Risky Biz News: JumpCloud compromised by APT group
In other news: Supply chain attack hits Pakistani government; WordPress security plugin logged user passwords in plaintext; UK IT worker sentenced to prison for trying to hijack ransomware payment.
This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Cloud hosting provider JumpCloud says that its recent rush to change all customer API keys was made in the aftermath of discovering a major security breach of its internal systems by a state-sponsored APT group.
In a post-mortem of the incident, JumpCloud CISO Robert Phan says the attack was "extremely targeted and limited to specific customers."
A timeline of the intrusion, according to the company's report, is as follows:
- June 22: The attacker gains access to some of JumpCloud's infrastructure following a successful spear-phishing attack.
- June 27: JumpCloud discovers anomalous activity on an internal orchestration system. The company links the activity to the spear-phishing attack, rotates credentials, and rebuilds infrastructure while it investigates its internal system and past logs.
- July 5: As part of its investigation, JumpCloud discovers unusual activity in the commands framework for a small set of customers.
- July 5: JumpCloud rotates all its customers' admin API keys and notifies customers of an "ongoing incident."
- July 12: The company links the attack to an APT group and publishes IOCs from the intrusion.
JumpCloud did not reveal what type of customers the attacker targeted, nor from which state it believes they operate.
At least two sources have told this newsletter the incident is suspected to have been carried by a DPRK group—although this early attribution comes with many asterisks.
A screenshot from a Slack channel for engineers from the CDN space also covered the intrusion and warned of possible links to a North Korean group, although the poster did not specify which one.
The targets of the JumpCloud intrusion are extremely likely companies from the cryptocurrency space. North Korean groups are notorious for their dogged and unrelenting pursuit of organizations from the financial and cryptocurrency verticals. Funds stolen from these companies are squirreled away and laundered back to North Korea, where—according to the UN and US—they're used to fund the country's weapons and missiles program.
Throughout the past decade, DPRK groups have used an arsenal of tactics to target and breach these types of companies. They have compromised the personal devices of employees as a way to pivot to corporate networks, they got some of their own programmers hired at their targets where they served as malicious insiders, and have hijacked accounts at domain registrars and cloud providers as a way to deploy malware on their target's server infrastructure.
One of their latest successful operations took place earlier this year when they pulled quite an innovative supply-chain-attack-inside-a-supply-chain-attack by compromising the installers of VoIP software provider 3CX in an attempt to breach financial trading companies across the globe—the typical users of this type of software. That hack netted the group quite the victims, far beyond what they initially expected, including government agencies and critical infrastructure operators.
As for this latest (suspected DPRK) intrusion, we wonder if the attackers realized that JumpCloud is one of GoFundMe's server providers. They must have! It was on JumpCloud's front page.
Updated on July 20 to add that SentinelOne has publicly and independently confirmed this story as a DPRK hack and linked it to the TraderTraitor (Jade Sleet) APT.
Breaches, hacks, and security incidents
MOVEit hacks: Stock photography portal Shutterfly and the Discovery Channel are the latest victims to be listed on Clop's leak site as a victim of the MOVEit hacks—now, more than 200.
Russian TV stations hacked (again): Ukrainian hackers breached and took over the TV broadcasts of several Russian TV stations last week. The hackers showed a clip from a Ukrainian Army commercial and warned that the "hour of reckoning has come" for Russian troops. The list of hacked TV channels includes RosTV, Zvezda, Ren TV, and Channel One. [Additional coverage in Obozrevatel]
General tech and privacy
New DUNS policy on the Play Store: All organizations that want to upload Android apps on the official Play Store will have to add a DUNS number to their Play Store developer account going forward. Google says the new requirement will help fight malware and prevent scams and fraud. DUNS numbers are nine-digit codes issued by risk management company Dun & Bradstreet and are used to verify that a real company exists in the real world. All new Play Store developer accounts will have to provide a DUNS number starting on August 31 this year. Existing developers will receive more information on how to update and verify their accounts in October.
OpenBSD new security feature: The OpenBSD team has enabled a new security feature to prevent CPU-level attacks. The new security feature is named Branch Target Injection on AMD chips and Indirect Branch Tracking on Intel ones. It will be enforced by default for all OpenBSD binaries. The feature will protect the "control flow," a technical term used to describe the order in which operations are executed inside the CPU. Malware and vulnerability exploits often hijack an app's control flow to inject their code and run it in the context of the victim app.
Descent into the far-right: Twitter continues its descent into the far-right, QAnon, and fascist-loving crowd with reports the company is now paying far-right figures to post on the platform through its creator program. Couple this with the fact that Twitter cowers before any autocratic regime and promotes government propaganda like there's no tomorrow, and you have a pretty accurate view of the Twitter 2.0 Musk promised a while back. [Additional coverage in the Washington Post/non-paywall]
Twitter changes everyone's DM settings: Twitter has forcibly changed everyone's DM settings as part of an attempt to limit spam coming from Twitter Blue accounts (which is quite a lot these days because spammers just buy a Twitter Blue subscription). Users who had their DMs open for everyone had this feature restricted last week. Going forward, Twitter says users will be able to receive messages only from their friends and Twitter Blue accounts they follow unless they change the setting back to open once again. [Additional coverage in TechCrunch]
Spotify makes private playlists private: Music streaming service appears to have made all the private playlists of their users public. [Additional coverage in BleepingComputer]
Reddit removes years of DMs: And keeping with companies that do whatever they want, Reddit has just removed years of private conversations from users' accounts—all without any warning. [Additional coverage in Mashable]
Meta blocks EU users on Threads: Meta has blocked EU users from using a VPN service to create and access Threads accounts. The service never launched in the EU because Meta doesn't like the GDPR and private protection laws.
Government, politics, and policy
Dutch government bans ten mobile apps: The Dutch government has secretly banned employees from installing ten mobile apps from adversarial nations on their work devices. The ban went into effect in March, and initial media coverage focused on the government's TikTok ban. Since then, the name of four other apps have also become public, and they include Chinese online shopping app AliExpress, Chinese instant messaging client WeChat, Chinese video editing software CapCut, and Russian social media app VKontankte. The name of the other five apps are not known, but all ten apps are from countries such as China, Russia, Iran, and North Korea. [Additional coverage in NOS/English coverage in NLTimes]
Sponsor interview
This week's sponsor is RunZero. In this Risky Business News sponsor interview, Tom Uren talks to RunZero CEO Chris Kirsch about how the company has evolved from offering an active scanning product to one that can now discover assets on OT and cloud environments using both active and passive scanning approaches:
Cybercrime and threat intel
Rogue IT worker sentenced: A British man has been sentenced to three years in prison for blackmail and unauthorized access to a computer network after he tried to hijack a ransomware payment from his employer. The incident is related to a February 2018 ransomware attack that hit an Oxford-based company where Ashley Liles was working as an IT security analyst. UK officials say that after his employer got hit by a ransomware gang, Liles abused his position in the company's IT staff to secretly log into his manager's email account and replace the attacker's Bitcoin address with his own. Liles also created an email address that was nearly identical to the attackers' address and pressured his employer to pay. The scheme collapsed when the company's security team noticed the unauthorized access to the executive's email, and a subsequent investigation tied the intrusions to Liles' home IP address.
Scareware developer arrested after 10 years: The Spanish National Police detained a Ukrainian national for his involvement in a large-scale scareware operation between 2006 and 2011. The scheme infected computers and showed popup messages that told users they were infected with malware. The popups urged users to buy a security program from the group for $129. The suspect was arrested at the Barcelona El Prat airport shortly after arriving for a planned city visit. He was arrested based on an Interpol Red Notice issued by the US, and Spanish authorities say the suspect had been on the run for more than ten years.
Pompompurin pleads guilty: BreachForums administrator Conor Brian Fitzpatrick has pleaded guilty to hacking and child pornography possession charges. Known online as Pompompurin, he was arrested in March this year at his home in Peekskill, New York. According to the plea agreement [PDF], Fitzpatrick could face up to 40 years in prison and a fine of up to $750,000. The legal proceedings and guilty plea were delayed after Fitzpatrick reportedly attempted suicide and was hospitalized in April. [Additional coverage in DataBreaches.net]
New npm malware: Sixty-four malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Malicious GitHub repos dropping malware: A security researcher has discovered two GitHub repositories (Twitter-Cracker, Valorant-Account-Checker) that install malware on users' systems. The malware includes an infostealer, a Discord token grabber, a cryptominer, and a possible virus that infects other local apps.
Genesis Market sold to new owner: The administrator of the Genesis Market has announced that the platform has been sold to a new owner. The sale comes after the FBI seized the clearnet version of the Genesis Market in late March, making this transaction quite an interesting development. Who in their right mind buys a cybercrime platform actively targeted by the FBI? [Additional coverage in The Record]
Malware technical reports
Website redirection malware: Sucuri has the details on a piece of malware they found on hacked websites that redirects incoming visitors to third-party domains in order to generate ad revenue. The oddity in this campaign is that the redirection was first redirecting users to parked domains before users were sent to their destination sites.
BlotchyQuasar: IBM X-Force has published a technical analysis of BlotchyQuasar, a new banking trojan launched this year by Hive0129, a cybercrime group from South America.
"In comparison to the large threat landscape of banking trojans impacting the LATAM region, BlotchyQuasar clearly stands out. Most banking trojans such as Ousaban or Grandoreiro are developed in Delphi, whereas .NET is used far less. However, many of BlotchyQuasar's sophisticated capabilities are shared with other banking trojans, such as the installation of root certificates, the use of proxy auto-config as well as a facilitation for hidden-VNC tools. It is also less likely to be detected as a banking trojan, due to its use of commodity loaders and the well-known QuasarRAT code-base, which acts as a smokescreen. Nevertheless, BlotchyQuasar boasts all features of a classic banking trojan with the ability to detect, manipulate and impersonate targeted banking applications for financial gain."
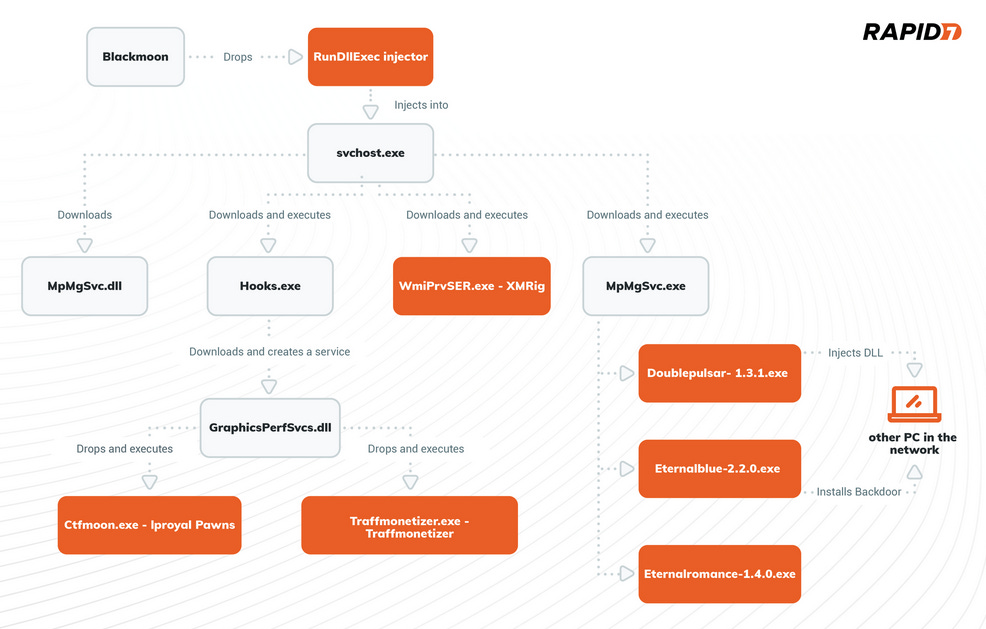
Blackmoon: The operators of the Blackmoon (KRBanker) banking trojan have retooled their code and are now operating as a malware delivery service. The group has been spotted infecting victims with a new version of their trojan and then delivering other payloads, such as cryptominers and proxyware traffic stealers. Blackmoon has been active since 2015 and has primarily operated by redirecting infected users to fake banking login portals where the gang stole its victims' login credentials. According to Rapid7, Blackmoon's recent pivot to a Dropper-as-a-Service model appears to have taken place in November of last year. Blackmoon is the latest in a long list of banking trojan operations that have jumped into the malware-dropping business. Other operations that have gone down this path—with great financial success—include Emotet, TrickBot, and Qakbot.
Sponsor Demo
RunZero is one of this newsletter's main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network, including OT devices in critical environments. To learn more, please check out this runZero product demo below:
APTs and cyber-espionage
Pakistani government supply chain attack: Security firm Trend Micro has discovered a supply chain attack targeting Pakistani government agencies. The company says it found a version of the Shadowpad backdoor hidden inside E-Office, an app developed by the government for its own employees. The Shadowpad malware was discovered in 2017 in another supply chain attack and has been historically used by multiple Chinese cyber-espionage groups such as APT41, Earth Akhlut, or Earth Lusca. Trend Micro has not linked this attack to any specific Chinese APT but says it found links to past Earth Lusca IOCs. [Archived]
XDSpy: Russian security firm FACCT has published details about a new XDSpy APT campaign targeting Russian organizations. XDSpy is an APT discovered in 2020 that has historically targeted Russian organizations only. FACCT says victims received a phishing email from the group that asked organizations to review a list of employees who "symphathize with groups that want to destabilize Russia." The phishing campaign used emails posing to come from the Ministry of Emergency Situations and tried to infect victims with a backdoor. Victims included Russian private companies and a well-known research institute.
Armageddon APT: Ukraine's CERT team has published an analysis of recent Armageddon (UAC-0010) APT operations, which also appear to have included a destructive attack against a Ukrainian information infrastructure facility.
Storm-0558: Microsoft has published more technical details about the Storm-0558 attack that compromised the email accounts of government officials across Europe and the US. Microsoft says it still hasn't discovered how the attacker managed to gain access to one of its MSA consumer signing keys, which Storm-0557 used to sign email tokens and access victim accounts. Several theories on how that could have happened are shaping up.
Vulnerabilities, security research, and bug bounty
Microsoft bug reporting: Microsoft's Security Response Center (MSRC) has published a detailed step-by-step description of how it handles bug reports.
Ghostscript RCE PoC: Kroll has released details and a PoC for CVE-2023-36664, a remote code execution in the Ghostscript PostScript processing engine. According to researchers, exploitation can occur upon opening a file.
WP plugin logs passwords in plaintext: The developers of the All-In-One Security WordPress plugin have released an urgent security update to fix an issue where the plugin logged user passwords in plaintext. The new version fixes the accidental logging issue and also removes old logs. The plugin's developers advised websites to force a password change for all their users in order to mitigate any accidental exposure of user passwords caused by their bug.
Crit.IX vulnerabilities: Armis researchers have discovered a set of nine vulnerabilities—which they named Crit.IX—in Honeywell's Experion ICS automation platform. The vulnerabilities can be used to alter the operation of DCS controllers, hide any modifications from the Experion platform, and hijack industrial equipment. Armis says Crit.IX vulnerabilities can be exploited without authentication but that the attackers require network access to a device. Honeywell has released fixes for its Experion platform to address the issues, and more details about the vulnerabilities will be presented next month at BlackHat.
EchOh-No vulnerability: A team of security researchers has discovered a vulnerability in Echo, an anti-cheat and cheater detection software advertised to gaming companies. The vulnerability resides in the tool's kernel driver and can be exploited by attackers to gain NT Authority\SYSTEM privileges on PCs where the Echo service is installed. Researchers say they tried to disclose the vulnerability to the Echo team, but they were mocked and banned from their Discord channel. Proof-of-concept code for the EchOh-No vulnerability is available on GitHub. The EchOh-No blog post also prompted other researchers to go looking into the Echo driver and find additional vulnerabilities.
Satellite security decades behind: A team of academics from Germany has analyzed the firmware of three low-earth orbit satellite models and found satellite security practices lagging by decades compared to modern laptops and mobile devices. Researchers found the firmware to be prone to several types of vulnerabilities, lacking basic protection features such as encryption and authentication. The researchers claim they devised attacks that could hijack satellite systems, cut satellites off from their ground stations, move satellites to new areas, and even crash them into the ground or other space objects.
ICS security paper: ICS security engineer Marina Krotofil has published a 133-page whitepaper on the cyber-physical security of ICS systems.
"The major objective of the white paper is to give the readers comprehensive yet sufficiently concise background on the engineering foundations of industrial control systems and their security requirements as well as to introduce the cyber-physical attack lifecycle. The white paper is written for a broad audience and is meant to be understandable even for people with no previous knowledge of industrial control systems and/or engineering background."
Infosec industry
Hardwear.io USA videos: Talks from the Hardwear.io USA 2023 security conference, which took place at the end of May, are now available on YouTube. More videos will be added to the playlist in the coming days.
fwd:cloudsec videos: Talks from the fwd:cloudsec 2023 security conference, which took place in mid-June, are now available on YouTube.
Summercon videos: Talks from the Summercon 2023 security conference, which took place last week, are now available on YouTube [Day 1 and 2].
Pass the SALT videos: Talks from the Pass the SALT 2023 security conference, which took place at the start of July, are now available on the conference's Ubicast page.
New tool—BINSEC: A group of security researchers has open-sourced BINSEC, a tool for binary code analysis.
"It relies on cutting-edge research in binary code analysis, at the intersection of formal methods, program analysis, security and software engineering. It is powered up by state-of-the-art techniques such as binary-level formal methods, symbolic execution, abstract interpretation, SMT solving and fuzzing."
New tools—AI VPN and Slips: Stratosphere IPS, a Cybersecurity Research Laboratory at the Czech Technical University in Prague, has open-sourced two new security tools. The first is AI VPN, a tool that performs security assessments of VPN clients' network traffic to identify cyber security threats. The second is Slips, a Python-based intrusion prevention system (IDS/IPS) that uses machine learning to detect malicious behavior in network traffic.
New tool—ShellSweep: Splunk's Michael Haag has released a tool named ShellSweep that can detect potential webshell files in a specified directory.
New tool—LolDriverScan: Security firm FourCore has open-sourced a tool named LolDriverScan that can scan for vulnerable drivers on their system. The tool uses a list of vulnerable drivers retrieved from the loldrivers.io website.
New tool—IAMActionHunter: Rhino Security has open-sourced a new tool named IAMActionHunter. The tool is an IAM policy statement parser and query tool that aims to simplify the process of collecting and understanding permission policy statements for users and roles in AWS Identity and Access Management (IAM).
"Although its functionality is straightforward, this tool was developed in response to the need for an efficient solution during day-to-day AWS penetration testing."
IDA Rust support: Hex-Rays has promised to improve IDA's support for Rust code.
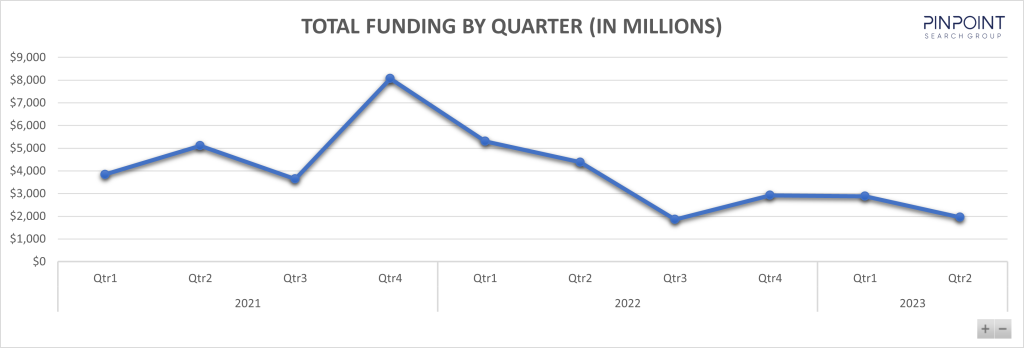
Infosec investments in Q2 2023: The Pinpoint Search Group says it tracked more than $1.9 billion in cybersecurity funding rounds and investments across the second quarter of 2023. The number is 55% down compared to the same period in 2022, when cybersecurity firms raised $4.3 billion. This year, cybersecurity vendors raised $4.8 billion over 172 rounds, 50% down from $9.7 billion raised in H1 2022. Pinpoint says inflation and fear of recession posed a major factor in less funds being raised this year. [Additional coverage in CybersecurityDive]
Security for the board: Google Cloud has published the second edition of the "Perspectives On Security For The Board" report. This edition deals with zero-days and AI security. Get the PDF for the first and second editions here.
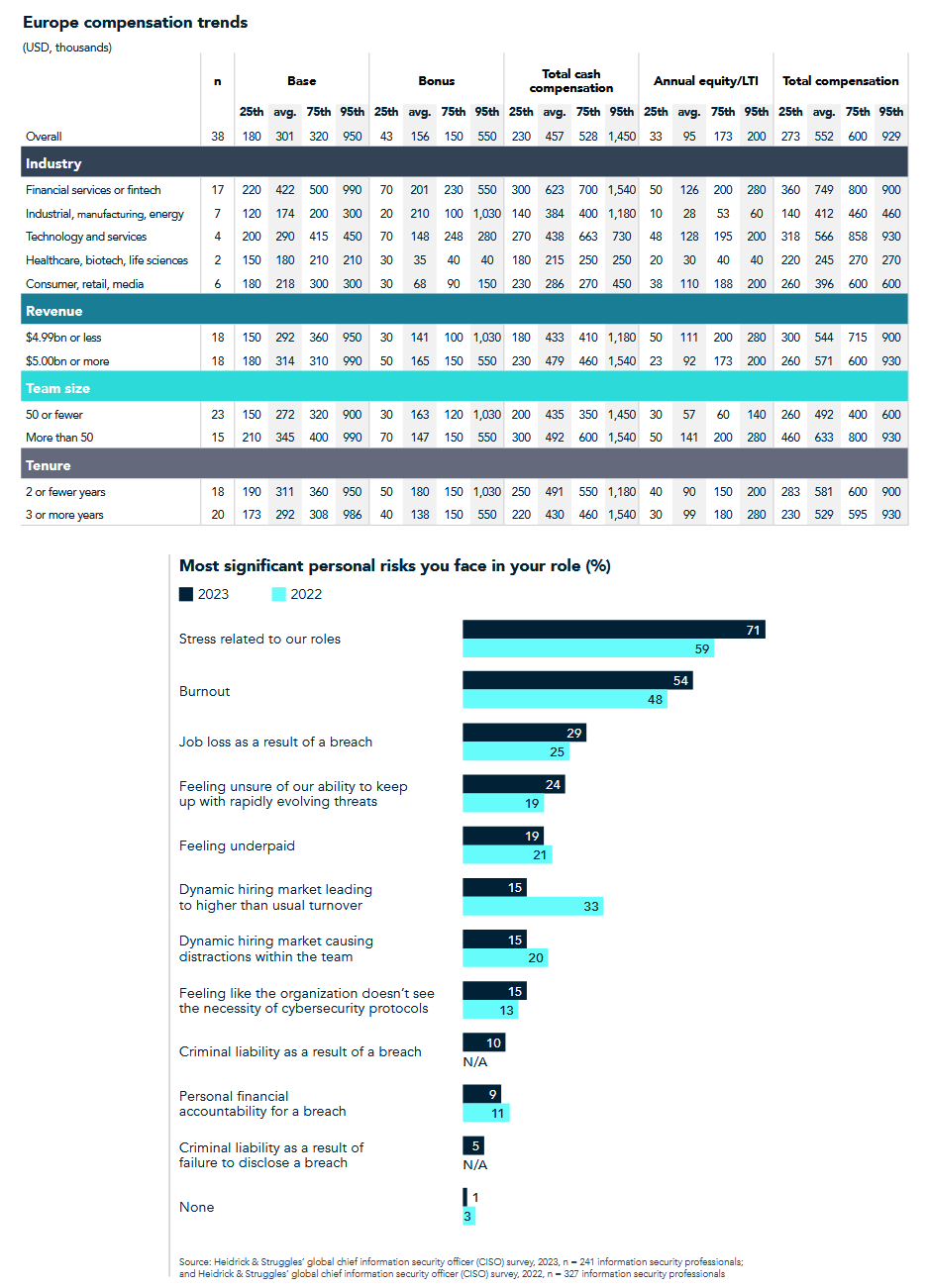
CISO survey: Executive search company Heidrick & Struggles has published the results of a survey with 262 CISOs from around the globe. The survey includes compensation trends and tables for CISOs working in Europe, the US, and Australia, as well as answers on various topics such as job stress factors, board support, severance policies, personal risks, and more. On the same note, Censys has a similar survey/report out, too, focusing on the vulnerability management side of things.
Risky Business Podcasts
In this podcast, Patrick Gray and Tom Uren talk about Citizen Lab's analysis of WeChat's behavior and its privacy policy.




