rockstar sources that this weekend’s massive Grand Theft Auto VI leak is indeed real. The footage is early and unfinished, of course. This is one of the biggest leaks in video game history and a nightmare for Rockstar Games
— Jason Schreier (@jasonschreier) 1:21 PM ∙ Sep 18, 2022
Uber hack update: While Uber is still looking into its recent security breach, the company posted a formal update on its investigation and said that based on current evidence, there is no indication that the intruder—believed to be a teenager—gained access to any sensitive user data (like trip history). The company said that all its services, like Uber, Uber Eats, Uber Freight, and the Uber Driver app, are fully operational.
LastPass hack update: In another update to its data breach disclosure blog post, password management app LastPass said it completed its investigation into the incident and determined the hacker only had access to its systems for a period of four days in August. The company disclosed the breach on August 25, when it found that one of its developers' accounts had been compromised via social engineering.
Mosoblenergo defacement: Pro-Ukrainian hacktivists have defaced the website of Mosoblenergo, Moscow's main energy provider, and posted a photo of Oleksiy Danilov (Secretary of the Ukrainian National Security and Defense Council) against the backdrop of the Kremlin on fire.
Сайт Мособлэнерго сейчас выглядит так mosoblenergo.ru
— Илья Пономарев / Ілля Пономарьов (@iponomarev) 7:26 PM ∙ Sep 16, 2022
Hdr0 желает московским админам приятного пятничного вечера:) t.me/Hdr0_one/137
General tech and privacy
Fortnite anti-cheat: Epic Games announced over the weekend that they are now capable of detecting when controller players use a Cronus device to cheat and reduce their recoil in their Fortnite game.
FIFA anti-cheat: On the same front, EA Games also announced a new kernel-level anti-cheat system for its popular FIFA game franchise that will be launched later this week.
Government, politics, and policy
US cyber grant: The Biden administration on Friday launched a long-awaited federal cybersecurity grant program that will funnel up to $1 billion to state and local governments to upgrade their digital defenses. [Additional coverage in The Record]
Romania bans Russian antivirus products: The Romanian government has banned the use of Russian antivirus software on the network of central and local governments. Authorities cited the risk of these products being used to launch cyberattacks against government agencies. The Romanian government said the decision is only temporary and the ban will last for as long as Russia's invasion of Ukraine. Officials ordered IT departments to uninstall all existing products or disconnect them from the internet. Polish authorities similarly banned Russian antivirus software from its government networks back in June [PDF].
Kosovo to establish cyber-security agency: The Kosovo government said it plans to establish a cyber-security agency later this year following a series of DDoS attacks that disrupted its major telecom provider last week. The government on Wednesday approved a draft law on cyber security, which will include forming an agency, BalkanInsight reported.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
Canadian hacker raided: Aubrey Cottle, a Canadian hacker and a member of the Anonymous hacktivist group, said he was raided last week by Ontario police. The suspect said all his devices were seized and, as a result of the raid, was also later evicted from his rented home. Cottle told Cyberscoop that he believes the FBI is also involved in the investigation but could not tell what the raid was about.
Crypto-scam increase: Security firm Group-IB said the number of crypto-scam-related domains rose in the first half of 2022 by five times compared to last year.
According to Group-IB, 63% of the new fraudulent domain names were registered with Russian registrars, but the fake websites are primarily designed to target English and Spanish-speaking crypto investors in the US and other countries.
DEV-0796: Microsoft said they're seeing activity from a threat actor the company tracks as DEV-0796, which is using malicious links inside YouTube comments to redirect users to malicious ISO file downloads that then install a malicious click-fraud-focused browser extensions on victims' devices.
Microsoft researchers are tracking an ongoing wide-ranging click fraud campaign where attackers monetize clicks generated by a browser node-webkit or malicious browser extension secretly installed on devices. Microsoft attributes the attack to a threat actor tracked as DEV-0796.
— Microsoft Security Intelligence (@MsftSecIntel) 11:04 PM ∙ Sep 16, 2022
Altenen carding forum scam: Threat intel firm Digital Shadows said a recently hacked database that was dumped on the XSS forum appears to belong to Altenen, a former Arabic and English language carding forum, known for scamming its users. Forum DMs included in the leaked database show how the site's admins worked together to defraud their own users.
FKNO: Another lame pro-Russian hacktivist group announced its existence over the weekend, claiming the super original name of FKNO, which they say stands for "F*** NATO."
LockerGoga decrypter: Bitdefender researchers have released a decrypter for past victims of the LockerGoga ransomware. Twelve LockerGoga members were detained last year in Ukraine and Switzerland, and Bitdefender said the decrypter was created part of a joint effort between them, Europol, the NoMoreRansom Project, the Zürich Public Prosecutor's Office, and the Zürich Cantonal Police.
Malware technical reports
ConfuserEx research: Switzerland's CERT published research last week on the ConfuserEx code obfuscation tool.
Atombot: Tencent's security team said in a report in June that it was seeing threat actors exploit a GitLab vulnerability (CVE-2021-22205) to compromise servers with the Atombot DDoS malware.
Racoon Stealer 2.0: Security firm CloudSEK published a technical report on the latest version of the RacoonStealer malware, also known as Recordbreaker.
Vulnerabilities and bug bounty
Browser spellcheck leak: Otto's research team discovered that the advanced spellchecker in the Google Chrome browser and the Microsoft Editor spellchecker in Microsoft Edge will upload some of the text they verify to Google and Microsoft servers, respectively, leading to situations where PII data or passwords may be sent to these systems. These two spellcheckers are included in both browsers but are not the default ones, and users have to manually enable them for any leaks to occur.
Stray payment: Sam Curry, an Omaha-based web application security researcher, said he accidentally received $250,000 from Google in what appears to be a mistake in the company's bug bounty payouts. [Additional coverage in NPR]
It's been a little over 3 weeks since Google randomly sent me $249,999 and I still haven't heard anything on the support ticket. Is there any way we could get in touch @Google?
— Sam Curry (@samwcyo) 3:54 AM ∙ Sep 14, 2022
(it's OK if you don't want it back...)
Infosec industry
VeloCon videos: Talks from the VeloCon 2022 security conference, which took place last week, are now available on YouTube.
New tool—PEBear: Malware analyst Aleksandra "hasherezade" Doniec has open-sourced the code of PEBear, a freeware reversing tool for Windows PE files.
Surprise! #PEbear is Open Source now! github.com/hasherezade/pe… - please check it out and let me know what do you think!
— hasherezade (@hasherezade) 7:44 AM ∙ Sep 18, 2022




