Risky Biz News: KeePass disputes vulnerability designation for feature that exposes cleartext passwords
In other news: Russia blocks access to CIA and FBI websites; bulletproof hosting hotbed Seychelles to establish cybercrime unit; new data wiper malware discovered in Ukraine.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
There's a tiny bit of tech and infosec drama unfolding in the forums of password management app KeePass; in a topic related to a supposed bug that was recently assigned a vulnerability identifier of CVE-2023-24055.
The bug was reported several times over the past year, and security researchers claim that an attacker with access to a user's system can easily obtain cleartext versions for all passwords stored in a KeePass app by modifying a line in the app's XML config file.
The modification is what KeePass calls a trigger, in this case, a trigger to export the app's database in a cleartext format like CSV or HTML.
The supposed bug impacts all versions of the KeePass app, and the controversy comes from the KeePass team's refusal to acknowledge it as a security flaw, let alone fix it.
KeePass devs go by the old adage that if a threat actor has control over your system, it's not your system anymore.
On the other side of the argument, security researchers claim this is a vulnerability because no input (such as entering the master password) is required from the KeePass owner to export the passwords, which should not be possible even in situations when a threat actor gains access to a device.
There are certainly arguments on both sides of the discussion to be had here, but we're leaning towards siding with the security researchers. Password managers should not have a built-in system that dumps all your passwords butt-naked in a file without you having to enter your master password first.
But for KeePass users, things are about to get a hell lot worse in the coming weeks, as proof-of-concept code to exploit this issue was published last week on GitHub and will most likely make its way into all your run-of-the-mill infostealers and remote access trojans by the end of the year.
Breaches and hacks
Blockchain Bandit update: After six years of inactivity, the threat actor known as the Blockchain Bandit has begun moving $90 million worth of stolen cryptocurrency funds. The Blockchain Bandit is a famous hacker who used a technique called Ethercombing to steal more than 51,000 Ether coins and 470 Bitcoin from more than 10,000 users between 2015 and 2016. Ethercombing refers to a technique of reverse-engineering weak public and private key combinations and then emptying out cryptocurrency accounts that used them. Years after the last heists, blockchain analysis company Chainalysis says the stolen funds were moved to new addresses. The funds have not been laundered yet.
General tech and privacy
Incognito session protections on Chrome: Google has added a new feature to its Chrome web browser that lets users lock their incognito browser sessions using biometric authentication. Once enabled, this feature will require a fingerprint or face scan before allowing the user to access their previous Chrome incognito browsing sessions.
To enable it, go to Chrome Settings → Privacy & Security → Turn ON "Lock incognito tabs when you close Chrome."
GitHub milestone: Microsoft-owned GitHub announced last week that it passed an important milestone, surpassing 100 million registered users.
Government, politics, and policy
Russia blocks access to CIA, FBI, and RfJ sites: The Russian government has blocked access inside the country's borders to the websites of the CIA, FBI, and the US State Department's Rewards for Justice program. Russian officials with Roskomnadzor, the country's internet watchdog, told Interfax they blocked access to the websites for "spreading fakes about the Russian military and discrediting them." However, the timing of this decision is odd and telling, as it came hours after the State Department offered a $10 million reward for information on the Hive ransomware gang and its possible ties to a foreign government.
Singapore tackles SMS scam: Singapore telcos will label SMS messages from organizations that have not registered with the local government's IMDA authority as "likely scam" starting February 1 this week. The Singapore SMS Sender ID Registry (SSIR) was established last year, and registration started last November. Organizations that want to send SMS messages to Singapore residents must register in the IMDA's SSIR database, or they'll have their messages labeled "likely scam" and potentially blocked. The government says that roughly 1,200 organizations have signed up for the SSIR so far.
FCC threatens Twilio: The US Federal Communications Commission has threatened to disconnect Twilio from the US telecommunications network if the company does not take proactive steps to block robocalls originating from its systems. In a cease-and-desist letter sent to Twilio last week, the FCC said that its service had been abused by a company named PhoneBurner as part of a major mortgage scam targeting US homeowners. The FCC has given Twilio two weeks to take action against robocallers abusing its service.
AFP warning for parents: The Australian Police Force is warning parents and caretakers that online predators may abuse online chat features found inside online and mobile games to contact children. The AFP warns that predators may use the chat feature to request sexually explicit images or to meet with children. The AFP recommends that parents check on their children and who they are talking to online and look into disabling any chat or direct messaging functionality; if the game includes such a feature. The AFP also issued a second security advisory, urging parents to see if any parental and privacy settings are available on their children's digital devices and configure them accordingly.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
Hive reward: The US State Department is offering a $10 million reward for any information that can reveal the identity and location of members of the recently-disrupted Hive ransomware group or information that could help link the gang's members with a foreign government.

Golden Chickens: Something we missed last August is this eSentire report, where the company claims to have tracked down the person behind the Golden Chickens Malware-as-a-Service (MaaS). eSentire researchers believe the malware's creator (badbullzvenom) is a Moldovan national living in Canada or a Canadian sharing their account with someone in Moldova. The Golden Chickens malware has been linked to attacks carried out by three major threat actors known as FIN6, the Cobalt Group, and Evilnum.
StreamJacking: Guardio Security says it is seeing hundreds of YouTube accounts getting hijacked each day to promote Elon Musk-themed cryptocurrency scams. Researchers say the threat actor behind these attacks, which they are calling StreamHacking, is making as much as $100,000 per day via "donations" and "investments" from gullible cryptocurrency users. In some cases, users are also lured to phishing sites that prompt them for personal data and crypto-wallet passphrases, allowing the threat actor to easily empty out their accounts.
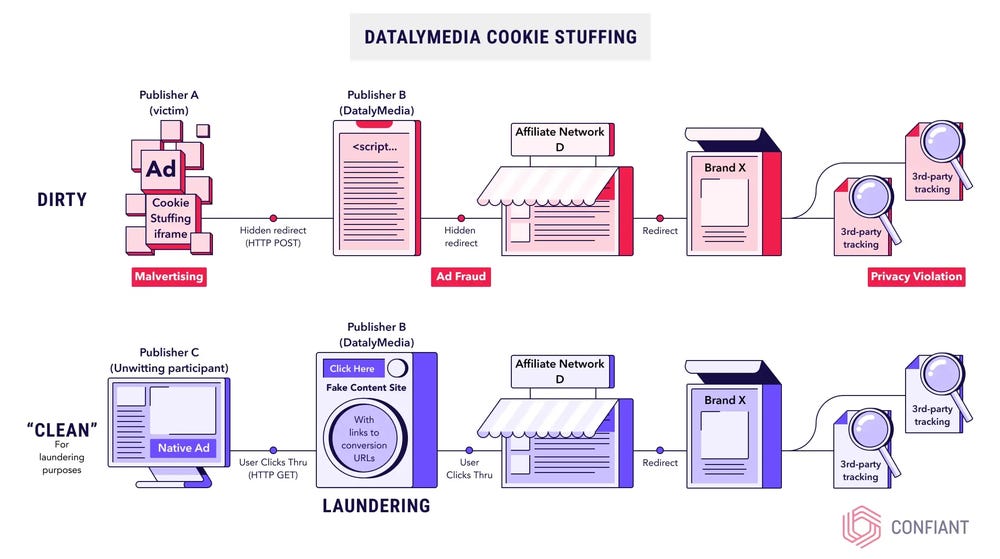
DatalyMedia: Confiant researchers say they've uncovered a malvertising campaign from a threat actor named DatalyMedia that uses cookie stuffing to generate fake clicks and defraud advertising platforms and their customers. Cookie stuffing is a technique through which a malvertiser generates fake clicks on ads and then mixes those fraudulent requests with real clicks at an intermediary service called a "launderer." Confiant says DatalyMedia has been active since at least 2015 and appears to operate through at least four legal entities.
Killnet: Radware has a report out exploring the network of "friends" that provide support for Killnet, the pro-Russian hacktivist group that has been attacking western orgs with DDoS attacks. This includes the HooliganZ, a Moscow-based jewelry manufacturer, and Russian rapper Кажэ Обойма (Kazhe Oboyma).
NoName057(16): Threat intelligence giant Team Cymru has published a report analyzing the backend infrastructure used by on pro-Kremlin hacktivist group NoName057(16). To no one's surprise, the company's researchers found that NoName hosts its backend infrastructure within Russia and that the servers are "likely operated by individual(s) with experience in systems design/maintenance." The NoName group appeared after Russia's invasion of Ukraine as Russia's answer to the Ukraine IT Army. The group is primarily known for carrying out DDoS against NATO countries that have shown their support for Ukraine. Team Cymru says that the vast majority of NoName's DDoS attacks are carried out via two interlinked hosting providers named MIRhosting and Stark Industries, which provides the opportunity for easy prevention and mitigation.
Opportunistic phishing in Italy: Italian security firm D3Lab says it spotted an SMS phishing campaign exploiting the recent downtimes of local email providers Libero and Virgilio to trick users into handing over their email account credentials.
New phishing lures: Symantec researchers say they're seeing a threat actor distributing the Agent Tesla malware using a novel email lure related to hand sanitizer and soap dispenser technology. The company believes this may target companies in areas still grappling with the COVID-19 pandemic. On the same note, threat actors are also using the recent tech layoffs as a lure as well, per Zscaler.
Phishing explosion: Google's VirusTotal division says the number of URLs used in phishing attacks in 2022 has doubled compared to the previous year, in 2021. Furthermore, VirusTotal says the number of emails distributing any kind of malware increased its share on the threat landscape from 11.4% in 2021 to 26.5% in 2022, highlighting an explosion in the number of threats sent to users via their email accounts. VT's conclusion is below:
"As a very brief summary, email as a distribution vector hosting suspicious PDFs in external hosting was an unexpected return to the past. The rotation in exploitation techniques seems to follow whatever works better for attackers given the quick adoption of any exploit, with some outliers such as Follina. It is also interesting comparing the scale of some threats that we sometimes tend to underestimate just because they became ubiquitous, with examples such as Mirai or Zloader. LOLBINs seem to keep growing in terms of internal monitoring to avoid lateral movement. Finally, Collections offer a OSINT-based high level overview of actors and victimology."
Cybercrime unit in Seychelles: The government of Seychelles plans to establish a cybercrime unit as part of its police forces. The unit was announced during a recent visit of an Interpol delegation to the small archipelago in the western Indian Ocean. Seychelles is currently one of the main harborers of bulletproof hosting providers, a term used to describe web hosting companies that knowingly host malicious and malware sites.
Malware technical reports
Raspberry Robin: eSentire's team has a technical breakdown of the Raspberry Robin malware, a worm spreads via infected USB drives and connects to compromised QNAP servers to fetch additional payloads.
Gootloader: Mandiant has published a technical report on a typical infection with Gootloader, a malware strain "exclusively" used by the UNC2565 threat actor.
GuLoader: On the same note, Trellix also has a report on the GuLoader malware, also known as CloudEye, and not to be confused with the aforementioned Gootloader. Both GuLoader and Gootloader saw broad use last year, but GuLoader was primarily used to deploy run-of-the-mill infostealers and RATs like Agent Tesla, LokiBot, NanoCore RAT, and NetWire.
APTs and cyber-espionage
BlueBravo: Recorded Future has the lowdown on a campaign carried out by an APT the company tracks as BlueBravo. Recorded Future says the group overlaps with Russian APT activity tracked as APT29 and NOBELIUM, which Western governments and researchers have linked to the Russian Foreign Intelligence Service (SVR).
Sandworms' SwiftSlicer: Cybersecurity firm ESET says it detected a new data-wiping malware strain that was deployed in Ukraine by Sandworm, a Russian cyber-espionage group linked to Russia's military intelligence service, the GRU. Named SwiftSlicer, the wiper is written in the Go programming language and works by rewriting files with randomly generated data and deleting local volume shadow copies to prevent data restoration operations. ESET says it detected the malware for the first time on January 25, last week, but did not share details about the victim(s).
Ukrinform attack: Ukraine's cybersecurity agencies, the SSSCIP and CERT-UA, say the Russian hackers who attacked the country's Ukrinform news agency deployed five data wipers, and not just one, as they initially reported the day following the attack. Besides the CaddyWiper malware, officials say the attackers also deployed versions of ZeroWipe, SDelete, AwfulShred, and BidSwipe. The SSSCIP and CERT-UA say the Ukrinform attack was "only a partial success" as it did not impact all of the agency's data storage systems. Ukrainian officials attributed the attack to Sandworm, a Russian cyber-espionage group linked to Russia's military intelligence service, the GRU.
Vulnerabilities and bug bounty
OpenEMR vulnerability: SonarSource researchers have published details about a trio of vulnerabilities in OpenEMR, a popular open-source software for electronic health records and medical practice. The issue allows for remote code execution attacks. The vendor patched it in v7.0.0 last November.
Lexmark zero-day update: Lexmark has published security patches to address a zero-day vulnerability used at the Pwn2Own Toronto 2022 hacking contest and for which proof-of-concept code was published earlier this month. The zero-day has been assigned the CVE-2023-23560 identifier. See more in the company's security advisory [PDF]. Tens of Lexmark printers have been officially confirmed as vulnerable and will need to be patched.
Infosec industry
Remembering SQL Slammer: Arbor Networks has a post on the SQL Slammer worm, the worm that infected ~75K vulnerable MSSQL servers worldwide 20 years ago.
"SQL Slammer was the latest in a series of aggressively-propagating internet worms such as CodeRed and NIMDA, which were intended to compromise vulnerable computers and subsume them into botnets which could be used to send spam email, propagate malware, and launch DDoS attacks. Like the original Morris internet Worm of 1988, the authors of these newer worms didn't seem to realize that designing these worms to propagate at network line rates would result in an inadvertent DDoS attack against the networks to which they were connected — thus defeating the purpose of the worm, which was to compromise as many systems as possible."
Cyber Partisans interview: Videos from The Secret Club of Radical Transparency conference, held last September, are now live, including an interview with Yuliana Shemetovets, a spokesperson of the Cyber Partisans. The Secret Club of Radical Transparency is a conference on hacking, whistleblowing, surveillance, and freedom of information.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




